Network infrastructure analysis plays a large role in the study of malicious campaigns. Information about which IP addresses corresponded to a domain name at various intervals allows you to identify new attacker servers. Solving the opposite problem (a retrospective of domains that resolved to a given IP address) gives new domains for which you can repeat the search procedure, spinning the chain further and further. All the information obtained helps to get an idea about the geography of the nodes, highlight the “favorite” hosters and registrars, and note the characteristic values of the fields that the attacker indicates when he registers the next domain.
At first glance, useless meta-information can come in handy after a few days, weeks, and even months. Indeed, in the course of malware analysis, sooner or later the question arises of attribution, belonging of an instrument to a particular criminal group: and here all indirect signs come to the aid, including data on network indicators.
In this article, we will consider the most characteristic features of the TA505 network infrastructure and show intersections with another hacker group, Buhtrap.
Domain name registrars
In total, we analyzed 372 domains of the group and identified 22 organizations providing domain name acquisition services. The following resources were of greatest interest to attackers:
- WhoisGuard, Inc. - 28 domain names,
- Eranet International Limited - 26 domain names.
The Panamanian organization WhoisGuard provides an opportunity to hide their registration data from public access. This is by no means the first case of using the services of this company to anonymize and complicate investigations.
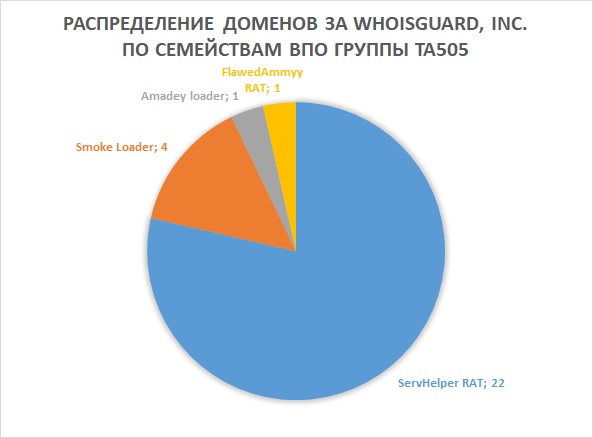
Distribution of TA505 domains registered using the WhoisGuard service by the malware families of the group
In addition, we found the use of other similar services - PROTECTSERVICE, LTD, Whois Privacy Protection Foundation, Domains by Proxy, LLC - but to a lesser extent.
Eranet International Limited is one of Hong Kong's largest registrars. It is worth noting that when registering most of the domains with this provider, the attackers used dynamic DNS - as a result, the IP addresses to which the domain name was resolved changed very often, making it difficult to find further traces.
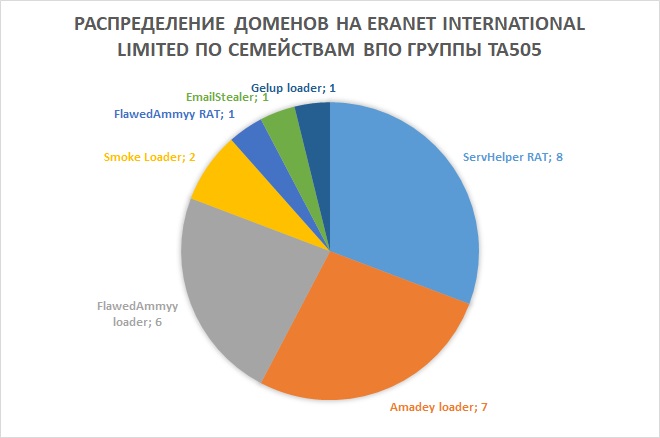
The distribution of TA505 domains registered using the Eranet International Limited service by the malware families of the group
Domain Name Registrants
During the study of the WHOIS information of domain names, in some cases it was possible to obtain unique values for some fields.
TA505 Group Domain Name WHOIS Information:

Of course, not all fields can be blindly trusted. However, the values of some of them can provide interesting information. For example, by email at ctouma2@gmail.com, you can go to the list of other domains that are registered to the same value. Another mailbox 0141.koppe.pan@gmail.com leads to many different resources: an account on Github , Steam , the Japanese hacker forum Qiita with a link to a malicious domain in the profile, YouTube channel , Skype account (live: 141.koppe. pan), etc.
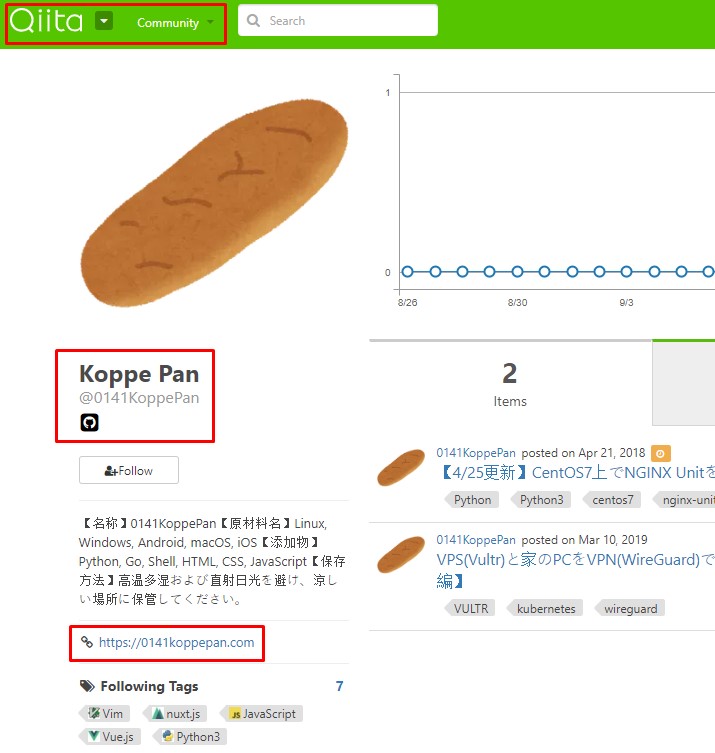
Suspicious domain registrant page on Qiita hacker forum
We will leave in-depth analysis of WHOIS data beyond the scope of this article. We only note that attackers often resort to hacked legitimate resources to host malware in the first stage. Below are examples of such domains:
- greenthumbsup [.] jp
- fakers.co [.] jp
- nanepashemet [.] com
- nagomi-753 [.] jp
- iluj [.] in
Autonomous Systems (AS)
For the sake of completeness, we give the top of Autonomous Systems (AS), which own the IP addresses of the management servers. Of course, a single autonomous system owns a lot of hosts: both legitimate and not, including various malware families of very different origins. The statistics below should be understood as a characteristic of the attacker's preferences. Together with other facts, it can be material for attribution.
Autonomous systems often used by the TA505 group:

Intersection with Buhtrap Group
On July 11, 2019, our ESET colleagues published an article about a recent attack by the Buhtrap group using a zero-day vulnerability in the Win32k Windows component. One of the modules described was the so-called grabber module for stealing user passwords from email clients, browsers, etc. After some time, we found a module similar to that described (MD5: c6e9d7280f77977a6968722e8124f51c) with the same managing server in the body (redmond.corp- microsoft [.] com).
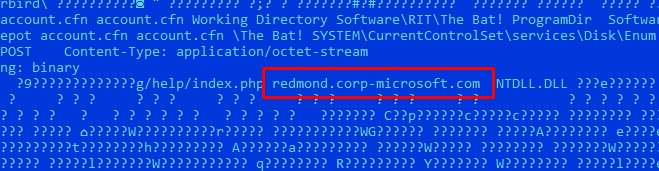
Managing server in the Buhtrap grabber module
According to the PaSiveTotal resource, this host resolves to the IP address 95 [.] 179.159.170 from June 6, 2019.
A little earlier, on July 2, 2019, our colleagues from Proofpoint announced new TA505 tools, one of which is called Andromut (also known as Gelup) and is the FlawedAmmyy RAT bootloader. One of the bootloader variations (MD5: 0cbeb424d96e5c268ec2525d603f64eb) that we met uses the compatexchange-cloudapp [.] Net domain as the management server.
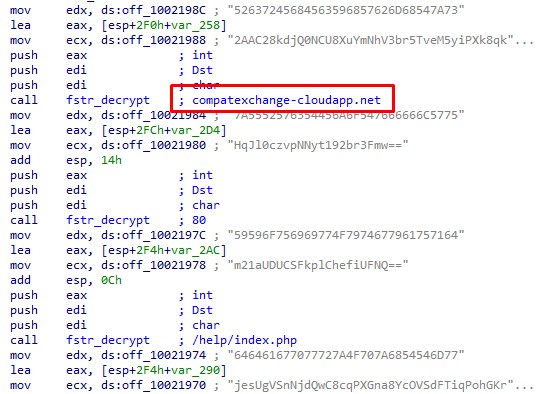
Gelup management server from TA505 after decryption
According to the PaSiveTotal resource, this host resolves to the IP address 95 [.] 179.159.170 from June 8, 2019.
Both domains are registered with the same registrar (Tucows Domains Inc.) with a difference of two days, they are resolved to the same IP address. Considering the fact that both groups carried out regular attacks during June, we conclude that Buhtrap and TA505 use a common host as a management server.
We add that the domain compatexchange-cloudapp [.] Net was used not only in the bootloader above, but also in older versions of Buhtrap components.
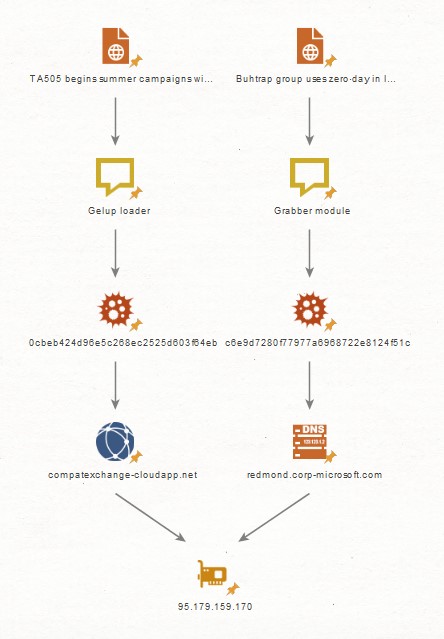
The first intersection of TA505 and Buhtrap in infrastructure
After some time, we met another similar intersection: this time, the domains of another grabber from Buhtrap and the Smoke Loader from TA505 met in the same way: domain test-service012505 [.] Com Smoke Loader (MD5: 5fc6f24d43bc7ca45a81d159291955d1) and domain secure-telemetry [. ] net grabber (MD5: 79d1a836423c7ee57b6127cf2930a9d9) from July 17 and 16, 2019, respectively, are resolved to the IP address 194 [.] 4.56.252.
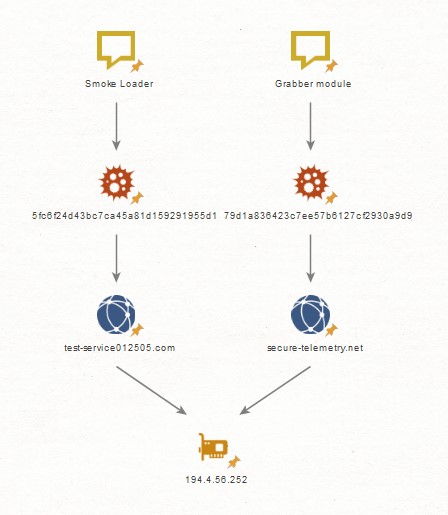
The second intersection of TA505 and Buhtrap in infrastructure
conclusions
We got acquainted with the features of the network infrastructure of the TA505 group. We examined the characteristic features of domain name registrars and hosters for management servers. We noted the curious features of customer information specified during domain registration; this may serve as a starting point for more detailed research. We examined the infrastructure intersections between the TA505 and Buhtrap groups. The situation with shared servers can be explained in different ways: groups can share servers by agreement; groups may have a single managing entity coordinating their actions; both groups can rent servers from third parties (and those, in turn, save on resources). We will continue to monitor the activity of both groups and will look for new information about their possible connections and joint activities.
Authors : Alexey Vishnyakov and Maxim Anfinogenov, Positive Technologies
IOCs
TA505 C2:
0141koppepan [.] Com
bigpresense [.] top
elast [.] pw
fakers.co [.] jp
greenthumbsup [.] jp
iluj [.] in
kentona [.] su
koppepan [.] app
makosoft [.] hu
microsoftsyncservice [.] biz
nagomi-753 [.] jp
nanepashemet [.] com
newfolder2-service [.] space
office365onlinehome [.] com
solsin [.] top
test-service012505 [.] com
windows-several-update [.] com
windows-update-02-en [.] com
c6e9d7280f77977a6968722e8124f51c - Buhtrap grabber module
redmond.corp-microsoft [.] com - Grabber C&C
0cbeb424d96e5c268ec2525d603f64eb - Gelup downloader from TA505
compatexchange-cloudapp [.] net - Gelup C&C
95.179.159 [.] 170 - TA505 and Buhtrap Shared Host
79d1a836423c7ee57b6127cf2930a9d9 - Buhtrap grabber module
secure-telemetry [.] net - Grabber C&C
5fc6f24d43bc7ca45a81d159291955d1 - Smoke Loader downloader from TA505
test-service012505 [.] com - Smoke Loader C&C
194 [.] 4.56.252 - TA505 and Buhtrap Shared Host
0141koppepan [.] Com
bigpresense [.] top
elast [.] pw
fakers.co [.] jp
greenthumbsup [.] jp
iluj [.] in
kentona [.] su
koppepan [.] app
makosoft [.] hu
microsoftsyncservice [.] biz
nagomi-753 [.] jp
nanepashemet [.] com
newfolder2-service [.] space
office365onlinehome [.] com
solsin [.] top
test-service012505 [.] com
windows-several-update [.] com
windows-update-02-en [.] com
c6e9d7280f77977a6968722e8124f51c - Buhtrap grabber module
redmond.corp-microsoft [.] com - Grabber C&C
0cbeb424d96e5c268ec2525d603f64eb - Gelup downloader from TA505
compatexchange-cloudapp [.] net - Gelup C&C
95.179.159 [.] 170 - TA505 and Buhtrap Shared Host
79d1a836423c7ee57b6127cf2930a9d9 - Buhtrap grabber module
secure-telemetry [.] net - Grabber C&C
5fc6f24d43bc7ca45a81d159291955d1 - Smoke Loader downloader from TA505
test-service012505 [.] com - Smoke Loader C&C
194 [.] 4.56.252 - TA505 and Buhtrap Shared Host