Details of malicious campaign for iPhone users revealed
On August 29, Project Zero, after a thorough study, published detailed information about the detected attack vectors during a massive campaign to steal iPhone user data.
The result of a successful attack on the user was the launch of a tracking agent (“implant”) with privileged rights in the background.
During the study, within the framework of attack vectors, 14 vulnerabilities were discovered:
- 7 iPhone browser vulnerabilities;
- 5 kernel vulnerabilities;
- 2 sandbox bypass vulnerabilities.

Although the discovered information was provided by Apple on February 1, 2019, as a result of which an unscheduled release of iOS 12.1.4 was released a week later, at least one privilege escalation vulnerability still remains a zero-day vulnerability and does not have a patch (CVE-2019-7287 )
Campaign discovery
In 2019, Google’s Threat Analysis Group (TAG) discovered several hacked web resources that were used to target targeted website visitors with 0-day iPhone vulnerabilities. At the same time, any visitor of the captured resources was attacked and, if successful, an “implant” was installed on the device, stealing user data. Presumably, the audience of sites amounted to several thousand visitors per week.
TAG identified 5 unique and independent attack vectors applicable to iOS versions 10-12 (with the exception of iPhone 8/8 + Xr / Xs), which indicates constant attempts to hack users for at least 2 years. Next, Google, together with the Project Zero team, conducted a thorough analysis of the detected malware.
According to Project Zero, “The main reason [of these vulnerabilities] ...: [in this case] is we see examples of broken code without the necessary code quality control or even simple testing and review before delivery to user devices.”
The root causes I highlight here are not novel and are often overlooked: we'll see cases of code which seems to have never worked, code that likely skipped QA or likely had little testing or review before being shipped to users. © Project Zero: A very deep dive into iOS Exploit chains found in the wild
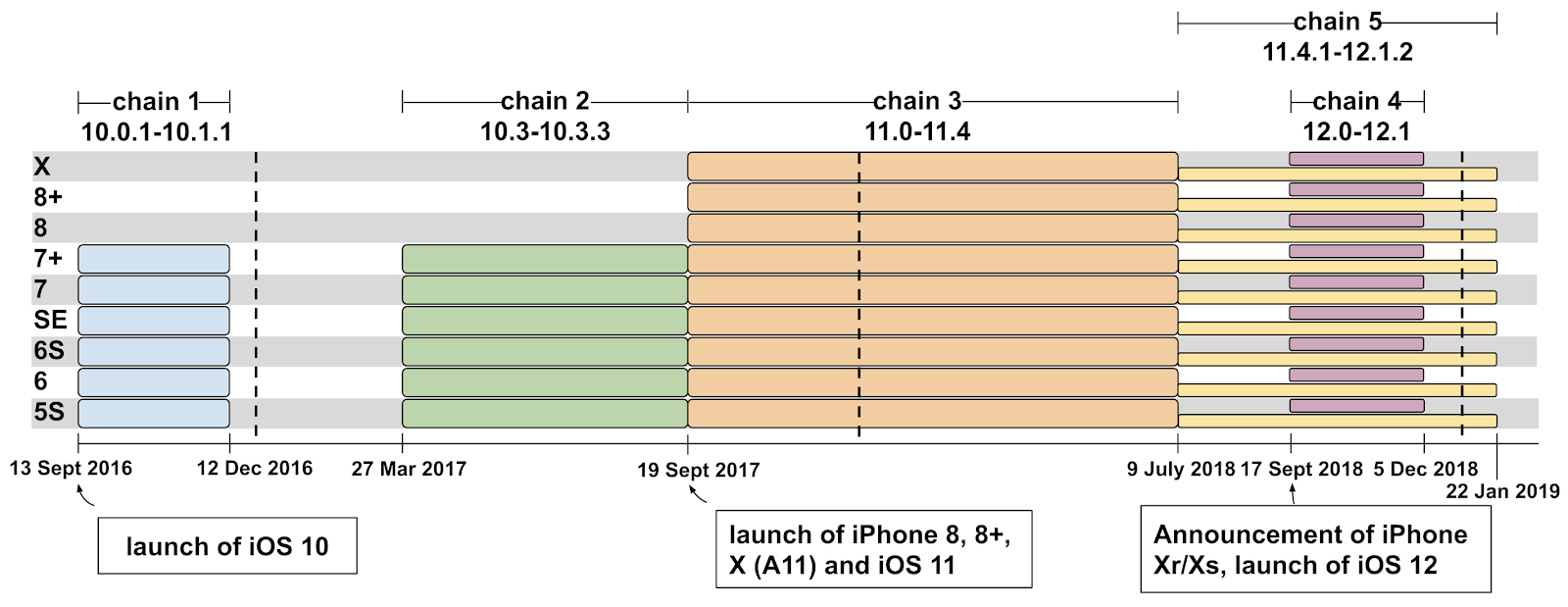
The diagram from Project Zero shows the time period from September 13, 2016 to January 22, 2019 and the attack vectors used in it.
Details of implant behavior
The implant specialized in stealing files and uploading data about the user's current geolocation by requesting commands from the attacker's server every 60 seconds. Due to privileged launch rights, the implant had access to all files on the victim’s device, including encrypted messenger databases: Whatsapp, Telegram, iMessage, Hangouts.
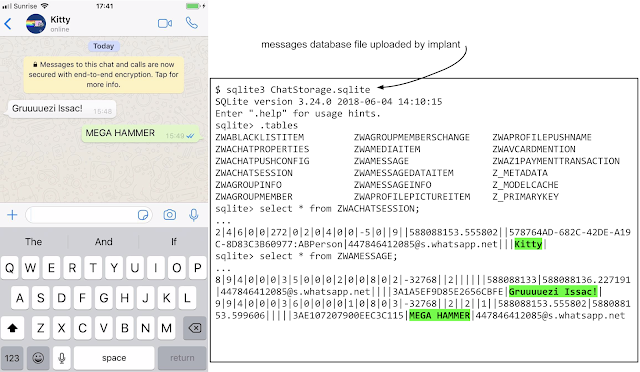
Example of data collected by the implant
The implant also unloaded the keychain of the device, containing data on the user access information stored or used at the time of execution.
Additionally, the following device information was collected and sent:
- iPhone model
- The name of the device (for example, Ian's iPhone)
- Unique ICCID SIM card number
- iPhone serial number
- telephone number;
- iOS version
- size and free space of the information carrier;
- active network interfaces.
All Articles