annotation
In modern companies, an internal intruder is a significant part of security threats. To close the leak problem, the use of DLP systems is recommended. This article proposes to consider three DLP systems and choose the best one from them.
Introduction
Currently, companies pay much attention to external security threats, often ignoring potential dangers within the enterprise. Any employee can cause a leak of confidential information, whether it is a deliberate act or negligence, and cause much more damage to the company. Therefore, there is a need for comprehensive protection of information from leaks, and the most appropriate solution to this problem is the use of DLP systems.
A DLP system is a set of software and hardware tools that ensure information is protected from leaks by intercepting and then analyzing and blocking the data stream that crosses the perimeter in the direction “outward” or circulates inside the protected corporate network.
In this article, DLP systems of three domestic software developers in the field of information security will be considered:
- Searchinform KIB - a product from Searchinform;
- "Falcongaze SecureTower" - a software solution to prevent information leakage, developed by the company "Falcongaze";
- InfoWatch Traffic Monitor is the flagship of the InfoWatch group of companies.
Comparison of these products will reveal the most suitable system for protection against internal threats.
Study
Consider the interface of Searchinform KIB

On the “Search” tab, you can configure the search and interception of data by templates, keywords and phrases from the system, correspondence in social networks and instant messengers. "Current activity" allows you to see the user's screen in real time. “File Auditor” collects information about files and folders on a PC with the possibility of shadow copying. Using the "Center Profile", you can create a psychological profile of the user based on his activity. On the “Report” tab, reporting on events of interest is configured.
Next, consider the Falcongaze Secure Tower console.

The user’s console includes such tabs as “Information Search”, which searches for intercepted data, “Combined Search”, “Monitoring File Systems”, which allows you to search for various files on workstations. There are also tools for monitoring user activity on the network and monitoring the user's workplace using interception of audio and video streams. On the “Reporting Center” tab, reports are implemented according to various criteria. Security Center configures security policies. In addition, the console contains tools for working with documentation during investigations in the corresponding tab “Center for Investigations”.
Finally, explore the main InfoWatch Traffic Monitor window.
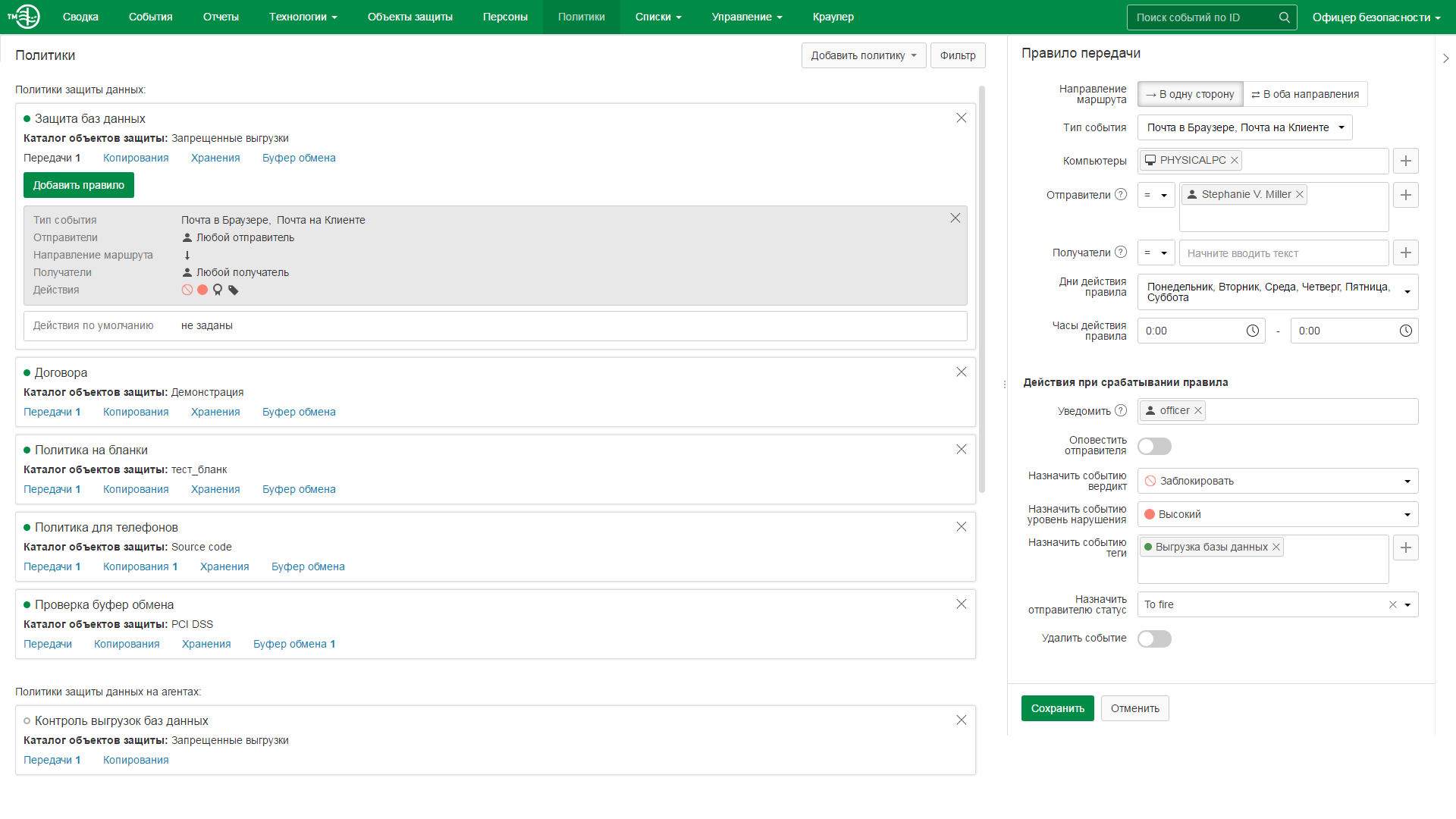
The Summary section contains statistical information about the violation and violators. In the "Events" a list of interception objects and means for working with them is presented. The “Reports” tab allows you to view visualized statistics of intercepted objects. The Technologies section contains editable reference books of categories and terms, text objects, reference documents, letterheads, seals, unloading from databases, as well as a list of predefined graphic objects. User information can be found on the Persons tab. The “lists” section contains editable directories of tags, web resources, statuses, perimeters and an uneditable list of files. You can configure the actions that the System performs in response to the actions of persons and workstations in the "Policies" section.
Functional Comparison
Next, we will conduct a comparative analysis of the functionality of DLP systems based on general information provided by manufacturers in the public domain. The comparison results are shown in the table below.
| Serchinform KIB | Falcongaze SecureTower | Infowatch traffic monitor | |
|---|---|---|---|
| Email (Controlled Protocols) | SMTP, POP3, IMAP, MAPI, NNTP, S / MIME, Web Mail Control | SMTP, POP3, IMAP, MAPI, Web Mail Control | SMTP, POP3, IMAP, MAPI, S / MIME, Web Mail Control |
| Messengers and social networks | All popular instant messengers, also sites on the Mamba platform; VK, Facebook, etc. | All popular instant messengers; VK, Facebook, etc. | All popular instant messengers; VK, Facebook, etc. |
| Cloud service and storage control | Yes | Yes | Yes |
| Encrypted Traffic Control | Yes | Yes | Yes |
| Print control | Yes | Yes | Yes |
| Controlling and blocking external media | Yes | Yes | Yes |
| Audio and video monitoring | Yes | Yes | Yes |
| Screenshots of the current screen | Yes | Yes | Yes |
| Live screen view | Yes | Yes | Not |
| Keylogger | Yes | Yes | Yes, in a separate console |
| Security policy setting | Yes, in a separate console | Yes | Yes |
| Supported file formats (text, images, archives) | Common text formats, including Microsoft Office, PDF, RTF;
All popular image formats. Popular archive formats: | Common formats, including Microsoft Office, OpenOffice, PDF;
Popular graphic formats; Archive formats GZIP, ZIP, TAR, TIFF | Microsoft Office, PDF, RTF, CHM;
All popular image formats; Popular archive formats |
The study showed that the functionality of all three products is generally similar, there are necessary tools for analyzing incidents in computer systems and networks.
Conclusion
All three DLP systems have broad capabilities in protecting the system from internal threats, so the best one in this study was selected based on the ease of setup and the convenience of working with the system.
In Searchinform KIB, security policies and incidents are configured in separate modules. "InfoWatch Traffic Monitor" is the most cumbersome solution, because additional functionality, for example, monitoring user activity, is implemented as an independent product, and there is no centralized management.
In "Falcongaze SecureTower" all the necessary functionality is available in one console, which makes this system the most convenient and preferred in the framework of the study.