
In this article, we will deal with decompiling the MIPS binary in Ghidra and reverse the program written in golang in the IDA.
Part 1 - C, C ++ and DotNet decompile.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
ELF MIPS
Download and check the file.

This is a 32-bit executable file for MIPS architecture processors. To solve this problem we will use Ghidra. Open the hydra, create a new project and add it to our executable file.

Now open the investigated file, and move to the Symbol Tree window. In search, type main to find the entry point of the program.
When you select a function, it immediately opens in the decompiler.

Let's convert the code.
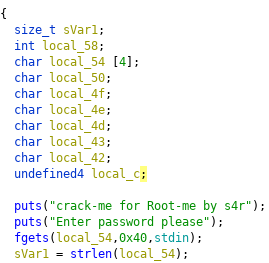
We see that 64 bytes are read into the local_54 variable, let's rename it to input (hotkey L) and make a 64-character char array of it (hotkey Ctrl + L). You can also rename the variable sVar1.

After some conversion, the code began to look a little more beautiful.

We analyze the code. The string we enter should consist of 19 characters. At what position which character should be clear from the code. In this case, from the 8th to the 17th should be the symbol 'i'. We recover, pass the password.
Golang basic
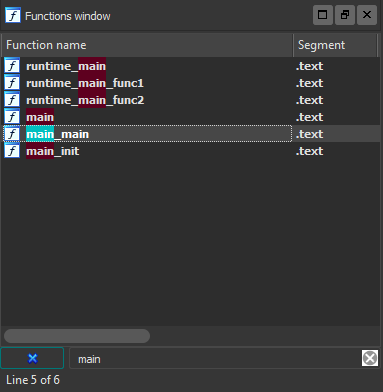
In this assignment, we are provided with an executable file written in Go. You can even find out which version. I throw in the IDA. It should be said right away that the main function is not called main, but called main_main. Therefore, we perform a search by function and go to the real main one.
Let's parse the code. Let's start from the very beginning.
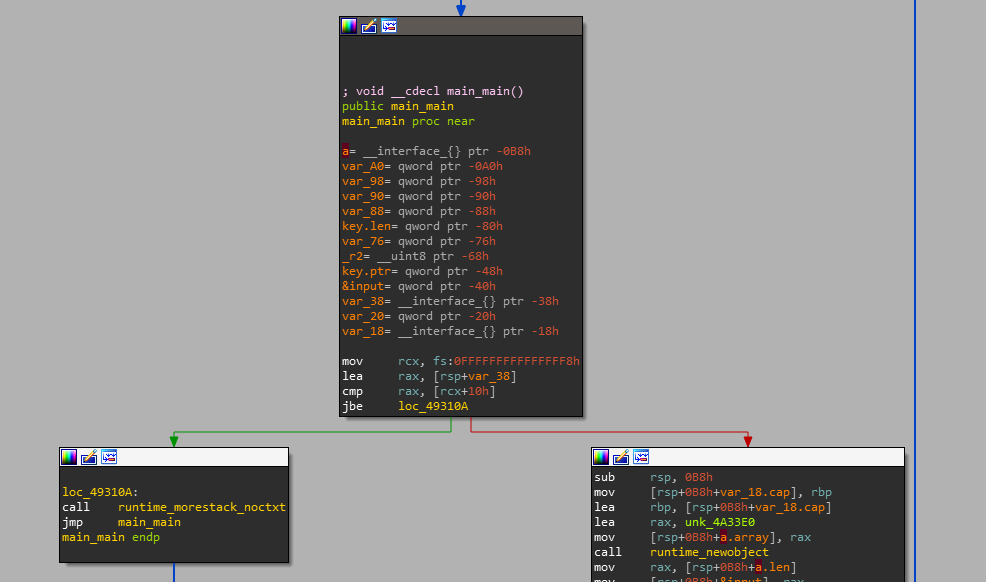
There are definitions of a, key, input. The left block is responsible for completing the main_main function. Consider the left block.
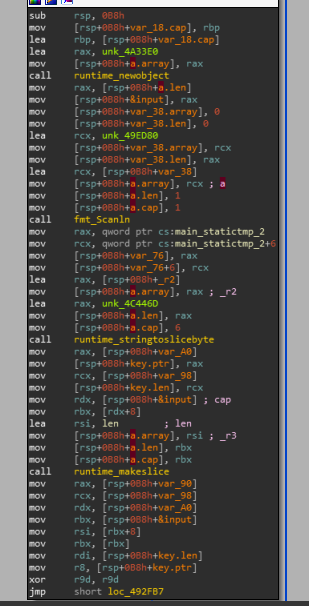
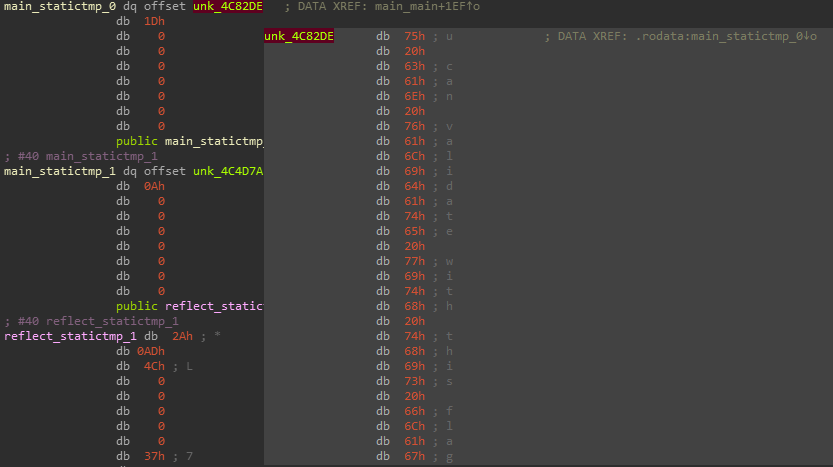
The fmt_Scanln function is designed to read a line from the console. We also observe the main_statictmp_2 data already saved in the program.

Next, the runtime_stringtoslicebyte function is called, according to the code, we can assume that it takes the first 6 bytes from the next line.

Key.ptr will point to the beginning of this slice. Let's see what comes next.

Depending on the comparison of the nullified register r9 and the register rsi, where the length of user input is located. From this we can conclude that r9 will most likely be a counter. Let's take a look at the right block, where control will go, after a sale on the line we entered.
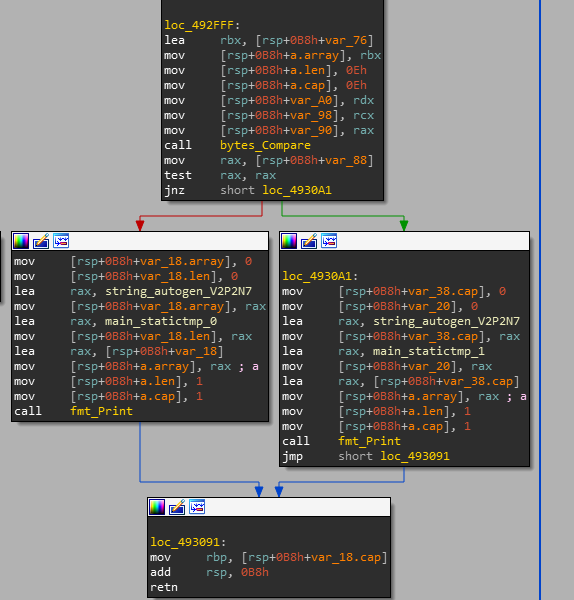
The bytes_Compare function is called, which, depending on the comparison result, displays one of the lines.

We figured out the output of the program, now let's go look at the line breaks (on the left branch).
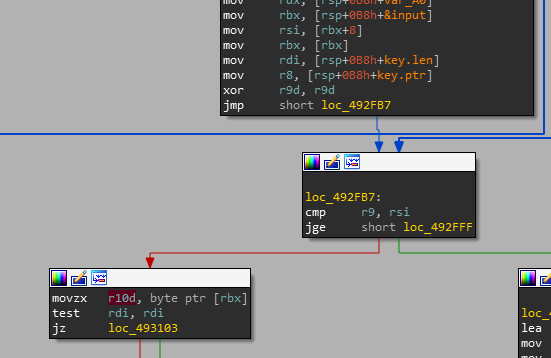
The character from user input is entered into the r10 register, and then there is a bunch of complex code for comparisons to control exceptions like panic divide and panic index. I highlighted the program execution branch.
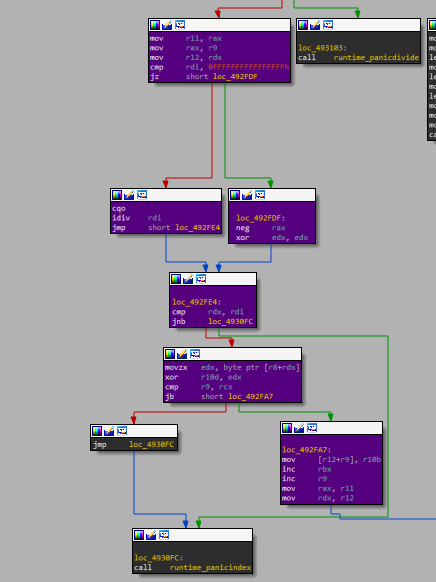
Thus, a byte from a statically specified string is placed in EDX and quarrels with r10, where is the byte from the slice. Next, the counter r9 increases. Two middle adjacent blocks are most likely needed to control the length of the cut.
Let's combine everything together: the entered line is contaminated with a slice and compared with a statically specified line. Let's proxy to find out the correct password.

We get the answer. The complexity of the reverse of Go binaries is that there are complicating factors such as the absence of a null character at the end of lines, the presentation of their types, garbage collector, etc.
That's all for now. To be continued ... You can join us on Telegram . There you can propose your own topics and vote on the choice of topics for the following articles.