 Last week, hacking of VPN provider NordVPN was widely discussed, as well as a couple of other similar services (in particular, TorGuard was mentioned). The source of information was Twitter , the messages from there were then picked up by the media ( Techcrunch , Habr ). NordVPN and TorGuard published refutations in the wake of these articles: in both cases there was a leak of the private key (in one case - in 2018, in the other the key was stolen back in 2017). What kind of a key it was and what consequences such a leak has (or had in the past) for users - opinions differ. The facts released by NordVPN indicate that the only one of the company's hundreds of servers was compromised, and the key leak did not jeopardize even those clients who connected through the hacked server to the network.
Last week, hacking of VPN provider NordVPN was widely discussed, as well as a couple of other similar services (in particular, TorGuard was mentioned). The source of information was Twitter , the messages from there were then picked up by the media ( Techcrunch , Habr ). NordVPN and TorGuard published refutations in the wake of these articles: in both cases there was a leak of the private key (in one case - in 2018, in the other the key was stolen back in 2017). What kind of a key it was and what consequences such a leak has (or had in the past) for users - opinions differ. The facts released by NordVPN indicate that the only one of the company's hundreds of servers was compromised, and the key leak did not jeopardize even those clients who connected through the hacked server to the network.
The situation is complicated, let's say, by rather aggressive marketing of VPN services with an emphasis on the security of user data. Therefore, such news is extremely sensitive for VPN providers, and they are discussed in social networks with an excessive degree of drama. In a separate NordVPN report on measures to improve the security of the service, the correct conclusion was made: there is no one hundred percent immunity from hacking. This applies to both the VPN providers themselves and the users. And the point here is not what type of VPN is used: commercial, free or your own server with preference and poetesses.
The original Twitter post contains a link to a leaked private key owned by NordVPN, which expired in October 2018. This key, according to NordVPN, was stolen from the hacked server of the company in March 2018. It was one of more than three thousand servers through which VPN service users can redirect their traffic. Again, according to NordVPN, the hoster made a configuration error - the attackers gained access to the client servers through the control panel. Instead of informing customers about this, the hoster silently deleted the compromised account. They learned about the hacking at NordVPN on April 13, 2019, after which they immediately deleted the server.
The attacker managed to gain access to the private key. According to NordVPN, this certificate has expired at the time of the theft, but there is a mismatch with the dates. Perhaps we are talking about the fact that the key surfaced on the network after the expiration date. In any case, the key could not be used to decrypt client traffic. However, according to the version in the tweet above and according to an anonymous commentator in an article on TechCrunch, the problem is much more serious. Quote from TechCrunch: "This is a sign of a complete remote hacking of the infrastructure of this provider."
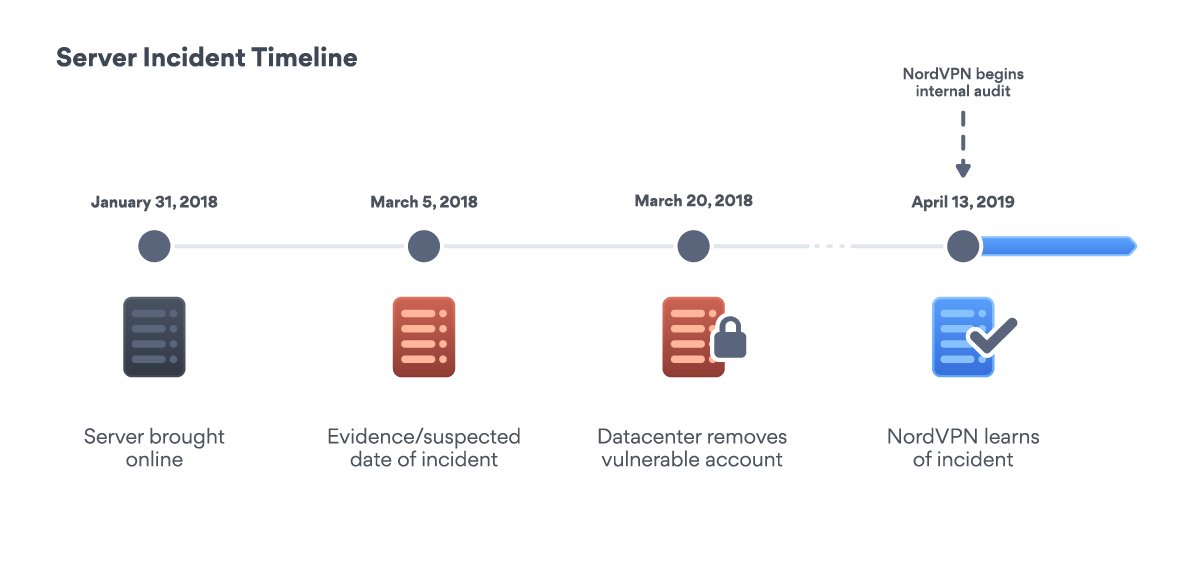
Who to believe? On the one hand, there is a fairly detailed description of the incident from NordVPN, on the other hand, comments by experts and Twitter users who prefer not to call themselves. Most likely, nothing serious and the truth happened. Access to the server did not leak information about the traffic of users who connected through this server: NordVPN does not store logs in any case. The credentials did not leak either, because NordVPN applications do not transfer real logins and passwords to the server. But wait, NordVPN and other providers have the ability to connect to the server directly! How are things going then?
At best, a stolen key could be used in what NordVPN calls a "complex MITM attack." That is, theoretically, someone could use a key still to pick up a fake server, supposedly owned by NordVPN, lure the user to it using DNS spoofing and steal all the transmitted data. Is such a scenario possible? The probability is not zero. Was it really used? What proportion of NordVPN users could suffer if they were?
This whole discussion is complicated by the approach of many VPN services to advertising their services. They tend to exaggerate the benefits of a VPN connection, they say that your data is completely secure, although in fact, no technology provides absolute security. Competition in the VPN market is high, and as a result of discussions like "the security of our VPN is safer than that of competitors", mutual accusations and other events that are far from technology take place.
Any message about the vulnerability is perceived by the providers themselves, and their customers, and by extras in social networks as a kind of end of the world, which is not entirely correct. The result is this: those who talked about “hacking the entire infrastructure” did not provide any convincing evidence. NordVPN described in sufficient detail the problem and methods for solving it, but their material contains almost no technical details of the incident. Not the fact that your own VPN server is, as some people suggest, the right solution. It requires technical skills, and in fact the set of risks is just slightly changing. We must not forget that any remedy solves any one problem and is not able to get rid of all threats on a global scale. Which is not a reason to completely abandon protection.
What else happened:
18 applications were removed from the Apple App Store, which in the background increase website traffic. Malicious activity occurred with a delay, which allowed applications to pass an audit by Apple.
Google Chrome has been updated to version 78. A couple of serious vulnerabilities have been closed; fixed bug causing URL spoofing. The previously promised beta testing of the DNS-over-HTTPS functions was decided to be postponed until the next version. A similar feature appeared in Firefox in September, and in the latest release of Firefox 70 they began to block cross-site cookies on social networks.
Experts of Kaspersky Lab! released a threat overview for users of the Steam gaming platform. Interesting examples of phishing that take into account the two-factor authentication mechanism are provided.
An interesting vulnerability was found in the robotic assistants used in the Japanese hotel chain. The bug allows you to intercept streams from the camcorder and the microphone of the device. Operation requires physical access - first a device is hacked in a hotel, then surveillance is carried out.
A vulnerability has been detected in the Xiaomi cat food dispenser. Allows you to remotely disable devices. Or arrange a feast for your pets.