DPI Quick Start Guide: Usage Scenarios
In our today's article, we will talk about how DPI systems help Internet providers save, protect their customer data, and talk about connection methods.

/ Unsplash / israel palacio
Prioritize traffic. A few years ago, Netflix traffic on the network of an Australian provider amounted to a quarter of the total. This has affected the quality of the work of the remaining Internet services from the point of view of users. DPI solutions help circumvent such problems and optimize network congestion by prioritizing “gluttonous” protocols.
A similar approach allows you to work with bursts of traffic. Usually they are predictable and occur on certain days and hours. To cope with peak loads, operators pay an extra lane. However, expanding the bandwidth can be disadvantageous because the activity window is small and unstable. Prioritization helps the provider save and not lose customers as a user experience. For example, to optimize traffic, our system is used by the telecom operator from Latin America, Yota de Nicaragua. The priority ladder is structured as follows: service traffic, DNS, MPEG4 and HTTP.
Caching For video content on YouTube, OS updates, as well as browsers and antiviruses, you can use the DPI-based cache server. It distributes this data locally. A similar task is performed by Google Global Cache. GGC servers are located in the networks of local providers, closer to users. These devices temporarily store the most requested content. This approach speeds up access to services like YouTube, Google Play, Google Maps and saves bandwidth for both corporations and carriers.
Notification of subscribers. And the conclusion of notifications like the timing of technical work or emergency. So the government is discussing the relevant decree . Providers may be required to inform subscribers about technological disasters, fires, hurricanes and so on.
Network protection. To combat DDoS, the operator must find out: from where the network is attacking, who is attacking it and which of the clients came under attack. DPI helps answer these questions. For example, in SCAT DPI from VAS Experts there is a mini-firewall for these tasks. The system detects anomalies in the network, notifies clients of suspicious activity and blocks access to intruders. Additionally, DPI works in conjunction with anti-virus, anti-spam solutions, as well as DLP systems .
As a result, DPI solves several problems at once: from optimization of communication channels to protection against malicious attacks. Next, let's talk a little about how these systems integrate into the network.
Most often they use two DPI connection schemes in the network of the Internet provider. The first is a “break” setting, and the second is traffic mirroring.
Installation "in the gap." DPI is installed behind the border router, as if "breaking" the external channel of the provider. For example, according to this model , DPI is deployed at Yota de Nicaragua.
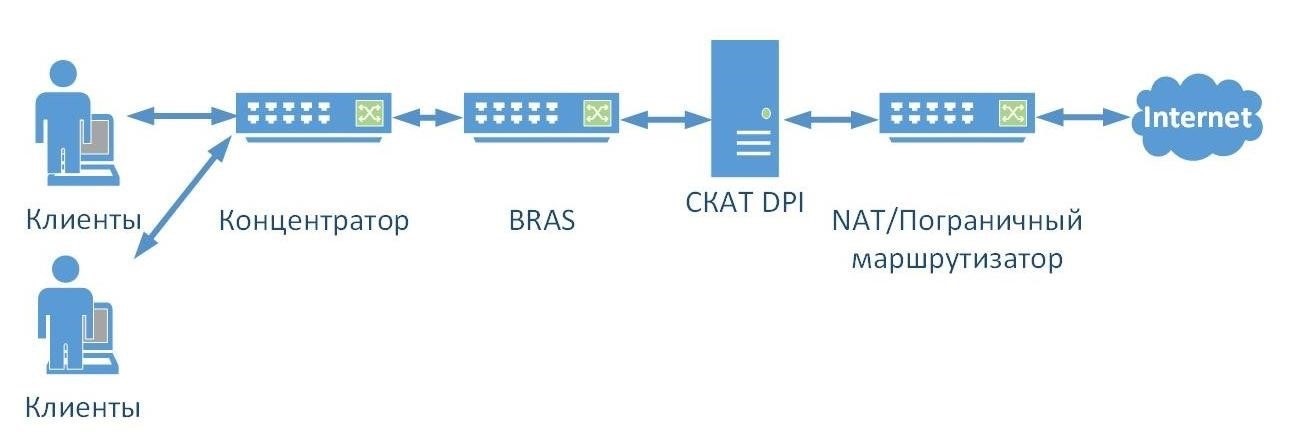
But such a scheme implies the emergence of a single point of failure. A malfunction in the DPI will disable the entire network. Therefore, providers often install a backup system that takes the load in the event of an emergency.
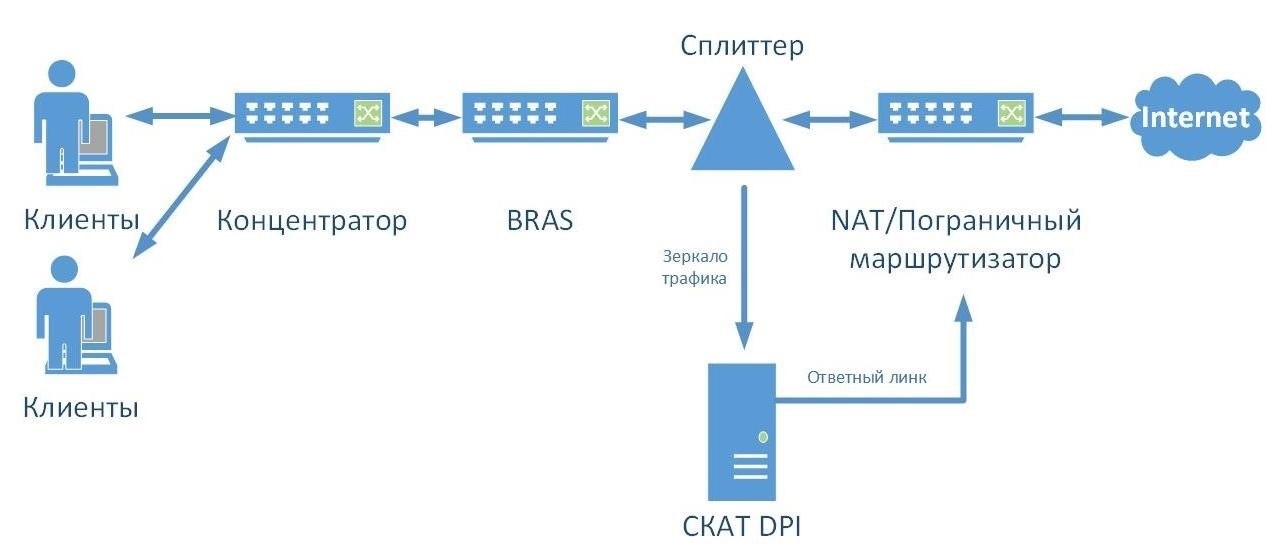
Traffic mirroring. Traffic is routed through SPAN ports or optical splitters. So, there is no need to modify the network architecture and use bypass cards. This scheme allows you to connect cache servers and process SORM requests. But the full functionality of the DPI system will not be available.
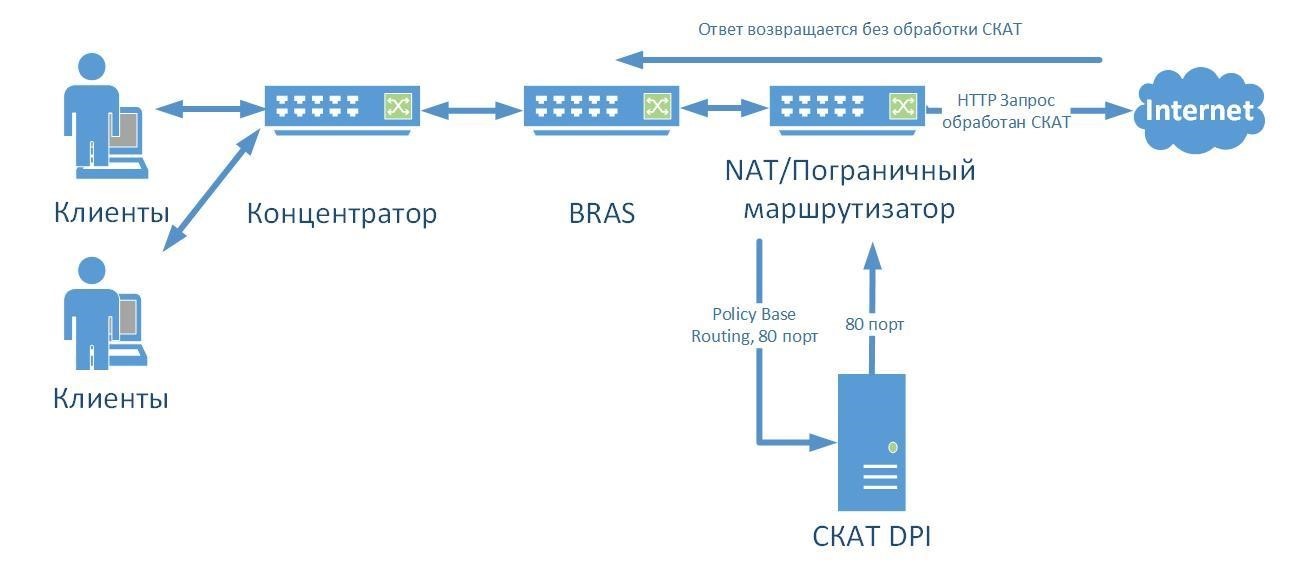
Alternative connection scheme. If you need to handle only web traffic, you can resort to an asymmetric scheme. In this case, the so-called policy-based routing (PBR) is involved. HTTP traffic occupies a small part of the bandwidth, so this DPI-system will work even on relatively weak equipment. But in this case, you can not use analytics.
As a result, the choice of the DPI connection model depends on the required fault tolerance and functionality.

/ Unsplash / israel palacio
Use cases
Prioritize traffic. A few years ago, Netflix traffic on the network of an Australian provider amounted to a quarter of the total. This has affected the quality of the work of the remaining Internet services from the point of view of users. DPI solutions help circumvent such problems and optimize network congestion by prioritizing “gluttonous” protocols.
A similar approach allows you to work with bursts of traffic. Usually they are predictable and occur on certain days and hours. To cope with peak loads, operators pay an extra lane. However, expanding the bandwidth can be disadvantageous because the activity window is small and unstable. Prioritization helps the provider save and not lose customers as a user experience. For example, to optimize traffic, our system is used by the telecom operator from Latin America, Yota de Nicaragua. The priority ladder is structured as follows: service traffic, DNS, MPEG4 and HTTP.
Caching For video content on YouTube, OS updates, as well as browsers and antiviruses, you can use the DPI-based cache server. It distributes this data locally. A similar task is performed by Google Global Cache. GGC servers are located in the networks of local providers, closer to users. These devices temporarily store the most requested content. This approach speeds up access to services like YouTube, Google Play, Google Maps and saves bandwidth for both corporations and carriers.
A couple of fresh materials from our blog on Habré:
Notification of subscribers. And the conclusion of notifications like the timing of technical work or emergency. So the government is discussing the relevant decree . Providers may be required to inform subscribers about technological disasters, fires, hurricanes and so on.
Network protection. To combat DDoS, the operator must find out: from where the network is attacking, who is attacking it and which of the clients came under attack. DPI helps answer these questions. For example, in SCAT DPI from VAS Experts there is a mini-firewall for these tasks. The system detects anomalies in the network, notifies clients of suspicious activity and blocks access to intruders. Additionally, DPI works in conjunction with anti-virus, anti-spam solutions, as well as DLP systems .
As a result, DPI solves several problems at once: from optimization of communication channels to protection against malicious attacks. Next, let's talk a little about how these systems integrate into the network.
DPI connectivity options
Most often they use two DPI connection schemes in the network of the Internet provider. The first is a “break” setting, and the second is traffic mirroring.
Installation "in the gap." DPI is installed behind the border router, as if "breaking" the external channel of the provider. For example, according to this model , DPI is deployed at Yota de Nicaragua.

But such a scheme implies the emergence of a single point of failure. A malfunction in the DPI will disable the entire network. Therefore, providers often install a backup system that takes the load in the event of an emergency.
Traffic mirroring. Traffic is routed through SPAN ports or optical splitters. So, there is no need to modify the network architecture and use bypass cards. This scheme allows you to connect cache servers and process SORM requests. But the full functionality of the DPI system will not be available.

Alternative connection scheme. If you need to handle only web traffic, you can resort to an asymmetric scheme. In this case, the so-called policy-based routing (PBR) is involved. HTTP traffic occupies a small part of the bandwidth, so this DPI-system will work even on relatively weak equipment. But in this case, you can not use analytics.

As a result, the choice of the DPI connection model depends on the required fault tolerance and functionality.
What we write about in the VAS Experts corporate blog:
All Articles