Well Apple Bleee
Apple is actively introducing to the masses the idea that everything is now in order with the privacy of user data for their products. But researchers from Hexway found that the standard and actively used Bluetooth LE (BLE) mechanism allows you to learn quite a lot about your iPhone.
If Bluetooth is turned on, then anyone within the range of the signal can find out:
- device status
- charge information;
- device name
- Wi-Fi status
- buffer availability;
- iOS version
- phone number.

This is most likely due to the new Find my feature announced this year ( Apple's 'Find My' Feature Uses Some Very Clever Cryptography | WIRED ). Its essence is to create an ecosystem of Apple devices that exchange BLE information with each other to be able to track stolen and lost devices without using GPS and mobile communication channels, even when turned off . Although it was stated that
... it built the feature on a unique encryption system carefully designed to prevent exactly that sort of tracking — even by Apple itself
Translation: [Find my] uses a unique cryptosystem designed to prevent tracking [by other people], including Apple.
Examples of relevant attack vectors
Airdrop
This technology allows you to exchange files between Apple devices without an Internet connection. Each time you "share" the device sends a hash of your phone to SHA256. Thus, having created a database of phone numbers (hash: phone number), you can get quite efficiently catching phones in crowded places ... and send personalized messages to their owners via iMessage (you can get the owner’s name through TrueCaller or from the device’s name). Profit for stores is more than obvious: sending spam to everyone passing by.
Getting Wi-Fi Passwords
When connected to an Apple Wi-Fi network, the device sends a broadcast request, and an Apple-friendly device can help you access the network if the user wants it. If you get 3 bytes of hashes of one employee and, when trying to connect to the corporate network, make a Broadcast with the received data, then perhaps the other employee will be very kind and, seeing a familiar name in the request, will share the password with you.
How it works
BLE packet analysis
By modifying the scripts from the py-bluetooth-utils package, you can view the sniffer of BLE traffic. Apple uses ADV_IND messages to send device status.
Advertise package structure
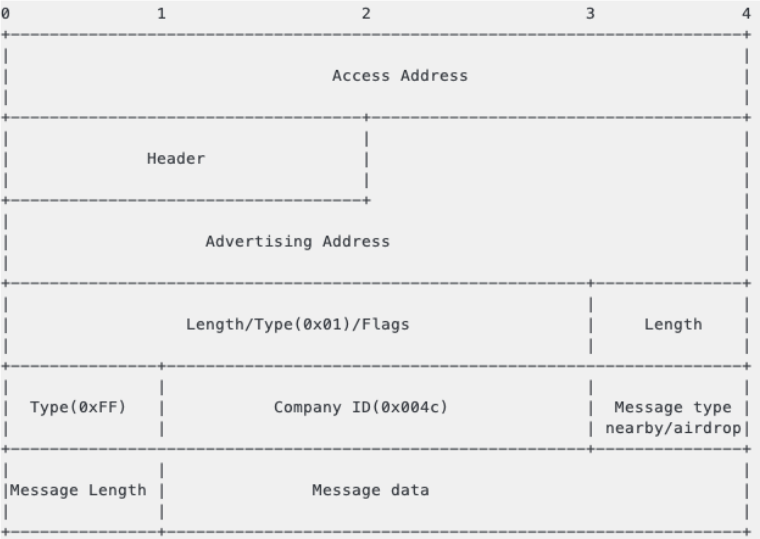
Nearby Messages
Example message types:
0x05 - Airdrop
0x07 - Airpods
0x10 - Nearby
0x0b - Watch Connection
0x0c - Handoff
0x0d - Wi-Fi Settings
0x0e - Hotspot
0x0f - Wi-Fi Join Network
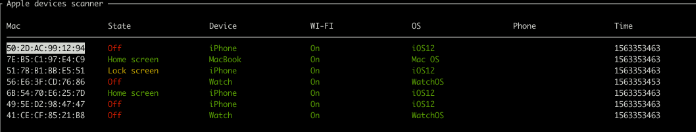
Also from Nearby packages you can get the statuses:
0x0b - Home screen
0x1c - Home screen
0x1b - Home screen
0x11 - Home screen
0x03 - Off
0x18 - Off
0x09 - Off
0x13 - Off
0x0a - Off
0x1a - Off
0x01 - Off
0x07 - Lock screen
0x17 - Lock screen
0x0e - Calling
0x5b - Home screen
0x5a - Off
As a result, you can create a simple BLE packet analyzer:
Wifi
When trying to connect to Wi-Fi from device A, a packet of the following structure is sent containing the first three bytes from the SHA256 hashes of AppleID (5-7 bytes), phone number (8-11 bytes), email (12-14 bytes):

Presumably, Apple devices hashed all contacts and compared with those received in the advertise package. When device B receives a packet with matching hashes of contacts, device B will offer a network connection password to device A.
If you generate a table of hashes of phone numbers for a specific region (about several million), then for the first 3 bytes of the hash you can get a collision of the order of several tens of numbers per hash. There are two ways to check the correctness of numbers:
- Some numbers can be excluded by checking them through the HLR ( HLR Lookup - Front Page - Index ).
- Since the number must be tied to AppleID, you can check through iMessage.
In any case, the obtained set of numbers will allow deanonymizing the owner quite effectively (for example, further using social engineering methods).
Airdrop
Apple AirDrop has three privacy settings:
- Receiving Off.
- Contacts Only.
- Everyone.
When AirDrop starts, a packet of the following structure is sent, containing two bytes of AppleID hashes, email and phone number:

At the same time, AirDrop is used only to initiate the transfer; for the data transfer itself, a peer2peer connection via Wi-Fi (AWDL - Apple Wireless Direct Link) is used.
During authentication, the sender sends the sender's record data to verify the privacy settings of the recipient. This message contains the full SHA256 hash of the sender. Thus, an attacker can respond to all other AirDrop BLE requests, receiving full hashes of numbers.
AirDrop operation scheme:

Summarizing
Only part of the information leakage that is possible using BLE is considered. At the moment, it is difficult to call this a vulnerability, rather, a poorly thought out implementation of the new ecosystem of Apple. What, in principle, they themselves stated:
Apple warns that it's still a somewhat simplified version of the Find My protocol, and that the system is still subject to change before it's actually released in MacOS Catalina and iOS 13 later this year. ©
Wired
Translation: Apple warned that a simplified version of Find My protocol is currently being used and is due to be updated in future releases towards the end of the year.
At the moment, there is no way to prevent data leaks other than turning off Bluetooth. Moreover, this behavior is typical of iOS versions 10.3.1 and higher (including iOS 13 beta). Older devices (up to iPhone 6s) also use this functionality, but with a limited number of messages, possibly to save battery power.
References
GitHub - hexway / apple_bleee: Apple BLE research
Apple bleee. Everyone knows What Happens on Your iPhone - hexway
All Articles