Since then, a large number of courses have been read, but the problem of resources has not disappeared, until a huge blue mammal loaded with containers loomed on the horizon.
Of course, I think everyone google “Container vs VM” and got something like that.
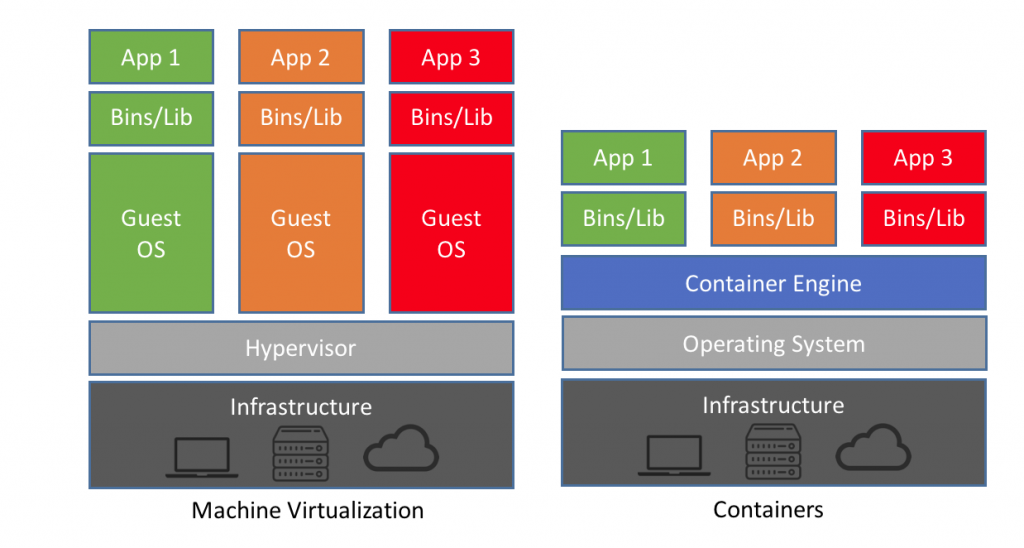
It does not explain much, but the general essence is clear: instead of a large number of operating systems and applications on them, we launch one operating system, and the necessary applications start inside it. This approach has its advantages and disadvantages, but today we’ll talk about how containers can help with training pentesters and auditors.
The simplest thing that could be is using containers to create intentionally vulnerable work environments. Now, instead of deploying the necessary versions of apache, mysql and other things, we can get a ready-made container with everything you need. Let's start, of course, with the classics:
• The most popular and damn vulnerable DVWA web application. A classic php / mysql application with your favorite XSS, CSRF, LFI and more. A bit outdated, but continues to be found at every second pentest:
Damn Vulnerable Web Application (DVWA) (docker pull citizenstig / dvwa)
• Another popular application in which vulnerabilities are structured according to OWASP TOP10:
OWASP Mutillidae II Web Pen-Test Practice Application (docker pull citizenstig / nowasp)
• OWASP juice store, created on the basis of the popular angular, node.js, nosql, but no less vulnerable to this. My choice for anyone who plunges into the brave world of penetration testing:
OWASP Juice Shop (docker pull bkimminich / juice-shop).
• The same OWASP TOP10, only based on Node.js:
OWASP NodeGoat (docker-compose build && docker-compose up)
• Another application from OWASP with the same set of vulnerabilities:
OWASP WebGoat Project 8.0 docker image (docker pull webgoat / webgoat-8.0)
• Once there is a goat, there must be a shepherd. In our case, this is OWASP Security Shepherd, which allows you to look at the client side of web applications, as well as mobile applications:
OWASP Security Shepherd (docker pull ismisepaul / securityshepherd)
Periodically, when another vulnerability is revealed, it can be useful to touch it with your hands. You do not need to raise a virtual machine for this. We have VaaS - vulnerability as a service:
• Vulnerability as a service: Heartbleed (docker pull hmlio / vaas-cve-2014-0160)
• Vulnerability as a service: SambaCry (docker pull vulnerables / cve-2017-7494)
• Vulnerability as a service: Shellshock (docker pull hmlio / vaas-cve-2014-6271)
You can also explore specific products that you most often encounter in pentests, for example, vulnerable WordPress:
• Vulnerable WordPress Installation (docker pull wpscanteam / vulnerablewordpress)
In addition, the testing tools themselves can be obtained in the form of containers: nmap , zap , wpscan , metasploit , etc.
And even the whole Kali Linux image can be obtained with the docker pull kalilinux / kali-linux-docker command
By the way, now the containers themselves have become objects of testing, so the corresponding virtual machines began to appear for self-study - Vulnerable Docker: 1 , BSidesTLV: 2018 CTF , myHouse7: 1 , DonkeyDocker: 1 .
Containers have many advantages, however, it is obvious that the number of adherents of classic virtual machines is not getting smaller. There are many reasons for this, but in fact, if the resources of your training center allow, and you can automate the work using Packer and Vagrant, it is too early to think about this topic.
Sergey Polunin ,
Team Leader, Design Department, Gazinformservice LLC