Medium Weekly Digest # 5 (9 - 16 Aug 2019)
We constantly hear the phrase “national security”, but when the state begins to monitor our communication, fixing it without good suspicion, legal basis and without any apparent purpose, we must ask ourselves the question: are they really protecting national security or are they protect your own?
- Edward Snowden
This digest is designed to increase the interest of the Community in the issue of privacy, which in the light of recent events is becoming more relevant than ever.
On the agenda:
 Enthusiasts of the decentralized Internet provider Medium community create their own search engine
Enthusiasts of the decentralized Internet provider Medium community create their own search engine
 Medium has established a new certification center, Medium Global Root CA. Who will be affected by the change?
Medium has established a new certification center, Medium Global Root CA. Who will be affected by the change?
 Security certificates for every home - how to create your own service on the Yggdrasil network and issue a valid SSL certificate for it
Security certificates for every home - how to create your own service on the Yggdrasil network and issue a valid SSL certificate for it

Remind me - what is Medium?
Medium (Eng. Medium - “intermediary”, original slogan - Don’t ask for your privacy. Take it back ; also in English the word medium means “intermediate”) - a Russian decentralized Internet provider that provides access to the Yggdrasil network for free basis.
Full name - Medium Internet Service Provider. Initially, the project was conceived as a Mesh network in the Kolomensky urban district .
It was established in April 2019 as part of the creation of an independent telecommunications environment by providing end users with access to Yggdrasil network resources using Wi-Fi wireless data technology.
More information on the topic: “Everything you wanted to know about the decentralized Internet provider Medium, but were afraid to ask”
Enthusiasts of the decentralized Internet provider Medium community create their own search engine
Initially, the Yggdrasil network, which the decentralized Internet provider Medium uses as a transport, did not have its own DNS server or public key infrastructure - however, the need to issue security certificates for Medium network services solved these two problems.
Why PKI is needed if Yggdrasil “out of the box” provides the ability to encrypt traffic between peers?
There is no need to use the HTTPS protocol to connect to web services on the Yggdrasil network if you connect to them through a locally working Yggdrasil network router.
Indeed: Yggdrasil transport at the protocol level allows you to safely use resources within the Yggdrasil network - the possibility of conducting a MITM attack is completely excluded.
The situation changes radically if you get access to the Yggdarsil intranet resources not directly, but through an intermediate node - the access point of the Medium network, which is administered by its operator.
Who in this case can compromise the data that you transmit:
Solution : use the HTTPS protocol (level 7 of the OSI model ) to access web services within the Yggdrasil network. The problem is that it is not possible for Yggdrasil network services to issue a genuine security certificate by conventional means such as Let's Encrypt .
Therefore, we established our own certification authority - “Medium Global Root CA” . The vast majority of Medium network services are signed with the root security certificate of the Medium Domain Validation Secure Server CA intermediate certification authority.

The possibility of compromising the root certificate of the certification authority was certainly taken into account - but here the certificate is more necessary to confirm integrity during data transfer and exclude the possibility of MITM attacks.
The Medium network services from different operators have different security certificates, one way or another signed by the root certification authority. However, the operators of the root certification authority are not able to listen to the encrypted traffic of the services to which they signed the security certificates (see "What is CSR?" ).
Those who are especially concerned about their safety can use such tools as PGP and the like as additional protection.
At the moment, the Medium network public key infrastructure has the ability to verify the status of a certificate using the OCSP protocol or through the use of CRL .
Indeed: Yggdrasil transport at the protocol level allows you to safely use resources within the Yggdrasil network - the possibility of conducting a MITM attack is completely excluded.
The situation changes radically if you get access to the Yggdarsil intranet resources not directly, but through an intermediate node - the access point of the Medium network, which is administered by its operator.
Who in this case can compromise the data that you transmit:
- Access Point Operator . Obviously, the current Medium access point operator can listen to unencrypted traffic that passes through its equipment.
- Attacker (the man in the middle ). Medium has a problem similar to that of the Tor network , only with respect to the input and intermediate nodes.
This is how it looks 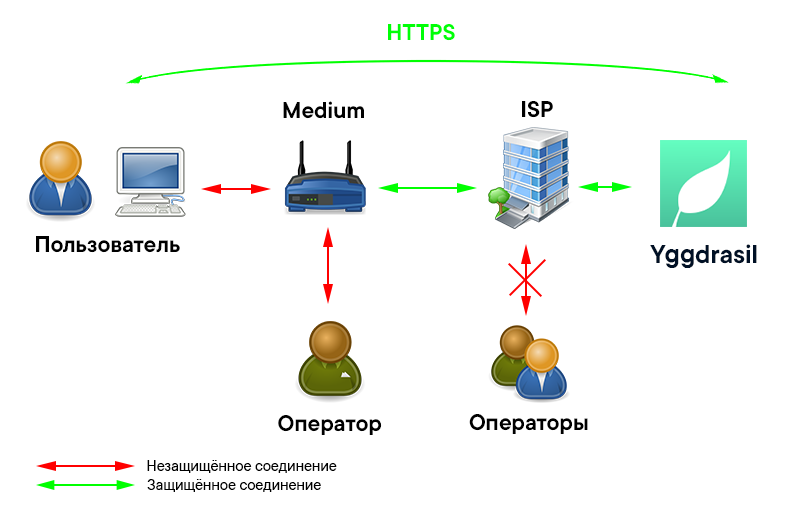

Solution : use the HTTPS protocol (level 7 of the OSI model ) to access web services within the Yggdrasil network. The problem is that it is not possible for Yggdrasil network services to issue a genuine security certificate by conventional means such as Let's Encrypt .
Therefore, we established our own certification authority - “Medium Global Root CA” . The vast majority of Medium network services are signed with the root security certificate of the Medium Domain Validation Secure Server CA intermediate certification authority.

The possibility of compromising the root certificate of the certification authority was certainly taken into account - but here the certificate is more necessary to confirm integrity during data transfer and exclude the possibility of MITM attacks.
The Medium network services from different operators have different security certificates, one way or another signed by the root certification authority. However, the operators of the root certification authority are not able to listen to the encrypted traffic of the services to which they signed the security certificates (see "What is CSR?" ).
Those who are especially concerned about their safety can use such tools as PGP and the like as additional protection.
At the moment, the Medium network public key infrastructure has the ability to verify the status of a certificate using the OCSP protocol or through the use of CRL .
Get to the point
@NXShock started developing a search engine for web services located on the Yggdrasil network. An important aspect is the fact that the determination of IPv6 addresses of services when performing a search is carried out by sending a request to a DNS server located inside the Medium network.
The main TLD is .ygg . Most domain names have this TLD, with the exception of two: .isp and .gg .
The search engine is under development, but its use is already possible today - just visit the website search.medium.isp .
You can help the development of the project by joining the development on GitHub .

Medium has established a new certification center, Medium Global Root CA. Who will be affected by the change?
Yesterday, the public testing of the functionality of the Medium Root CA certification center was completed. At the end of testing, errors in the operation of public key infrastructure services were fixed and a new root certificate of the Medium Global Root CA certification center was created.
All the nuances and features of PKI were taken into account - now the new Medium Global Root CA CA certificate will not be released until ten years later (after its expiration). Now, security certificates are issued only by intermediate certification authorities - for example, Medium Domain Validation Secure Server CA.
What does the certificate trust chain look like now? 


What needs to be done to make it work if you are a user:
Since some services use HSTS, before using the resources of the Medium network, it is necessary to delete the data of the intranet resources of Medium. You can do this on the History tab of your browser.
You must also install a new certificate from the Medium Global Root CA Certification Authority.
What you need to do to make it work if you are a system operator:
You need to reissue the certificate for your service on the pki.medium.isp page (the service is available only in the Medium network).
Security certificates for every home - how to create your own service on the Yggdrasil network and issue a valid SSL certificate for it
Due to the growing number of intranet services of the Medium network, the need for issuing new security certificates and setting up their services in such a way that they support SSL has increased.
Since Habr is a technical resource, in each new digest one of the agenda items will reveal the technical features of the Medium network infrastructure. For example, below is a comprehensive guide for issuing an SSL certificate for your service.
The examples will indicate the domain name domain.ygg , which must be replaced with the domain name of your service.
Step 1. Generate the private key and Diffie-Hellman parameters
openssl genrsa -out domain.ygg.key 2048
Then:
openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048
Step 2. Create a certificate signing request
openssl req -new -key domain.ygg.key -out domain.ygg.csr -config domain.ygg.conf
The contents of the domain.ygg.conf file:
[ req ] default_bits = 2048 distinguished_name = req_distinguished_name x509_extensions = v3_req [ req_distinguished_name ] countryName = Country Name (2 letter code) countryName_default = RU stateOrProvinceName = State or Province Name (full name) stateOrProvinceName_default = Moscow Oblast localityName = Locality Name (eg, city) localityName_default = Kolomna organizationName = Organization Name (eg, company) organizationName_default = ACME, Inc. commonName = Common Name (eg, YOUR name) commonName_max = 64 commonName_default = *.domain.ygg [ v3_req ] subjectKeyIdentifier = hash keyUsage = critical, digitalSignature, keyEncipherment extendedKeyUsage = serverAuth basicConstraints = CA:FALSE nsCertType = server authorityKeyIdentifier = keyid,issuer:always crlDistributionPoints = URI:http://crl.medium.isp/Medium_Global_Root_CA.crl authorityInfoAccess = OCSP;URI:http://ocsp.medium.isp
Step 3. Submit a certificate request
To do this, copy the contents of the domain.ygg.csr file and paste it into the text box on pki.medium.isp .
Follow the instructions on the site, then click Submit. If successful, you will receive a message to the e-mail address you specified, containing an attachment in the form of a certificate signed by an intermediate certification authority.
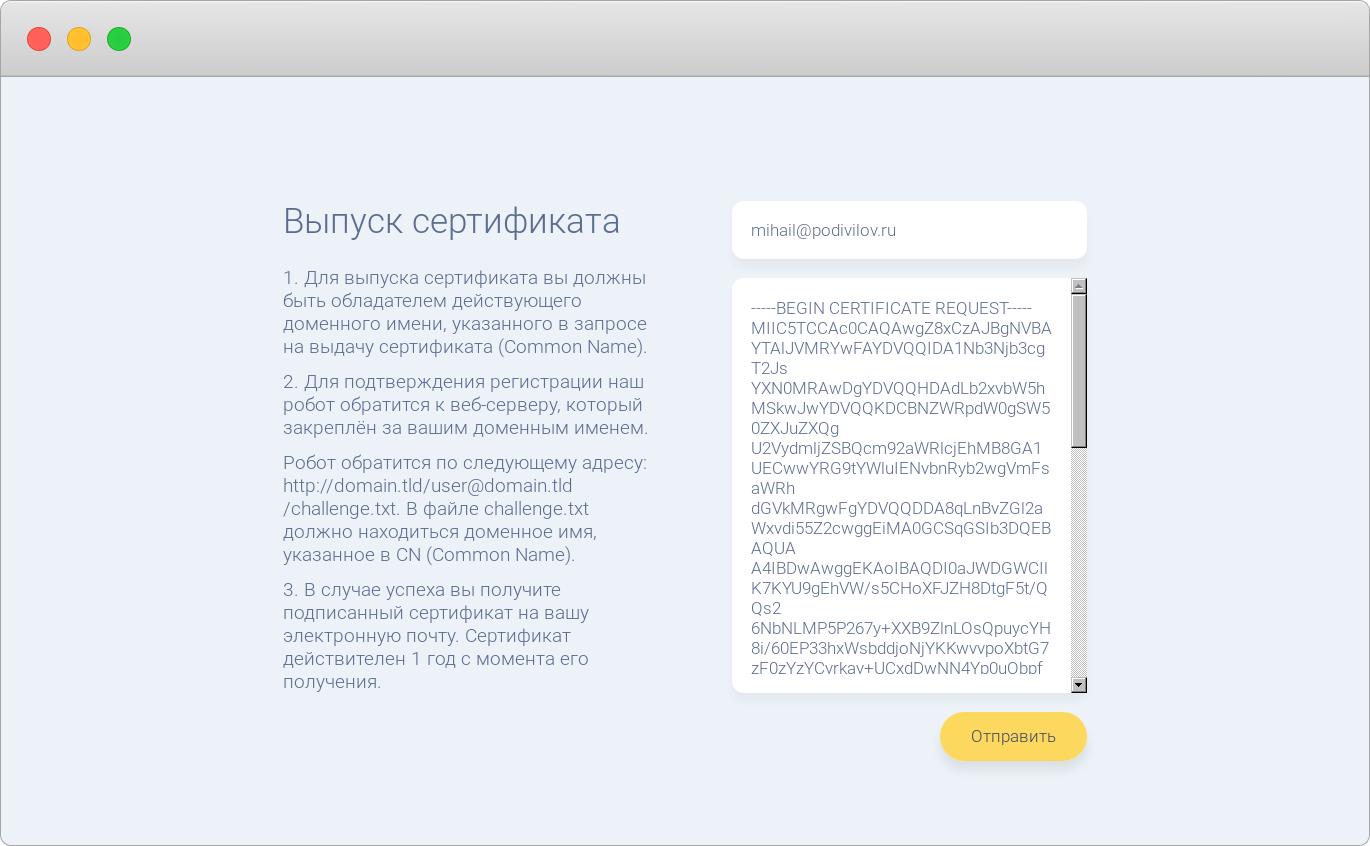
Step 4. Configure your web server
If you are using nginx as a web server, use the following configuration:
The file domain.ygg.conf in the directory / etc / nginx / sites-available /
server { listen [::]:80; listen [::]:443 ssl; root /var/www/domain.ygg; index index.php index.html index.htm index.nginx-debian.html; server_name domain.ygg; include snippets/domain.ygg.conf; include snippets/ssl-params.conf; location = /favicon.ico { log_not_found off; access_log off; } location = /robots.txt { log_not_found off; access_log off; allow all; } location ~* \.(css|gif|ico|jpeg|jpg|js|png)$ { expires max; log_not_found off; } location / { try_files $uri $uri/ /index.php$is_args$args; } location ~ \.php$ { include snippets/fastcgi-php.conf; fastcgi_pass unix:/run/php/php7.0-fpm.sock; } location ~ /\.ht { deny all; } }
The ssl-params.conf file in the / etc / nginx / snippets / directory
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH"; ssl_ecdh_curve secp384r1; ssl_session_cache shared:SSL:10m; ssl_session_tickets off; add_header Strict-Transport-Security "max-age=15552000; preload"; add_header X-Frame-Options DENY; add_header X-Content-Type-Options nosniff; ssl_dhparam /etc/ssl/certs/dhparam.pem;
The domain.ygg.conf file in the directory / etc / nginx / snippets /
ssl_certificate /etc/ssl/certs/domain.ygg.crt; ssl_certificate_key /etc/ssl/private/domain.ygg.key;
The certificate you received by e-mail must be copied at /etc/ssl/certs/domain.ygg.crt . Place the private key ( domain.ygg.key ) in the / etc / ssl / private / directory.
Step 5. Restart your web server
sudo service nginx restart
Free Internet in Russia starts with you
You can provide all possible assistance to the establishment of a free Internet in Russia today. We have compiled an exhaustive list of exactly how you can help the network:
- Share the Medium network with your friends and colleagues. Share a link to this article on social networks or a personal blog.
- Take part in the discussion of the technical issues of the Medium network on GitHub
- Create your web service on the Yggdrasil network and add it to the Medium DNS network
- Raise your Medium Access Point
Previous issues:
 Medium Weekly Digest # 1 (12 - 19 Jul 2019)
Medium Weekly Digest # 1 (12 - 19 Jul 2019)
 Medium Weekly Digest # 2 (19 - 26 Jul 2019)
Medium Weekly Digest # 2 (19 - 26 Jul 2019)
 Medium Weekly Digest # 3 (26 Jul - 2 Aug 2019)
Medium Weekly Digest # 3 (26 Jul - 2 Aug 2019)
 Medium Weekly Digest # 4 (2 - 9 Aug 2019)
Medium Weekly Digest # 4 (2 - 9 Aug 2019)
Read also:
Everything you wanted to know about the decentralized Internet provider Medium, but were afraid to ask
Honey we kill the internet
Decentralized Internet Service Provider Medium - Three Months Later
We are on Telegram: @medium_isp
All Articles