
Following Google, the “ mobile first ” approach was adopted not only by designers, but also by cybercriminals who, in search of benefits, follow the trend: Back in 2016, the share of mobile Internet traffic exceeded desktop traffic . In 2019, mobile user traffic is 52.9% of the total , 5.1 billion people use the Internet from mobile devices, while from desktops - only 4.4 billion. Thus, attacks on mobile devices are becoming more profitable: more users are more likely to make money.
But there is one obstacle in the way of criminals. Mobile device manufacturers are conducting systematic work to improve the security of their products, so breaking a modern smartphone or tablet is not an easy task. In order not to create difficulties for themselves, cybercriminals changed their tactics and redirected attacks to the weak link - the user, using the most effective tactic - phishing.
The combination of the high effectiveness of phishing attacks and the massive use of mobile devices has made mobile phishing one of the most visible threats of our time. Today we’ll talk about the features of mobile phishing, the reasons for the growth of its popularity and high efficiency, and also find out what can be opposed to the tricks of cybercriminals.
What is the value?
The ultimate goal of conducting most of the phishing campaigns is to get paid, and mobile phishing is no exception. Smartphones and tablets provide a lot of opportunities for fraudulent income. Attacking their owners, cybercriminals can:
- Sell stolen personal data on Darknet;
- use stolen private information for blackmail;
- taking control of the device, use it for cryptocurrency mining, as a proxy server or as a participant in the zombie network for a DDoS botnet;
- steal accounts for access to corporate resources, penetrate the company’s network and steal confidential or commercial information;
- forcing him to trick him into installing a program for remote control, stealing money from a bank account ;
- compromise credentials for a banking application and steal money by intercepting SMS / push codes for 2FA and confirming transactions;
- after a user installs a fraudulent application, show him unwanted ads and conduct other malicious activities;
- connect the user with a premium premium subscription to SMS or additional features in the application.
The growing number of mobile gadgets is not the only reason for the spread of the threat of mobile phishing. Consider the features of smartphones that make life easier for the organizers of fraudulent campaigns.
Relatively small screen size
Despite the high and ultra-high resolutions, the physical screen size of most mobile devices does not exceed 6 inches. This makes it difficult to check suspicious URLs and makes it almost impossible to detect punycode attacks related to the use of UTF characters from other alphabets, as well as attacks indicating misspelled domains.
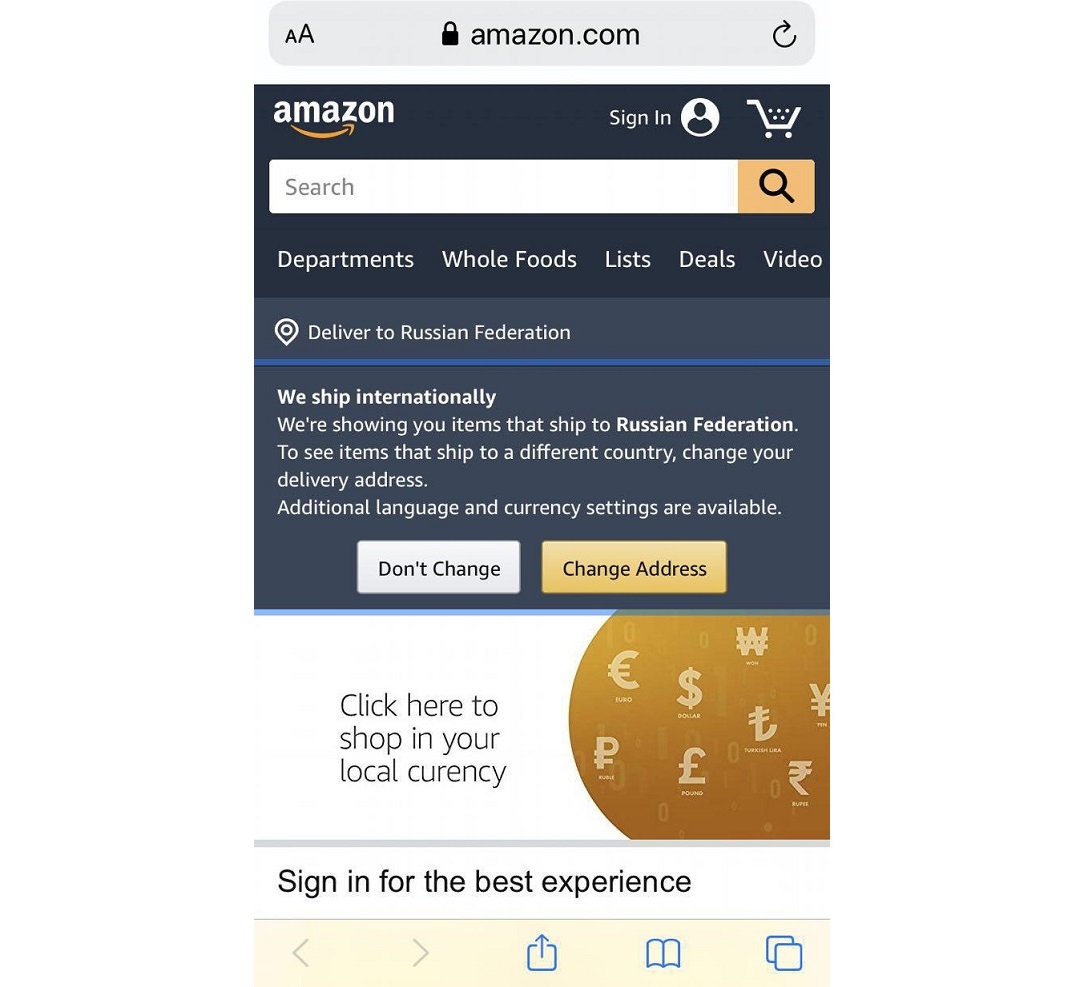
www.amazon.com/home
www.arnazon.com/home
The combination of letters “rn” can be difficult to distinguish from “m” even on a computer screen.
Mobile Browsers
To save space on the gadget’s screen, when scrolling through the site’s page, the address bar is reduced or completely hidden, making the task of recognizing forged URLs impossible.

Alerts
Pop-up messages and sound notifications from instant messengers and email clients, reminders about the birthdays of relatives and friends, that it is time to make another installment on a mortgage, update several applications or respond to a new comment on a photo, etc., etc. , have long become a familiar part of life. At the same time, when they come regularly and in large numbers, the user's attention is scattered: with a large number of notifications, there is no time to read them, the gadget owner has the wrong skill of instant reaction to notifications - in the order of things it starts to wipe another reminder from the screen so that it does not interfere with work. This practice greatly increases the chances of success of a phishing attack.
The trust
A curious fact, mobile device users trust their gadgets more than computer users their laptops and PCs. A gadget, unlike a computer, is something personal, hidden from prying eyes, hidden in a jacket pocket or purse. This is a device for personal use that can only be used by the owner. Unlocking the screen with a password, fingerprint or FaceID enhances trust and creates a false sense of security. After all, manufacturers assure that no one outsider can penetrate the device. However, the problem is that the victims of phishing damage their actions, less critically assessing their consequences when they are confident of invulnerability. In fact, they themselves “let in” scammers.
Variety of attack channels
The main medium for phishing attacks in the corporate environment has become email. That is why most of the security solutions offered to companies are focused on mail services. However, the proliferation of mobile technology, coupled with the growing popularity of the BYOD approach, has significantly changed the landscape of phishing attacks.
According to the Wandera report, 83% of successful mobile phishing attacks occur outside of email . The multibillion-dollar army of WhatsApp, Viber and Facebook Messenger users provides an extensive field of activity for scammers .
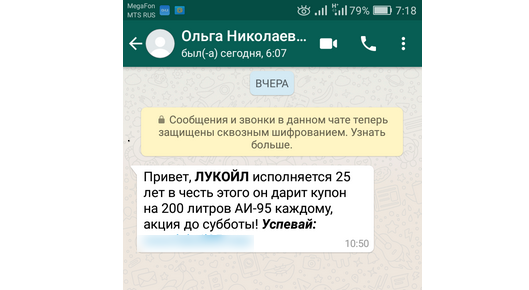

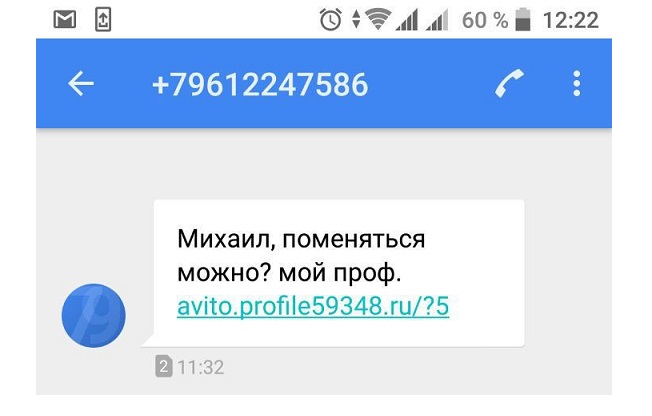
In addition to messengers, phishing messages on mobile devices are successfully distributed via SMS, iMessage, Skype, social networks, games and dating applications. You can use almost any platform to distribute fraudulent messages that allows you to send some text to another user.
Rich functionality
Mobile gadgets have many features that facilitate the penetration and operation of malicious applications. For example, Android apps use a feature called Toast messages. These are the quickly disappearing notifications that appear at the bottom of the screen. They, for example, uses Gmail, informing that the letter is sent.
A feature of Toast messages is that they are displayed on top of the program window.
ToastAmigo , detected by Trend Micro in 2017, used this function to display a huge notification with a fake interface, which hid requests for access to the Android Accessibility service. Users clicked on the buttons of the fake interface, but in reality gave permission to the malicious program.
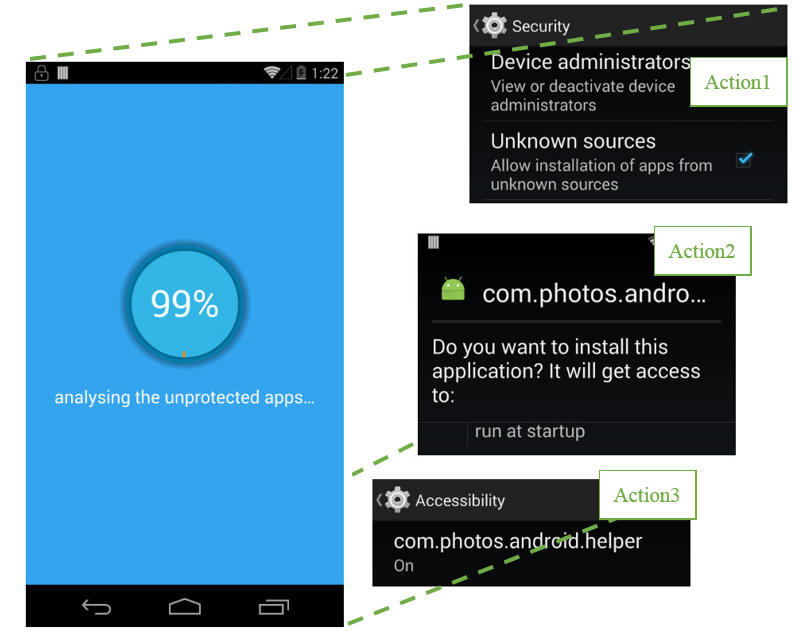
Work ToastAmigo. Source: Trend Micro
Having received the necessary permissions, ToastAmigo installed AmigoClicker on the device, an application that downloads ads in the background and clicks on advertising banners.
Another feature of Android that is popular among cyber fraudsters is related to flaws in the permission system. They were used, for example, by the attack “Cloak & Dagger” (Cloak & Dagger) , which abused application rights. Using the SYSTEM_ALERT_WINDOW and BIND_ACCESSIBILITY_SERVICE functions, a malicious application could display windows that blocked the smartphone’s interface and perform any actions in the background without user confirmation. But most importantly, any application installed from the official Google Play store received these rights.
According to Check Point, flaws in Android permissions were used by 74% of ransomware, 57% of adware malware and at least 14% of bankers .
And this is how Facebook password theft occurs (video): https://www.youtube.com/watch?v=oGKYHavKZ24
Malware Stores
Despite all the checks carried out by official Google and Apple app stores, scammers find ways to add malicious functionality to their designs by disguising them as games, photo-processing programs, and other popular software.
In August 2019, Trend Micro researchers found 85 malicious applications installed on Google Play more than 8 million times.
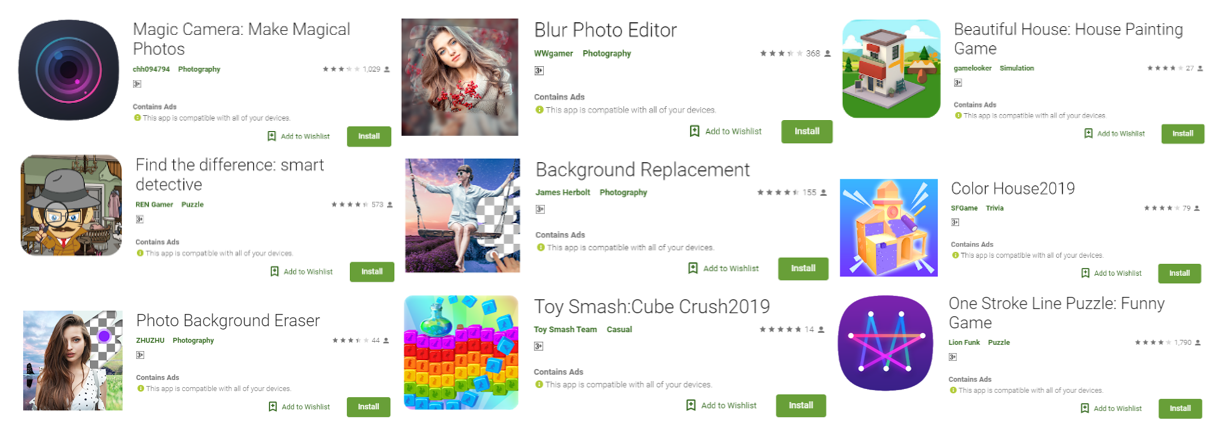
All malicious programs specialize in displaying ads that are difficult to close, and use unique ways to track user behavior.
The author of another malicious collection of 42 Android applications monitored the Google APIs to protect themselves from analysis, and waited 24 minutes before starting to display unwanted ads . This allowed him to bypass the standard automated scan of Android applications, which takes 10 minutes.

A selection of malicious iOS applications of the Indian developer AppAspect Technologies. Source: Wandera
Despite tighter security controls, there are also fraudulent programs in the Apple app store. At the end of October, 17 applications were discovered in the App Store that contained malicious modules for clicks on advertisements and background opening of sites.
How to deal with mobile phishing
Given their huge variety, it is much more difficult to defend against mobile phishing attacks. But here, the recommendations we provide for companies wishing to protect themselves from the compromise of business correspondence , targeted attacks and other types of email fraud will be relevant here.
- Improving user literacy in the field of security: they should be aware of the dangers of the thoughtless use of mobile devices, in particular, following links in messages and installing programs from unverified sources. And if we are talking about devices used by BYOD in labor, it is better to refrain from installing applications that are not necessary for work.
- Training in safe behavior skills: for this, you should contact the companies that provide simulated phishing attacks services and find out if there is a training on combating mobile fraud in the list of their services.
- Installing security solutions on mobile devices: from the list of Trend Micro products, Mobile Security & Antivirus and Enterprise Mobile Security for Android and iOS can be distinguished, as well as the Trend Micro WiFi Protection application for protection when working on public wireless networks.