 Photo: TASS
Photo: TASS
Probably for security reasons, the headache was to separate server roles. Start multiple machines to physically separate the domain controller and the file server.
Fortunately, virtualization came to our aid, and now several services can work in isolation from each other, which, for security reasons, cannot work on the same server. Virtualization brought a lot of convenience, deploying virtual machines from one template saves specialists time, and physically, all in one box with powerful hardware.
There are fewer machines, and there are more and more servers, even for me, to “just see” two domain controllers were formed, a file server, a server for Java applications and a bunch of web servers, so let's talk about how to efficiently manage Windows servers, without lifting your left hand from the coffee.
- Using Powershell!
Of course yes, but ... no. The product is positioned as a convenient tool for managing a giant infrastructure. It is clear that this is not entirely true, for such cases there are Powershell ISE and scripts, so I would like to consider really useful user cases. If you have your own experience that you want to share, we can add it to this article.
TL; DR
Windows Admin Center is better for managing stock components. Currently, only RSAT can manage installed roles.
Using WAC, you can improve the security of your infrastructure if you use it as a gateway.
A summary table of that, he knows how and does not know how:
System management
| Wac | RSAT | |
|---|---|---|
| Component management | Yes | Yes |
| Registry Editor
| Yes
| Not
|
| Network management
| Yes
| Yes
|
| Event Viewer
| Yes
| Yes
|
| Shared Folders
| Yes
| Yes
|
| Drive management
| Yes
| Only for servers with a GUI
|
| Task Scheduler
| Yes
| Yes
|
| Device management
| Yes
| Only for servers with a GUI
|
| File management
| Yes
| Not
|
| user management
| Yes
| Yes
|
| Group management
| Yes
| Yes
|
| Certificate management
| Yes
| Yes
|
| Updates
| Yes
| Not
|
| Uninstall programs
| Yes
| Not
|
| System monitor
| Yes
| Yes
|
Role management
| Wac
| RSAT
| |
|---|---|---|
| Advanced thread protection | TEXT | Not |
| Windows defender
| TEXT
| Yes
|
| Containers
| TEXT
| Yes
|
| AD Administrativ Center
| TEXT
| Yes
|
| AD Domain and Trusts
| Not
| Yes
|
| AD sites and services
| Not
| Yes
|
| DHCP
| TEXT
| Yes
|
| DNS
| TEXT
| Yes
|
| DFS Manager
| Not
| Yes
|
| GPO Manager
| Not
| Yes
|
| IIS Manager
| Not
| Yes
|
Preview - installing beta versions of components for WAC, is not part of the assembly. It is not necessary to list everything, because literally all components are controlled only using RSAT.
Nuances
Powershell in the Windows Admin Center does not have its own scripting environment similar to Powershell ISE.
Windows Admin Center does not support Powershell below 5.0, on older machines you must install the new Powershell if you want to use it.
The main disadvantage of Windows Admin Center in micro instances is the consumption of server RAM. It creates four sessions of 50-60 megabytes each, and each session remains even after the Windows Admin Center closes.
The same problem with Powershell via Enter-PSSession, it also creates a new session, and if you just close the terminal window, a session weighing 70 megabytes will remain on the remote server if you do not close it before exiting using Exit-PSSession or Remove-Pssession.
When using the Windows Admin Center, you will have to put up with this, it will take away about 170 megabytes of RAM, RSAT does not suffer from this.
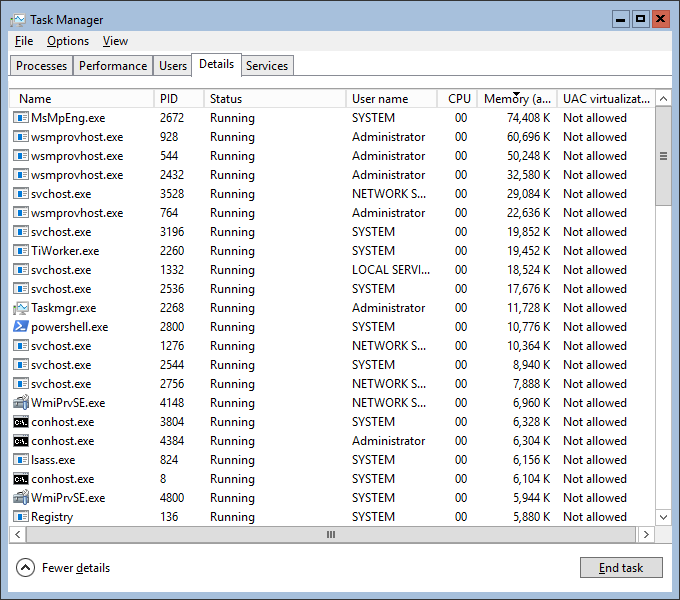
(See wsmprovhost.exe)
Simplify the work
Maximum management convenience is achieved if your workstation on which the WAC is installed is in the domain. It takes the credentials of the user who is logged in, connecting to the servers is carried out with one click.
You can import the server list using a txt file, listing server names by line feed, as in RSAT.
What is also pleasing, earlier, in order to integrate the Server Core virtual machine into AD, you had to do it through sconfig, which means you need direct access to its screen. In the case of hosting, I had to do all this through VNC. Now, when you go to the main page, you can click "Change Computer ID" and enter into the domain.
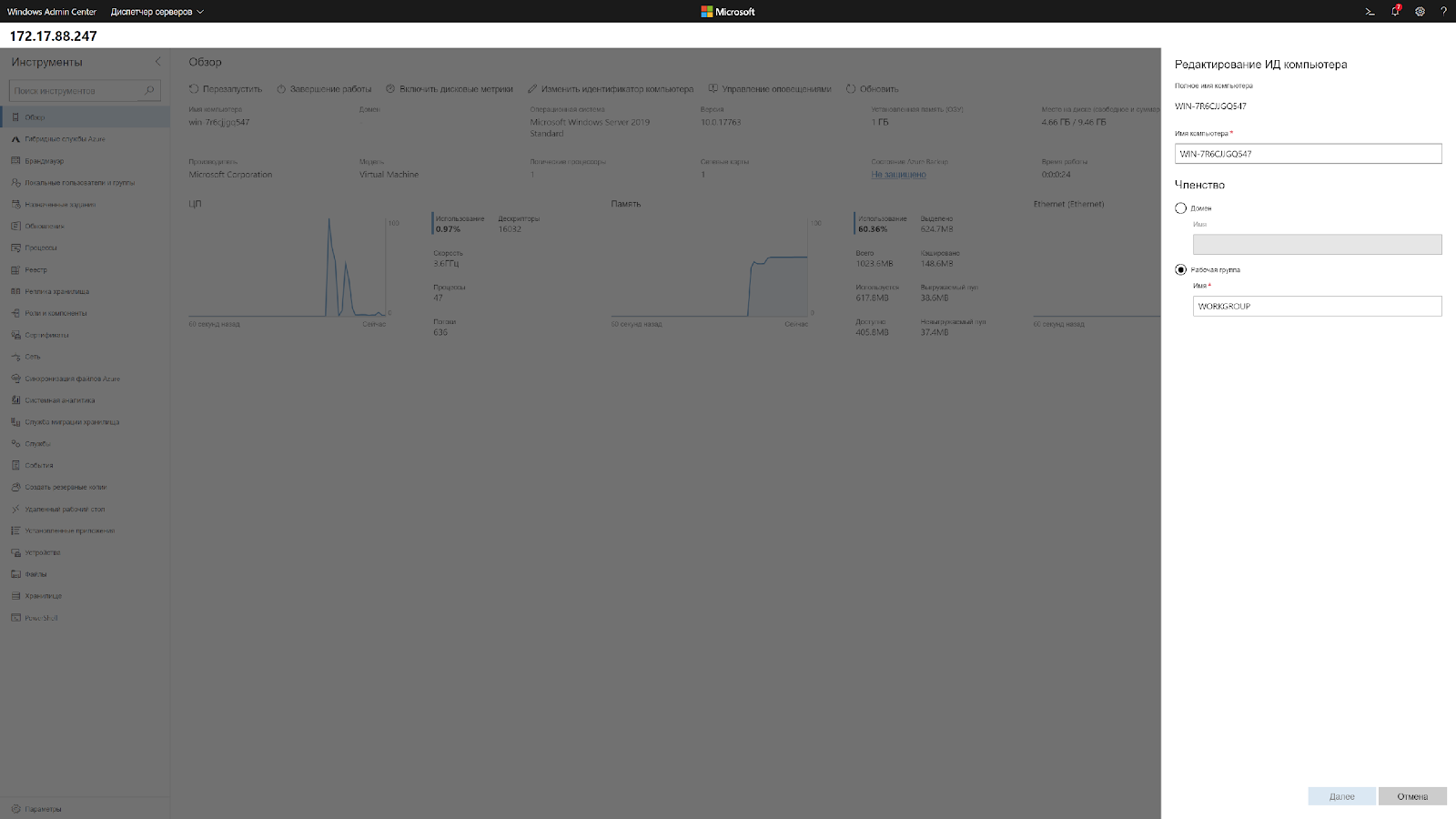
By the way, to enter Windows Server 2019 into the domain, Sysprep is no longer required, because Sysprep also had to be completed through VNC.
To change the network settings now you need to make two clicks. Connect to the server and change.
It comes out as fast as through WinRM, with just one hand.

Increase security
There are currently four types of deployment. Local, as a gateway, installation on one of the production servers and as part of a cluster.
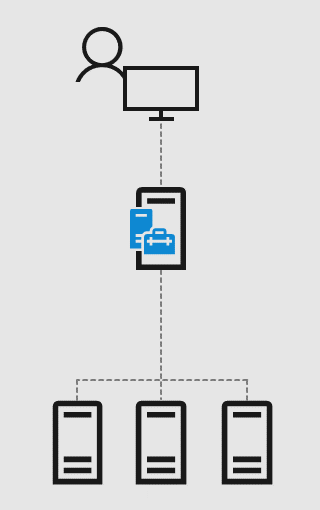
* Image from Microsoft website
Installing as a gateway, on a separate server, is the most secure and recommended option. This is an analogue of a VPN scheme when access to management is available only from a specific IP address or network section.
Agree, it’s much more convenient to keep the vidos and memes on one tab and the Windows Admin Center on the other than to completely lose the connection to YouTube due to the entrance to the secure network.
How to secure all your N servers? Using the following script:
## ## $servers = Get-Content -Path .\Servers.txt ## ## $rules = Get-Content -Path .\Rules.txt ## IP WAC ## $gate = "1.1.1.1" $MySecureCreds = Get-Credential foreach ($server in $servers.Split("`n")) { foreach ($line in $rules.Split("`n")) { Invoke-Command -ComputerName $server -ScriptBlock { Set-NetFirewallRule -Name $Using:line -RemoteAddress $Using:gate } -Credential $MySecureCreds } } # , RULES.txt# RemoteDesktop-UserMode-In-TCP RemoteDesktop-UserMode-In-UDP WINRM-HTTP-In-TCP WINRM-HTTP-In-TCP-PUBLIC # , SERVERS.txt# 1.1.1.1, 1.1.1.2, 1.1.1.3
This script will change the standard firewall rules in such a way that you can use RDP and WinRM only from a specific IP address, you will need to organize secure access to the infrastructure.
Powershell in Windows Admin Center does not have its own scripting environment similar to Powershell ISE, you can only call ready-made scripts.

By the way, this is what RDP looks like on Windows Server Core.

conclusions
Currently, Windows Admin Center is not able to replace RSAT, however, it already contains functions that RSAT does not have. Old snap-ins are added, which are not so convenient for managing through the browser.
The development priority is strange, the most actively added are the functions integrated with Azure, hosting from Microsoft, instead of really useful functions.
Unfortunately, for now, you can only manage all the functions of Windows Server with convenience by connecting to it via RDP.
Despite all the disadvantages, the Windows Admin Center has its own SDK, with which you can write your own modules and manage your own software through it, which will one day make it better than RSAT.
