Photos taken hostage. The first hacking of digital cameras via WiFi (PTP / IP protocol)

Nowadays, no device with a network connection is protected from potential hacking. Even the camera.
At the DEF CON 2019 hacker conference, Eyal Itkin of Check Point Software Technologies revealed the world's first live exploit for the PTP (Picture Transfer Protocol) protocol. Many modern DSLRs support file transfer over WiFi. In this case, a malicious WiFi access point is described, to which the surrounding cameras are automatically connected.
The exploit also works when the camera is physically connected to the computer via PTP / USB. In both cases, an attacker can establish a connection with the camera and load executable code on it. For example, to encrypt all images on a card.
For example, Check Point Eyal Itkin uploaded a demo version of a ransomware malware to a Canon EOS 80D camera that encrypts files on a flash card. Itkin suggests that this is a very real monetization model: photos of important life events are often stored there, so people will want to pay to get them back.
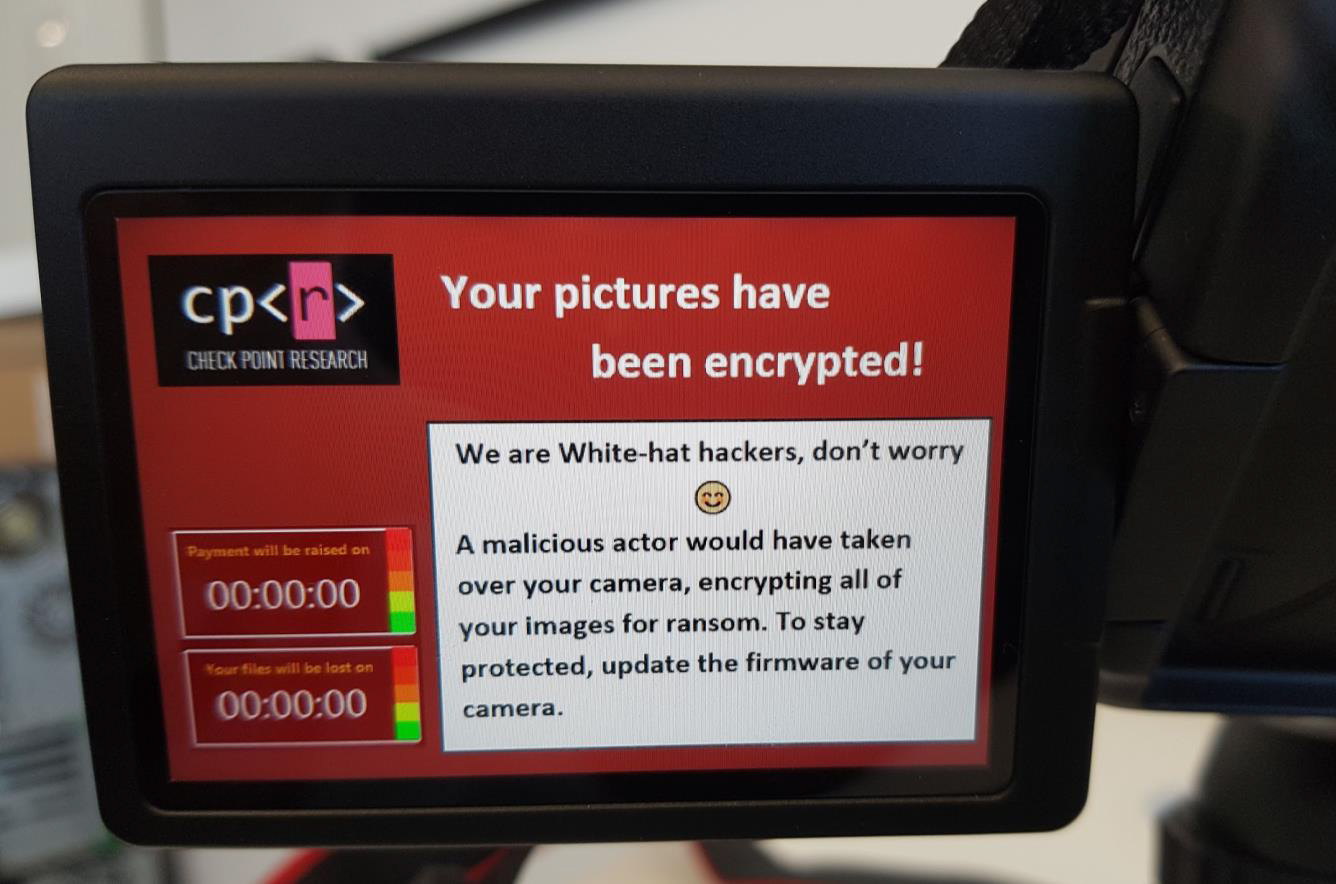
In addition to the ransomware, other exploit exploitation methods are theoretically possible:
- Complete incapacitation
- Using the camera for espionage (she already takes photos)
They chose the Canon model because this manufacturer controls more than 50% of the global digital camera market. In addition, an extensive modding movement has developed around Canon cameras. Activists reverse engineered firmware and hardware to release free firmware with enhanced functionality: see Magic Lattern and Canon Hack Development Kit (CHDK).
But similar methods apply to other cameras, since they all support PTP in a standard way. And this protocol has important properties that favor hacking:
- no authentication and encryption (the protocol was originally created under USB, then the existence of PTP / IP was not assumed);
- support for dozens of complex teams with rich functionality;
- WiFi support.
In connection with the hacking, Canon issued a patch and a security warning , in which it recommends users to take precautions, do not connect to suspicious WiFi and disable network functions if they are not used.
Video demo
Attack Technical Details
The first thing the hacker did was reverse engineer and analyze the camera firmware. It turned out that it is encrypted by AES, but there is no key. But the Magic Lattern community has already solved this problem. They used ROM Dumper and got keys.
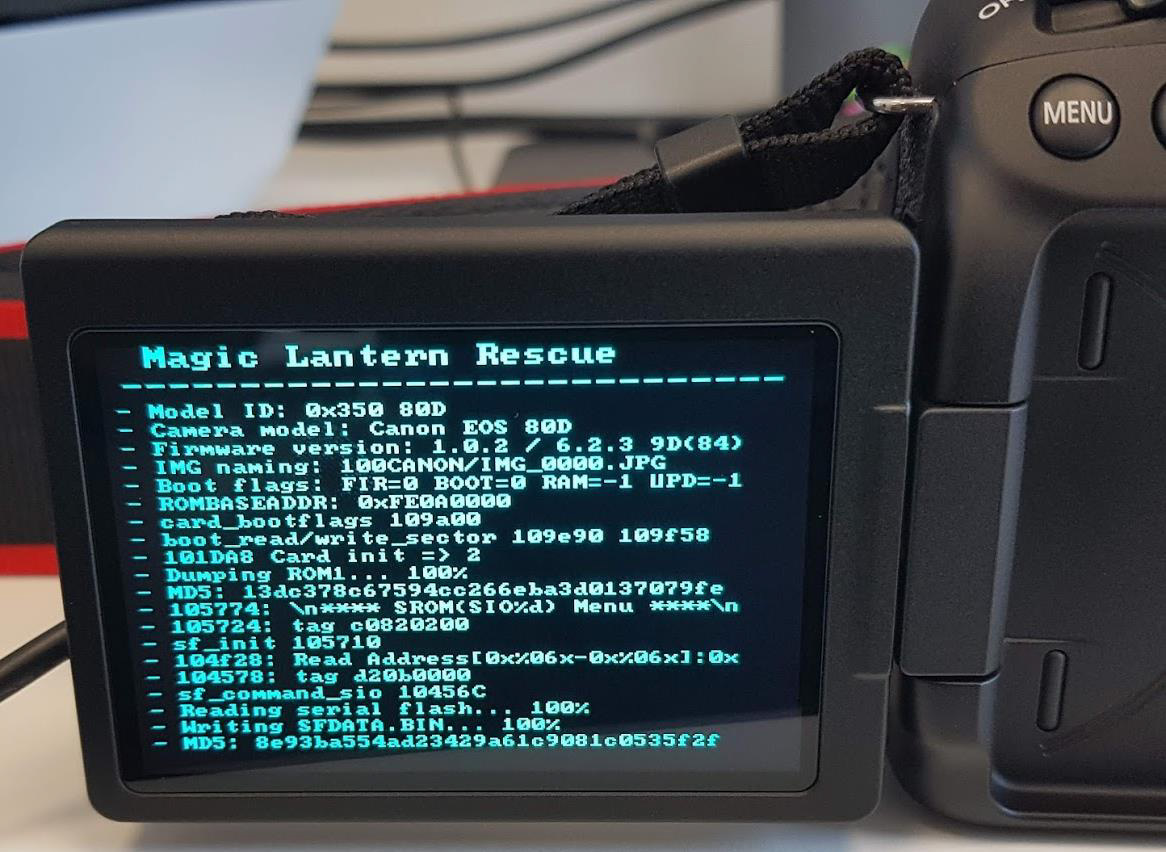
The dump is loaded into the IDA, and Magic Lattern has a good database with documented addresses where this or that function is called from. Canon cameras use the proprietary DryOS real-time OS. Thanks to her, the device is able to reboot in just three seconds.
Here is a list of PTP commands with opcodes in DryOS. To find the necessary code in the firmware, it is enough to start the search for the corresponding constant indicated in the list for each command.
A superficial analysis of some functions that work with PTP commands showed that they are rather difficult to implement (148 unique handlers in one function) and there are obvious vulnerabilities in buffer overflows.
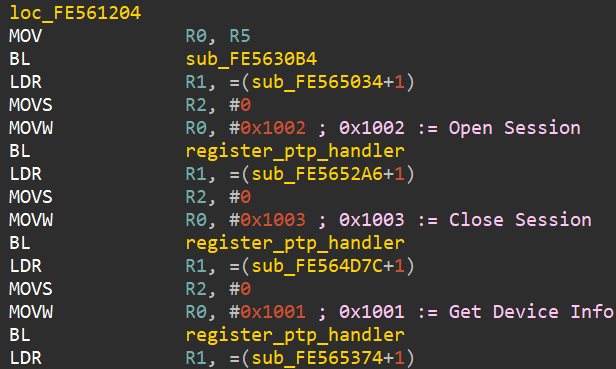
Itkin found four buffer overflow vulnerabilities when calling four PTP commands (SendObjectInfo, NotifyBtStatus, BLERequest, SendHostInfo): vulnerability numbers CVE-2019-5994, CVE-2019-5998, CVE-2019-5999, CVE-2019-6000). Interestingly, two vulnerabilities are related to Bluetooth processing, although this camera model does not support Bluetooth.
Now it remained to collect a suitable exploit, which was done. But the author did not stop there and, for a more visual demonstration, decided to write a ransomware program that will encrypt files on a flash card. And the idea was not to implement your own cryptography, but to use the AES encryption functions built into the Canon firmware itself ! In search of cryptographic functions, Iskin even found the encryption keys themselves.
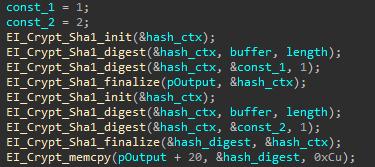 Due to the proprietary implementation, it was difficult to understand how the key is generated in the firmware. But this understanding is not necessary for using cryptographic functions, Itkin said. At the command of the malware, they successfully encrypt photos on the map and calculate the correct signature.
Due to the proprietary implementation, it was difficult to understand how the key is generated in the firmware. But this understanding is not necessary for using cryptographic functions, Itkin said. At the command of the malware, they successfully encrypt photos on the map and calculate the correct signature.
Itkin also developed a way to install a malicious firmware update on the camera without user intervention (CVE-2019-5995).
In a presentation on DEF CON, the author says that this is the first exploit for the PTP protocol and “a reliable way to capture most DSLR without exploiting any vulnerabilities”.

All Articles