Security Week 36: Smartphone Vulnerability Lifetime
 The main news of the past week was a large-scale study of a real attack on iOS-based devices, published by expert Jan Ber from the Google Project Zero team ( news , Jan’s blog post with links to seven additional publications). This is a rare example of a study that describes in detail not only the process of hacking the iPhone, but also the results of the installed implant.
The main news of the past week was a large-scale study of a real attack on iOS-based devices, published by expert Jan Ber from the Google Project Zero team ( news , Jan’s blog post with links to seven additional publications). This is a rare example of a study that describes in detail not only the process of hacking the iPhone, but also the results of the installed implant.
The study did not reveal the target of the attackers, and there are some oddities. Exploits infected iOS devices without additional user actions, it was enough to visit the hacked website. At the same time, all site visitors were infected, which, in the context of the price of a working exploit for Apple devices, is, to put it mildly, short-sighted. Despite the fact that “thousands of users every week” visited infected sites, this particular campaign lasted at least two years, changing attack methods as new versions of iOS became available.
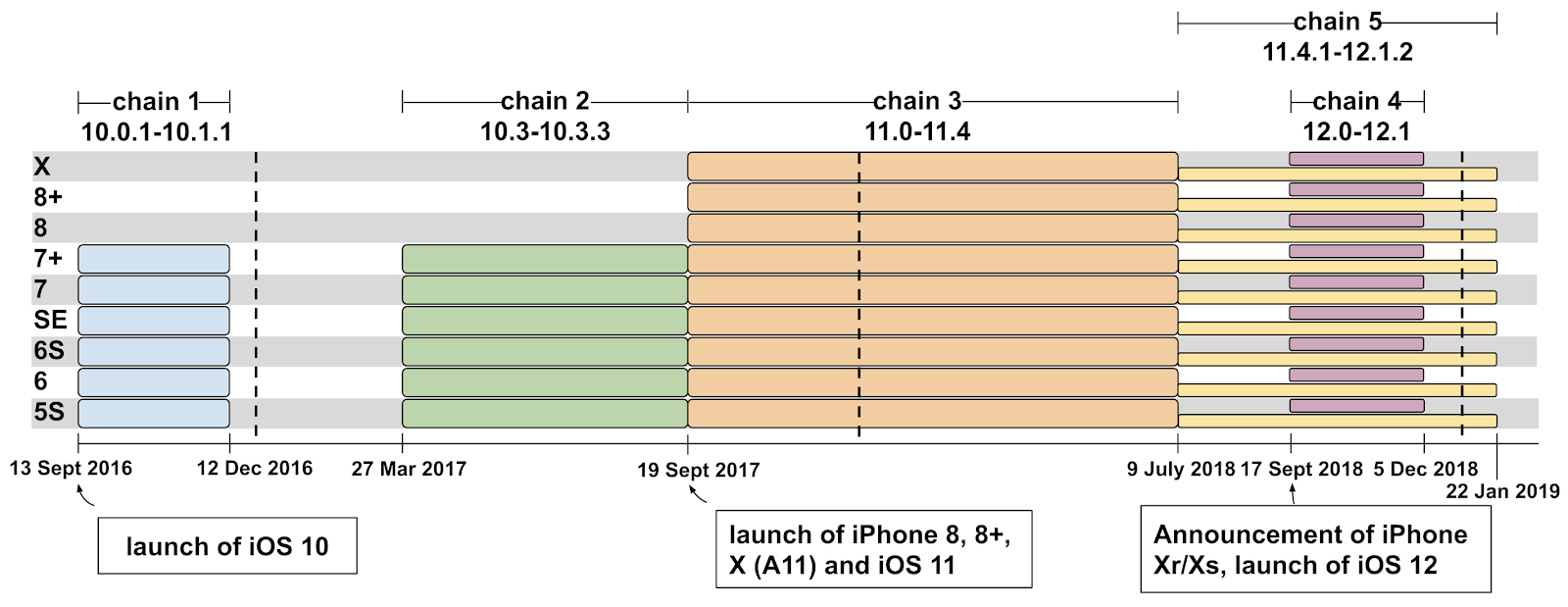
The attacks began in 2016, they were subjected to all iPhone models from 5s and up to the most modern, running iOS 10-12 version. A study of infected websites revealed 14 vulnerabilities that were used in five different combinations to hack iOS. Each method provided complete control over the victim’s telephone. As iOS updates were released, attack methods changed, most likely in response to closing vulnerabilities in new versions of iOS, but, possibly, for some other reasons. For current today iOS 12, two attack scenarios were used. At the time of discovery, only one of them used vulnerabilities not covered in the latest version of iOS: an emergency patch for them was released in February this year.
The Google Project Zero blog details all five attack methods and analyzes the vulnerabilities used in various iOS components. Separately, researcher Samuel Gross describes vulnerabilities in the browser , more precisely, in the WebKit engine. There is an interesting observation: the researchers suggest (but cannot say for sure) that the attackers carefully watched the patches of the WebKit engine itself and used exploits against iOS, until the next update was released for Apple smartphones.
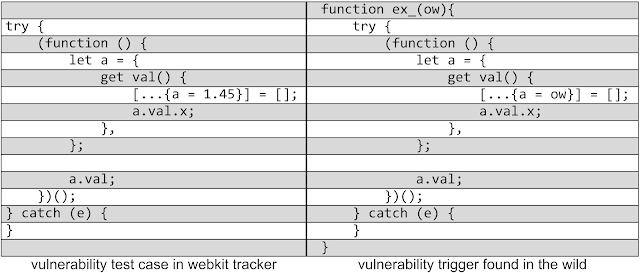
In some cases, along with a vulnerability patch, researchers published the Proof of Concept. The image above shows what the public PoC attack organizers used with minimal changes. This vulnerability was closed in WebKit on March 11, 2017, and the release of iOS 10.3.2 with this patch took place only on May 15. In total, the article describes seven vulnerabilities in WebKit, and in each case, the attackers had about two months of handicap before the release of the patch. Vulnerabilities in the browser themselves do not provide full control over the mobile device, but thanks to them, it becomes possible to exploit vulnerabilities in other components of the OS and gain full control.
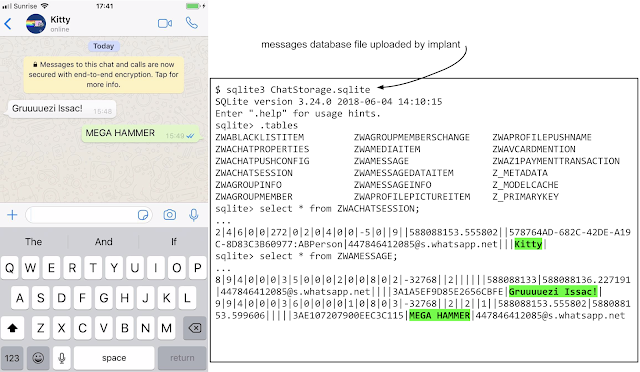
Finally, a separate article describes the functionality of the malware that attackers installed after hacking iOS. Quite often, researchers are limited to a simple list of possibilities, here everything is clearly shown with screenshots. Namely: theft of correspondence from Telegram, Whatsapp, Hangouts and iMessage, interception of unencrypted correspondence in the GMail application, theft of contacts, photos and transfer of the victim’s geolocation every minute. The implant also uploads WiFi passwords and tokens to the server of attackers to access services, such as a Google account. The malicious program does not survive a reboot, but, firstly, smartphones do not reboot so often, and secondly, even the short-term operation of the malicious program gives the attacker a lot of information to further compromise the mail account and other things.
It looks scary. The user cannot determine the presence of malware in any way, since he himself does not have access, for example, to the list of running processes. It is possible to identify the infected device by the characteristic every minute calls to the command server. Moreover, all stolen data is transmitted without encryption, via http, and theoretically available not only to the organizers of the attack, but generally to anyone. How did attackers manage to work undetected for a long time, while not really hiding and exploiting zero-day vulnerabilities? The publication of Google Project Zero does not answer this question. The article only says that such a campaign is unlikely to be the only one.
In this study, the lifetime of a working exploit during its moderately public exploitation is of interest. Judging by the timeline shown by the researchers, it takes from three to nine months, although not all the methods shown worked on an updated phone to the latest version.

Previously, Kaspersky Lab experts talked about a massive attack on Android users ( news , research ). The popular CamScanner application, which recognizes the text of a photographed document, was compromised at some point: an ad module was added to the program code on Google Play, which accessed the attacker's servers and downloaded malicious code from there. In this case, the Necro.n Trojan made money on victims by any means available, from showing ads on top of other applications to sending SMS to paid numbers. At the moment, the application has been removed from the Google store, and judging by user reviews, the malicious version spread for about a month - so many massive attacks on smartphones go unnoticed. According to data from the store itself, the application has been downloaded more than 100 million times.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
All Articles