Group-IB and Belkasoft Joint Courses: What We Teach and Who to Come

Algorithms and tactics for responding to information security incidents, trends in current cyberattacks, approaches to investigating data leaks in companies, researching browsers and mobile devices, analyzing encrypted files, extracting geolocation data and analyzing large volumes of data - all these and other topics can be explored on new topics Joint Group-IB and Belkasoft courses. In August, we announced the first Belkasoft Digital Forensics course, which starts on September 9, and after receiving a large number of questions, we decided to talk in more detail about what students will learn, what knowledge, competencies and bonuses (!) Will be received by those who reach the end . First things first.
Two All In One
The idea of conducting joint training courses appeared after students of Group-IB courses began to ask about a tool that would help them in the study of compromised computer systems and networks, and combined the functionality of various free utilities that we recommend to use when responding to incidents .
In our opinion, such a tool could be the Belkasoft Evidence Center (we already talked about it in an article by Igor Mikhailov, “Key to the Start: the best software and hardware for computer forensics”). Therefore, we, together with Belkasoft, developed two training courses: Belkasoft Digital Forensics and Belkasoft Incident Response Examination .
IMPORTANT: courses are consistent and interconnected! Belkasoft Digital Forensics is dedicated to Belkasoft Evidence Center, and Belkasoft Incident Response Examination is investigating incidents using Belkasoft products. That is, before taking the Belkasoft Incident Response Examination course, we strongly recommend that you take the Belkasoft Digital Forensics course. If you start right away with a course on incident investigation, the listener may have unfortunate knowledge gaps on using the Belkasoft Evidence Center, finding and researching forensic artifacts. This can lead to the fact that during the training on the Belkasoft Incident Response Examination course, the student will either not have time to master the material or will inhibit the rest of the group in acquiring new knowledge, since the training time will be spent by the trainer on explaining the material from the Belkasoft Digital Forensics course.
Computer Forensics with Belkasoft Evidence Center
The purpose of the Belkasoft Digital Forensics course is to familiarize students with the Belkasoft Evidence Center program, teach them how to use this program to collect evidence from various sources (cloud storage, random access memory (RAM), mobile devices, storage media (hard drives, flash drives, etc.) etc.), to master basic forensic techniques and techniques, forensic research methods for Windows artifacts, mobile devices, memory dumps.You will also learn to identify and document artifacts of browsers and instant exchange programs messages, create forensic copies of data from various sources, retrieve geolocation data and search for text sequences (keyword search), use hashes when conducting research, analyze the Windows registry, master the skills of researching unknown SQLite databases, the basics of researching graphical and video files and analytical techniques used during investigations.
The course will be useful to experts with specialization in the field of computer-technical expertise (computer expertise); technicians who determine the reasons for a successful invasion analyze the chain of events and the consequences of cyber attacks; technical specialists who identify and document the theft (leakage) of data by an insider (internal violator); e-Discovery specialists; SOC and CERT / CSIRT employees; information security officers; computer forensics enthusiasts.
Course Plan:
- Belkasoft Evidence Center (BEC): first steps
- Creating and processing cases in BEC
- Forensic Evidence Collection with BEC

- Using filters
- Reporting
- Researching Instant Messaging Programs
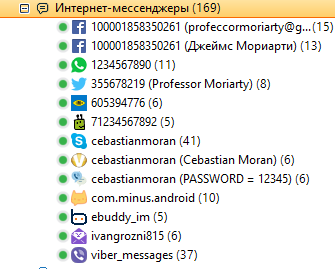
- Web Browser Research
- Mobile research
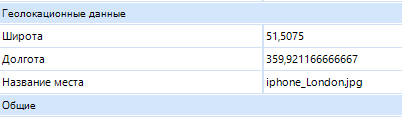
- Geolocation data retrieval
- Search for text sequences in cases
- Extract and analyze data from cloud storage
- Using bookmarks to highlight significant evidence found during the study
- Exploring Windows system files

- Windows registry analysis
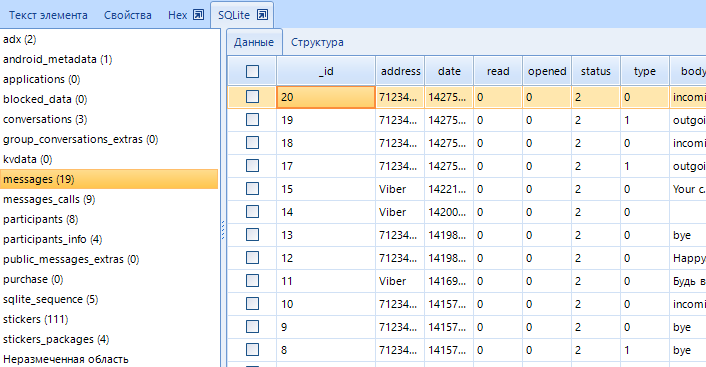
- SQLite Database Analysis
- Data Recovery Methods
- Methods of research of dumps of random access memory
- Using a hash calculator and hash analysis in forensic research
- Analysis of encrypted files
- Research methods for graphic and video files
- The use of analytical techniques in forensic research
- Automate routine actions with Belkascripts built-in programming language

- Practical lessons
Course: Belkasoft Incident Response Examination
The purpose of the course is to study the basics of the forensic investigation of cyber attacks and the possibilities of using Belkasoft Evidence Center in the investigation. You will learn about the main vectors of modern attacks on computer networks, learn to classify computer attacks based on the MITRE ATT & CK matrix, apply operating system research algorithms to establish the fact of compromise and reconstruct attackers' actions, find out where artifacts are located that indicate which files were opened last , where the operating system stores information about downloading and running executable files, how attackers moved across the network, and learn how to explore these artifacts using BE C. You will also learn which events in the system logs are of interest in terms of investigating incidents and establishing the fact of remote access and learn how to investigate them using BEC.
The course will be useful to technical specialists who determine the reasons for a successful invasion, analyze the chain of events and the consequences of cyberattacks; system administrators; SOC and CERT / CSIRT employees; information security officers.
Course Overview
Cyber Kill Chain describes the main stages of any technical attack on the victim's computers (or computer network) as follows:
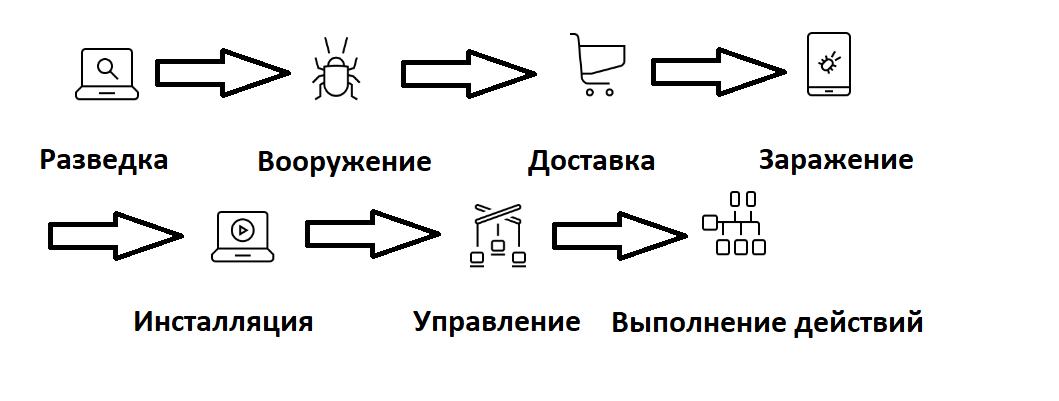
The actions of SOC employees (CERT, information security, etc.) are aimed at preventing intruders from securing information resources.
If the attackers nevertheless infiltrated the protected infrastructure, then the above-mentioned persons should try to minimize the damage from the activity of the attackers, determine how the attack was carried out, reconstruct the events and sequence of the attackers in the compromised information structure and take measures to prevent this type of attack in the future.
In a compromised information infrastructure, the following types of traces can be found indicating a compromised network (computer):

All such tracks can be found using the Belkasoft Evidence Center.
The BEC has an Incident Investigation module, which, when analyzing storage media, contains information about artifacts that can help a researcher investigate incidents.
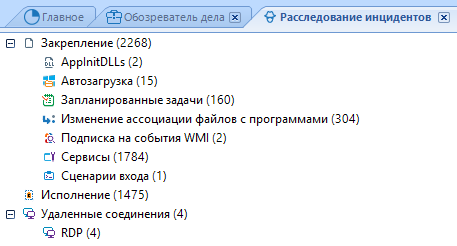
BEC supports the study of the main types of Windows artifacts that indicate the launch of executable files in the system under study, including Amcache, Userassist, Prefetch, BAM / DAM, Windows 10 Timeline files, and analysis of system events.
Information about traces containing information about user actions in a compromised system can be presented as follows:
This information, including, includes information about running executable files:
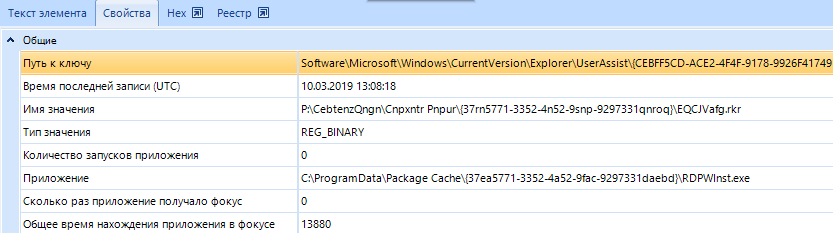
Information about starting the file 'RDPWInst.exe'.
Information about fixing attackers in compromised systems can be found in the Windows registry startup keys, services, scheduled tasks, Logon scripts, WMI, etc. Examples of detection of information about fixing in the system of attackers can be seen in the following screenshots:
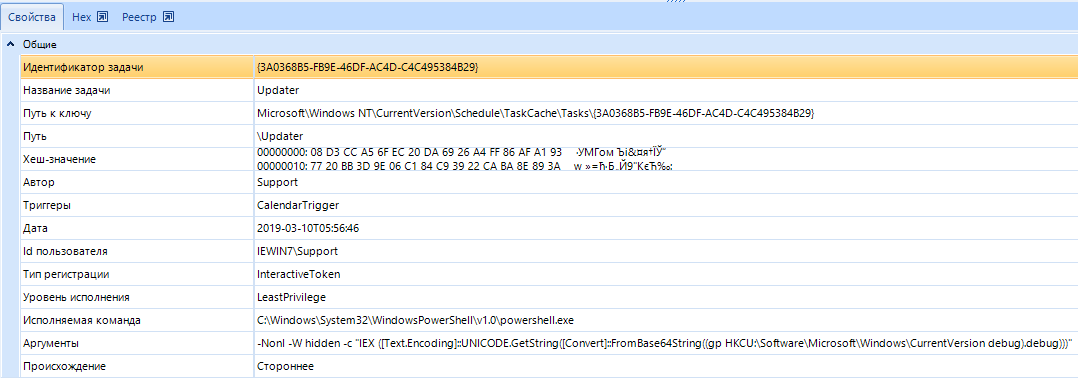
Fixing attackers using the task scheduler, by creating a task that launches a PowerShell script.
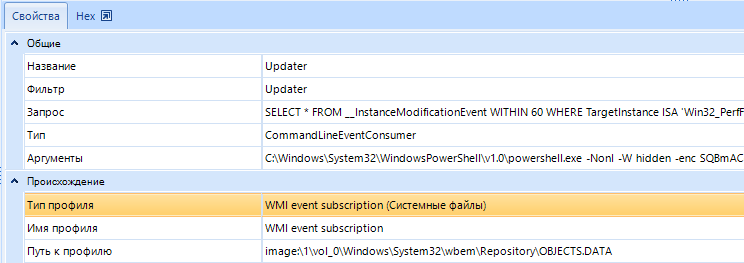
Securing attackers using Windows Management Instrumentation (WMI).
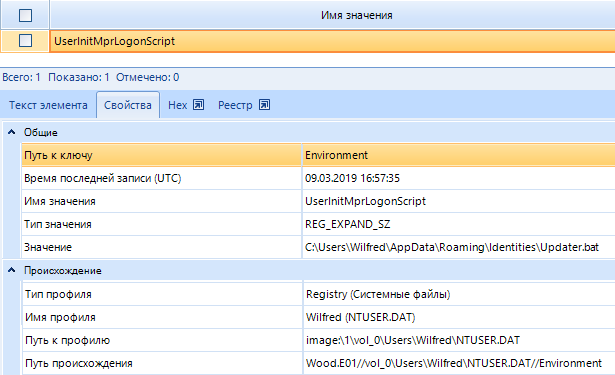
Securing attackers with a Logon script.
The movement of attackers over a compromised computer network can be detected, for example, by analyzing Windows system logs (when attackers use the RDP service).
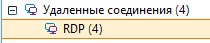
Information about detected RDP connections.

Information about the movement of attackers over the network.
Thus, the Belkasoft Evidence Center is able to help researchers identify compromised computers in an attacked computer network, find traces of malware launches, traces of attachment to the system and movement through the network, and other traces of attacking computers that have been compromised.
How to conduct similar studies and detect the artifacts described above is described in the Belkasoft Incident Response Examination training course.
Course Plan:
- Trends in cyberattacks. Technologies, tools, targets of attackers
- Using threat models to understand attacking tactics, techniques, and procedures
- Cyber kill chain
- The incident response algorithm: identification, localization, formation of indicators, search for new infected nodes
- Windows System Analysis with BEC
- Identification of methods of primary infection, spread over the network, fixing, network activity of malware using BEC
- Detection of infected systems and restoration of infection history using BEC
- Practical lessons
FAQ
Where are the courses held?
Courses are held at Group-IB headquarters or at an external venue (training center). A trainer can go to the site to corporate customers.
Who conducts the classes?
The trainers at Group-IB are practitioners with many years of experience in conducting forensic research, corporate investigations and information security incident response.
Qualification of trainers is confirmed by numerous international certificates: GCFA, MCFE, ACE, EnCE, etc.
Our trainers easily find a common language with the audience, explaining even the most complex topics. Students learn a lot of relevant and interesting information about the investigation of computer incidents, methods for detecting and countering computer attacks, and gain real practical knowledge that can be applied immediately after graduation.
Will the courses provide useful skills that are not related to Belkasoft products, or without these software, these skills will not be applicable?
The skills acquired during the training will be useful without using Belkasoft products.
What is included in the initial testing?
Primary testing is a test of knowledge of the basics of computer forensics. No knowledge testing of Belkasoft and Group-IB products is planned.
Where can I find information about the company's educational courses?
As part of the training courses, Group-IB trains specialists in incident response, malware research, cyber intelligence (Threat Intelligence), specialists for the Security Operation Center (SOC), specialists in proactive threat search (Threat Hunter), etc. . A full list of copyright courses from Group-IB is available here .
What bonuses do students who have completed the joint Group-IB and Belkasoft courses receive?
Those who completed the joint courses of Group-IB and Belkasoft will receive:
Courses are held at Group-IB headquarters or at an external venue (training center). A trainer can go to the site to corporate customers.
Who conducts the classes?
The trainers at Group-IB are practitioners with many years of experience in conducting forensic research, corporate investigations and information security incident response.
Qualification of trainers is confirmed by numerous international certificates: GCFA, MCFE, ACE, EnCE, etc.
Our trainers easily find a common language with the audience, explaining even the most complex topics. Students learn a lot of relevant and interesting information about the investigation of computer incidents, methods for detecting and countering computer attacks, and gain real practical knowledge that can be applied immediately after graduation.
Will the courses provide useful skills that are not related to Belkasoft products, or without these software, these skills will not be applicable?
The skills acquired during the training will be useful without using Belkasoft products.
What is included in the initial testing?
Primary testing is a test of knowledge of the basics of computer forensics. No knowledge testing of Belkasoft and Group-IB products is planned.
Where can I find information about the company's educational courses?
As part of the training courses, Group-IB trains specialists in incident response, malware research, cyber intelligence (Threat Intelligence), specialists for the Security Operation Center (SOC), specialists in proactive threat search (Threat Hunter), etc. . A full list of copyright courses from Group-IB is available here .
What bonuses do students who have completed the joint Group-IB and Belkasoft courses receive?
Those who completed the joint courses of Group-IB and Belkasoft will receive:
- certificate of completion;
- Free monthly subscription to Belkasoft Evidence Center;
- 10% discount on Belkasoft Evidence Center.
We remind you that the first course starts on Monday, September 9 , - do not miss the opportunity to get unique knowledge in the field of information security, computer forensics and incident response! Registration for the course here .
Sources
In preparing the article, Oleg Skulkin’s presentation “Using host-based forensics to get indicators of compromise for successful intelligence-driven incident response” was used.
All Articles