Training Cisco 200-125 CCNA v3.0. Day 30. Cisco Network Architecture and Troubleshooting
We have almost reached the end of the topic of the first part of the CCNA course, which is necessary for passing the ICND1 exam. Since I skipped a few topics, this and the next video tutorials will focus on filling the gaps in your knowledge. Today we will cover three topics:
Cisco uses two approaches to network architecture: the three-tier hierarchical architecture of Cisco 3 Tier Architecture and the two-tier architecture Collapsed Core Architecture.
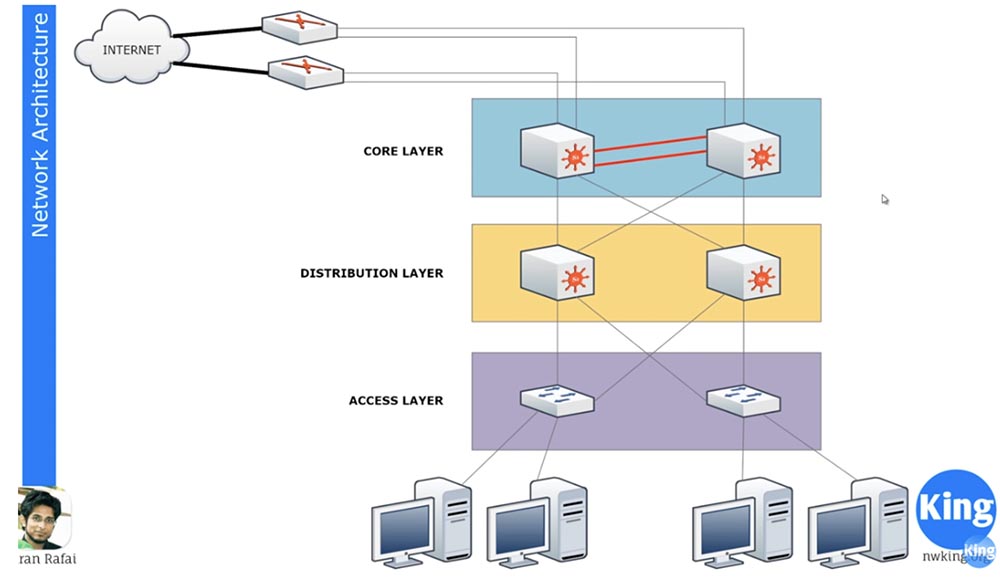
This slide shows the Cisco 3 Tier architecture, which consists of 3 layers: the Access layer, the Distribution layer, and the core of the core layer. The access level is represented by devices that are directly connected to end-user devices. All office devices are connected to an access level switch. Usually at this level, inexpensive and not too powerful switches are installed. They are not interconnected, so if you have hundreds of devices and dozens of switches in each building, they are all connected by cables to a common network cabinet. To avoid confusion, these switches are never directly connected to each other, because this can result in real hell from the wires.
To ensure the collaboration of these network devices, a distribution level is used, which is represented by more powerful devices. If the access level devices want to communicate with each other, they turn to the distribution level devices, and they organize such a connection. Distribution levels are usually called the "building level" because if the company is located in several buildings, each of them has its own Distribution layer, consisting of powerful switches.
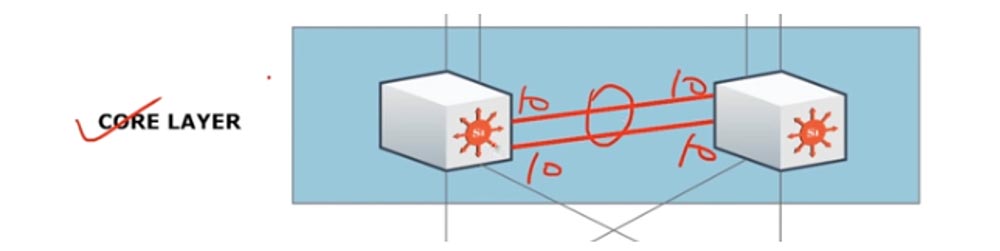
The distribution level is related to the core layer of the Core layer. This level is located on the border of the local network and the Internet and serves to provide external connections outside the VPN. All devices of the distribution layer are connected to devices of the main level, and the Core layer switches themselves are connected to each other. This connection is called Ether channel, we will consider it in more detail in the subject of ICDN2, for now I will say that this connection consists of several cables connecting two switches of the network core. For example, if you have 2 Gigabit Ethernet 10 cables, then the Ether channel will look like a logical 20-gig cable connecting these two devices.
Unlike network core devices, access level and distribution level devices do not connect to each other. Three-tier architecture helps to avoid many problems. Firstly, dividing the traffic into different flows allows you to establish a more secure stable connection, since one group of access level devices communicates with a distribution level device that broadcasts traffic to another group of access level devices. If you want to contact devices located in another building, traffic from the distribution level is sent to network core devices that redirect it down the levels to user devices. This allows a logical distribution of traffic with a minimum of malfunctions and maximum efficiency.
If you have a small company with a small number of devices, you can use a two-tier architecture consisting of an access level and a Collapsed Core level, which is a combination of Core Layer and Distribution layer levels.
At the same time, Collapsed Core devices are connected to each other, but access level devices are not, therefore, when they want to communicate with each other, they should turn to the upper level.

This is a fairly efficient network architecture, and if you do not have enough money and network resources, it is worth using Collapsed Core.
Let's move on to considering devices that affect network performance. According to ICND1, you should know about three types of such devices. The first type is a firewall, which we did not particularly talk about, because firewalls are discussed in detail in the CCNA Security course. We already talked about traffic filtering when we discussed ACLs, and so, a firewall is a device designed exclusively for filtering traffic packets.
Suppose you have a local area network, which includes two computers, a switch and a router, and an external network - the Internet. The firewall is located between your device and the Internet connection, in my figure it is a red rectangle in front of the cloud.
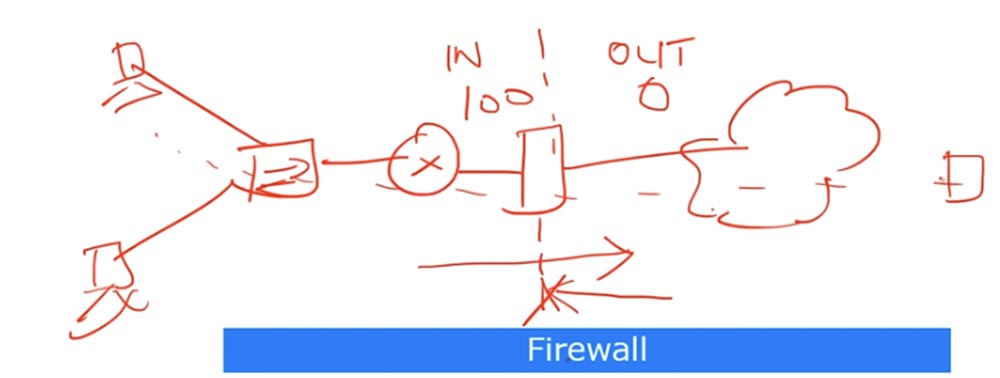
The firewall filters incoming traffic from insecure areas of the Internet. Usually it has 2 zones of responsibility: internal IN and external OUT. The inner zone has a security level of 100, this is maximum security, and the outer zone has zero security. By default, traffic routed from the zone with maximum security to the zone of minimum security is always allowed, and traffic backward is prohibited.
Let's say one of the local computers pings a device located on the Internet. Outgoing ping packets will be skipped and the incoming firewall will be discarded because they are routed from the minimum security zone to the enhanced security zone. Thus, when analyzing the network, you need to pay attention to setting up a firewall. However, there are not only network firewalls, your computer also has its own software firewall. If you are unable to connect to an external server or if you do not start any application that requires access to the Internet, you first need to pay attention to the firewall settings. By default, the firewall on client machines blocks all traffic of the application that is trying to connect to the Internet, so you need to go into the firewall settings and open a blocked port or put the application on the exclusion list. Of course, it all depends on whether your company considers this software necessary for work or is it just a user’s initiative.
The next device that affects the network is the Access Point. If your company does not use wireless devices, your network is much safer compared to a network that allows wireless connection. The fact is that the wireless access point in your office allows any unauthorized person to connect to your local network if he received a password in a legal or illegal way. We will not take into account the case of hacking the password, suppose that you just forgot to set a password for the access point. In this case, it will be constantly available, and any outsider who is in your office or near it will be able to connect to it.
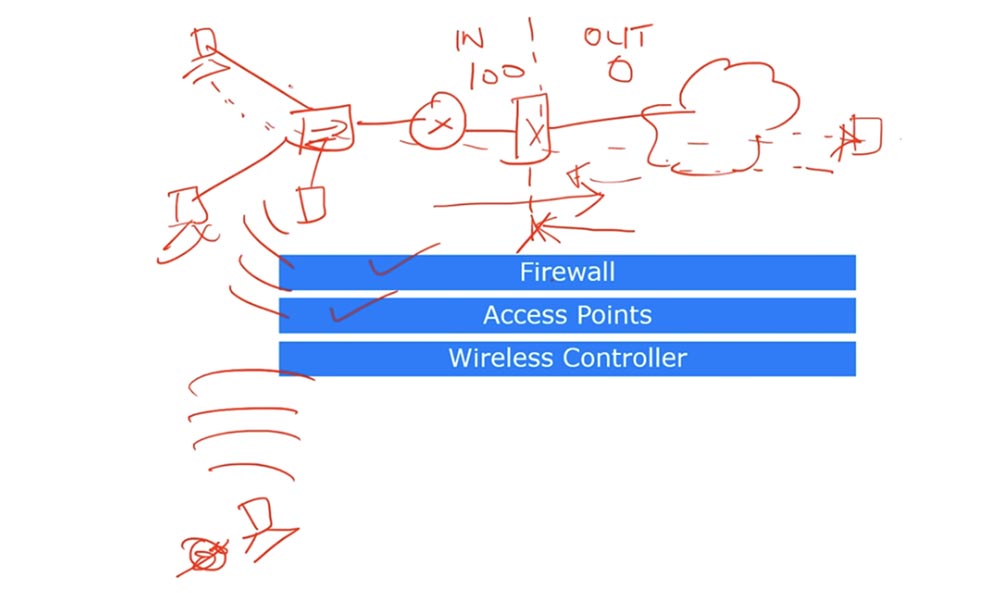
In this case, the “alien” will gain access to any shared files, folders and networks. Therefore, wireless access points must be carefully documented and you, as the network administrator, must ensure that they are properly protected.
Consider what a wireless controller is. Suppose your organization has hundreds of access points. If we are talking about a home access point such as a wireless router, you can manually configure the SSID and password for each home device, but for a large organization this method is not suitable. If the password for the office access point has been hacked, you will have to manually change the password on several hundred wireless devices of the company, which is too burdensome. For such cases, a wireless controller is used, under the control of which several access points operate.
This controller is connected to your local network and to all wireless access points, hundreds of such points can be connected to one controller. If you change the SSID or password in the central wireless controller, then all these access points will automatically update this information.
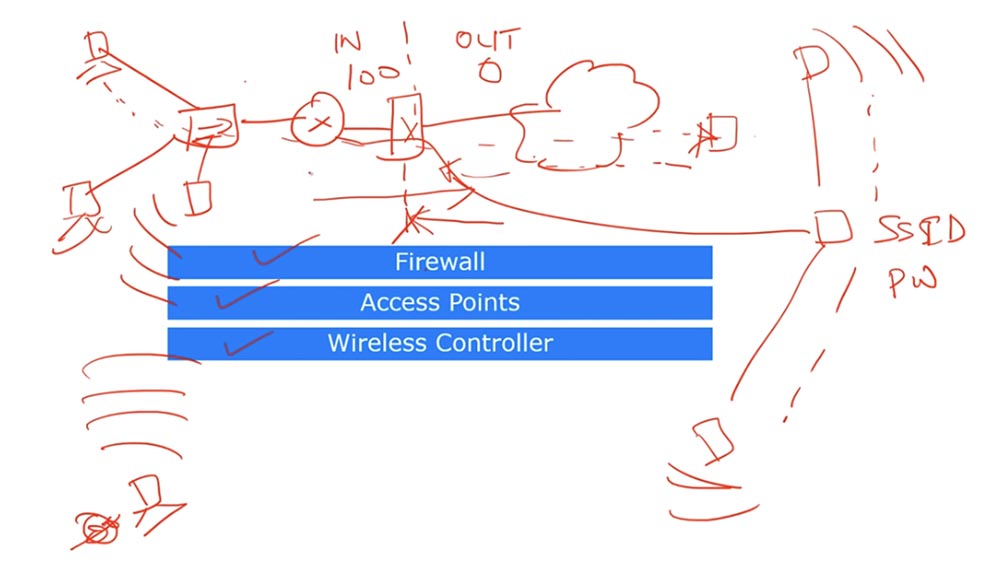
Therefore, access points controlled by a wireless controller are much more convenient than individual points, since you can control the entire wireless network using one controller.
Now let's look at the methodology for diagnosing and troubleshooting. For example, a user contacts technical support and reports that the Internet does not work for him. Technical support staff considers the appeal and reports that the reason is not on the Internet, but in the incorrect operation of one of the programs installed on the client’s computer. So if you are a network engineer, you must understand the troubleshooting methodology. They can call you and tell you about the most commonplace problem as if it were the end of the world, so it is very important to know the method for diagnosing the cause of the problem.

You always need to start with the definition of the problem, with its correct formulation. If someone calls you and says that the Internet does not work for him, you should ask him clarifying questions. Perhaps his computer is not turned on at all, or the computer is turned on, but the monitor is turned off, and so on. I am exaggerating a little, but we have already devoted so much time to discussing network problems that I hope you can ask the right leading questions.
Having formulated the problem, you need to proceed to the accumulation of facts. The accumulation of facts characterizing a specific problem will allow us to establish a possible cause of its occurrence. For example, if someone cannot access the Internet, you need to find out if this happens at a particular time or constantly and whether some other, extraneous device can influence it. You need to find out if computers work with colleagues of a given user, whether they can establish communication with each other, and the like. Try to collect as many facts as possible. If a user calls you and says that he does not have the Internet, it is wrong to assume in advance that his computer is malfunctioning. Perhaps there is no connection with the switch or the switch is simply turned off. Find out everything that may be related to this problem.
Further, since you learned more about the problem than the user knows about it, you can assume what exactly could fail, that is, proceed to determine the possible causes of the problem based on the facts collected. If the hardware is OK, then the reason is software, and so on. This step will help you narrow down the range of possible problems in order to develop the most effective action plan.
The next stage is the development of an action plan. You can create plans A, B, C to then find out what will happen when implementing Plan A, Plan B, and so on. The plan can be aimed at eliminating a specific problem or several problems, but in the second case it will be difficult to establish the cause of a single problem.
The next step is to implement the action plan. Try not to plan to solve several problems at the same time. This may help at the moment, but the problem may recur in a few days, and you still haven’t found out what exactly was the cause of the previous problem. Apply one solution at a time, see what it leads to, and if the problem is not resolved, proceed to the next solution.
If the result of your decision helped fix the problem, document all the steps and complete the troubleshooting process. If the problem persists, return again to the definition of the problem or to the facts gathered in order to develop a new action plan and proceed with its implementation.
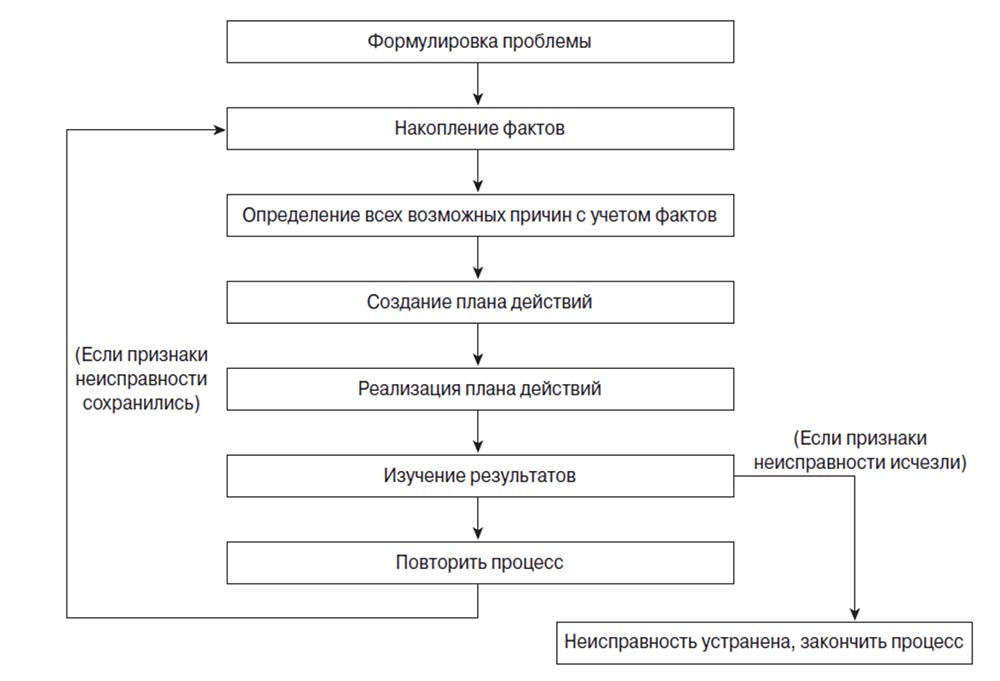
Each time you successfully solve the problem, you need to write down exactly what measures led to its elimination, and make any changes you made to the journal. For example, you solved a problem on Saturday and wrote everything down in a journal. If on Monday someone contacts you about a problem, you can review your Saturday notes and conclude if the changes you made could lead to such consequences. It is possible that you were not in the office at the time the problem was fixed by another network specialist, and when you return to work on Monday, you can look at the changes made by him in the journal and find out if they could cause a problem that occurred on Monday.
Do not forget to ensure that the user's desires correspond to the requirements of the business, that is, relate exclusively to the sphere of fulfilling his professional duties. If the user has a problem accessing the site to download music or movies, it should not be solved, since such problems do not apply to work. Different organizations have different business goals, and you should understand this in order not to go on about employees and eliminate only those problems that impede the achievement of these goals. In addition, make sure that the decisions you make do not interfere with the company's workflow on the principle that “we treat one and cripple the other.” This is the methodology for the decision-making process for diagnosing and troubleshooting network problems.
As I said, we have come to the end of the topic ICND1, in the next video lesson I will talk about what we missed in previous classes and I think that the video lesson “Day 32” will mark the end of the first part of the CCNA course.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
- network architecture;
- devices affecting the operation of the network;
- diagnostics and troubleshooting techniques.
Cisco uses two approaches to network architecture: the three-tier hierarchical architecture of Cisco 3 Tier Architecture and the two-tier architecture Collapsed Core Architecture.

This slide shows the Cisco 3 Tier architecture, which consists of 3 layers: the Access layer, the Distribution layer, and the core of the core layer. The access level is represented by devices that are directly connected to end-user devices. All office devices are connected to an access level switch. Usually at this level, inexpensive and not too powerful switches are installed. They are not interconnected, so if you have hundreds of devices and dozens of switches in each building, they are all connected by cables to a common network cabinet. To avoid confusion, these switches are never directly connected to each other, because this can result in real hell from the wires.
To ensure the collaboration of these network devices, a distribution level is used, which is represented by more powerful devices. If the access level devices want to communicate with each other, they turn to the distribution level devices, and they organize such a connection. Distribution levels are usually called the "building level" because if the company is located in several buildings, each of them has its own Distribution layer, consisting of powerful switches.
The distribution level is related to the core layer of the Core layer. This level is located on the border of the local network and the Internet and serves to provide external connections outside the VPN. All devices of the distribution layer are connected to devices of the main level, and the Core layer switches themselves are connected to each other. This connection is called Ether channel, we will consider it in more detail in the subject of ICDN2, for now I will say that this connection consists of several cables connecting two switches of the network core. For example, if you have 2 Gigabit Ethernet 10 cables, then the Ether channel will look like a logical 20-gig cable connecting these two devices.

Unlike network core devices, access level and distribution level devices do not connect to each other. Three-tier architecture helps to avoid many problems. Firstly, dividing the traffic into different flows allows you to establish a more secure stable connection, since one group of access level devices communicates with a distribution level device that broadcasts traffic to another group of access level devices. If you want to contact devices located in another building, traffic from the distribution level is sent to network core devices that redirect it down the levels to user devices. This allows a logical distribution of traffic with a minimum of malfunctions and maximum efficiency.
If you have a small company with a small number of devices, you can use a two-tier architecture consisting of an access level and a Collapsed Core level, which is a combination of Core Layer and Distribution layer levels.
At the same time, Collapsed Core devices are connected to each other, but access level devices are not, therefore, when they want to communicate with each other, they should turn to the upper level.

This is a fairly efficient network architecture, and if you do not have enough money and network resources, it is worth using Collapsed Core.
Let's move on to considering devices that affect network performance. According to ICND1, you should know about three types of such devices. The first type is a firewall, which we did not particularly talk about, because firewalls are discussed in detail in the CCNA Security course. We already talked about traffic filtering when we discussed ACLs, and so, a firewall is a device designed exclusively for filtering traffic packets.
Suppose you have a local area network, which includes two computers, a switch and a router, and an external network - the Internet. The firewall is located between your device and the Internet connection, in my figure it is a red rectangle in front of the cloud.

The firewall filters incoming traffic from insecure areas of the Internet. Usually it has 2 zones of responsibility: internal IN and external OUT. The inner zone has a security level of 100, this is maximum security, and the outer zone has zero security. By default, traffic routed from the zone with maximum security to the zone of minimum security is always allowed, and traffic backward is prohibited.
Let's say one of the local computers pings a device located on the Internet. Outgoing ping packets will be skipped and the incoming firewall will be discarded because they are routed from the minimum security zone to the enhanced security zone. Thus, when analyzing the network, you need to pay attention to setting up a firewall. However, there are not only network firewalls, your computer also has its own software firewall. If you are unable to connect to an external server or if you do not start any application that requires access to the Internet, you first need to pay attention to the firewall settings. By default, the firewall on client machines blocks all traffic of the application that is trying to connect to the Internet, so you need to go into the firewall settings and open a blocked port or put the application on the exclusion list. Of course, it all depends on whether your company considers this software necessary for work or is it just a user’s initiative.
The next device that affects the network is the Access Point. If your company does not use wireless devices, your network is much safer compared to a network that allows wireless connection. The fact is that the wireless access point in your office allows any unauthorized person to connect to your local network if he received a password in a legal or illegal way. We will not take into account the case of hacking the password, suppose that you just forgot to set a password for the access point. In this case, it will be constantly available, and any outsider who is in your office or near it will be able to connect to it.

In this case, the “alien” will gain access to any shared files, folders and networks. Therefore, wireless access points must be carefully documented and you, as the network administrator, must ensure that they are properly protected.
Consider what a wireless controller is. Suppose your organization has hundreds of access points. If we are talking about a home access point such as a wireless router, you can manually configure the SSID and password for each home device, but for a large organization this method is not suitable. If the password for the office access point has been hacked, you will have to manually change the password on several hundred wireless devices of the company, which is too burdensome. For such cases, a wireless controller is used, under the control of which several access points operate.
This controller is connected to your local network and to all wireless access points, hundreds of such points can be connected to one controller. If you change the SSID or password in the central wireless controller, then all these access points will automatically update this information.

Therefore, access points controlled by a wireless controller are much more convenient than individual points, since you can control the entire wireless network using one controller.
Now let's look at the methodology for diagnosing and troubleshooting. For example, a user contacts technical support and reports that the Internet does not work for him. Technical support staff considers the appeal and reports that the reason is not on the Internet, but in the incorrect operation of one of the programs installed on the client’s computer. So if you are a network engineer, you must understand the troubleshooting methodology. They can call you and tell you about the most commonplace problem as if it were the end of the world, so it is very important to know the method for diagnosing the cause of the problem.

You always need to start with the definition of the problem, with its correct formulation. If someone calls you and says that the Internet does not work for him, you should ask him clarifying questions. Perhaps his computer is not turned on at all, or the computer is turned on, but the monitor is turned off, and so on. I am exaggerating a little, but we have already devoted so much time to discussing network problems that I hope you can ask the right leading questions.
Having formulated the problem, you need to proceed to the accumulation of facts. The accumulation of facts characterizing a specific problem will allow us to establish a possible cause of its occurrence. For example, if someone cannot access the Internet, you need to find out if this happens at a particular time or constantly and whether some other, extraneous device can influence it. You need to find out if computers work with colleagues of a given user, whether they can establish communication with each other, and the like. Try to collect as many facts as possible. If a user calls you and says that he does not have the Internet, it is wrong to assume in advance that his computer is malfunctioning. Perhaps there is no connection with the switch or the switch is simply turned off. Find out everything that may be related to this problem.
Further, since you learned more about the problem than the user knows about it, you can assume what exactly could fail, that is, proceed to determine the possible causes of the problem based on the facts collected. If the hardware is OK, then the reason is software, and so on. This step will help you narrow down the range of possible problems in order to develop the most effective action plan.
The next stage is the development of an action plan. You can create plans A, B, C to then find out what will happen when implementing Plan A, Plan B, and so on. The plan can be aimed at eliminating a specific problem or several problems, but in the second case it will be difficult to establish the cause of a single problem.
The next step is to implement the action plan. Try not to plan to solve several problems at the same time. This may help at the moment, but the problem may recur in a few days, and you still haven’t found out what exactly was the cause of the previous problem. Apply one solution at a time, see what it leads to, and if the problem is not resolved, proceed to the next solution.
If the result of your decision helped fix the problem, document all the steps and complete the troubleshooting process. If the problem persists, return again to the definition of the problem or to the facts gathered in order to develop a new action plan and proceed with its implementation.

Each time you successfully solve the problem, you need to write down exactly what measures led to its elimination, and make any changes you made to the journal. For example, you solved a problem on Saturday and wrote everything down in a journal. If on Monday someone contacts you about a problem, you can review your Saturday notes and conclude if the changes you made could lead to such consequences. It is possible that you were not in the office at the time the problem was fixed by another network specialist, and when you return to work on Monday, you can look at the changes made by him in the journal and find out if they could cause a problem that occurred on Monday.
Do not forget to ensure that the user's desires correspond to the requirements of the business, that is, relate exclusively to the sphere of fulfilling his professional duties. If the user has a problem accessing the site to download music or movies, it should not be solved, since such problems do not apply to work. Different organizations have different business goals, and you should understand this in order not to go on about employees and eliminate only those problems that impede the achievement of these goals. In addition, make sure that the decisions you make do not interfere with the company's workflow on the principle that “we treat one and cripple the other.” This is the methodology for the decision-making process for diagnosing and troubleshooting network problems.
As I said, we have come to the end of the topic ICND1, in the next video lesson I will talk about what we missed in previous classes and I think that the video lesson “Day 32” will mark the end of the first part of the CCNA course.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles