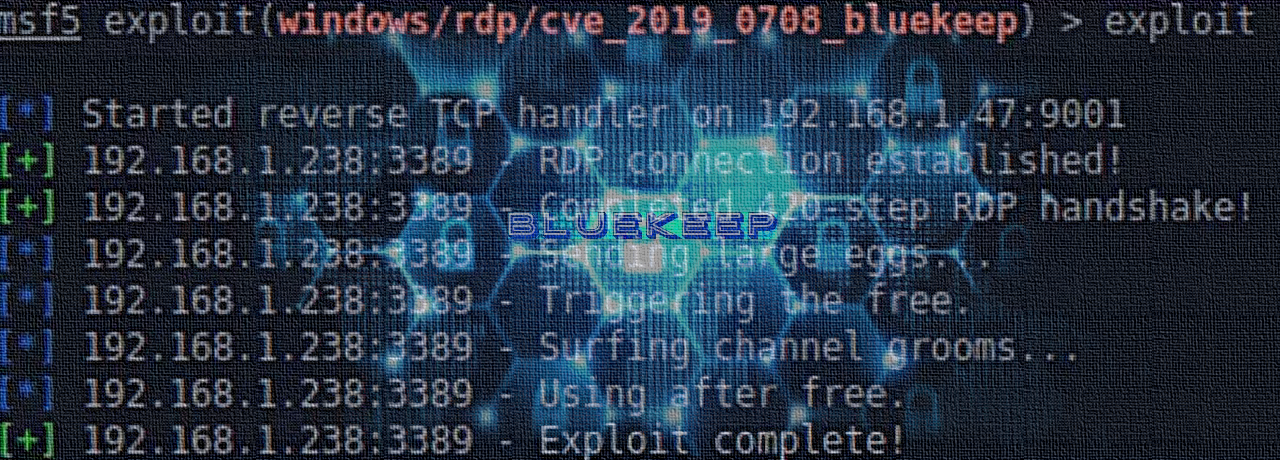
The analysis of the crash dump of RAM allowed to detect traces
a shellcode designed to download and run a cryptominer from a remote server by running a powershell script. At the same time, this shellcode is identical to the shellcode of the BlueKeep module in the Metasploit project.
The following is a general chronology of events related to this vulnerability.
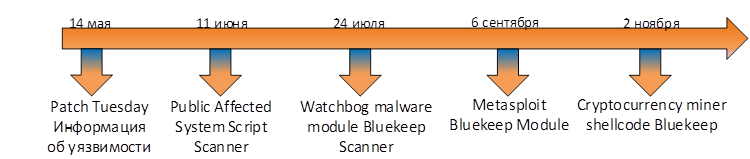
It is worth noting that the activity detected last week is the second well-known attempt by cybercriminals to include code from the public regarding BlueKeep in their projects. Recall that in late July it became known that the Lunix malware Watchbog has a module for scanning systems that are vulnerable to BlueKeep.
Borrowing code from the public, as well as leaving the servers from the RDP Honeypot network to the BSOD state, indicates that at present, attackers trying to infect the servers with the Monero crypto miner do not have a stable exploit and are only trying to hone their skills. Nevertheless, the chronology of events suggests that soon we will see sections of code that operate BlueKeep, as part of a wide variety of malicious families.
Keep in mind that BlueKeep is not the only vulnerability aimed at implementing the RDP protocol. Earlier, we wrote about DejaBlue vulnerabilities (CVE-2019-1181 / 1182), which have much greater potential coverage, since the most current versions of Windows are affected by them.
We strongly recommend that you take an inventory of your company’s published services and follow up on the recommendations we made earlier.