FAQ about cloud [electronic] signature
Our platform became the first federal electronic trading operator to introduce a new cloud-based electronic signature technology. If the usual ES caused a lot of questions, then this service, on the one hand, is still more incomprehensible to business, and on the other hand, everything has become much simpler.
- What it is?
There used to be a paper signature on the document. It is not very convenient, not very safe and requires physical paper. Then came a flash drive with a certificate and a kit around (up to the antivirus). She was first called EDS - an electronic digital signature. Then she became just an EP. Now this flash drive has been put in the cloud, and it has become an OEP.
- How does the EIA work?
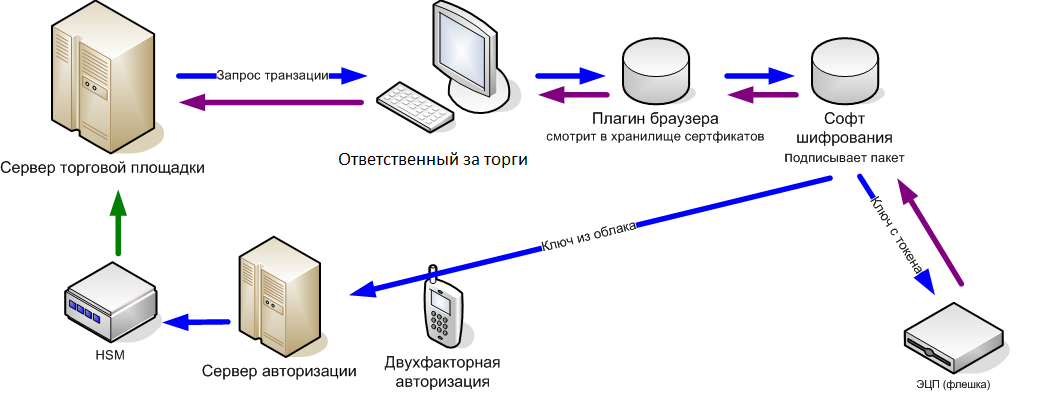
Suppose you submit your proposal for a tender. Previously, in order to sign a document, it was necessary to install a plug-in for a browser that could communicate with software on the user's local computer. This software accessed the software on the USB flash drive, the software on the USB flash drive issued the key, the transaction was signed with this key and transferred to the browser plug-in ready-made. Now we remove the flash drive from this chain: the software accesses the cloud storage via an encrypted tunnel.
- Is it possible without software on the local machine?
Yes, if there is an intermediate server on the site that actually proxies requests and appears to be this very local computer, then everything can be done from any browser. But this requires processing the backend of the site (in our case, we made a separate server for trading from mobile phones). If this path does not work, the standard one is selected. It is assumed that in the future this option will be the most common. As an example of one of such implementations, the Roseltorg SME platform (Purchasing among small and medium-sized businesses).
- OEP and EP are one and the same, but lie in different places, right?
Signatures have a common core with certificate and security. Functionally, this is one and the same, just changing the method of the internal API to encrypt the transaction. One method takes the key from the local device, the other from the remote.
“Wait a minute, but you still need authorization?”
Yes. But now it is two-factor and without reference to the device. The usual scheme: install the application on the phone or the browser plug-in on the desktop, then enter the login and password to start work, then when making the transaction - the PIN code sent from the authorization server. That is, to sign the document for you, you will need to steal the password + login and intercept an SMS or push notification with a code.
- What is the profit then?
- Where is the certificate stored on the side of the certification authority?
There is a special piece of hardware called HSM (hardware security module). Technically, this is a repository divided into closed cells without the possibility of mass access to all at once.
Simplifying a bit: you log in, create a transaction, it is sent to HSM to subscribe, and from there the protected object is output. The private key is not issued outside.
That is, HSM acts as a third party, like a notary, confirming in a transaction that you are you. More precisely, you have the right to sign a document.
Each certification authority has its own HSM.
Each decision is licensed by the FSB. The piece of iron is equipped with a large number of security levels, in particular, anti-jail sensors. The terminal is physically built into the server itself, no external connections for management are supported, there is no web interface. You need to configure something - a sweater, a gym, a large iron box with a small LCD screen.

- How about backward compatibility?
Again, simplifying, new versions of software for working with EPs are now able to do something like emulating this very flash drive for all the old software. That is, it does not matter what you use: a token on a physical medium or access to HSM. Updated software will sign everything, as in the good old days.
- What does the first connection look like?
When configured on the end-user device, two DSS server addresses are specified. This, in fact, is the whole setting. After that, you will need to log in to the server. The user enters a unique login and password, which are issued to him in the certification center. After entering the login and password, you need to go through two-factor authorization. Typically, the user scans the QR code issued to him and installs the application. This is one common signature vendor application that is customized for a specific certification authority. The second code is scanned with reference to its cell in the HSM. A PIN code is sent for a specific transaction to the subscriber's phone, he uses it and confirms himself. After that, you need to change the access password.
The following transactions may be simpler: PIN is sent by push notification. It is assumed that if the phone is protected by FaceID or fingerprint recognition, then this second factor (in combination with entering the login and password) is enough.
If the phone is lost, you need to go through the procedure with QR codes again.
A locked phone without a PIN is useless.
A PIN without a login password is useless.
If you have lost an unlocked phone with a photo of your login and password recorded on a piece of paper (a real case in our CA), then you can request an access lock until clarification.
- How to get an envelope with access to the EIA?
A simple case: the applicant (general director of the legal entity) comes personally with a passport to the certification center and receives an envelope.
Difficult case: an employee arrives with a certified power of attorney that meets the requirements of 63-FZ (On electronic signature) and the requirements of the security service of the certification center.
- This is a mass phenomenon?
Yes. For the first month of work, the UTES EC issued about a thousand certificates using the new EIA technology. About 70% of users who have issued electronic signatures are legal entities, another 23% are individual entrepreneurs. More than 60% of users of the new service are companies from Moscow. There are certificates in St. Petersburg, Novosibirsk, Khabarovsk, Rostov-on-Don.

- What it is?
There used to be a paper signature on the document. It is not very convenient, not very safe and requires physical paper. Then came a flash drive with a certificate and a kit around (up to the antivirus). She was first called EDS - an electronic digital signature. Then she became just an EP. Now this flash drive has been put in the cloud, and it has become an OEP.
- How does the EIA work?
Suppose you submit your proposal for a tender. Previously, in order to sign a document, it was necessary to install a plug-in for a browser that could communicate with software on the user's local computer. This software accessed the software on the USB flash drive, the software on the USB flash drive issued the key, the transaction was signed with this key and transferred to the browser plug-in ready-made. Now we remove the flash drive from this chain: the software accesses the cloud storage via an encrypted tunnel.
- Is it possible without software on the local machine?
Yes, if there is an intermediate server on the site that actually proxies requests and appears to be this very local computer, then everything can be done from any browser. But this requires processing the backend of the site (in our case, we made a separate server for trading from mobile phones). If this path does not work, the standard one is selected. It is assumed that in the future this option will be the most common. As an example of one of such implementations, the Roseltorg SME platform (Purchasing among small and medium-sized businesses).

- OEP and EP are one and the same, but lie in different places, right?
Signatures have a common core with certificate and security. Functionally, this is one and the same, just changing the method of the internal API to encrypt the transaction. One method takes the key from the local device, the other from the remote.
“Wait a minute, but you still need authorization?”
Yes. But now it is two-factor and without reference to the device. The usual scheme: install the application on the phone or the browser plug-in on the desktop, then enter the login and password to start work, then when making the transaction - the PIN code sent from the authorization server. That is, to sign the document for you, you will need to steal the password + login and intercept an SMS or push notification with a code.
- What is the profit then?
- If you lose a flash drive, you need to get a new key. In the case of OEP - just change the password for the signature.
- There is no reference to the workplace: before, ES was installed on one specific computer.
- No browser bindings: it used to be IE. Which caused a number of problems even at the OS choice level: Linux admins circumvented this, but on Mac devices it was more difficult.
- There is no reference to geography: authorization works from any country (due to the peculiarities of protecting electronic devices on flash drives, they often worked only in Russian networks).
- It is assumed that everything has become safer due to two-factor identification by default without the ability to "simplify your life."
- Destroying a flash drive with a signature does not jeopardize current transactions.
- In general, all this is more correct, especially because of the ability to quickly sign from mobile phones.
- Where is the certificate stored on the side of the certification authority?
There is a special piece of hardware called HSM (hardware security module). Technically, this is a repository divided into closed cells without the possibility of mass access to all at once.
Simplifying a bit: you log in, create a transaction, it is sent to HSM to subscribe, and from there the protected object is output. The private key is not issued outside.
That is, HSM acts as a third party, like a notary, confirming in a transaction that you are you. More precisely, you have the right to sign a document.
Each certification authority has its own HSM.
Each decision is licensed by the FSB. The piece of iron is equipped with a large number of security levels, in particular, anti-jail sensors. The terminal is physically built into the server itself, no external connections for management are supported, there is no web interface. You need to configure something - a sweater, a gym, a large iron box with a small LCD screen.

- How about backward compatibility?
Again, simplifying, new versions of software for working with EPs are now able to do something like emulating this very flash drive for all the old software. That is, it does not matter what you use: a token on a physical medium or access to HSM. Updated software will sign everything, as in the good old days.
- What does the first connection look like?
When configured on the end-user device, two DSS server addresses are specified. This, in fact, is the whole setting. After that, you will need to log in to the server. The user enters a unique login and password, which are issued to him in the certification center. After entering the login and password, you need to go through two-factor authorization. Typically, the user scans the QR code issued to him and installs the application. This is one common signature vendor application that is customized for a specific certification authority. The second code is scanned with reference to its cell in the HSM. A PIN code is sent for a specific transaction to the subscriber's phone, he uses it and confirms himself. After that, you need to change the access password.

The following transactions may be simpler: PIN is sent by push notification. It is assumed that if the phone is protected by FaceID or fingerprint recognition, then this second factor (in combination with entering the login and password) is enough.
If the phone is lost, you need to go through the procedure with QR codes again.
A locked phone without a PIN is useless.
A PIN without a login password is useless.
If you have lost an unlocked phone with a photo of your login and password recorded on a piece of paper (a real case in our CA), then you can request an access lock until clarification.
- How to get an envelope with access to the EIA?
A simple case: the applicant (general director of the legal entity) comes personally with a passport to the certification center and receives an envelope.
Difficult case: an employee arrives with a certified power of attorney that meets the requirements of 63-FZ (On electronic signature) and the requirements of the security service of the certification center.
- This is a mass phenomenon?
Yes. For the first month of work, the UTES EC issued about a thousand certificates using the new EIA technology. About 70% of users who have issued electronic signatures are legal entities, another 23% are individual entrepreneurs. More than 60% of users of the new service are companies from Moscow. There are certificates in St. Petersburg, Novosibirsk, Khabarovsk, Rostov-on-Don.
All Articles