 Once again looking at the functionality of the cryptoarmpkcs utility, I noticed that it, mainly working with cryptographic tokens / smartcards PKCS # 11, does not have a built-in functionality for their configuration. We are talking about initializing tokens , setting PIN codes, etc. And it was decided to add this functionality. The first step was to expand the functionality of the TclPKCS11 package, whose library is written in C.
Once again looking at the functionality of the cryptoarmpkcs utility, I noticed that it, mainly working with cryptographic tokens / smartcards PKCS # 11, does not have a built-in functionality for their configuration. We are talking about initializing tokens , setting PIN codes, etc. And it was decided to add this functionality. The first step was to expand the functionality of the TclPKCS11 package, whose library is written in C.
New TclPKCS11 Features
Three new features appeared in the package:
::pki::pkcs11::inittoken <handle> <slotId> <SO-pin> <label for token>
::pki::pkcs11::inituserpin <handle> <slotId> <SO-pin> <USER-pin>
::pki::pkcs11::setpin <handle> <slotId> <so | user> <oldpin> <newpin>
The first function :: pki :: pkcs11 :: inittoken is to initialize the token. It must be borne in mind that if this function is applied to a working token, then all objects on it will be destroyed.
The second function :: pki :: pkcs11 :: inituserpin is for initializing a user PIN (USER PIN).
After the initial initialization of the user PIN-code, it must immediately be changed to the PIN-code, which will be used in the future, and keep it, like the SO-PIN, away from prying eyes. For security purposes, tokens, as a rule, do not allow you to log in to them with the initial PIN code.
To change the PIN codes, the third function is used, namely :: pki :: pkcs11 :: setpin. This feature allows you to change both a user PIN and SO-PIN.
It should also be borne in mind that tokens, as a rule, do not allow to restore the original SO-PIN (default). But if you re-initialize the token, you will again get the default SO-PIN. The implementation of the TclPKCS11 package can be viewed on github .
Now, having on hand, the TclPKCS11 package with new functions, it was not difficult to implement a GUI for these functions:

Training Tokens
But before using them, let's pay attention to the fact that another button “Create Tokens” has been added to the utility functionality.
This is due to the fact that not everyone has a PKCS # 11 hardware token with support for Russian cryptography, and if so, it is scary to use it for educational purposes. And just so that the utility could be easily used for educational purposes, first of all, the “Create Tokens” button appeared. By clicking on this button, you will see instructions on how to get either software or cloud tokens:

These tokens implement the latest TK-26 recommendations for PKCS # 11 v.2.40.
We will briefly review how to get a cloud token. Download the necessary distribution package, unpack it if necessary, and run it. If we do not have a cloud token, then we will receive the following message:

Since we don’t have a cloud token yet, we click the “Register in the cloud” button:
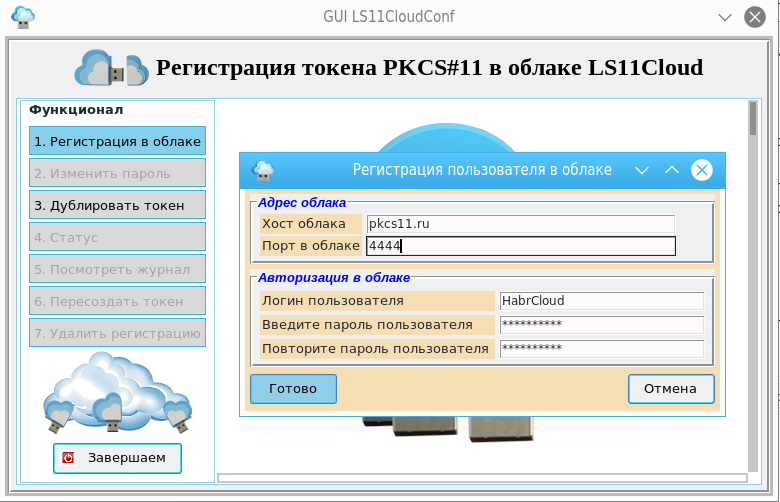
After filling in the fields, click the “Finish” button:

Since we are talking primarily about training, we can save a password to access the cloud (but not the token) in the workplace:
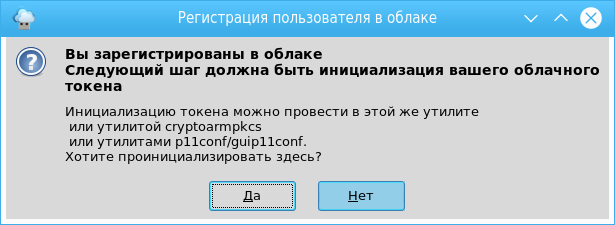
Token Initialization
Now that we are registered in the cloud, we exit the guils11cloud_conf utility and return to the cryptoarmpkcs utility to configure the cloud token. It should be noted here that the cloud token library will be saved in the ls11cloud folder created in the user's home directory. It is this library that will need to be selected as the PKCS # 11 library for the cloud token. After choosing a library, you can see the supported cryptographic mechanisms:

We return to initializing the cloud token by clicking the "Token Configuration" button. We select the operation “Initialization of the token”, fill in the fields (remember that the default SO-PIN is 87654321) and click the button “Perform operation”:

All token is ready to work. But do not forget to change the SO-PIN and periodically change the user PIN. Using a similar scheme, you can create a software token. Those interested can try:

Now we can store our personal certificates on them, sign documents, do everything that was written about in this series of articles.
Upcoming innovations in PKI / PKI
On November 7, 2019, the State Duma adopted on first reading amendments to the law “On Electronic Signatures”. This amendment applies to all organizations and individual entrepreneurs, as the rules for issuing electronic signatures will change.
If I understood everything correctly, legal entities and individual entrepreneurs can receive qualified certificates only at the Federal Tax Service, and financial organizations at the Central Bank of the Russian Federation. And only using these certificates can it be set
Enhanced Qualified Electronic Signature (Cades-XLT1).
Certification centers (CAs) accredited by the Ministry of Telecom and Mass Communications will be able to issue such certificates only to individuals.
Moreover, the requirements for CAs will change significantly: equity should be increased from 7 million to 500 million - 1 billion, the amount of insurance liability increases from 30 million to 300-500 million rubles, the accreditation period is reduced from 5 years to 3 years.
The bill has already sparked sharp criticism. The main complaints are that the changes will lead to the closure of the vast majority of commercial CAs, require significant budgetary expenditures to expand and maintain the capacities of the CA Federal Tax Service, as well as the concentration of all types of risks on a single infrastructure, which will become a convenient target for cyber attacks.
There is one more amendment - the obligation to sign company documents not by one but by two enhanced qualified signatures at the same time. The head of the organization will have to put on the document the signature of the legal entity and a personal digital signature as an individual.
And here the cryptoarmpkcs utility will be very, very helpful, because its functionality allows you to put several signatures under the document, as well as see who and when signed the document:

PS For those who want to get utilities for the first time, this can still be done here: