The motives can be very different: hackers, for example, can be paid by the government or the corporation, and sometimes they are just criminals who want to have fun and make money.
In Russia, the military more and more frightens us with possible cyber attacks on “critical infrastructure facilities” (just to protect against this, at least formally, they passed a law on sovereign Internet).

However, this is not only a horror story. According to Kaspersky, in the first half of 2019, hackers attacked Internet of things devices more than 100 million times - most often using the Mirai and Nyadrop botnets. By the way, Russia in terms of the number of such attacks is only in fourth place (despite the sinister image of “Russian hackers” created by the Western press); in the first three - China, Brazil and even Egypt. The United States is only in fifth place.
So is it possible to successfully repel such attacks? Let's first look at a few well-known cases of such attacks to find the answer to the question of how to secure your devices at least at a basic level.
Bowman Avenue Dam
Bowman Avenue Dam is located in the town of Rye Brook (New York State) with a population of less than 10 thousand people - its height is only six meters, and the width does not exceed five. In 2013, US intelligence agencies spotted malicious software in the dam information system. Then the hackers did not use the stolen data to disrupt the operation of the object (most likely, because the dam was disconnected from the Internet during the repair work).
Bowman Avenue is needed to prevent flooding of areas near the stream during a spill. And there could be no destructive consequences from the dam's failure - in the worst case, the basements of several buildings along the stream would be flooded, but this can not even be called a flood.

Mayor Paul Rosenberg then suggested that hackers might confuse the structure with another large dam of the same name in Oregon. It is used for irrigation of numerous farms, and there malfunctions would cause serious damage to local residents.
It is possible that the hackers simply trained on a small dam, then to arrange a serious invasion of a large hydroelectric power station or any other element of the US energy system.
The attack on Bowman Avenue Dam was recognized as part of a series of banking system hacks that were successfully carried out by seven Iranian hackers throughout the year (DDoS attacks). During this time, the work of 46 largest financial institutions of the country was disrupted, the bank accounts of hundreds of thousands of customers were blocked.
Later, Iranian Hamid Firuzi was charged with a series of hacker attacks on banks and on Bowman Avenue Dam. It turned out that he used the Google Dorking method to search for “holes” in the dam's work (later, the local press brought down a flurry of accusations against Google). Hamid Fizuri was not located in the United States. Since there is no extradition from Iran to the States, hackers have not received any real terms.
2.Free Metro in San Francisco
On November 25, 2016, the message “You have been hacked, all data is encrypted” appeared in all electronic terminals for the sale of public transport tickets in San Francisco. All Windows computers belonging to the City Transport Agency were also attacked. Malicious HDDCryptor software (an encryptor attacking the main boot record of a Windows computer) got to the organization’s domain controller.

HDDCryptor encrypts local hard drives and network files using randomly generated keys, and then overwrites the MBR of the hard drives to prevent systems from loading properly. Equipment, as a rule, becomes infected due to the actions of employees who accidentally open a file trap in an email, then the virus spreads over the network.
Attackers suggested that the local government contact them by mail cryptom27@yandex.com (yes, Yandex). For the key to decrypt all the data, they demanded 100 bitcoins (at that time about 73 thousand dollars). Hackers also suggested decrypting one machine for one bitcoin to prove that recovery is possible. But the government coped with the virus on its own, however, it took more than a day. During the restoration of the entire system, the metro ride was made free.
“We opened the turnstiles as a precaution to minimize the impact of this attack on passengers,” explained municipality spokesman Paul Rose.The criminals also claimed that they had access to 30 GB of internal documents from the San Francisco City Transportation Agency and promised to merge them into the network if the ransom was not paid within 24 hours.
By the way, a year earlier in the same state the Hollywood Presbyterian Medical Center was attacked. Then the hackers were paid 17 thousand dollars to restore access to the hospital's computer system.
3. Dallas emergency alert system
In April 2017, in Dallas at 23:40, 156 emergency sirens were activated to alert the public about emergencies. They could be turned off only two hours later. During this time, the 911 service received thousands of alarming calls from local residents (a few days before the incident, three weak tornadoes went through Dallas, destroying several houses).

An emergency warning system was installed in Dallas in 2007, with sirens supplied by Federal Signal. The authorities did not specify the details of the operation of the systems, but reported that it uses “tonal signals”. Such signals are usually broadcast through the meteorological service using Dual-Tone Multi-Frequency (DTMF) or Audio Frequency Shift Keying (AFSK). These are encrypted commands that were transmitted at a frequency of 700 MHz.
City authorities suggested that the attackers recorded audio signals that were broadcast during the testing of the warning system, and then reproduced them (a classic replay attack). For its implementation, it was enough for hackers to purchase test equipment for working with radio frequencies, it can be purchased without problems in specialized stores.
Experts from the research company Bastille noted that the conduct of such an attack implies that the attackers have well studied the work of emergency city alerts, frequencies, codes.
The mayor of Dallas the next day made a statement that hackers would be found and punished, and all warning systems in Texas would be modernized. However, the culprits were never found.
***
The concept of smart cities is fraught with serious risks. If the megalopolis management system is hacked, attackers will gain remote access to control traffic situations and strategically important city objects.
Risks are also associated with the theft of databases, which include not only information about the entire infrastructure of the city, but also personal data of residents. We must not forget about excessive energy consumption and network congestion - all technologies are tied to communication channels and nodes, including the consumed electricity.
The level of anxiety of owners of IoT devices tends to zero
In 2017, Trustlook conducted a study of the level of awareness of IoT device owners about their security. It turned out that 35% of respondents do not change the default (factory) password before using the device. And more than half of users do not install third-party software to protect against hacker attacks. 80% of owners of IoT devices have never heard of the existence of the Mirai botnet.
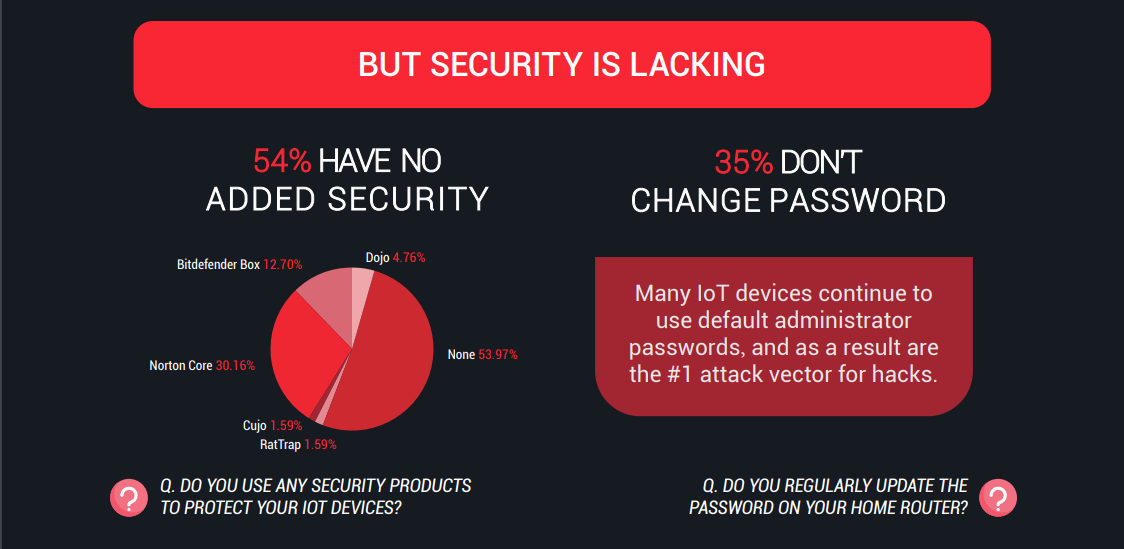
At the same time, with the development of the Internet of things, the number of cyber attacks will only increase. And while companies are being purchased with “smart” devices, forgetting about basic safety rules, cybercriminals are gaining more and more opportunities to make money on careless users. For example, they use networks of infected devices to conduct DDoS attacks or as a proxy server for other malicious actions. And most of these unpleasant incidents can be prevented by following simple rules:
- Change the factory password before using the device.
- Install reliable internet security software on your computers, tablets and smartphones.
- Do your research before you buy. Devices become smart because they collect a lot of personal data. You need to know what type of information will be collected, how it will be stored and protected, whether it is transmitted to third parties.
- Check for firmware updates regularly on the device manufacturer’s website.
- Do not forget to audit the event log (first of all, analysis of all uses of USB ports)