攻撃と侵害は数分で発生する可能性があり、 攻撃プロセス→ 侵害 → データ漏洩 → インシデント検出 → 応答と除去には数日、数週間、場合によっては数か月もかかります。 ほとんどの場合、これは攻撃者がデータを侵害した後に発生します。 同時に、シスコの情報セキュリティに関する年次報告書によると、セキュリティの専門家は就業日中に受信する脅威メッセージの56%しか処理できず、これらの脅威アラートの中で正当であると認識されるのは1秒に1回だけです(つまり28%)。 したがって、インシデントの44%は無視されます!
同時に、市場には、すべてのインシデントを処理できるリソースだけでなく、システム全体も非常に不足しているため、サイバー攻撃の初期段階でそれらに対応することができます-理想的には運用前に、脅威に関する分散した知識を蓄積し、受信したデータを共有します、脅威の原因を調査し、すぐに対応します。 考えられる脅威に関する情報をより迅速に蓄積するには、さまざまなソースからの有用なデータを共有するよう努力する必要があります。 同時に、この情報が標準化されていることが重要です。つまり、データの送信と提供のための標準とプロトコルが事前に定義されています。
脅威追跡は、効果的なビジネス保護のための最も重要な機能の1つです。 TI-脅威、攻撃が彼らに危害を加える前にそれについて学ぶことを可能にするシステム。 インシデントが発生した場合、TIは、既存の脅威または潜在的な脅威に関するコンテキスト、メカニズム、侵害の指標、および分析を使用して知識ベースを拡大しながら、対応、分析、および調査することができます。
脅威インテリジェンスタスク
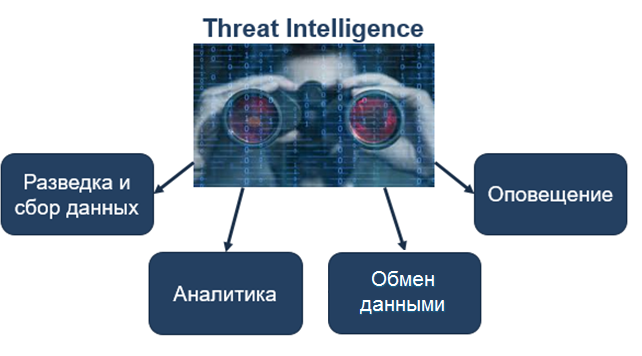
図1.脅威インテリジェンスタスク
脆弱性と脅威インテリジェンスとインテリジェンス
TIはセキュリティシステムに統合する必要があり、脆弱性と脅威に関する情報を公的および私的ソースから集中的に収集する機能を提供する必要があります。
分析
TIは、脅威への対応に関する推奨事項の検出、開示、開発、および発行に関する知識ベースを分析および構築する必要があります。
データ交換
TIは、受信したデータをリアルタイムで交換する機能も提供する必要があります。 分析情報は、内部および外部の両方の保護手段に標準化された形式で即座に配布される必要があります。
クイックアラート
TIは、分類されたデータを持つ単一の標準化されたデータベースを使用して、あらゆるエンドポイントでの攻撃と脅威について迅速に通知する必要があります。
脅威インテリジェンスのデータ型
TIは、戦術的、運用的、戦略的の3種類のデータを扱う必要があります。
戦術
攻撃データ:侵入者が使用するツール、戦術、技術および手順(TTP)、侵害インジケータに関するデータ(IoC)は、インフラストラクチャ内の悪意のあるアクティビティの兆候を検出するための個別のデータです。
運用中
新しい脅威ベクトル、キルチェーン、情報処理プロセスを侵害する方法などを追跡することで取得した現在および予測される攻撃に関するデータ。
戦略的
情報セキュリティシステムの開発戦略を開発するというさらなる目標を掲げた、世界の脅威の傾向に関する分析データ。
Threat Intelligenceプロセスを構築するために必要なもの
利用可能なすべての外部および内部ソースから受信した情報に基づいた対策を使用して、脅威を検出して対応するプロセスを構築するには、次のことが必要です。
•データソース(フィード)を特定する-侵害の兆候のソースデータを取得する場所(内部と外部の両方)。
•内部分析の実施-組織内には、方向性のある有益な情報を特定して統合できる専門家や関連部門の専門家が多数いる場合があります。
•データ提供の異なるソース間の効果的な通信のために、データの転送と提供のためのオープンな標準とプロトコルを導入します 。 この段階では、すべての脅威を記述し、侵害クラスに組み合わせて正常に転送することが重要です。
•データの処理と分析のためのプラットフォームを導入します。 フィード、API、標準、プロトコルがすでに含まれている可能性があり、さまざまなシステムと統合できるなど、独自のオープンソースソリューションか既製のオープンソースソリューションかを分析する必要があります。
データソース
内部データソース
まず、内部情報保護ツールからのSIEMまたはLMなどを使用して、データ収集の可能な実装に関して社内で分析を行うことができます。 したがって、有用なデータを取得できます。
•ネットワークトラフィックの異常(Netflow / jFlow / sFlow)。
•異常なIPアドレスからのアクティビティ。
•DNSクエリ。
•URLおよびURI。
•SMTPヘッダー。
•メールアドレス。
•悪意のあるコードのサンプル。
•ユーザーアクティビティ。
•ログイン試行の失敗。
•管理アクセス。
•DBMSを使用した操作。
•非定型ポートでの接続。
•非定型プロトコルの出現。
•サービスプロトコルのパケットサイズの標準との不一致。
•アノニマイザーのアドレス。
•HTTPのユーザーエージェント。
•悪意のあるIP。
•ユーザー、サイト、ファイルなどの評判
外部データソース
セキュリティ機能を強化するには、IoCおよびその他の脅威に関する情報を入手できる外部リソースを特定する必要があります。 同時に、会社のニーズに応じてフィードソースを選択する際の重要な要素を考慮する必要があります。
•ソースのタイプ。
•さまざまなデータ形式(JSON、XML、CyBOX、STiX、CSVなど)のサポート。
•情報提供の頻度。
•提供されるデータの量。
•データを提供するソースを信頼します。
•企業インフラストラクチャのコンプライアンス。
•価格。
最も人気のある外部フィードソース
図2.最も一般的な外部フィードソース
内部分析
内部および外部フィードに加えて、会社は以下の存在下で独立した独立した分析を行うこともできます。
•事件調査員。
•マルウェア分析の専門家。
•情報セキュリティの分野で「ホットな」ニュースを追跡するスペシャリスト。例:
o侵害されたサイトおよび感染したサイト。
oフィッシングリソース。
o悪意のあるファイルのハッシュ。
o悪意のあるコードが検出されたプロセス。
oレジストリキーなど
•リアルタイムで明らかになった情報。
この段階で見つかったすべての情報は、関連する専門家によって確認およびテストされ、その後単一のソースに入力される必要があります。 検証とテストに加えて、この段階では、考えられるリスクを軽減するための推奨事項を策定することも重要です。
TI規格
特定されたすべての脅威は、標準化されて記述される必要があります。 また、それらに関する情報を送信する機能を提供する必要があります。 現在、データを提供および送信するこれらの問題を解決するための多数のオープン標準およびプロトコルがあります。 最も人気のあるものを検討してください:
• STIX (Structured Threat Information eXpression)-統合されたサイバー脅威情報(CTI)を提供するために使用される標準。 さまざまな分野のさまざまな脅威と関連パラメータの説明を共有できます。 STIXは、次のような統合されたインシデント情報を提供します。
o情報オブジェクト(たとえば、レジストリキーの作成、特定のIPアドレスへのネットワークトラフィック、特定のアドレスからの電子メールの送信など)。
oインジケータ。
oインシデント;
o戦術、方法、攻撃の手順(攻撃パターン、マルウェア、エクスプロイトなど)。
o操作オブジェクト(脆弱性、セキュリティエラー、不適切な構成など)。
o対策(インシデントレスポンスまたはセキュリティの脆弱性/エラーの修正);
oサイバー攻撃のグループ(一連のインシデント、TTP)。
oサイバー脅威への参加者(識別、敵の特性)。
以下は、STIXアーキテクチャです。
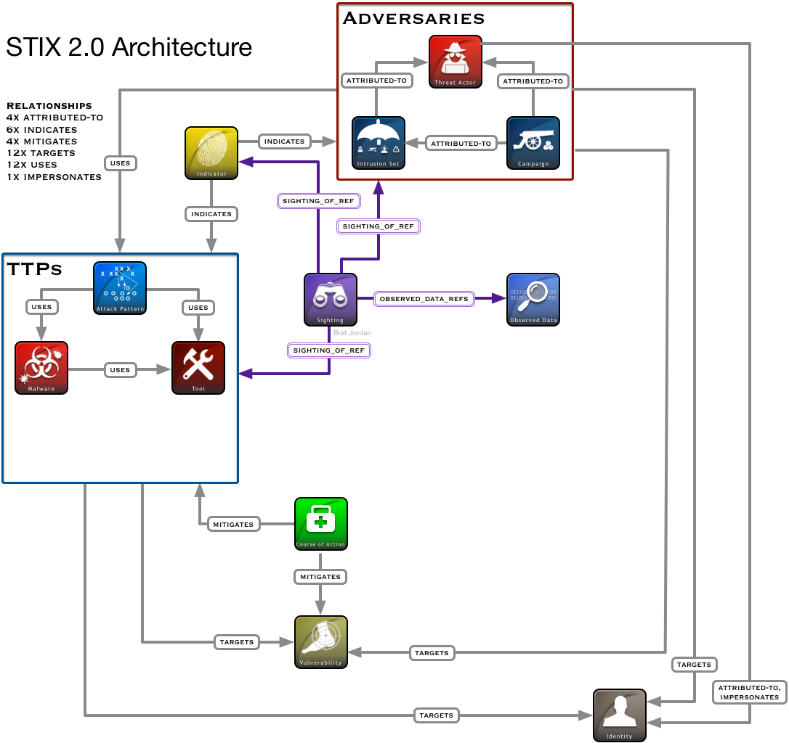
図3. STIXアーキテクチャ
• CybOX (Cyber Observable eXpression)-観察されたセキュリティイベントのインジケータを記述および表示するための共通の構造を提供する標準。 現在、ファイル、ネットワーク接続、HTTPセッション、ネットワークトラフィック、X.509証明書など、70を超えるさまざまな監視対象オブジェクトが既に送信されています。
• TLP (Traffic Light Protocol)-情報を4色で「色付け」できるプロトコルで、脅威に関する受信情報を受信できるユーザーに影響を与えます。
 -情報は配布用ではありません。
-情報は配布用ではありません。
 -組織内でのみ利用可能。
-組織内でのみ利用可能。
 -社会またはコミュニティ内でのみ利用可能。
-社会またはコミュニティ内でのみ利用可能。
 -誰でも利用できます。
-誰でも利用できます。
• IODEF (インシデントオブジェクトの説明と交換形式)(RFC 5070)-連絡先情報、金銭的損害、時間、影響を受けるオペレーティングシステムおよびアプリケーションなどを含む、インシデントの30のクラスおよびサブクラスを超えるXML形式で含まれる標準 IODEFは十分に開発された標準であり、すでに多くの場所で使用されています。 IODEF-SCI(構造化サイバーセキュリティ情報のIODEF)-IODEFに追加データを追加できるIODEFの拡張:攻撃パターン、プラットフォームに関する情報、脆弱性、無力化の指示、危険レベルなど
• OpenIOC ( 侵害の兆候 )- 侵害の兆候を記述するためのオープンスタンダード。 XMLに基づいて構築され、主にノード(ホスト)-ファイル、ドライバー、ディスク、プロセス、レジストリ、システム、ハッシュなど、500を超えるさまざまなインジケーターが含まれています。
• MISP-インジケーターの構造化された説明、脅威に関する情報、 攻撃者、金融詐欺、JSONに基づくオープン形式。
• VERIS (イベント記録とインシデント共有の語彙)-脅威とインシデントを記述するための標準。 VERISスキームは、5つの部分で構成されています。
-インシデント追跡;
-被害者層;
-インシデントの説明。

-発見と応答;
-影響評価。
• TAXII (インテリジェンス情報の信頼された自動交換)-STIXを使用して記述されたHTTPSプロトコルでサイバー脅威情報(CTI)を交換する方法を統一するために使用される標準。
データを交換するにはいくつかの方法があります。
-ハブアンドスポーク。 このアーキテクチャは、1つの組織が情報交換の中心として機能することを想定しています-対話の他のすべての参加者のハブ-スポーク。 スポークは情報をハブと共有し、ハブはこの情報を他のスポークと再共有します。
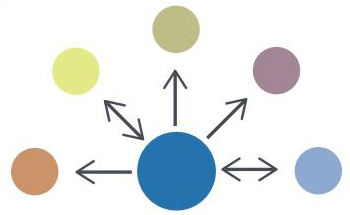
-ソース/サブスクライバー。 このアーキテクチャでは、1つの組織が他のすべての企業の情報源として機能すると想定しています。
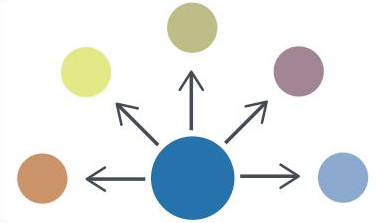
-ピアツーピア。 アーキテクチャは、組織が情報の生産者と消費者の両方として機能できることを前提としています。
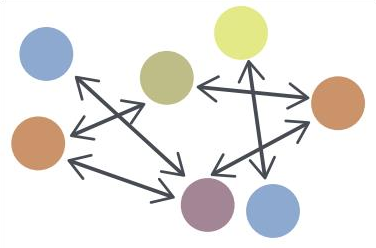
TAXIIには次のサービスが含まれる場合があります。これらのサービスは、一緒に使用することも個別に使用することもできます。
-受信ボックス:受信したコンテンツを受信するためのサービス。
-アンケート:コンテンツをリクエストするためのサービス。
-コレクション管理:データコレクションを操作するためのサービス。
-発見:サポートされている新しいサービスに関する情報。
• VEDEF (脆弱性とエクスプロイトの説明と交換形式 )-脆弱性とエクスプロイトに関する情報を交換するための標準。

図4.脆弱性とエクスプロイトの説明および交換形式
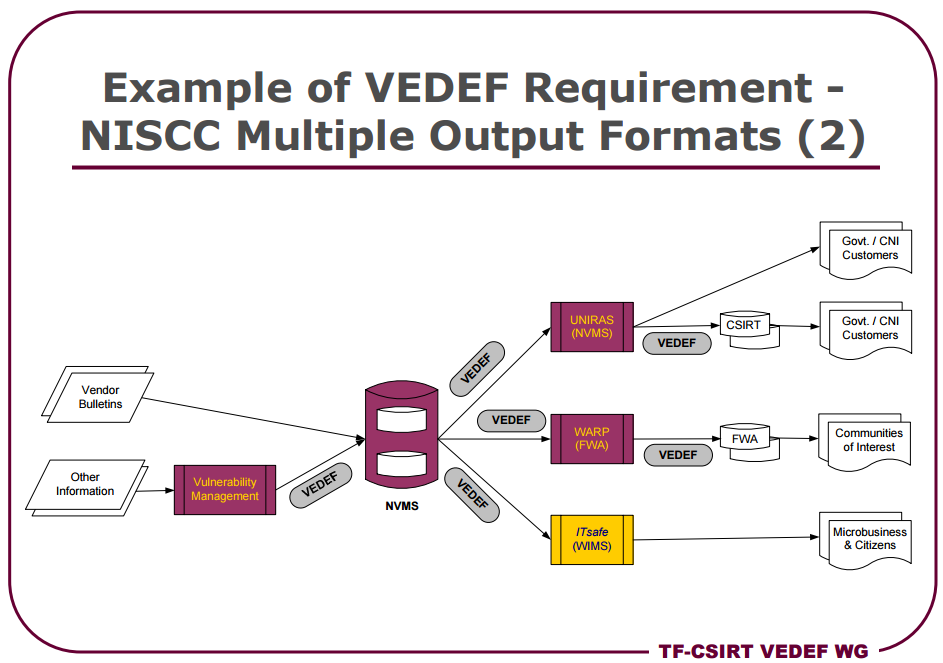
図5.脆弱性とエクスプロイトの説明および交換形式
• CAIF (共通アナウンスメント交換フォーマット)-セキュリティオブジェクトを保存および交換するためのXMLベースの標準。 主なセキュリティ問題を説明するために設計された基本的な要素セットを提供します。 要素のセットを展開できることが重要です。 複数の読者グループの情報をグループ化でき、1つのドキュメントで多言語テキストの説明も提供します。
• MMDEF (マルウェアメタデータ交換フォーマット)-マルウェアの標準メタデータ交換。
• RID (Real-time Inter-network Defense)-HTTP / HTTPSに基づいて構築された、さまざまな情報セキュリティシステムの相互作用を可能にするプロトコル。
脆弱性管理標準
MITER (連邦政府が後援する研究開発センターを運営する非営利組織、FFRDCを運営):
• CVE (Common Vulnerabilities and Exposures)-脆弱性の一般的な命名を定義する標準。
• OVAL (オープンな脆弱性と評価言語)-スキャナーとセキュリティ分析システムの脆弱性を記述するためのオープンな言語。
• CCE (共通構成列挙)-スキャナーおよびセキュリティ分析システムでさらに検証できる構成を記述するための標準。
• CEE (Common Event Expression)-異なる保護手段間のアラームの説明、保存、交換の標準。
• CME (Common Malware Enumeration)-CVEに似ていますが、マルウェアに焦点を当てた標準。
• CWE (Common Weakness Enumeration)-ソフトウェアの弱点の標準化されたセット。
• CPE (Common Platform Enumeration)-ITインフラストラクチャの要素を記述および命名するための標準。
• CAPEC (一般的な攻撃パターンの列挙と分類)-攻撃パターンの標準的な分類。
• CRF (Common Result Format)-テスト結果を記述したり、セキュリティを評価したりするための標準。
• SCAP (セキュリティコンテンツオートメーションプロトコル)-セキュリティデータの管理を自動化するためのプロトコル。 これは、安全性データの表示と交換のための技術仕様を定義する一連のオープンスタンダードです。
• CVSS (Common Vulnerability Scoring System)-脆弱性に優先順位を付けるための標準。
データ処理および分析のためのプラットフォーム
TIプラットフォームは、主にさまざまなソースから侵害の兆候を収集するように設計されています。 また、さらに関連するアクションを分類して実行する必要があります。
プラットフォームの選択は、実装を計画しているTIシステムの規模に直接依存する必要があります。 強力なTIの場合、たとえば、Miter CRIT、Maltego、ThreatConnect、IBM i2などのプラットフォームを検討できます。実装を容易にするために、オープンソースソリューションを使用できます。この場合、規模、機能、サポートよりも価格を優先します。 。 最も人気のあるプラットフォームを検討してください。
Anomali ThreatStream
•さまざまなフィード。
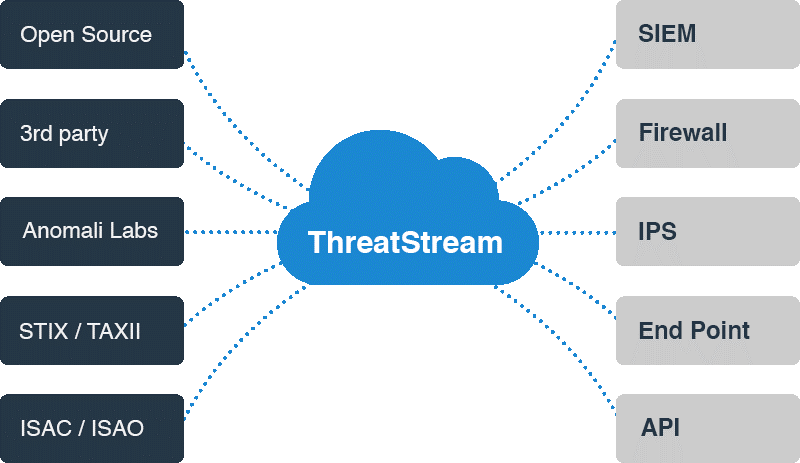
図6.さまざまなフィードを使用する
•多くの情報セキュリティ製品およびSIEMシステムとの統合。

図7.多くの情報セキュリティ製品とSIEMシステムとの統合
•脅威調査に関する詳細情報を提供します。
•APIの可用性。
MANTIS (脅威インテリジェンスソースのモデルベース分析)
OpenIOC、IODEF、CybOX、STIX、TAXII標準を使用して取得した脅威情報をインポートできる脅威管理プラットフォーム。 インポートされたSTIXデータのサンプル:
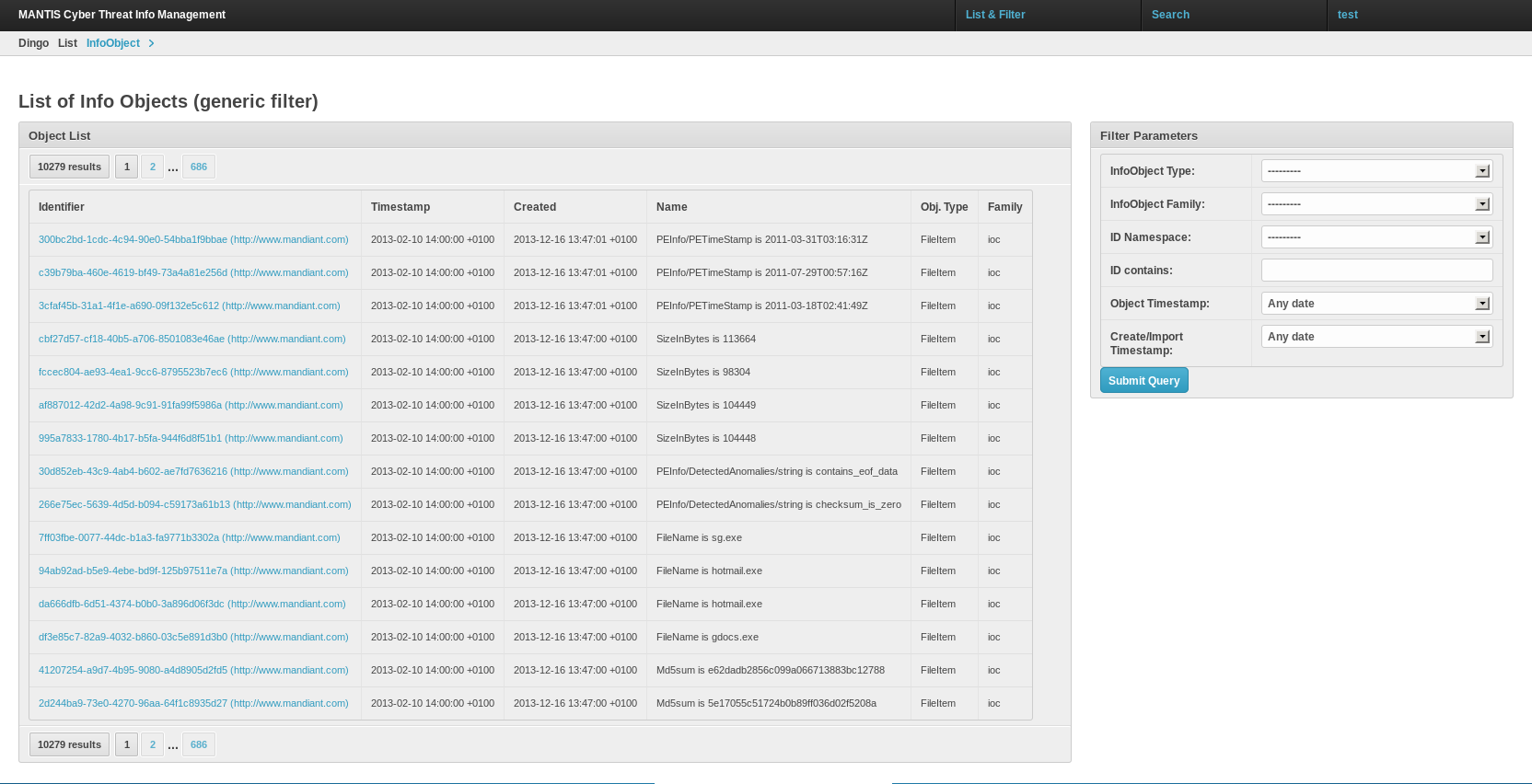
図8.インポートされたSTIXデータのサンプル
図9.インポートされたSTIXデータのサンプル
CIF (Collective Intelligence Framework)
•CIFをサポートするさまざまなソースから脅威情報を収集および統合する機能。
•受信した情報を使用してインシデントを特定します。
•Snort、iptables、およびその他の保護手段のルールを生成することによる脅威の検出と中和。
•ほとんどの場合、悪意のあるアクティビティに関連付けられているIPアドレス、ドメイン名、およびURLで動作します。
•IODEFを情報保存形式として使用します。
•オープンソースプラットフォーム。
•フィードとAPIの可用性。
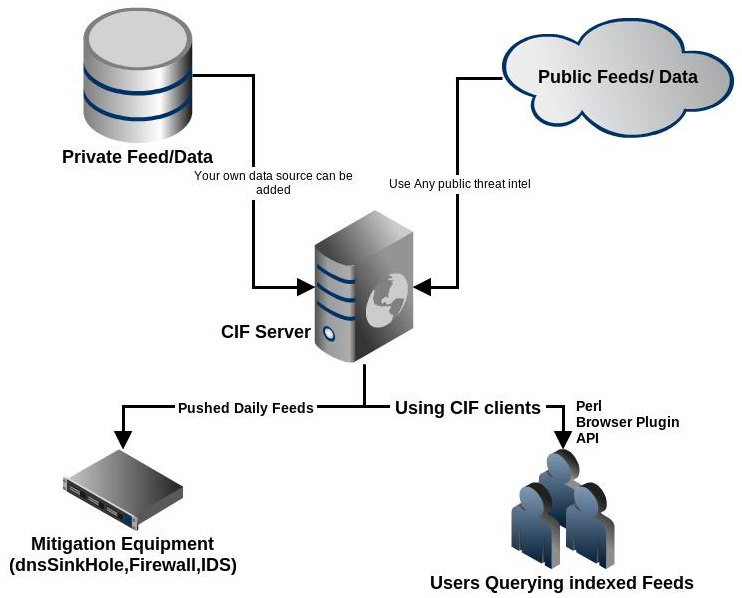
図10.コレクティブインテリジェンスフレームワーク
IBM X-Force Exchange
•1分ごとの動的更新による脅威分析。
•250億を超えるWebページおよび画像から脅威を追跡します。
•96,000を超える脅威に関する情報を含むデータベースによってサポートされています。
•スパムとフィッシングを使用した800万件を超える攻撃の分析。
•860,000の悪意のあるIPアドレスのレピュテーションデータを追跡します。
•IBM Security製品とX-Force Exchange分析を統合します。
•脅威を保護製品に関連付ける機能を実装しました。
•RESTfulを使用して、STIXおよびTAXII標準に基づく他のセキュリティソリューションと統合する機能。
•加入者がX-Force Exchangeからの脅威分析データを企業セキュリティセンター(SOC)や開発環境(DevOps)などの独自の運用に統合する機能。
ミス
•脅威情報を作成、処理、共有、およびコラボレーションするためのオープンソースプラットフォーム。
•柔軟な自動化機能、APIとの連携。
•ネイティブのSTIX形式とSTIX、OpenIOCの両方のサポート、テキストおよびcsvデータのインポート。
•異なるアクター間での脅威情報の自動セキュア交換のサポート。
•IDS、SIEM、Bro、Snort、Suricataなどのルールの自動生成。
おわりに
サイバー犯罪者は長い間、他の誰かの経験を利用して、より高度な新しい攻撃を仕掛けてきました。 情報セキュリティ業界は長い間閉鎖的なものとして発展してきました。 脅威を検出して攻撃を防ぐために役立つ知識と経験を共有した人はいませんでした。
TIは脅威と侵入者に関する大規模な知識ベースであり、攻撃者が危害を加えるために使用する方法とそれらに対処する方法に関する情報を蓄積します。 TIは、脅威のソースと侵害の兆候に関する動的な情報を処理します。
もちろん、TIの助けを借りてもすべてのトラブルを防ぐことはできませんが、サイバー犯罪に対応する最も強力な最新ツールであり、攻撃が行われている方向をすばやく特定し、それらから防御するのに役立ちます。
投稿者Oksana Kotereva、ソリューションプロモーションマネージャー
Informzashchita会社、o.kotereva @ infosec.ru