We’ll leave the topic of efficiency, in terms of circumventing DPI \ whitelist \ blacklist for another case, and just compare the performance of popular lock bypass tools.
Attention: In the article under the spoilers there will be a lot of pictures.
Disclaimer: this article compares the performance of popular VPN / proxy solutions, in conditions close to "ideal". The results obtained and described here do not necessarily coincide with your results in the fields. Because the number in the speed test will often depend not on how productive the bypass tool is, but on how your provider throttles \ QoSit \ blocks it.
Methodology
A cloud provider (DO) bought 3 VPS in different countries of the world. 2 in the Netherlands, 1 in Germany. The most productive IPNs (by the number of cores) were selected from those available for the account on offer for coupon loans.
A private iperf3 server is deployed on the first Dutch server.
On the second Dutch server, various servers for locking bypass tools are deployed in turn.
At the German UPU deployed the image of desktop Linux (xubuntu) with VNC and a virtual desktop. This VPS is a conditional client, and various proxy \ VPN clients are placed / launched on it one by one.
Speed measurements are carried out from three times, we focus on the average, we use 3 tools: in chromium via the web speed test; in chromium via fast.com; from the console via iperf3 through proxy 4 (where you need to put iperf3 traffic into the proxy).
A direct client-server connection iperf3 gives a speed of 2 Gbps, in iperf3, and a little less in a fast / speed test.
An inquisitive reader may ask, “why didn’t you choose speedtest-cli?” And he will be right.
The speed test-test turned out to be an unreliable / inadequate way to measure throughput, for reasons unknown to me. Three consecutive measurements could give three completely different results, or for example show a throughput much higher than the port speed of my IPS. Perhaps the problem is my squint, but it seemed impossible to conduct research with such an instrument.
Regarding the results of the three measurement methods (speed test \ fast \ iperf), I consider the iperf indicators to be the most accurate / reliable \ reliable, and the fast \ speed test - reference. But some bypass tools did not allow to complete 3 measurements through iperf3 and in such cases, you can focus on speedtest / fast.
speed test gives different results 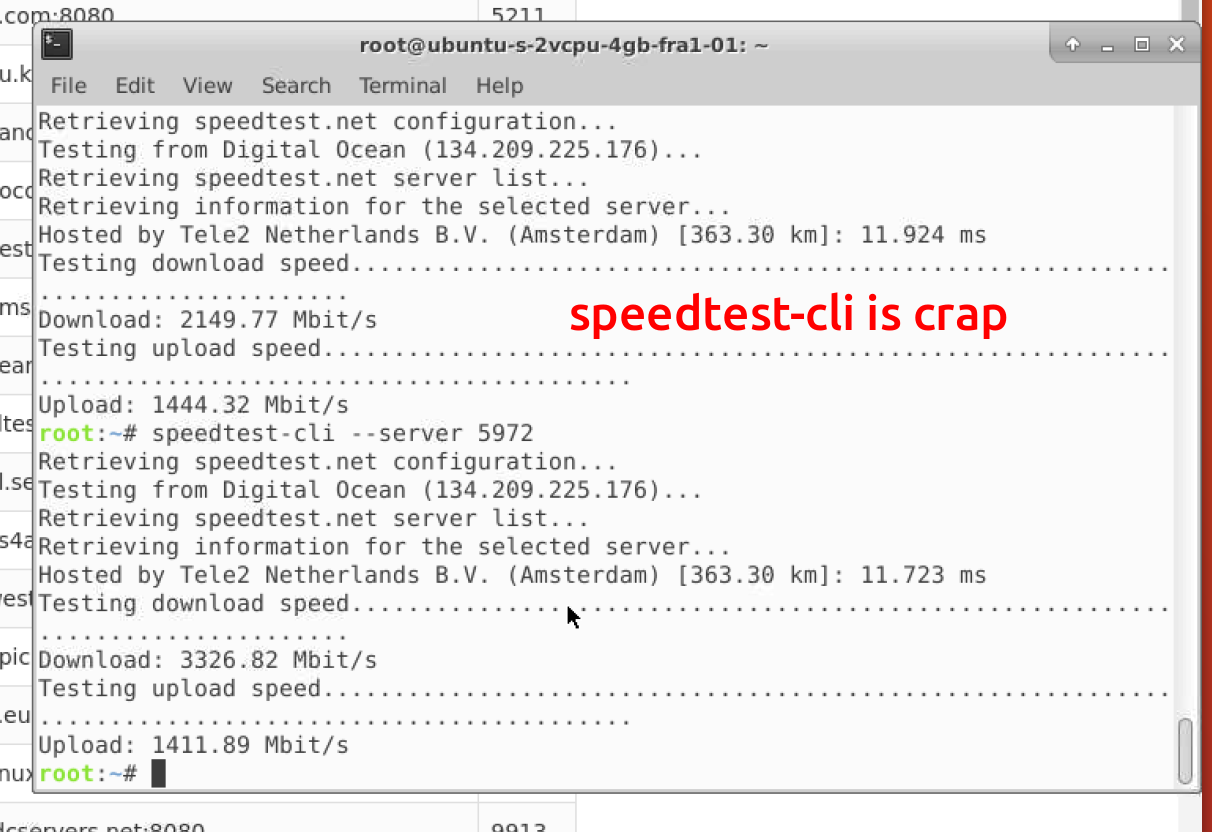

Tools
In total, 24 different workaround tools and / or their combinations were tested, for each of them I will give small explanations and my impressions of working with them. But essentially, the goal was to compare the speeds of shadowsocks (and heaps of different obfuscators to it) openVPN and wireguard.
In this article, I will not discuss in detail the question “how best to hide traffic so that they don’t disconnect”, because bypassing locks is a reactive measure - we adapt to what the censor uses and act on this basis.
results
Strongswan \ ipsec
According to my impressions - it’s very easy to configure, it works quite stably. Of the benefits - it is really cross-platform, without the need to look for clients for each platform.
download - 993 mbit \ s; upload - 770 mbit \ s 

Ssh tunnel
Probably only lazy did not write about using SSH as a tunnel tool. Of the minuses - “crutches” of the solution, i.e. deploying it from a convenient beautiful client on each platform will fail. Of the advantages - good performance, there is no need to install anything at all on the server.
download - 1270 mbit \ s; upload - 1140 mbit \ s 

Openvpn
OpenVPN was tested in 4 operating modes: tcp, tcp + sslh, tcp + stunnel, udp.
OpenVPN servers were configured automatically by installing streisand.
As far as one can judge, at the moment only the mode of operation through the stunnel is resistant to advanced DPI. The reason for the abnormal increase in throughput when wrapping open VPN-tcp in the stunnel is not clear to me, the checks were done in several visits, at different times and different days, the result was the same. Perhaps this is due to the network stack settings that are set when deploying the streysand, write if you have any ideas why.
openvpn \ tcp: download - 760 mbit \ s; upload - 659 mbit \ s 

openvpn \ tcp + sslh: download - 794 mbit \ s; upload - 693 mbit \ s 

openvpn \ tcp + stunnel: download - 619 mbit \ s; upload - 943 mbit \ s 

openvpn \ udp: download - 756 mbit \ s; upload - 580 mbit \ s 

Openconnect
Not the most popular tool for bypassing locks, it is included in the Streisand package, so it was decided to test it.
download - 895 mbit \ s; upload 715 mbit \ s 

Wireguard
A high-tech tool that is popular among Western users, the protocol developers even received some development grants from protection funds. Works as a Linux kernel module, via UDP. Recently, clients have appeared for windows \ ios.
Conceived by the creator as a simple quick way to watch netflix while not in the states.
Hence the pros and cons. Pros - a very fast protocol, relative ease of installation / configuration. Cons - the developer did not initially create it in order to bypass serious locks, and therefore the guard is easily detected by the simplest tools, including wireshark.
wireshard protocol in wireshark 

download - 1681 mbit \ s; upload 1638 mbit \ s 

Interestingly, the wargard protocol is used in the third-party tunsafe client, which when used with the same server, the wargard gives much worse results. It is likely that the wargard windows client will show the same results:
tunsafe \ client: download - 1007 mbit \ s; upload - 1366 mbit \ s 

Outlinevpn
Outline is the implementation of the shadow server and client with a beautiful and convenient gua from google jigsaw. In windows, the offline client is just a set of wrappers for the shadowsocks-local binaries (shadowsocks-libev client) and badvpn (tun2socks binary that directs all machine traffic to the local socks proxy).
Shadoxox was once resistant to the great Chinese firewall, but judging by the latest reviews, now this is no longer the case. Unlike shadowbox, “out of the box” does not support connecting obfuscation through plugins, but this can be done with pens by tinkering with the server and client.
download - 939 mbit \ s; upload - 930 mbit \ s 

Shadowsocks
ShadowsocksR is a fork of the original shadowbox written in python. In fact, it is a shadowbox to which several methods of traffic obfuscation have been firmly pinned.
There are ssR forks on libev and something else. Low bandwidth is probably due to code / language. The original shadowox on python is not much faster.
shadowsocksR: download 582 mbit \ s; upload 541 mbit \ s. 

Shadowsocks
A Chinese blocking bypass tool that randomizes traffic and interferes with automatic analysis in other wonderful ways. Until recently, GFW did not block, they say that it is now blocked only if you enable the UDP relay.
Cross-platform (there are clients for any platform), supports working with PT as torus obfuscators, there are several of their own or adapted obfuscators to it, fast.
There are a bunch of client and server implementations in different languages. In testing, shadowsocks-libev acted as a server, the clients are different. The fastest Linux client turned out to be shadowsocks2 on go, distributed as a default client in streisand, I can not say how much more efficient shadowsocks-windows is. In most of the further tests, shadowsocks2 was used as the client. Screens with testing pure shadowsocks-libev were not made, due to the obvious lag of this implementation.
shadowsocks2: download - 1876 mbit \ s; upload - 1981 mbit \ s. 

shadowsocks-rust: download - 1605 mbit \ s; upload - 1895 mbit \ s. 

Shadowsocks-libev: download - 1584 mbit \ s; upload - 1265 mbit \ s.
Simple-obfs
The plugin to shadowbox, now in the status of “depreciated” but still works (although not always well). It is largely superseded by the v2ray-plugin plugin. It obfuscates traffic either for an HTTP web socket (and allows you to spoof the headers / destination host, pretending that you are not looking at a pornhub, but, for example, the Russian constitution website) or under pseudo-tls (pseudo because it does not use any certificates, the simplest DPI types Detect free nDPI as “tls no cert.” In tls-mode, headers cannot be spoofed anymore).
It’s fast enough, it is installed from the repo with one command, it is configured very simply, it has a built-in function of a feylover (when traffic from a non-simple-obfs client comes to the port that listens to simple obfs, it will forward it to the address where you specify in the settings - such this way you can avoid manually checking the 80th port, for example, simply by redirecting to the website with https, as well as blocking through connection foreys).
shadowsocks \ s-obfs-tls: download - 1618 mbit \ s; upload 1971 mbit \ s. 

shadowsocks \ s-obfs-http: download - 1582 mbit \ s; upload - 1965 mbit \ s. 

Simple obfs in http mode can also work through reverse proxy CDN (for example, cloudflare), so for our provider the traffic will look like http-texttext traffic to cloudflare, this allows us to hide our tunnel a little better, and at the same time split the entry point and traffic output - the provider sees that your traffic is going towards the CDN ip-address, and extremist likes in the pictures are put at this moment from the VPS ip-address. I must say that it is c-obfs through CF that works ambiguously, periodically not opening some https resources for example. So, it was not possible to test the upload using iperf via shadowsocks \ s-obfs + CF, but judging by the results of the speed test, the bandwidth is at the level of shadowsocks \ v2ray-plugin-tls + CF. I do not apply screens with iperf3, because they should not be guided.
download (speedtest) - 887; upload (speedtest) - 1154. 

Download (iperf3) - 1625; upload (iperf3) - N \ A.
v2ray-plugin
V2ray-plugin replaced simple obfs as the main “official” obfuscator for ss lib. Unlike simple obfs, it is not yet in the repositories, and you need to either download a prebuilt binary, or compile it yourself.
It supports 3 modes of operation: default, http-web socket (with support for spoofing the headers of the destination host); tls-web socket (unlike c-obfs, this is full-fledged tls traffic, which is recognized by any web server \ reverse proxy and, for example, allows you to configure tls termination on cloudfleur servers or in nginx); quic - works through udp, but unfortunately the performance of the quick in v2 is very low.
Of the advantages compared to simple obfs: the v2ray plug-in works without problems through CF in the https-web socket mode with any traffic, in tls-mode it represents full-fledged tls-traffic, it requires certificates (for example, from let's encrypt or self-signed).
shadowsocks \ v2ray-plugin-http: download - 1404 mbit \ s; upload 1938 mbit \ s. 

shadowsocks \ v2ray-plugin-tls: download - 1214 mbit \ s; upload 1898 mbit \ s. 

shadowsocks \ v2ray-plugin-quic: download - 183 mbit \ s; upload 384 mbit \ s. 

As I said, v2rei can set headers, and thus it is possible to work with it through reverse proxy \ CDN (cloudfleur for example). On the one hand, this complicates the detection of the tunnel, on the other - it can slightly increase (and sometimes reduce) the lag - it all depends on the location of you and the servers. At the moment, CF is testing work with quic, but so far this mode is not available (at least for free accounts).
shadowsocks \ v2ray-plugin-http + CF: download - 1284 mbit \ s; upload 1785 mbit \ s. 

shadowsocks \ v2ray-plugin-tls + CF: download - 1261 mbit \ s; upload 1881 mbit \ s. 

Cloak
Shred is the result of further development of the GoQuiet obfuscator. Simulates TLS traffic, works accordingly through TCP. At the moment, the author has released a second version of the plugin, cloak-2, which is significantly different from the original cloc.
According to the developer, the first version of the plugin used the tls 1.2 resume session mechanism to spoof the destination address for tls. After the release of the new version (clok-2), all the wiki pages on the github describing this mechanism were deleted; there is no mention of this in the current description of encryption / obfuscation. According to the author’s description, the first version of the shred is not used due to the presence of “critical vulnerabilities in crypto”. At the time of the tests, there was only the first version of the cesspool, its binaries are still on the github, and, among other things, critical vulnerabilities are not very important, because shadousoks encrypts traffic in the same way as without a shred, and crypto shadowsoks does not influence crypto shadoksuksa.
shadowsocks \ cloak: download - 1533; upload - 1970 mbit \ s 

Kcptun
kcptun uses the KCP protocol as a transport and, in some special cases, can achieve increased throughput. Unfortunately (or fortunately) this is largely true for users from China, some of whose mobile operators are heavily trotting TCP and do not touch UDP.
Kcptun is hellishly gluttonous, and easily loads 100 zion kernels 100% when tested by 1 client. In addition, the plugin is “slow”, and also when working through iperf3 it does not finish the tests to the end. We are guided by the speed test in the browser.
shadowsocks \ kcptun: download (speedtest) - 546 mbit \ s; upload (speedtest) 854 mbit \ s. 

Conclusion
Need a simple fast VPN to wrap the traffic of the entire machine? Then your choice is a wargard. Do you want proxies (for selective tunneling or separation of flows \ virtual persons) or is it more important for you to obfuscate traffic from serious blockages? Then look at shadowbox with tls \ http obfuscation. Want to be sure that your Internet will work while the Internet is working at all? Choose traffic proxying through important CDNs, blocking of which will lead to the dump of half of the Internet in the country.
pivot table sorting by download 
