Network monitoring and detecting abnormal network activity with Flowmon Networks solutions

Recently, on the Internet you can find a huge number of materials on the topic of traffic analysis on the perimeter of the network . At the same time, for some reason, everyone completely forgot about the analysis of local traffic , which is no less important. This article is just visited this topic. Using Flowmon Networks as an example, we will recall the good old Netflow (and its alternatives), consider interesting cases, possible anomalies in the network and find out the advantages of the solution when the entire network works as a single sensor . And most importantly - a similar analysis of local traffic can be done completely free of charge, under a trial license ( 45 days ). If you are interested in the topic, welcome to cat. If you read laziness, then, looking ahead, you can register for the upcoming webinar , where we will show and tell you everything (in the same place you can learn about the upcoming product training).
What are Flowmon Networks?
First of all, Flowmon is a European IT vendor. The Czech company, headquartered in Brno (the issue of sanctions is not even raised). In its current form, the company has been represented on the market since 2007. Before that, it was known under the Invea-Tech brand. So in total almost 20 years have been spent on developing products and solutions.
Flowmon is positioned as an A-class brand. Develops premium solutions for corporate customers and is marked in the squares of Gartner in the direction of Network Performance Monitoring and Diagnostics (NPMD). And, interestingly, of all the companies in the report, Flowmon is the only vendor noted by Gartner as a manufacturer of solutions for both network monitoring and information protection (Network Behavior Analysis). It does not take the first place yet, but due to this, it does not stand like a wing from a Boeing.
What tasks does the product solve?
Globally, we can distinguish the following pool of tasks solved by the company's products:
- improving the stability of the network, as well as network resources by minimizing their downtime and inaccessibility;
- Improving overall network performance
- improving the efficiency of the administrative staff, due to:
- use of modern innovative network monitoring tools based on information about IP flows;
- providing detailed analytics about the functioning and condition of the network - users and applications running on the network, transmitted data, interacting resources, services and nodes;
- response to incidents before they occur, and not after the loss of service by users and customers;
- reducing the time and resources needed to administer the network and IT infrastructure;
- simplify troubleshooting tasks.
- increasing the level of security of the network and information resources of the enterprise, through the use of non-signature technologies to detect abnormal and malicious network activity, as well as “zero-day attacks”;
- providing the required level of SLA network applications and databases.
Flowmon Networks Product Portfolio
Now let's take a direct look at the Flowmon Networks product portfolio and find out what the company is specifically doing. As many have guessed from the name, the main specialization is in solutions for streaming flow monitoring of traffic, plus a number of additional modules that expand the basic functionality.
In fact, Flowmon can be called the company of one product, or rather - one solution. Let's figure it out whether it's good or bad.
The core of the system is the collector, which is responsible for collecting data on various flow protocols like NetFlow v5 / v9, jFlow, sFlow, NetStream, IPFIX ... It is quite logical that for a company that is not affiliated with any of the manufacturers of network equipment, it is important to offer the market a universal product, not tied to any one standard or protocol.

Flowmon collector
The collector is available both as a hardware server and as a virtual machine (VMware, Hyper-V, KVM). By the way, the hardware platform is implemented on customized DELL servers, which automatically removes most of the issues with warranty and RMA. Only FPGA traffic capture cards developed by a subsidiary of Flowmon, which allow monitoring at speeds up to 100 Gbps, are their own hardware component.
But what if there is no way to generate high-quality flow on existing network equipment? Or is the equipment load too high? No problem:

Flowmon prob
In this case, Flowmon Networks suggests using its own probes (Flowmon Probe), which are connected to the network through the SPAN port of the switch or using passive TAP splitters.
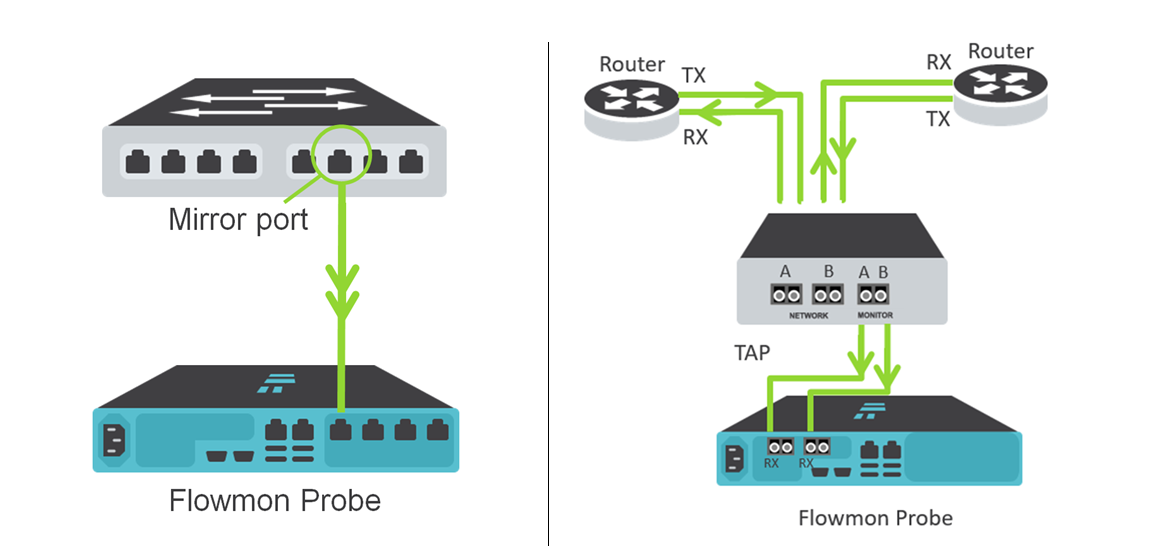
SPAN (mirror port) and TAP implementation options
In this case, the "raw" traffic arriving at Flowmon Probe is converted to Advanced IPFIX, containing more than 240 metrics with information . While the standard NetFlow protocol generated by network equipment contains no more than 80 metrics. This allows the visibility of the protocols not only at levels 3 and 4, but also at level 7 according to the ISO OSI model. As a result, network administrators can monitor the functioning of such applications and protocols as e-mail, HTTP, DNS, SMB ...
Conceptually, the logical architecture of the system is as follows:
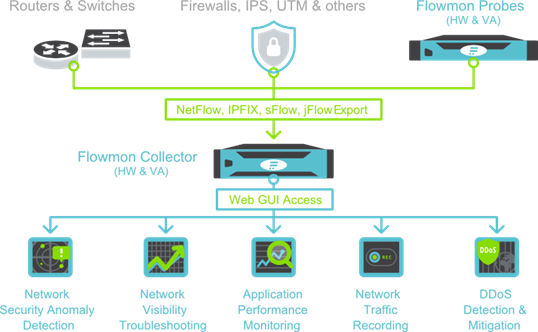
The central part of the entire Flowmon Networks ecosystem is the Collector, which receives traffic from existing network equipment or its own probes (Probe). But for Enterprise, providing solutions exclusively for monitoring network traffic would be too simple. Open Source solutions can do this, albeit not with such performance. The value of Flowmon are additional modules that expand the basic functionality:
- Anomaly Detection Security module - detection of abnormal network activity, including zero-day attacks, based on heuristic traffic analysis and a typical network profile;
- Application Performance Monitoring module - monitoring the performance of network applications without installing “agents” and affecting target systems;
- Traffic Recorder module - recording fragments of network traffic by a set of predefined rules or by a trigger from the ADS module, for further troubleshooting and / or investigation of information security incidents;
- DDoS Protection module - protection of the network perimeter from volumetric DoS / DDoS denial of service attacks, including attacks on applications (OSI L3 / L4 / L7).
In this article, we will look at how everything works live using the example of 2 modules - Network Performance Monitoring and Diagnostics and Anomaly Detection Security .
Initial data:
- Lenovo RS 140 server with VMware 6.0;
- image of the Flowmon Collector virtual machine, which can be downloaded here ;
- A pair of switches supporting flow protocols.
Step 1. Installing Flowmon Collector
The deployment of a virtual machine on VMware comes in a completely standard way from the OVF template. As a result, we get a virtual machine running CentOS and with ready-to-use software. Resource Requirements - Humane:

It remains only to perform basic initialization with the sysconfig command:
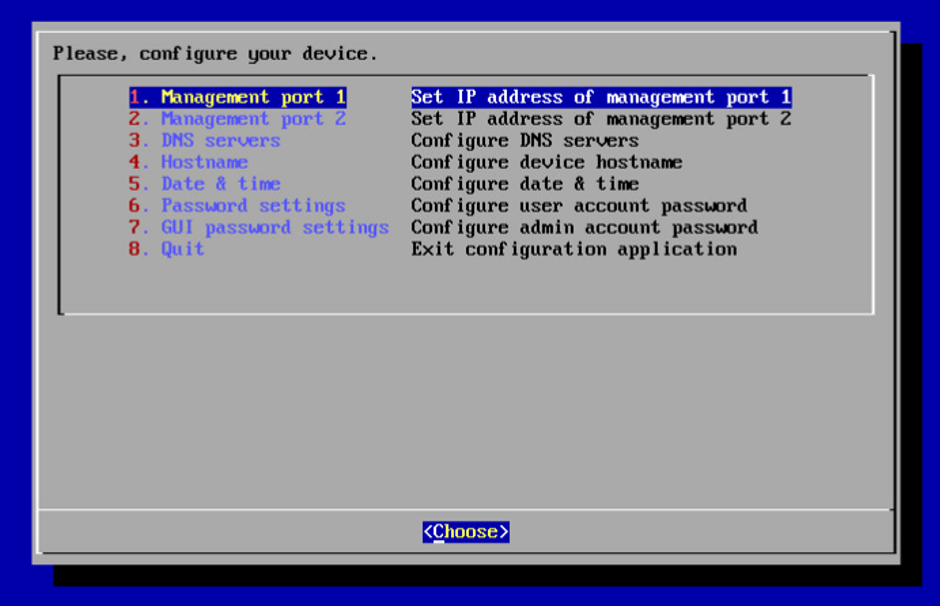
We configure IP on the management port, DNS, time, Hostname and can connect to the WEB interface.
Step 2. Installing the license
A trial license for a month and a half is generated and downloaded along with the image of the virtual machine. Loaded through Configuration Center -> License . As a result, we see:
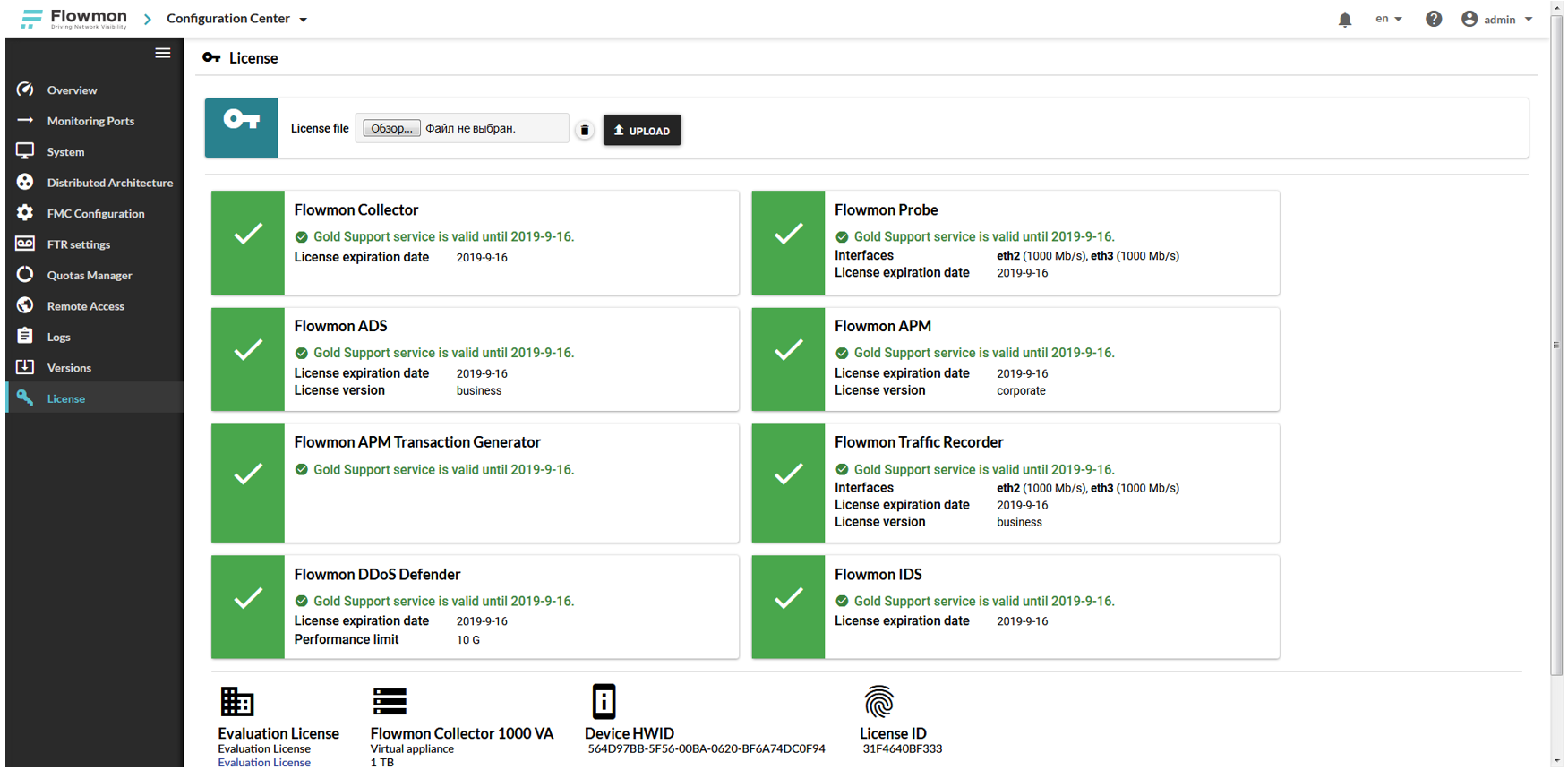
All is ready. You can get to work.
Step 3. Configuring the receiver on the collector
At this stage, you need to decide how the data from the sources will enter the system. As we said before, this can be one of the flow protocols or the SPAN port on the switch.
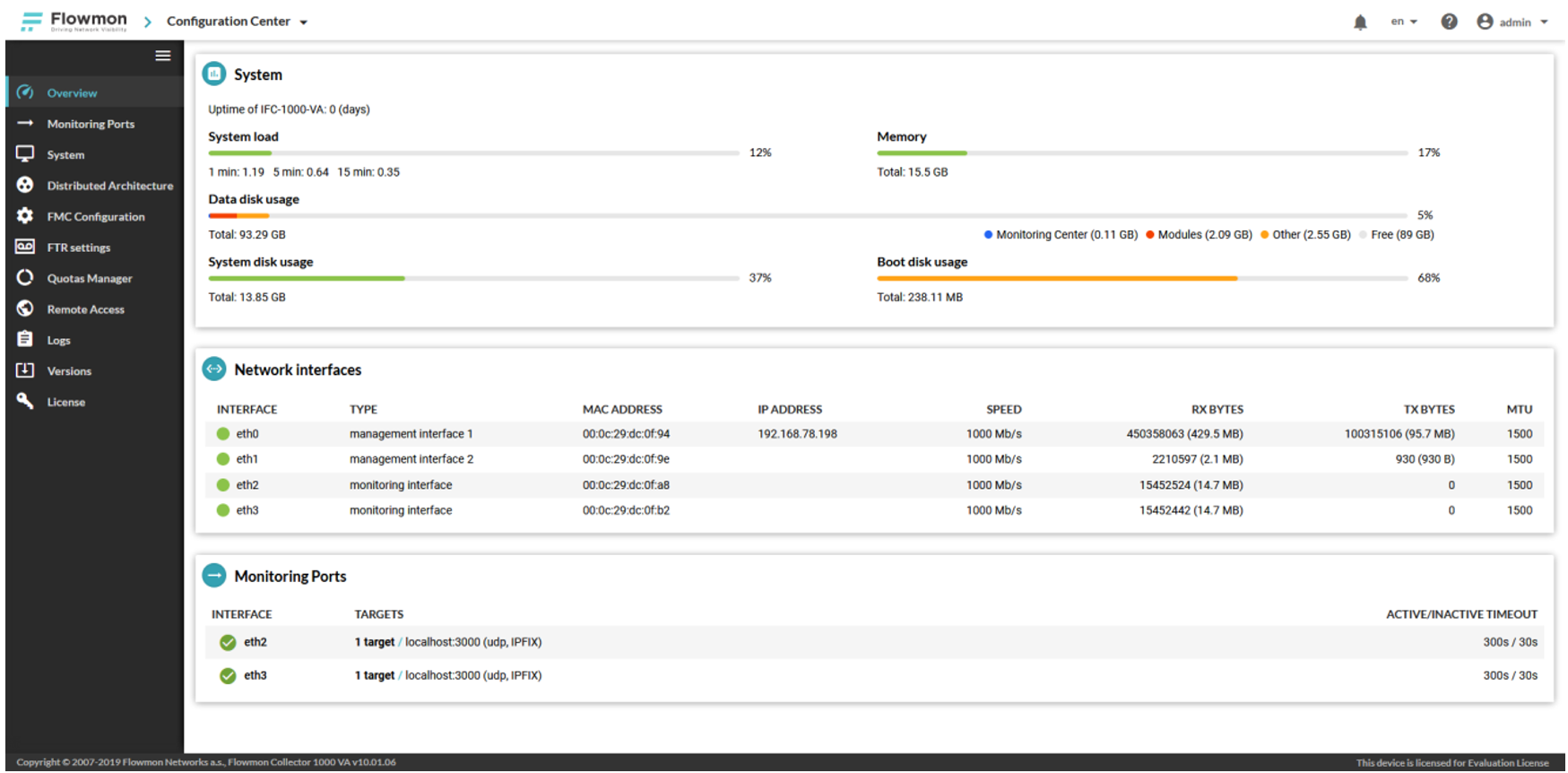
In our example, we will use data reception using the NetFlow v9 and IPFIX protocols. In this case, as a target we specify the IP address of the Management interface - 192.168.78.198 . The eth2 and eth3 interfaces (with the Monitoring interface type) are used to receive a copy of the raw traffic from the SPAN port of the switch. We skip them, not our case.
Next, check the collector port where traffic should flow.
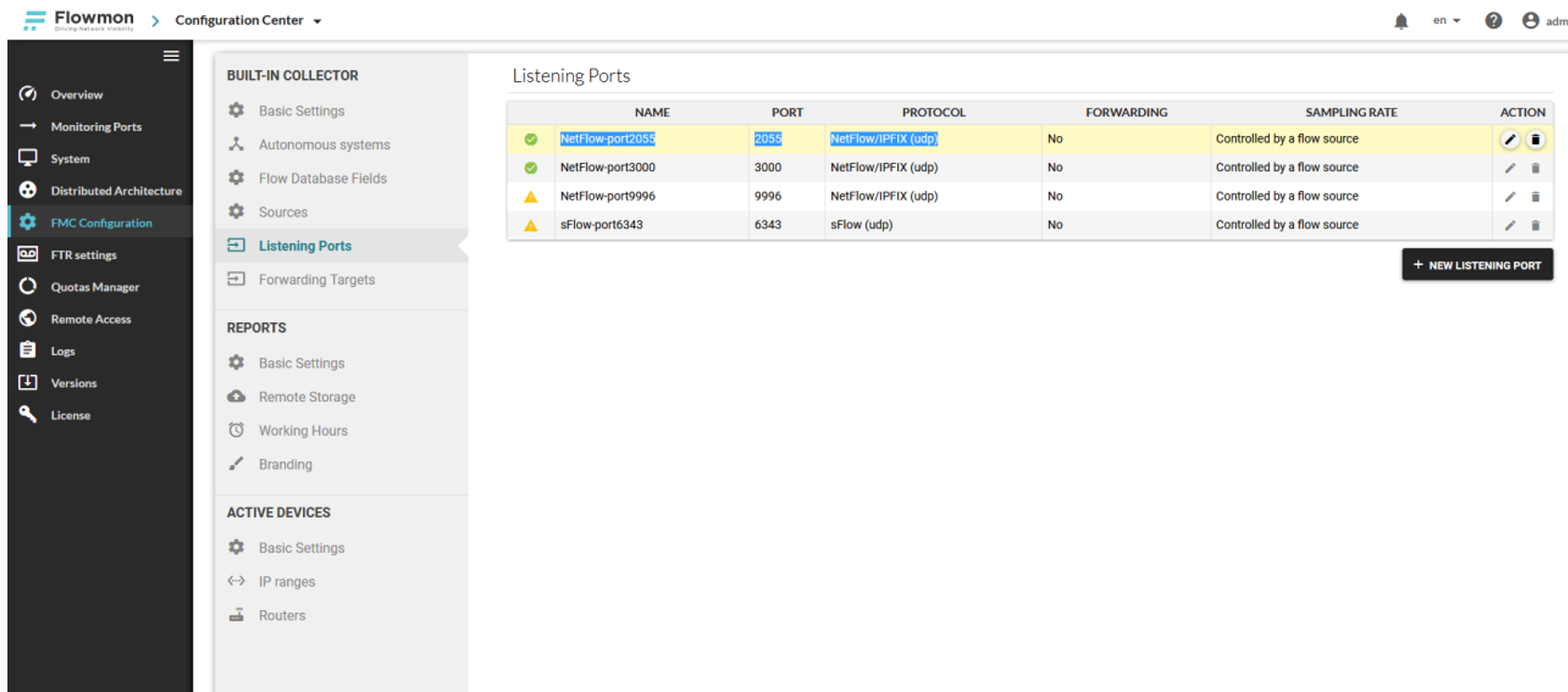
In our case, the collector expects traffic on the UDP / 2055 port.
Step 4. Configuring network equipment for flow export
Configuring NetFlow on Cisco Systems equipment can probably be called a completely normal thing for any network administrator. For our example, we will take something more unusual. For example, the MikroTik RB2011UiAS-2HnD router. Yes, oddly enough, this budget solution for small and home offices also supports NetFlow v5 / v9 and IPFIX protocols. In the settings, we set the target (collector address 192.168.78.198 and port 2055):

And add all the metrics available for export:
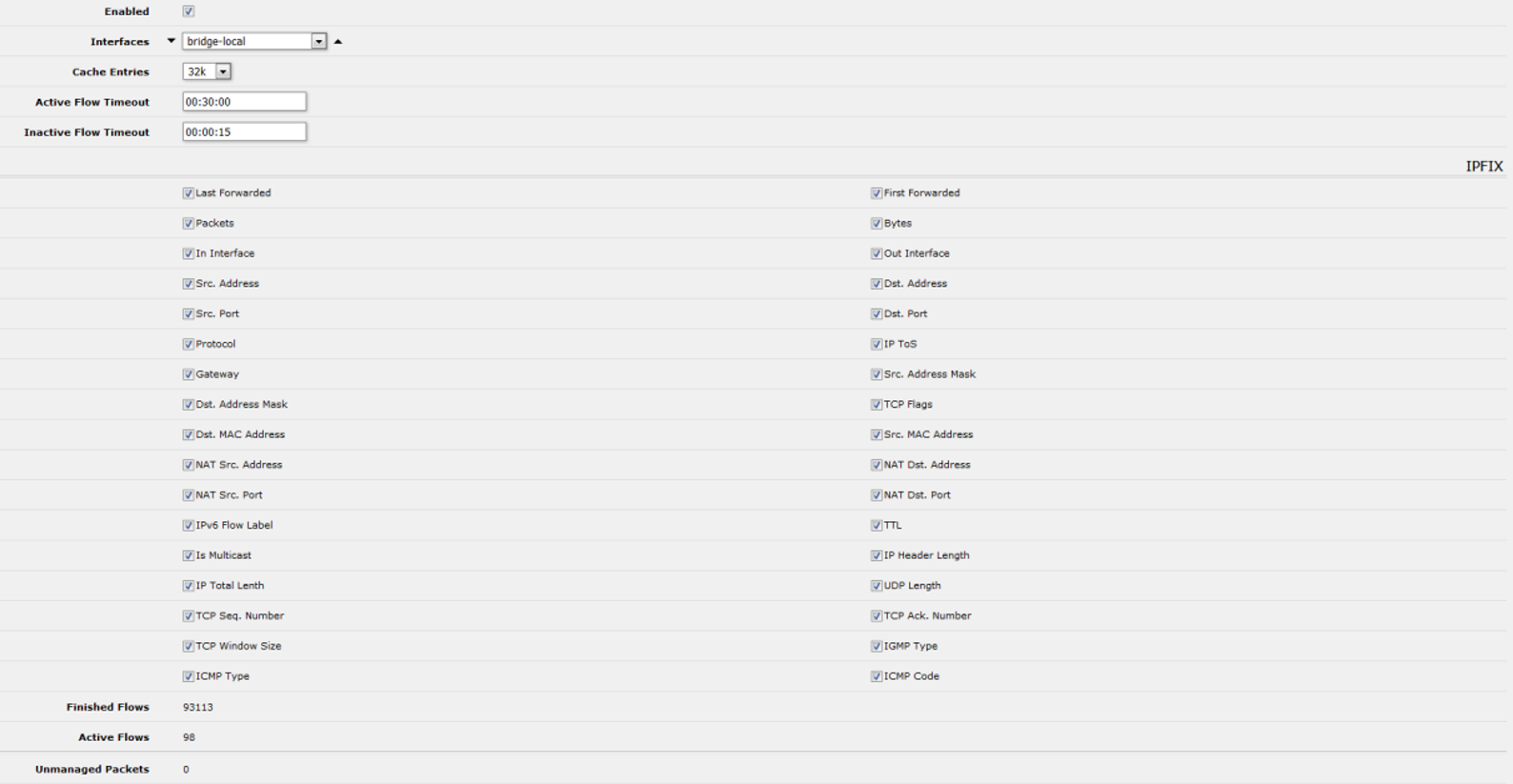
This can be said that the basic setup is complete. Check if traffic is entering the system.
Step 5. Test and operate the Network Performance Monitoring and Diagnostics module
You can check for traffic from the source in the Flowmon Monitoring Center -> Sources section:

We see that the data enters the system. Some time after the collector accumulates traffic, widgets will begin to display information:

The system is built on the principle of drill down. That is, the user, choosing a fragment of interest to him on a chart or graph, “falls through” to the level of data depth that he needs:

Up to the information about each network connection and connection:
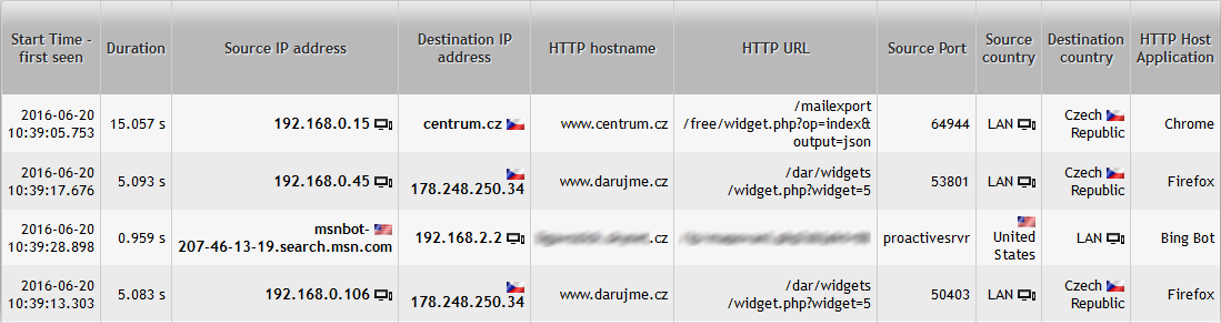
Step 6. Anomaly Detection Security Module
This module can be called perhaps one of the most interesting, thanks to the use of signatureless methods for detecting anomalies in network traffic and malicious network activity. But this is not an analogue of IDS / IPS systems. Work with the module begins with its “training”. To do this, a special wizard indicates all key components and services of the network, including:
- Gateway, DNS, DHCP and NTP server addresses
- Addressing in user and server segments.
After that, the system goes into a training mode, which on average lasts from 2 weeks to 1 month. During this time, the system generates baseline traffic characteristic of our network itself. Simply put, the system studies:
- What behavior is typical for hosts?
- What amounts of data are usually transmitted and are normal for the network?
- What is the typical runtime for users?
- What applications are online?
- and much more..
As a result, we get a tool that identifies any anomalies in our network and deviations from characteristic behavior. Here are a couple of examples the system can detect:
- distribution of new malware on the network that is not detected by antivirus signatures;
- building DNS, ICMP or other tunnels and transmitting data bypassing the firewall;
- the appearance on the network of a new computer posing as a DHCP and / or DNS server.
Let's see how it looks live. After your system has been trained and built baseline network traffic, it begins to detect incidents:
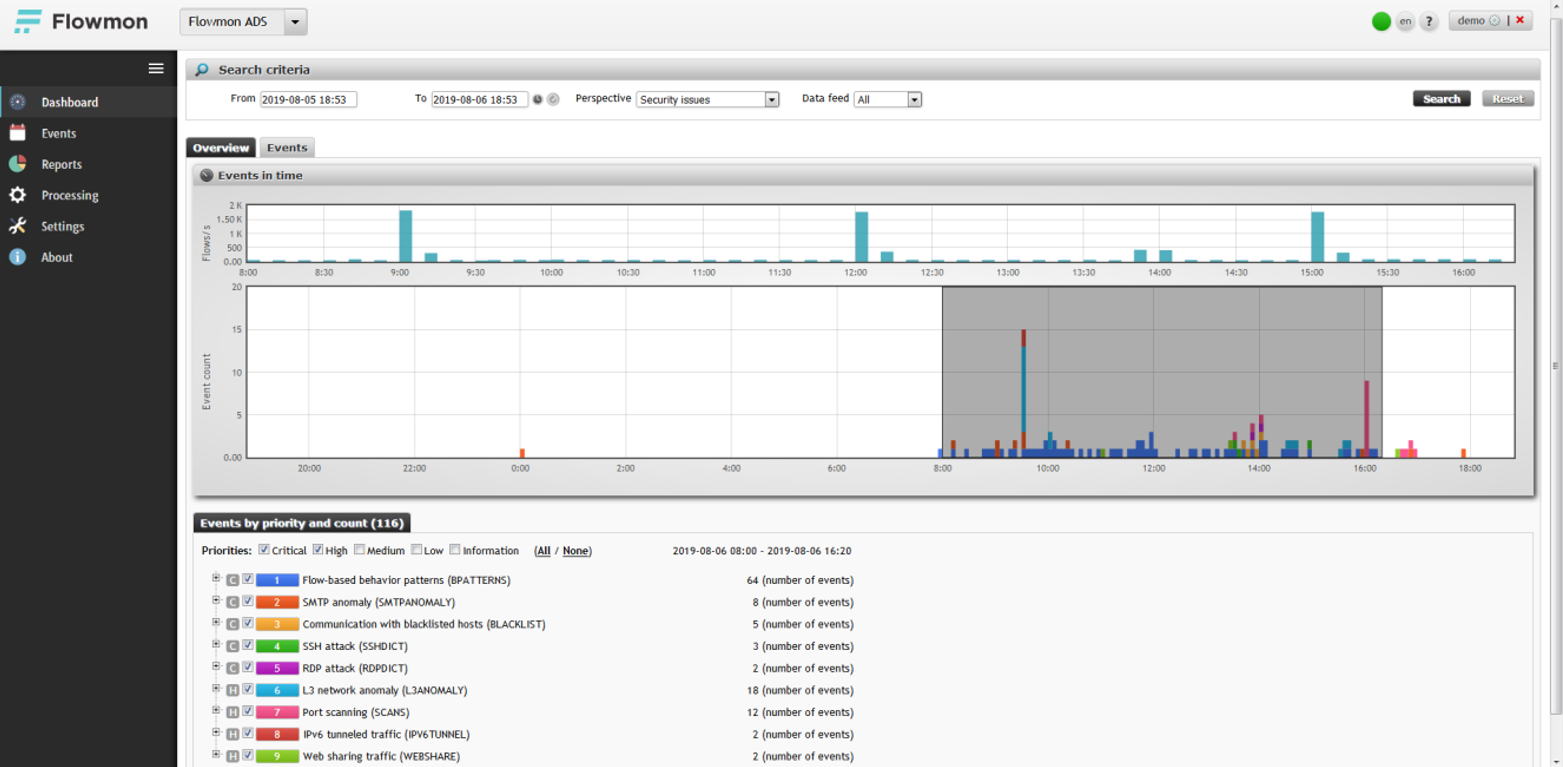
The main page of the module is a timeline with a display of identified incidents. In our example, we see a clear surge, approximately between 9 and 16 hours. We select it and look in more detail.
The abnormal behavior of an attacker on the network is clearly traced. It all starts with the fact that the host with the address 192.168.3.225 started a horizontal network scan on port 3389 (Microsoft RDP service) and finds 14 potential “victims”:
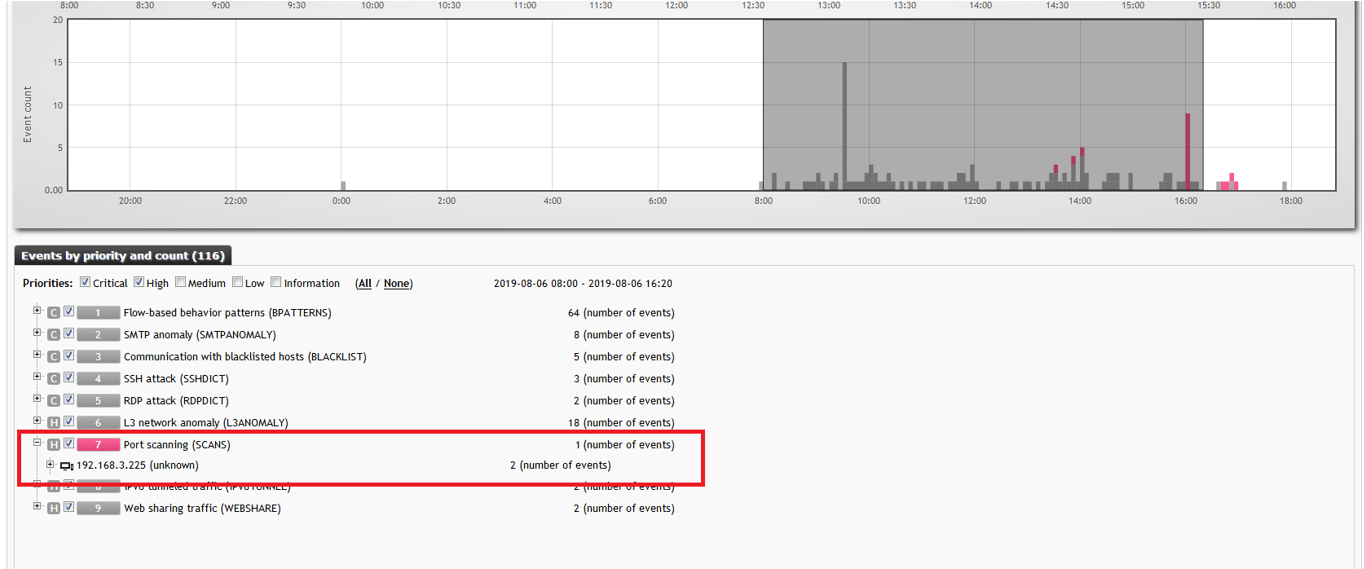
and
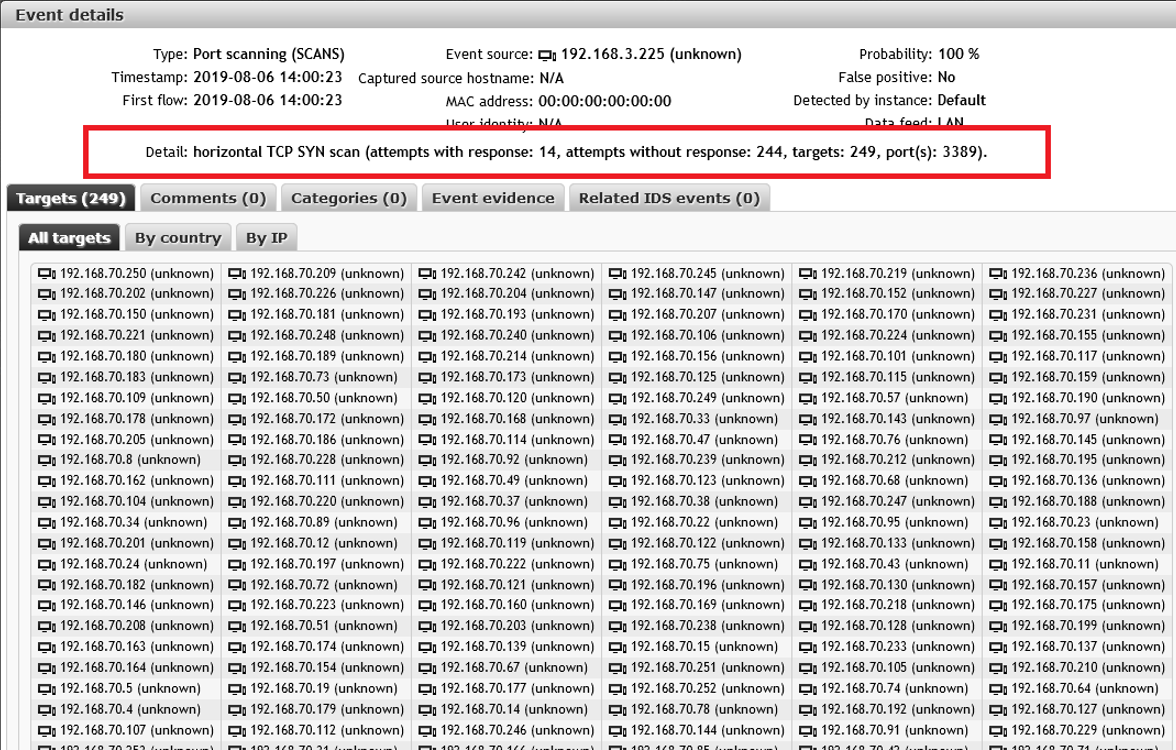
The following recorded incident - the host 192.168.3.225 starts a brute force attack to enumerate passwords for the RDP service (port 3389) at the previously identified addresses:
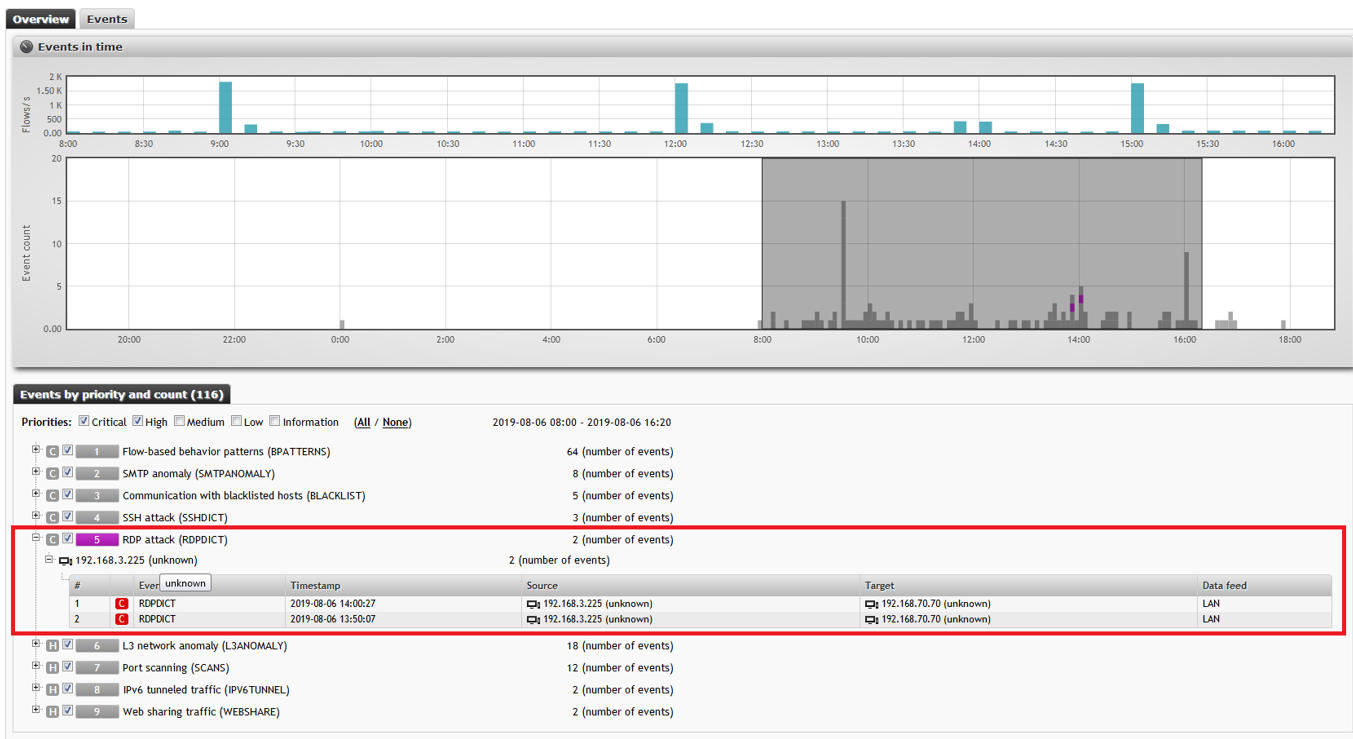
As a result of an attack on one of the hacked hosts, an SMTP anomaly is recorded. In other words, spamming began:
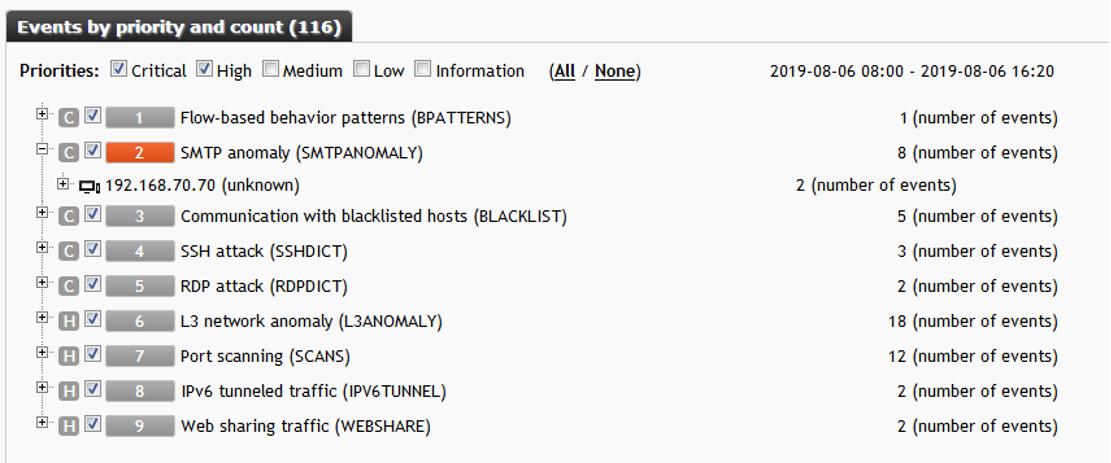
This example is a clear demonstration of the capabilities of the system and the Anomaly Detection Security module, in particular. Judge the effectiveness yourself. This concludes the functional review of the solution.
Conclusion
We summarize what conclusions we can draw about Flowmon in the bottom line:
- Flowmon - premium level solution for corporate Customers;
- due to its versatility and compatibility, data collection is available from any source: network equipment (Cisco, Juniper, HPE, Huawei ...) or proprietary probes (Flowmon Probe);
- the scalability of the solution allows you to increase the functionality of the system by adding new modules, as well as increase productivity through a flexible approach to licensing;
- due to the use of technologies of signatureless analysis, the system allows detecting even zero-day attacks not known to antiviruses and IDS / IPS systems;
- due to complete "transparency" in terms of installation and the presence of the system on the network - the solution does not affect the operation of other nodes and components of your IT infrastructure;
- Flowmon - the only solution on the market that supports traffic monitoring at speeds up to 100 Gb / s;
- Flowmon - a solution for networks of any scale;
- the best price / functionality ratio among similar solutions.
In this review, we examined less than 10% of the total solution functionality. In the next article, we will talk about the rest of the Flowmon Networks modules. Using the Application Performance Monitoring module as an example, we will show how business application administrators can ensure availability at a given SLA level and diagnose problems as quickly as possible.
Also, we want to invite you to our webinar (09/10/2019), dedicated to the solutions of the Flowmon Networks vendor. For pre-registration, please register here .
That's all for now, thanks for your interest!
All Articles