What we need to build Mesh: how the decentralized Internet provider Medium makes the new Internet based on Yggdrasil
Greetings!
Surely it will not be big news for you that the “Sovereign Runet” is just around the corner - the law comes into force on November 1 this year.
Unfortunately, how it will work (and whether it will work?) Is not entirely clear: there are so far no clear instructions for telecom operators. Also, there are no methods, fines, plans, distribution of responsibilities and those responsible - there is simply a declaration.
A similar situation was observed in relation to the implementation of the plans of the “Spring Law” - the equipment for the law did not have time to develop on time and the country's leading telecom operators were forced to repeatedly contact potential manufacturers of specialized equipment with relevant questions. However, they did not receive a response either about information about the equipment, or the samples themselves.
But the main thing is not how soon the law comes into force and what changes await us. The main thing is that, thanks to the introduction of this bill, the community of enthusiasts began to deploy an independent telecommunications environment in our country.
Today I will talk about what we have already managed to do, what we are going to do in the near future, and what difficulties and problems we had to face in the development of the project.
Before proceeding to the technical part of our project, I need to make a reservation about what the law “On Sovereign Runet” is all about.
In short: the authorities want to “secure” the Russian segment of the Internet in case conditional enemies want us to turn it off. But “the road to hell is paved with good intentions” - it’s not clear who they are going to protect us from and how the “enemies” can, in principle, disrupt the operation of the Russian segment of the Internet.
To implement this scenario, attacks must conspire all the countries of the world, cut all cross-border cables, bring down domestic satellites and create permanent radio interference.
That doesn't sound very believable.
Medium (Eng. Medium - “intermediary”, original slogan - Don’t ask for your privacy. Take it back ; also in English the word medium means “intermediate”) - a Russian decentralized Internet provider that provides access to the Yggdrasil network for free basis.
Initially, the project was conceived as a Mesh network in the Kolomensky urban district .
Medium was established in April 2019 to create an independent telecommunication environment by providing end users with access to Yggdrasil network resources using Wi-Fi wireless technology.
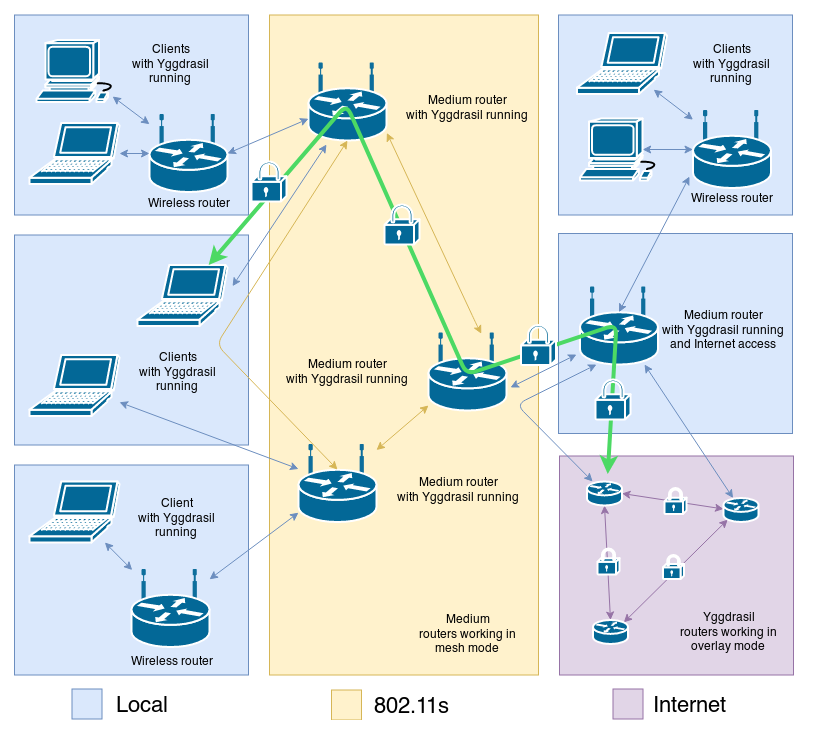
Yggdrasil is a self-organizing Mesh network with the ability to connect routers both in overlay mode (over the Internet) and directly to each other via a wired or wireless connection.
Yggdrasil is a continuation of the CjDNS project. The main difference between Yggdrasil and CjDNS is the use of the STP (spanning tree protocol) protocol.
By default, all network routers use end-to-end encryption to transfer data between other participants.
The choice of the Yggdrasil network as the main transport was due to the need to increase the connection speed (until August 2019, Medium used I2P ).
The transition to Yggdrasil also provided the project participants with the opportunity to start deploying a Mesh network with Full-Mesh topology. Such networking is the most effective antidote against censorship.
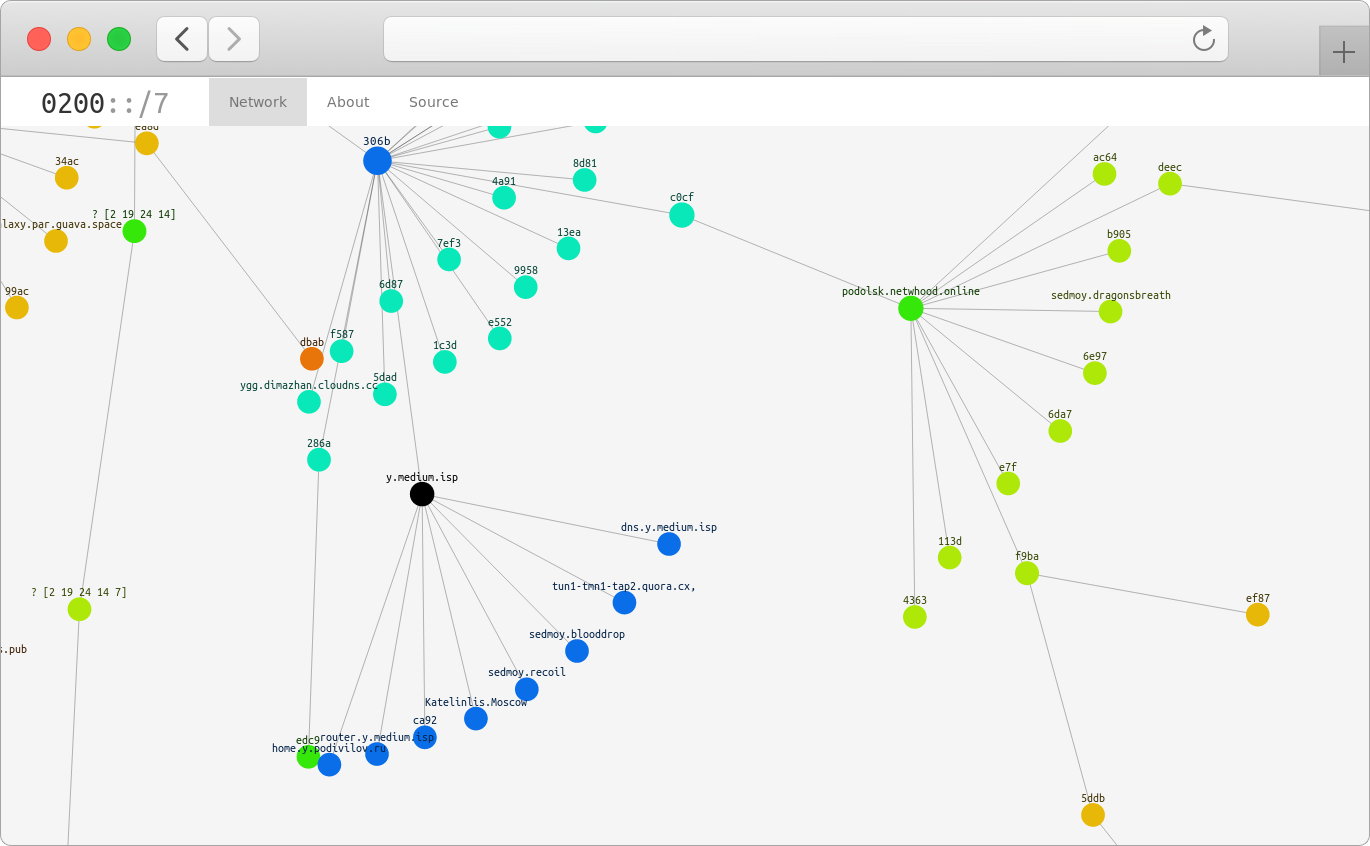
“Experience is the son of difficult mistakes.” During the development of Medium, we managed to resolve many problems that arose in our way.
One of the main problems at the time of network design was the ability to conduct a MITM attack . The traffic between the operator’s router and the client’s device was not encrypted in any way, because the main traffic was decrypted directly on the operator’s router.
The problem was that anyone could be behind the router - and we really didn’t want this “someone” to listen to everything that customers receive.
Our first mistake was the implementation of the Public Key Infrastructure (PKI).
Thanks to the use of level 7 of the OSI network model, we got rid of attacks such as MITM, but got a new problem - the need to install certificates of root certification authorities. And certification authorities are another superfluous problem. The key word here is "trust."
Again you need to trust someone! What if the certification authority is compromised? As comrade Murphy tells us, sooner or later the certification center will really be compromised. And this is the bitter truth.
We thought about the resolution of this problem for a long time and eventually came to the conclusion that there is no need to use PKI - it is enough to use Yggdrasil native encryption .
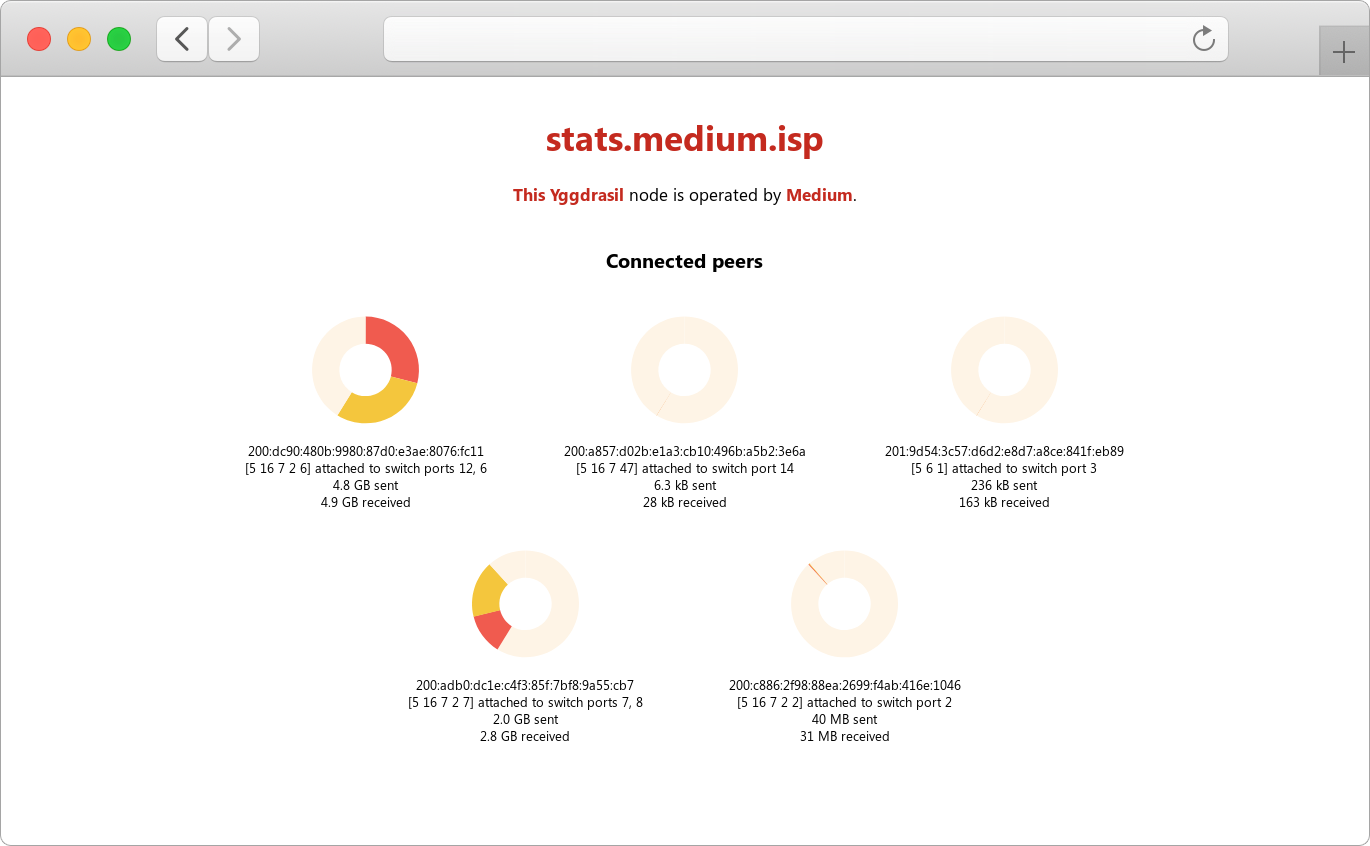
After making the appropriate adjustments, the topology of the Medium network took the following form:
We needed the domain name system from the very beginning, because bulky IPv6 addresses weren’t looking very good - it was inconvenient to use them in hyperlinks, and the lack of a semantic component was a big inconvenience.
We created several root DNS servers that stored a copy of the list of AAAA records located in the repository on GitHub .

However, the trust problem has not gone away - its operator could implement IPv6 address change on the DNS server in no time. In the presence of a certain dexterity - even almost imperceptibly for others.
Since we do not use HTTPS and, in particular, HSTS technology, when changing addresses in DNS, it was possible to carry out an attack by substituting the IPv6 address of the destination server without any problems.
The solution was not long in coming: we decided to resort to using EmerDNS technology - decentralized DNS.
In a sense, EmerDNS is similar to the hosts file, where there are records of all known sites. But unlike hosts:
Source: EmerDNS - An Alternative to DNSSEC
Initially, the word "Internet" meant by itself nothing more than interconnected networks or a network of networks .
Over time, the Internet has ceased to be associated with something academic in people and has become a more commonplace concept, since its influence has spread widely to the lives of ordinary people.
That is, initially the Internet was decentralized. Now it’s hard to call it decentralization, despite the fact that the concept has been preserved to this day - only the largest traffic exchange nodes are controlled by large companies. And large companies, in turn, are controlled by the state.
But back to our problem - the tendency towards centralization is set by the operators of individual services like social networks, email servers, instant messengers and so on.
“Medium” in this regard has been practically no different from the big Internet to date - most of the services have been centralized and controlled by individual operators.
Now we decided to take a course towards full decentralization - so that vital services could continue to work, regardless of whether the failure happened on the central server of the operator or not.
As a system for instant messaging, we use Matrix . As social networks - Mastodon and Hubzilla . For video hosting - PeerTube .
Of course, most services are still centralized and still controlled by individual operators, but the main thing is that there is a movement towards full decentralization and it is felt by all members of the community.
Read also:
I have nothing to hide
Everything you wanted to know about the decentralized Internet provider Medium, but were afraid to ask
Honey we kill the internet
Have questions? Join the discussion in Telegram: @medium_general .
Surely it will not be big news for you that the “Sovereign Runet” is just around the corner - the law comes into force on November 1 this year.
Unfortunately, how it will work (and whether it will work?) Is not entirely clear: there are so far no clear instructions for telecom operators. Also, there are no methods, fines, plans, distribution of responsibilities and those responsible - there is simply a declaration.
A similar situation was observed in relation to the implementation of the plans of the “Spring Law” - the equipment for the law did not have time to develop on time and the country's leading telecom operators were forced to repeatedly contact potential manufacturers of specialized equipment with relevant questions. However, they did not receive a response either about information about the equipment, or the samples themselves.
But the main thing is not how soon the law comes into force and what changes await us. The main thing is that, thanks to the introduction of this bill, the community of enthusiasts began to deploy an independent telecommunications environment in our country.
Today I will talk about what we have already managed to do, what we are going to do in the near future, and what difficulties and problems we had to face in the development of the project.

What is the law about?
Before proceeding to the technical part of our project, I need to make a reservation about what the law “On Sovereign Runet” is all about.
In short: the authorities want to “secure” the Russian segment of the Internet in case conditional enemies want us to turn it off. But “the road to hell is paved with good intentions” - it’s not clear who they are going to protect us from and how the “enemies” can, in principle, disrupt the operation of the Russian segment of the Internet.
To implement this scenario, attacks must conspire all the countries of the world, cut all cross-border cables, bring down domestic satellites and create permanent radio interference.
That doesn't sound very believable.

What is a Medium?
Medium (Eng. Medium - “intermediary”, original slogan - Don’t ask for your privacy. Take it back ; also in English the word medium means “intermediate”) - a Russian decentralized Internet provider that provides access to the Yggdrasil network for free basis.
When, where, and why was Medium created?
Initially, the project was conceived as a Mesh network in the Kolomensky urban district .
Medium was established in April 2019 to create an independent telecommunication environment by providing end users with access to Yggdrasil network resources using Wi-Fi wireless technology.
Where can I find a complete list of all network points?

What is Yggdrasil and why does Medium use it as its primary transport?
Yggdrasil is a self-organizing Mesh network with the ability to connect routers both in overlay mode (over the Internet) and directly to each other via a wired or wireless connection.
Yggdrasil is a continuation of the CjDNS project. The main difference between Yggdrasil and CjDNS is the use of the STP (spanning tree protocol) protocol.

By default, all network routers use end-to-end encryption to transfer data between other participants.
The choice of the Yggdrasil network as the main transport was due to the need to increase the connection speed (until August 2019, Medium used I2P ).
The transition to Yggdrasil also provided the project participants with the opportunity to start deploying a Mesh network with Full-Mesh topology. Such networking is the most effective antidote against censorship.

Debriefing: what rake we have already stepped on
“Experience is the son of difficult mistakes.” During the development of Medium, we managed to resolve many problems that arose in our way.
Mistake # 1: Public Key Infrastructure
One of the main problems at the time of network design was the ability to conduct a MITM attack . The traffic between the operator’s router and the client’s device was not encrypted in any way, because the main traffic was decrypted directly on the operator’s router.
The problem was that anyone could be behind the router - and we really didn’t want this “someone” to listen to everything that customers receive.
Our first mistake was the implementation of the Public Key Infrastructure (PKI).
Thanks to the use of level 7 of the OSI network model, we got rid of attacks such as MITM, but got a new problem - the need to install certificates of root certification authorities. And certification authorities are another superfluous problem. The key word here is "trust."
Again you need to trust someone! What if the certification authority is compromised? As comrade Murphy tells us, sooner or later the certification center will really be compromised. And this is the bitter truth.
We thought about the resolution of this problem for a long time and eventually came to the conclusion that there is no need to use PKI - it is enough to use Yggdrasil native encryption .
After making the appropriate adjustments, the topology of the Medium network took the following form:

Mistake # 2: centralized DNS
We needed the domain name system from the very beginning, because bulky IPv6 addresses weren’t looking very good - it was inconvenient to use them in hyperlinks, and the lack of a semantic component was a big inconvenience.
We created several root DNS servers that stored a copy of the list of AAAA records located in the repository on GitHub .

However, the trust problem has not gone away - its operator could implement IPv6 address change on the DNS server in no time. In the presence of a certain dexterity - even almost imperceptibly for others.
Since we do not use HTTPS and, in particular, HSTS technology, when changing addresses in DNS, it was possible to carry out an attack by substituting the IPv6 address of the destination server without any problems.
The solution was not long in coming: we decided to resort to using EmerDNS technology - decentralized DNS.
In a sense, EmerDNS is similar to the hosts file, where there are records of all known sites. But unlike hosts:
- Each line in EmerDNS can only be modified by its owner, and no one else
- The impossibility of "intervention of God (super-admin)" is ensured by the consensus of miners
- This file is the same for everyone, which is provided by the blockchain replication mechanism
- Fast file attached to file
Source: EmerDNS - An Alternative to DNSSEC
Mistake # 3: centralized everything
Initially, the word "Internet" meant by itself nothing more than interconnected networks or a network of networks .
Over time, the Internet has ceased to be associated with something academic in people and has become a more commonplace concept, since its influence has spread widely to the lives of ordinary people.
That is, initially the Internet was decentralized. Now it’s hard to call it decentralization, despite the fact that the concept has been preserved to this day - only the largest traffic exchange nodes are controlled by large companies. And large companies, in turn, are controlled by the state.
But back to our problem - the tendency towards centralization is set by the operators of individual services like social networks, email servers, instant messengers and so on.
“Medium” in this regard has been practically no different from the big Internet to date - most of the services have been centralized and controlled by individual operators.
Now we decided to take a course towards full decentralization - so that vital services could continue to work, regardless of whether the failure happened on the central server of the operator or not.
As a system for instant messaging, we use Matrix . As social networks - Mastodon and Hubzilla . For video hosting - PeerTube .
Of course, most services are still centralized and still controlled by individual operators, but the main thing is that there is a movement towards full decentralization and it is felt by all members of the community.
Read also:
I have nothing to hide
Everything you wanted to know about the decentralized Internet provider Medium, but were afraid to ask
Honey we kill the internet
Have questions? Join the discussion in Telegram: @medium_general .
A small present for those who have read to the end
All Articles