Retrospective
The scale, composition, and structure of cyberthreats for applications are evolving rapidly. For many years, users have accessed web applications over the Internet using popular web browsers. At each point in time, it was necessary to support 2-5 web browsers, and the set of standards for developing and testing web applications was sufficiently limited. For example, almost all databases were built using SQL. Unfortunately, after a short time, hackers learned to use web applications to steal, delete or modify data. They obtained illegal access and abused the capabilities of applications using various tricks, including tricking application users, implementing and remotely executing code. Soon, commercial web application security tools called Web Application Firewalls (WAF) appeared on the market, and society responded by creating an open web application security project, the Open Web Application Security Project (OWASP), to define and maintain development standards and methodologies secure applications.
Basic Application Protection
The OWASP Top 10 list is the starting point for securing applications and contains a list of the most dangerous threats and incorrect settings that can lead to application vulnerabilities, as well as tactics for detecting and repelling attacks. OWASP Top 10 is a recognized benchmark in the cybersecurity application industry worldwide and defines the basic list of capabilities that a web application security system (WAF) should have.
In addition, WAF functionality should take into account other common attacks on web applications, including cross-site request forgery (CSRF), clickjacking, web scraping, and file inclusion (RFI / LFI).
Threats and security challenges of modern applications
To date, not all applications are executed in the network version. There are cloud applications, mobile applications, APIs, and in the latest architectures, even individual software functions. All these types of applications need to be synchronized and controlled, as they create, modify and process our data. With the advent of new technologies and paradigms, new challenges and challenges arise at all stages of the application life cycle. This includes integration of development and operation (DevOps), containers, the Internet of things (IoT), open source tools, APIs, etc.
Distributed application deployment and a variety of technologies creates complex and complex tasks not only for information security specialists, but also for security solution manufacturers who can no longer rely on a unified approach. Application security features should take into account their business specifics to prevent erroneous operations and compromise the quality of services for users.
The ultimate goal of hackers is usually to steal data or disrupt service availability. Attackers also take advantage of technological evolution. First, the development of new technologies creates more potential gaps and vulnerabilities. Secondly, in their arsenal there are more tools and knowledge to circumvent traditional remedies. This greatly increases the so-called “attack surface” and the exposure of organizations to new risks. Security policies must be constantly changing following changes in technology and applications.
Thus, applications should be protected from an ever-growing variety of attack methods and sources, and automatic attacks should be reflected in real time based on informed decisions. As a result, operating costs and manual labor increase amid weakened security positions.
Task number 1: Manage bots
More than 60% of Internet traffic is generated by bots, half of which is referred to as “bad” traffic (according to the Radware security report ). Organizations are investing in increasing network bandwidth, essentially serving the dummy load. An exact distinction between real user traffic and bot traffic, as well as “good” bots (for example, search robots and price comparison services) and “bad” bots can result in significant cost savings and an increase in the quality of services for users.
Bots are not going to facilitate this task, and they can imitate the behavior of real users, bypass CAPTCHA and other obstacles. Moreover, in the case of attacks using dynamic IP addresses, protection based on filtering by IP address becomes ineffective. Often, open source development tools (for example, Phantom JS) that can run client-side JavaScript are used to launch brute-force attacks, credential stuffing attacks, DDoS attacks, and automated bot attacks .
Effective bot traffic management requires a unique identification of its source (like a fingerprint). Since a lot of entries occur in the case of a bot attack, its fingerprint allows you to identify suspicious activity and assign points, based on which the application protection system makes an informed decision - block / allow - with a minimum false positive rate.

Task # 2: API Protection
Many applications collect information and data from services with which they interact through the API. When transferring confidential data through the API, more than 50% of organizations do not check or protect APIs to detect cyber attacks.
API Usage Examples:
- IoT Integration
- Machine interaction
- Serverless environments
- Mobile applications
- Event driven applications
API vulnerabilities are similar to application vulnerabilities and include injections, protocol attacks, parameter manipulations, redirects and bot attacks. Dedicated API gateways guarantee the compatibility of application services that communicate through the API. However, they do not provide end-to-end security for the application, as WAF can be used with the necessary security tools, such as parsing HTTP headers, Layer 7 access control lists (ACLs), parsing and checking JSON / XML payloads, and protecting against all vulnerabilities from OWASP Top 10 list. This is achieved by inspecting key API values using positive and negative models.
Task 3: Denial of Service
The old denial of service (DoS) attack vector continues to prove its effectiveness in attacks on applications. Attackers have a number of successful techniques for disrupting application services, including HTTP or HTTPS floods, low-and-slow attacks (for example, SlowLoris, LOIC, Torshammer), attacks using dynamic IP addresses, buffer overflows, brute force -attacks, and many others. With the development of the Internet of Things and the subsequent emergence of IoT botnets, attacks on applications have become the main focus of DDoS attacks. Most connection-tracking WAFs can only withstand a limited amount of load. However, they can inspect HTTP / S traffic flows and remove attack traffic and malicious connections. Once an attack is detected, it makes no sense to re-pass this traffic. Since WAF's bandwidth to repel attacks is limited, an additional solution is needed on the perimeter of the network to automatically block the next “bad” packets. For this security scenario, both solutions must be able to interact with each other to exchange information about attacks.
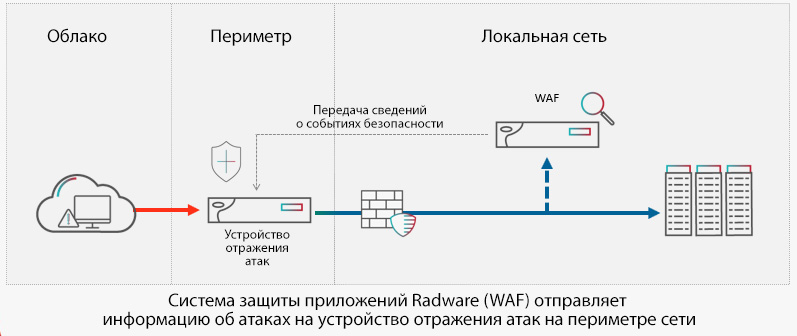
Figure 1. Organization of comprehensive network and application protection using Radware solutions as an example.
Task number 4: Continuous protection
Applications are often subject to change. Development and implementation methodologies, such as continuous updates, mean that modifications are made without human involvement and control. In such dynamic conditions, it is difficult to maintain adequately working security policies without a high number of false positives. Mobile applications are updated much more often than web applications. Third-party applications may change without your knowledge. Some organizations are seeking greater control and visualization to stay abreast of potential risks. However, this is not always achievable, and reliable application protection should use machine learning capabilities to account for and visually present available resources, analyze potential threats, create and optimize security policies in case of application modifications.
conclusions
As applications play an increasingly important role in everyday life, they become a primary target for hackers. The potential jackpot for cybercriminals and the potential losses for the business are huge. The complexity of the task of ensuring application security cannot be exaggerated, given the number and variations of applications and threats.
Fortunately, we are at a point in time when artificial intelligence can come to our aid. Machine learning-based algorithms provide real-time adaptive protection against the most advanced cyber threats aimed at applications. They also automatically update security policies to protect web, mobile, and cloud applications - as well as APIs - without false positives.
It is difficult to accurately predict what the next generation of cyberthreats will be for applications (possibly also based on machine learning). But organizations can definitely take steps to protect customer data, intellectual property and guarantee the availability of services with great benefits for the business.
Effective approaches and methods to ensure application security, the main types and vectors of attacks, risk zones and gaps in cyber security of web applications, as well as international experience and best practices are presented in the Radware study and report “ Web Application Security in a Digitally Connected World ”.