Bank fraud has become part of everyday life. Methods of attackers are becoming more sophisticated: often the victim does not immediately understand what happened.

We have collected several stories told by the victims and are freely available, and examined them in terms of the actions of attackers. Webself articles about how he drove scammers by the nose were also useful to us. Details under the cut.
What's happening?
Many stories are similar to one another: the victim is called from the bank number (or a very similar one) and asked to confirm the transaction, which, of course, no one committed. If the victim has questions, fraudsters skillfully rub into trust, giving details about finances that in an ideal world can only be known to the bank and the victim. Money from the victim’s accounts goes to the account of a third party, from where they will be withdrawn later. Attackers always have fallback options in case the victim encounters difficulties or asks too many questions.
We will not discuss who exactly deals with such matters, and leave aside the question of ethics. We are interested in the technical side of the actions of fraudsters, as well as ways to protect against them.
The information is provided for informational purposes only. The author is not responsible for any harm that may be caused after reading this article.
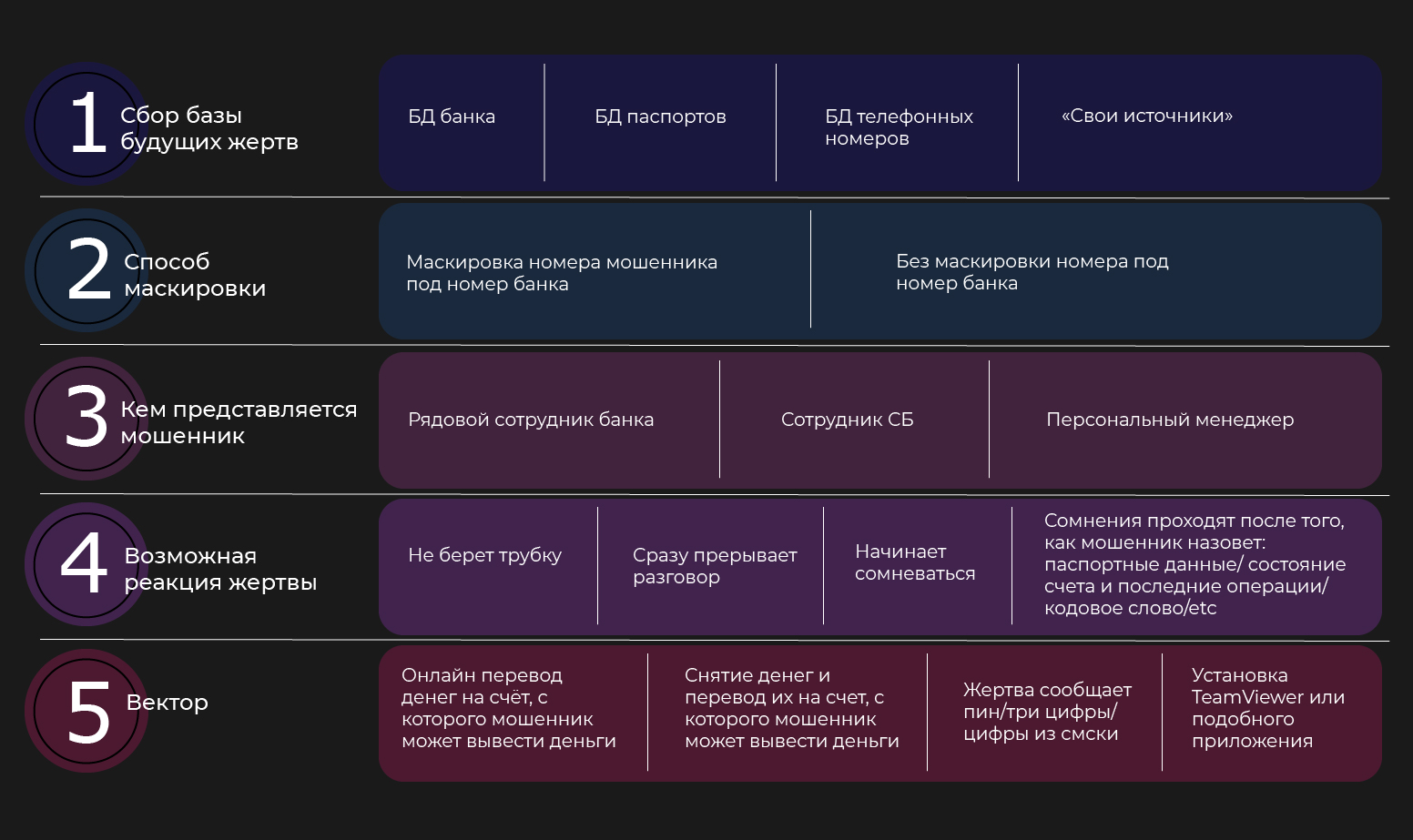
Where do the attackers get the data from potential victims? After all, this is not only a full name and a phone number, but also a code word, state of accounts and deposits, recent transactions. There are shadow platforms on the darknet that specialize in receiving and selling such data. This has been written in detail before us.
Having received the data of potential victims, scammers must create a legitimate cover. Here they have at least two options: choose a number very similar to a bank number, or replace your number with a bank number.
The second method is much more dangerous, since the victim, by googling, will make sure that the number belongs to the bank and continue the conversation.
Obviously, the substitution of numbers is a shadow service, which is provided by dozens of services. As a rule, this is done using SIP telephony, a subspecies of IP telephony. The servers, of course, are located outside our country, so law enforcement agencies will not investigate their activities.

Having reached the victim, the fraudster begins a social engineering session, the purpose of which is to get the maximum possible amount of money. If you omit the nuances, then you can divide all the cases into several groups:
- an attacker manages the victim’s actions, forcing her to go to an ATM, withdraw money and transfer it to a “safe” account belonging to a third party who, most likely, does not suspect anything;
- an attacker pulls out as much information as possible from the victim with the help of which you can access your personal account (numbers on the back of the card, codes from SMS, etc.);
- an attacker, in order to facilitate his task, offers the victim to install TeamViewer or its analogue under the guise of helping a client. Other actions from the victim may not be required - everything will happen before her eyes, but without her participation.
Typically, scammers act on a script that branches depending on what the victim says. This indicates the level of preparation of scammers and their determination :)
We tried to systematize the most common actions of scammers. The diagram below shows the results.
What to do?
Now we will talk about several ways to protect. They may seem obvious to some, but the continued success of fraudsters is a good reason to repeat what has been said many times.
- If you received a call from a number similar to a bank or identical to it, or the number is “left”, but the caller stubbornly appears to be a bank employee, you should refuse to talk. Then you can call by yourself the numbers indicated on the card of your bank and find out if they called you from the bank, whether the funds were transferred from your accounts, etc. Or you can go to the online bank to see the transactions on the card and state of accounts and deposits. In extreme cases, go to the bank branch, if he has one.
PS It is interesting that in situations where fraudsters replace their number with a bank number using SIP-telephony, a call to an incoming number (bank number) in most cases will lead you to a conversation with a bank employee. This is possible because the substitution of the number works only in one direction.
- There are many applications that determine whether an incoming call is a source of spam or divorce. But it may also be that the number you are being called from is being used recently, so it will not be defined as undesirable.
- You always need to remember that bank employees do not offer to make any money transactions, such as transfers to the bank’s “employees” accounts, withdrawing money from ATMs and then depositing them into someone else’s account, installing additional programs and applications on a smartphone. Those who offer this are 100% scammers. Bank employees will not be asked to install an application like TeamViewer . They don’t need it.
- Much has been said about SMS from banks not only by the banks themselves, but also by everyone who is not lazy. We will also say: don’t tell anyone the sequence of numbers from SMS, even the “robots” that scammers offer to talk to, motivating this with the fact that the robot is not a person, which means “no one”.
- Call centers of different banks are in no way connected with each other. If you were presented with Bank X, and you said that you are using Bank U, and they want to transfer you to the bank’s line right there, beware. Better immediately hang up.
That's all for now. Be careful.