Analytic note. Review of the order of the Ministry of Energy of the Russian Federation of November 6, 2018 N 1015
The authors
K.E. Polezhaev, Analyst
A.A. Zavedenskaya, Assistant Analyst
List of abbreviations used
AWP - Workstation
ASUTP - Automated process control system
BDU - Danger Data Bank
IB - Information Security
ME - Firewall
NDV - Undocumented (Undeclared) Opportunities
Software - Software
SRZI - Information Security Tools
SUMiD - System for remote monitoring and diagnostics of the main technological equipment
FSB of Russia - Federal Security Service of the Russian Federation
FSTEC of Russia - Federal Service for Technical and Export Control of the Russian Federation
Introduction
This Analytical Note contains an overview of Order No. 1015 of the Ministry of Energy of the Russian Federation dated November 6, 2019 published on the official Internet portal of legal information on February 18, 2019 “On approval of requirements for basic (mandatory) functions and information security of electric power facilities during the creation and subsequent operation of the territory of the Russian Federation of systems for remote monitoring and diagnostics of power equipment ”(Registered on February 15, 2019 No. 53815) (hereinafter referred to as the Order of the Ministry of Energy). The order takes effect after six months from the date of its official publication, i.e. since August 18, 2019.
In the electric power industry, in technological processes of production and transmission of electricity and heat, automated process control systems (hereinafter referred to as process control systems) are actively used. Automated process control systems can integrate with remote monitoring and diagnostics systems (hereinafter - SUMiD) of the technical condition of the main equipment of electric power facilities, which requires measures to ensure the safety of these systems. The order establishes organizational and functional requirements for ensuring the information security of the SUMiD, namely the security of its software components, hardware infrastructure, built-in information protection tools and ensuring security control. It also establishes the requirements for ensuring IS SUMiD at the stages of the life cycle and certification.
1. General Provisions
The Remote Monitoring and Diagnostics System (SUMiD) is a hardware-software complex that provides the process of remote monitoring and control of the state of the main technological equipment of an electric power facility, diagnosing and predicting changes in the technical condition of the main technological equipment based on the collected data received from data collection systems installed on technological equipment, and not affecting the normal mode of equipment / facility. For example, the indicated type of systems may include: a monitoring and diagnostic system "Monitoring and control system for transformer equipment" of the company "Inter", software from General Electric "On-Site Monitor" (OSM).
The requirements of the Order of the Ministry of Energy are established with respect to the basic functions of the SUMiD and the information security of electric power facilities during the creation and subsequent operation of the SUMiD in the Russian Federation. It can be concluded that the requirements apply to the Electricity Subjects that operate at the electric power facilities of the SUMiD. Due to the fact that information security requirements are imposed at the stage of creating a SUMiD, it is logical that electric power entities using a third-party SUMiD will try to assign part of the requirements of the Order of the Ministry of Energy to organizations that develop a SUMiD.
The subjects of the electric power industry are persons operating in the electric power industry, including the production of electric, thermal energy and power, the purchase and sale of electric energy and power, the supply of energy to consumers, the provision of electric power transmission services, operational dispatch control in the electric power industry, and the sale of electric power (capacity), the organization of the sale of electric energy and power.
Objects of the electric power industry - property objects that are directly used in the process of production, transmission of electric energy, operational dispatch control in the electric power industry, and marketing of electric energy, including electric grid facilities. The objects in the Order of the Ministry of Energy refer to those objects on the sites of which certain basic technological equipment functions, with SUMiD installed on this equipment and having certain basic functions.
The main technological equipment is equipment, the violation or termination of which leads to loss of control of the electric power facility, an irreversible negative change in the parameters of its functioning, or a significant decrease in the safety of the electric power facility.
According to the Order of the Ministry of Energy, the main technological equipment includes:
2. Basic functions and main components of the SUMiD
The order of the Ministry of Energy determined the basic (basic) functions of the SUMiD:
Based on the wording from the Order, the Ministry of Energy remains unclear whether the system that does not remotely control the main technological equipment should be classified as a SUMiD. Specialists of UTSB LLC sent a request to the Ministry of Energy of Russia to clarify the issue of the basic functions of the SUMiD. In response to a request, the Ministry of Energy of Russia clarifies that the requirements of the Order of the Ministry of Energy apply both to systems that carry out only technological monitoring and to systems that monitor and remotely control the main technological equipment.
Table 1 shows the software and hardware components that may be part of the SUMiD, according to the Order of the Ministry of Energy.
Table 1. Software and hardware components of the SUMiD
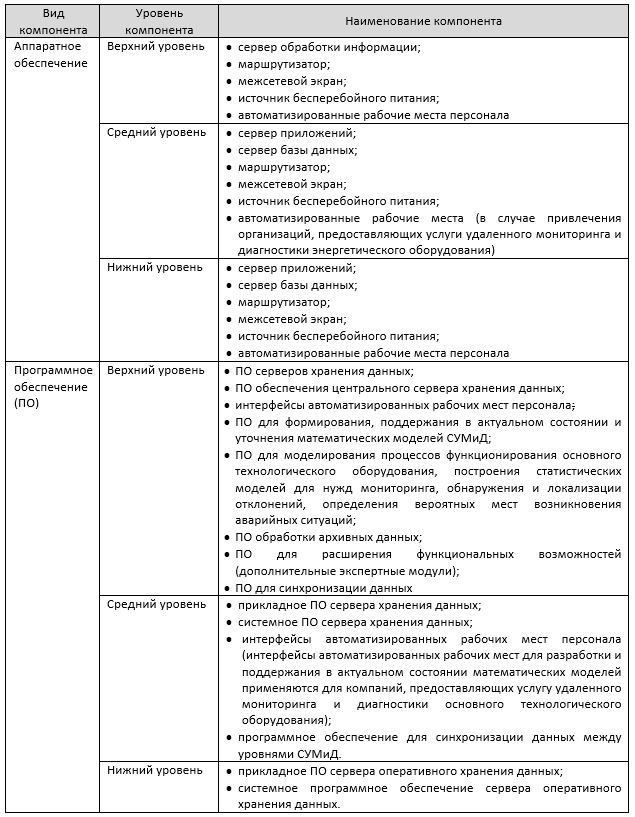
According to the Order of the Ministry of Energy, the Electricity Subject may use in SUMiD an incomplete set of software and hardware components from the above list. Also, the subject of the electric power industry may use other software and hardware components. However, the software and hardware of the SUMiD must be approved by the Electricity Subject in the form of a list of equipment and software approved for use.
3. Organizational requirements for ensuring IS SUMiD
Within the framework of organizational requirements, measures are established to organize the provision of information security by the Electricity Subject, as well as primary measures necessary for such an organization. The Ministry of Energy of Russia clarifies that the Electricity Subject can transmit the requirements of the Order of the Ministry of Energy to organizations participating in the implementation of the life cycle stages of the SUMiD by introducing measures and measures to ensure information security in the Terms of Reference.
Personnel access to the SUMiD software should be implemented through identification and authentication procedures. To enter a user account, a password policy must be approved and configured that meets the minimum requirements listed in table 2.
Table 2. Password Policy Requirements
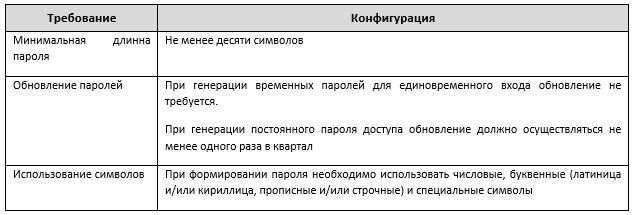
For personnel access to the SUMiD software, the Electricity Entity must provide access control rules that meet the following minimum requirements:
To maintain the composition of the hardware configuration of the SUMiD, the Electricity Entity must perform the following procedures:
The order of the Ministry of Energy of Russia did not establish the requirement for mandatory testing of the operability of software updates that ensure information security. Nevertheless, the “lack of testing or simplified software testing” vulnerability is part of the List of basic Vulnerabilities vulnerabilities necessary to analyze Vulnerabilities and to create a threat model for Vulnerabilities (Appendix 2 to the Order of the Ministry of Energy).
The subject of the electric power industry should take a number of the following measures:
After the segmentation procedure is completed, the Electricity Entity must determine the information security management processes of the SUMiD.
Personal server firewalls (hereinafter referred to as ME) should be enabled for server equipment and workstations for personnel of the Electricity Subject performing the functions of managing a set of technical means of information protection, information and telecommunication infrastructure of the SUMiD. Personal MEs should provide blocking of network access, not provided for by the functioning of the SUMiD. Passwords for access to software and relevant anti-virus protection tools with updates must also be set.
The subject of the electric power industry should check the conformity of the built-in means of information security protection with the goals of information security, which include:
The subject of the electric power industry must carry out the following set of measures:
The power industry entity should categorize the SUMiD in accordance with the Federal Law of July 26, 2017 No. 187- “On the Safety of Critical Information Infrastructure of the Russian Federation” in accordance with the Decree of the Government of the Russian Federation of 08.02.2018 No. 127 “On Approving the Rules for Categorizing Objects of Critical Information Infrastructure of the Russian Federation , as well as a list of indicators of the criteria for the significance of the objects of critical information infrastructure of the Russian Federation ”and ensured compliance normative legal acts based on the results of categorization.
Categorization of SUMiD by the Electricity Subject may cause difficulties in cases where the SUMiD is not the property of the Electricity Subject. In most cases, monitoring and diagnostics of the state of technological equipment is provided to the Electricity Subject as a service, and the SUMiD is supported by the organization - the SUMiD developer.
Information protection measures should be applied at all stages (stages) of creating the SUMiD defined by GOST 34.601-90 “Information technology. Set of standards for automated systems. Automated systems are in the making. ” Since the Order of the Ministry of Energy does not impose responsibility for ensuring information security, the UTSSB LLC experts consider it possible to indicate the organization-participants of each stage as responsible for ensuring information security at all stages (stages) of creating a SUMiD.
4. Requirements for ensuring IS SUMiD at the stages of the life cycle
During the creation and subsequent operation of SUMiD, the function of technological monitoring of the state of the main technological equipment of electric power facilities, in terms of data collection, storage and transmission (data processing centers), should be carried out through the data collection, storage and transmission infrastructure located in the Russian Federation. When transmitting data via a public communication network, information protection means (hereinafter referred to as SRZI) must be applied that have passed conformity assessment on the basis of the requirements of Federal Law of December 27, 2002 No. 184- On Technical Regulation. Conformity assessment of information protection means on the basis of the requirements of Federal Law of December 27, 2002 No. 184- "On Technical Regulation" is carried out in the form of certification of information protection means.
It should be noted that this requirement does not apply to the data processing infrastructure. Therefore, the function of technological monitoring of the state of the main technological equipment in terms of processing technological data can be carried out outside the Russian Federation.
In the case of using special software and / or a software module with a remote control function in the SUMiD, a check should be carried out for them no lower than at level 4 of the absence of NDV control.
The subject of the electric power industry should develop and approve a model of threats and an intruder for the SUMiD. To model IS threats, the FSTEC Russia Threat Data Bank should be used, as well as other available sources and the results of assessing the probability of the vulnerabilities of the SUMiD components being realized. When modeling threats, the sources of threats, typical vulnerabilities, objects of influence, destructive actions in relation to objects of the QMS are to be described.
Based on the generated model of information security threats, the SUMiD is developing an information security policy that includes the functional requirements for information security of the SUMiD.
In the Order of the Ministry of Energy, the concept of “functional requirements” is not defined, and the basic set of functional requirements for information security of the SUMiD is not given, on the basis of which the Electricity Subject could form its own set of functional requirements. According to the specialists of UTSB LLC, as well as on the basis of the Draft Order of the Ministry of Energy No. 1015, the functional requirements are formed on the basis of the document “GOST R ISO / IEC 15408-2-2013. Information Technology (IT). Security methods and tools. Criteria for assessing the security of information technology. Part 2. Functional safety components ”(hereinafter - GOST R ISO / IEC 15408-2-2013). Functional requirements are imposed on the object of assessment and include functional classes consisting of functional families and components. The subject of evaluation in the context of the Order of the Ministry of Energy will be the SUMiD.
Functional classes include:
A detailed description of the functional classes of their families and components is given in GOST R ISO / IEC 15408-2-2013.
To confirm the compliance of the SUMiD and its security subsystem with the Requirements established by the Order of the Ministry of Energy, the SUMiD and its security subsystems are subject to mandatory certification in accordance with the "Requirements for the protection of information not constituting state secrets contained in state information systems", approved by order of the FSTEC of Russia dated 11.02. 2013 No. 17. The introduction of the SUMiD and its safety subsystem should be carried out only after receiving the certificate of conformity of the SUMiD. The Ministry of Energy of Russia confirms that certification is subject to both the data collection server installed at the production facilities of the Electric Power Subjects and the data processing server of the SUMiD of service organizations.
Based on this, it should be concluded that the SRHI included in the SUMiD must be certified in accordance with the Federal Law of December 27, 2002 No. 184- “On Technical Regulation” (Clause 11 of the Requirements for the Protection of Information Not Composing a State Secret Contained in government information systems established by Order of the FSTEC of Russia dated 02.11.2013 No. 17).
It should be noted that in the case of placing a segment that processes technological information outside the Russian Federation, it is impossible to certify a segment of processing technological information for compliance with the requirements for the protection of information that is not a state secret contained in state information systems approved by the order of the FSTEC of Russia dated 11.02. 2013 No. 17.
It is also difficult to use the cryptographic information protection means that have been certified in accordance with the Federal Law of December 27, 2002 No. 184- On Technical Regulation in the processing information segment located outside the Russian Federation due to regulation by the Federal Security Service Licensing, Certification and State Secret Protection Center Russia import into the customs territory of the Eurasian Economic Union and the territory of the Russian Federation and export of encryption (cryptographic) means outside their borders.
To ensure the security system of the SUMiD, the Electricity Entity must comply with the requirements established by chapters III, IV and V of the order of the FSTEC of Russia dated December 21, 2017 No. 235.
The information security of SUMiD, which are significant objects of the critical information infrastructure of the Russian Federation, should be provided by the Electricity Subject in accordance with the Requirements for ensuring the security of significant objects of critical information infrastructure of the Russian Federation, approved by Order of the FSTEC of Russia dated 25.12.2017 No. 239 and with the Requirements for the creation of significant security systems objects of critical information infrastructure of the Russian Federation and their functioning Niya, approved by Order FSTEC Russia from 21.12.2017 №235.
As a result, if, based on the results of categorization, it was concluded that there is no need to assign the SUMiD a category of significance, then the requirements for software and hardware used to ensure the safety of significant objects of critical information infrastructure still remain mandatory, namely, the requirements for the use of SRI certified. Similarly, with the requirements for the functioning of the security system in terms of the organization of work to ensure the safety of significant objects of critical information infrastructure. According to these requirements, for the critical information infrastructure objects, planning and development of security measures should be carried out, implementation (implementation) of these measures, security status monitoring should be provided, and security improvements should be carried out.
findings
K.E. Polezhaev, Analyst
A.A. Zavedenskaya, Assistant Analyst
List of abbreviations used
AWP - Workstation
ASUTP - Automated process control system
BDU - Danger Data Bank
IB - Information Security
ME - Firewall
NDV - Undocumented (Undeclared) Opportunities
Software - Software
SRZI - Information Security Tools
SUMiD - System for remote monitoring and diagnostics of the main technological equipment
FSB of Russia - Federal Security Service of the Russian Federation
FSTEC of Russia - Federal Service for Technical and Export Control of the Russian Federation
Introduction
This Analytical Note contains an overview of Order No. 1015 of the Ministry of Energy of the Russian Federation dated November 6, 2019 published on the official Internet portal of legal information on February 18, 2019 “On approval of requirements for basic (mandatory) functions and information security of electric power facilities during the creation and subsequent operation of the territory of the Russian Federation of systems for remote monitoring and diagnostics of power equipment ”(Registered on February 15, 2019 No. 53815) (hereinafter referred to as the Order of the Ministry of Energy). The order takes effect after six months from the date of its official publication, i.e. since August 18, 2019.
In the electric power industry, in technological processes of production and transmission of electricity and heat, automated process control systems (hereinafter referred to as process control systems) are actively used. Automated process control systems can integrate with remote monitoring and diagnostics systems (hereinafter - SUMiD) of the technical condition of the main equipment of electric power facilities, which requires measures to ensure the safety of these systems. The order establishes organizational and functional requirements for ensuring the information security of the SUMiD, namely the security of its software components, hardware infrastructure, built-in information protection tools and ensuring security control. It also establishes the requirements for ensuring IS SUMiD at the stages of the life cycle and certification.
1. General Provisions
The Remote Monitoring and Diagnostics System (SUMiD) is a hardware-software complex that provides the process of remote monitoring and control of the state of the main technological equipment of an electric power facility, diagnosing and predicting changes in the technical condition of the main technological equipment based on the collected data received from data collection systems installed on technological equipment, and not affecting the normal mode of equipment / facility. For example, the indicated type of systems may include: a monitoring and diagnostic system "Monitoring and control system for transformer equipment" of the company "Inter", software from General Electric "On-Site Monitor" (OSM).
The requirements of the Order of the Ministry of Energy are established with respect to the basic functions of the SUMiD and the information security of electric power facilities during the creation and subsequent operation of the SUMiD in the Russian Federation. It can be concluded that the requirements apply to the Electricity Subjects that operate at the electric power facilities of the SUMiD. Due to the fact that information security requirements are imposed at the stage of creating a SUMiD, it is logical that electric power entities using a third-party SUMiD will try to assign part of the requirements of the Order of the Ministry of Energy to organizations that develop a SUMiD.
The subjects of the electric power industry are persons operating in the electric power industry, including the production of electric, thermal energy and power, the purchase and sale of electric energy and power, the supply of energy to consumers, the provision of electric power transmission services, operational dispatch control in the electric power industry, and the sale of electric power (capacity), the organization of the sale of electric energy and power.
Objects of the electric power industry - property objects that are directly used in the process of production, transmission of electric energy, operational dispatch control in the electric power industry, and marketing of electric energy, including electric grid facilities. The objects in the Order of the Ministry of Energy refer to those objects on the sites of which certain basic technological equipment functions, with SUMiD installed on this equipment and having certain basic functions.
The main technological equipment is equipment, the violation or termination of which leads to loss of control of the electric power facility, an irreversible negative change in the parameters of its functioning, or a significant decrease in the safety of the electric power facility.
According to the Order of the Ministry of Energy, the main technological equipment includes:
- steam turbines with an installed capacity of 5 MW or more and related auxiliary equipment involved in the main technological process, but not producing or converting electrical energy), designed to ensure the operability of the main technological equipment (hereinafter - auxiliary equipment);
- steam (energy) boilers providing steam to steam turbines with an installed capacity of 5 MW or more, and related auxiliary equipment;
- hydraulic turbines with an installed capacity of 5 MW or more and related auxiliary equipment;
- gas turbines with a unit capacity of more than 25 MW and related auxiliary equipment;
- power transformers with voltage of 110 kV and higher, with a capacity of more than 63 MVA and related auxiliary equipment.
2. Basic functions and main components of the SUMiD
The order of the Ministry of Energy determined the basic (basic) functions of the SUMiD:
- technological monitoring of the state of the main technological equipment;
- remote control of the main technological equipment with the possibility of remote exposure to the main technological equipment in order to change the parameters of its functioning or its shutdown, using special software and (or) the software module SUMiD.
Based on the wording from the Order, the Ministry of Energy remains unclear whether the system that does not remotely control the main technological equipment should be classified as a SUMiD. Specialists of UTSB LLC sent a request to the Ministry of Energy of Russia to clarify the issue of the basic functions of the SUMiD. In response to a request, the Ministry of Energy of Russia clarifies that the requirements of the Order of the Ministry of Energy apply both to systems that carry out only technological monitoring and to systems that monitor and remotely control the main technological equipment.
Table 1 shows the software and hardware components that may be part of the SUMiD, according to the Order of the Ministry of Energy.
Table 1. Software and hardware components of the SUMiD

According to the Order of the Ministry of Energy, the Electricity Subject may use in SUMiD an incomplete set of software and hardware components from the above list. Also, the subject of the electric power industry may use other software and hardware components. However, the software and hardware of the SUMiD must be approved by the Electricity Subject in the form of a list of equipment and software approved for use.
3. Organizational requirements for ensuring IS SUMiD
Within the framework of organizational requirements, measures are established to organize the provision of information security by the Electricity Subject, as well as primary measures necessary for such an organization. The Ministry of Energy of Russia clarifies that the Electricity Subject can transmit the requirements of the Order of the Ministry of Energy to organizations participating in the implementation of the life cycle stages of the SUMiD by introducing measures and measures to ensure information security in the Terms of Reference.
Personnel access to the SUMiD software should be implemented through identification and authentication procedures. To enter a user account, a password policy must be approved and configured that meets the minimum requirements listed in table 2.
Table 2. Password Policy Requirements

For personnel access to the SUMiD software, the Electricity Entity must provide access control rules that meet the following minimum requirements:
- Account personnel must be created for the personnel of the system with respect to the QMS & A, in accordance with the requirements of the password policy;
- settings of personnel accounts in relation to SUMiD must be approved by the Electricity Subject;
- built-in accounts (non-personalized accounts) must be disabled.
To maintain the composition of the hardware configuration of the SUMiD, the Electricity Entity must perform the following procedures:
- providing support for technological processes with a finite set of software, the list of which must be approved;
- providing organizational and technical measures for recording security events for all software included in the SUMiD;
- definition and adjustment of update parameters (time interval) of software providing information security;
- organization and updating of the archive of design and operational documentation SUMiD;
- approval of the composition of the SUMiD hardware equipment, as well as the software used for the hardware infrastructure in the form of a list of equipment and software approved for use.
The order of the Ministry of Energy of Russia did not establish the requirement for mandatory testing of the operability of software updates that ensure information security. Nevertheless, the “lack of testing or simplified software testing” vulnerability is part of the List of basic Vulnerabilities vulnerabilities necessary to analyze Vulnerabilities and to create a threat model for Vulnerabilities (Appendix 2 to the Order of the Ministry of Energy).
The subject of the electric power industry should take a number of the following measures:
- the segmentation of the SUMiD hardware infrastructure was carried out with the mandatory allocation of a minimum set of segments (the segment of data collection, storage and transmission; the operation segment; the maintenance segment; system software);
- Rules for determining and approving the composition of the SUMiD hardware infrastructure and providing control over the SUMiD hardware infrastructure have been developed;
- in the places where the SUMiD hardware infrastructure is located, physical access control is provided and regulated.
After the segmentation procedure is completed, the Electricity Entity must determine the information security management processes of the SUMiD.
Personal server firewalls (hereinafter referred to as ME) should be enabled for server equipment and workstations for personnel of the Electricity Subject performing the functions of managing a set of technical means of information protection, information and telecommunication infrastructure of the SUMiD. Personal MEs should provide blocking of network access, not provided for by the functioning of the SUMiD. Passwords for access to software and relevant anti-virus protection tools with updates must also be set.
The subject of the electric power industry should check the conformity of the built-in means of information security protection with the goals of information security, which include:
- audit of information security events;
- providing cryptographic protection;
- discrete access for system users;
- control of network interaction;
- passing security attributes;
- identification and authentication;
- security configuration
- Establishing trusted connections
- availability of information.
The subject of the electric power industry must carry out the following set of measures:
- control of design documentation and initial state of software;
- protection against unauthorized access to information on technical and technological parameters of the main technological equipment;
- formation and storage of reporting of these activities.
- As a basic set of information security controls for the SUMiD, the Electricity Subject must perform the following measures:
- approve information security policy;
- distribute responsibilities within the organization to ensure information security;
- provide education and training for information security personnel;
- provide education and training for personnel in maintaining information security regimes;
- organize processes for reporting cases of violation of protection;
- apply antivirus protection;
- protect data and design documentation;
- monitor compliance with an approved information security policy.
The power industry entity should categorize the SUMiD in accordance with the Federal Law of July 26, 2017 No. 187- “On the Safety of Critical Information Infrastructure of the Russian Federation” in accordance with the Decree of the Government of the Russian Federation of 08.02.2018 No. 127 “On Approving the Rules for Categorizing Objects of Critical Information Infrastructure of the Russian Federation , as well as a list of indicators of the criteria for the significance of the objects of critical information infrastructure of the Russian Federation ”and ensured compliance normative legal acts based on the results of categorization.
Categorization of SUMiD by the Electricity Subject may cause difficulties in cases where the SUMiD is not the property of the Electricity Subject. In most cases, monitoring and diagnostics of the state of technological equipment is provided to the Electricity Subject as a service, and the SUMiD is supported by the organization - the SUMiD developer.
Information protection measures should be applied at all stages (stages) of creating the SUMiD defined by GOST 34.601-90 “Information technology. Set of standards for automated systems. Automated systems are in the making. ” Since the Order of the Ministry of Energy does not impose responsibility for ensuring information security, the UTSSB LLC experts consider it possible to indicate the organization-participants of each stage as responsible for ensuring information security at all stages (stages) of creating a SUMiD.
4. Requirements for ensuring IS SUMiD at the stages of the life cycle
During the creation and subsequent operation of SUMiD, the function of technological monitoring of the state of the main technological equipment of electric power facilities, in terms of data collection, storage and transmission (data processing centers), should be carried out through the data collection, storage and transmission infrastructure located in the Russian Federation. When transmitting data via a public communication network, information protection means (hereinafter referred to as SRZI) must be applied that have passed conformity assessment on the basis of the requirements of Federal Law of December 27, 2002 No. 184- On Technical Regulation. Conformity assessment of information protection means on the basis of the requirements of Federal Law of December 27, 2002 No. 184- "On Technical Regulation" is carried out in the form of certification of information protection means.
It should be noted that this requirement does not apply to the data processing infrastructure. Therefore, the function of technological monitoring of the state of the main technological equipment in terms of processing technological data can be carried out outside the Russian Federation.
In the case of using special software and / or a software module with a remote control function in the SUMiD, a check should be carried out for them no lower than at level 4 of the absence of NDV control.
The subject of the electric power industry should develop and approve a model of threats and an intruder for the SUMiD. To model IS threats, the FSTEC Russia Threat Data Bank should be used, as well as other available sources and the results of assessing the probability of the vulnerabilities of the SUMiD components being realized. When modeling threats, the sources of threats, typical vulnerabilities, objects of influence, destructive actions in relation to objects of the QMS are to be described.
Based on the generated model of information security threats, the SUMiD is developing an information security policy that includes the functional requirements for information security of the SUMiD.
In the Order of the Ministry of Energy, the concept of “functional requirements” is not defined, and the basic set of functional requirements for information security of the SUMiD is not given, on the basis of which the Electricity Subject could form its own set of functional requirements. According to the specialists of UTSB LLC, as well as on the basis of the Draft Order of the Ministry of Energy No. 1015, the functional requirements are formed on the basis of the document “GOST R ISO / IEC 15408-2-2013. Information Technology (IT). Security methods and tools. Criteria for assessing the security of information technology. Part 2. Functional safety components ”(hereinafter - GOST R ISO / IEC 15408-2-2013). Functional requirements are imposed on the object of assessment and include functional classes consisting of functional families and components. The subject of evaluation in the context of the Order of the Ministry of Energy will be the SUMiD.
Functional classes include:
- security audit;
- communication;
- cryptographic support;
- user data protection;
- identification and authentication;
- security management;
- privacy
- protection of safety functions of the subject of assessment;
- resource usage;
- access to the subject of assessment;
- trusted route / channel.
A detailed description of the functional classes of their families and components is given in GOST R ISO / IEC 15408-2-2013.
To confirm the compliance of the SUMiD and its security subsystem with the Requirements established by the Order of the Ministry of Energy, the SUMiD and its security subsystems are subject to mandatory certification in accordance with the "Requirements for the protection of information not constituting state secrets contained in state information systems", approved by order of the FSTEC of Russia dated 11.02. 2013 No. 17. The introduction of the SUMiD and its safety subsystem should be carried out only after receiving the certificate of conformity of the SUMiD. The Ministry of Energy of Russia confirms that certification is subject to both the data collection server installed at the production facilities of the Electric Power Subjects and the data processing server of the SUMiD of service organizations.
Based on this, it should be concluded that the SRHI included in the SUMiD must be certified in accordance with the Federal Law of December 27, 2002 No. 184- “On Technical Regulation” (Clause 11 of the Requirements for the Protection of Information Not Composing a State Secret Contained in government information systems established by Order of the FSTEC of Russia dated 02.11.2013 No. 17).
It should be noted that in the case of placing a segment that processes technological information outside the Russian Federation, it is impossible to certify a segment of processing technological information for compliance with the requirements for the protection of information that is not a state secret contained in state information systems approved by the order of the FSTEC of Russia dated 11.02. 2013 No. 17.
It is also difficult to use the cryptographic information protection means that have been certified in accordance with the Federal Law of December 27, 2002 No. 184- On Technical Regulation in the processing information segment located outside the Russian Federation due to regulation by the Federal Security Service Licensing, Certification and State Secret Protection Center Russia import into the customs territory of the Eurasian Economic Union and the territory of the Russian Federation and export of encryption (cryptographic) means outside their borders.
To ensure the security system of the SUMiD, the Electricity Entity must comply with the requirements established by chapters III, IV and V of the order of the FSTEC of Russia dated December 21, 2017 No. 235.
The information security of SUMiD, which are significant objects of the critical information infrastructure of the Russian Federation, should be provided by the Electricity Subject in accordance with the Requirements for ensuring the security of significant objects of critical information infrastructure of the Russian Federation, approved by Order of the FSTEC of Russia dated 25.12.2017 No. 239 and with the Requirements for the creation of significant security systems objects of critical information infrastructure of the Russian Federation and their functioning Niya, approved by Order FSTEC Russia from 21.12.2017 №235.
As a result, if, based on the results of categorization, it was concluded that there is no need to assign the SUMiD a category of significance, then the requirements for software and hardware used to ensure the safety of significant objects of critical information infrastructure still remain mandatory, namely, the requirements for the use of SRI certified. Similarly, with the requirements for the functioning of the security system in terms of the organization of work to ensure the safety of significant objects of critical information infrastructure. According to these requirements, for the critical information infrastructure objects, planning and development of security measures should be carried out, implementation (implementation) of these measures, security status monitoring should be provided, and security improvements should be carried out.
findings
- The considered Order of the Ministry of Energy approves a set of measures to ensure the information security of the SUMiD, which affect the functioning of the main technological equipment of the Electricity Subjects. The order takes effect on August 15, 2019.
- The order of the Ministry of Energy classifies SUMiD as critical information infrastructure facilities and requires that the SUMiD be categorized in accordance with Decree of the Government of the Russian Federation of 08.02.2018 No. 127 “On approval of the rules for categorizing objects of critical information infrastructure of the Russian Federation, as well as a list of indicators of criteria for the importance of objects of critical information infrastructure of the Russian Federation”. Subsequently, the Electricity Industry Entities must implement the requirements established by Order of the FSTEC of Russia dated December 21, 2017 No. 235 and Order of the FSTEC of Russia dated December 25, 2017 No. 239 for critically important facilities that, although they are similar to the requirements of the Order, do not exclude responsibilities for their implementation. If in relation to the SUMiD it is concluded that there is no need to assign a category of significance, then only the requirements of the Order of the Ministry of Energy will be binding.
- Compliance with the requirements of the Order of the Ministry of Energy should help to reduce risks for critical facilities that are associated with the SUMiD, in terms of minimizing the threat of remote management of objects or violating the integrity of information on the basis of which management decisions are made.
- The means of information protection used in the SUMiD must be certified in accordance with the Federal Law of December 27, 2002 No. 184- On Technical Regulation. Regarding the built-in means of information protection, the Subject must verify compliance with the information security objectives.
- The Order of the Ministry of Energy contains a description of the threat model for the SUMiD adapted for the electric power industry. The threat data base of the FSTEC of Russia and the results of assessing the probability of the implementation of vulnerabilities of the SUMiD components are used as input data for threat modeling. Also, in the Order of the Ministry of Energy, a list of basic attacks on SUMiD is carried out when threats to information security are implemented, which must be taken into account when analyzing vulnerabilities; list of basic vulnerabilities, basic destructive actions and classification for the intruder model.
- If SUMiD has the functionality of remote control of the main technological equipment, then for such software and / or the SUMiD software module, a check should be performed no lower than at level 4 of the control of the absence of undeclared capabilities.
- The main requirements of the Order of the Ministry of Energy are:
- certification of the SUMiD for compliance with the requirements established by order of the FSTEC of Russia dated 11.02.2013 No. 17;
- the use in the SUMiD of information protection means certified in accordance with the requirements of the Federal Law of December 27, 2002 No. 184- On Technical Regulation.
All Articles