Training Cisco 200-125 CCNA v3.0. Day 27. Introduction to ACL. Part 2
Another thing that I forgot to mention is that the ACL not only filters traffic on the basis of the allow / refuse principle, it performs many more functions. For example, an ACL is used to encrypt VPN traffic, but to pass the CCNA exam, you only need to know how it is used to filter traffic. Back to Problem number 1.

We found that accounting and sales department traffic can be blocked on the R2 exit interface using the ACL listed.
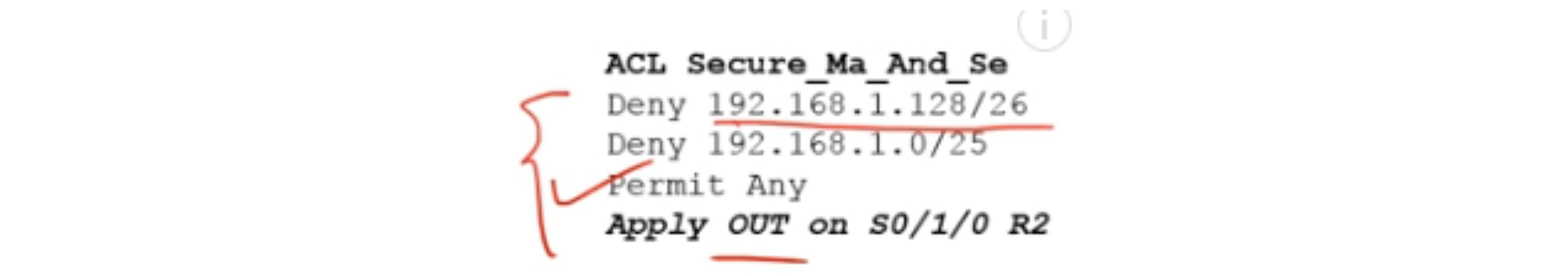
Do not worry about the format of this list, it is only needed as an example to understand the essence of the ACL. We will get to the right format as soon as we get started with Packet Tracer.
Problem number 2 is as follows: the server can communicate with any hosts except the hosts of the management department. That is, the server computers can have access to any computers of the sales and accounting department, but should not have access to the computers of the management department. This means that the server IT staff should not have remote access to the computer of the head of the management department, and in case of a malfunction, come to his office and fix the problem on the spot. Keep in mind that this task does not carry any practical sense, because I don’t know the reasons why the server room could not communicate over the network with the management department, so in this case we just consider a case study.
To solve this problem, you first need to determine the path of traffic transfer. Data from the server is fed to the input interface G0 / 1 of the router R1 and sent to the management department via the output interface G0 / 0.
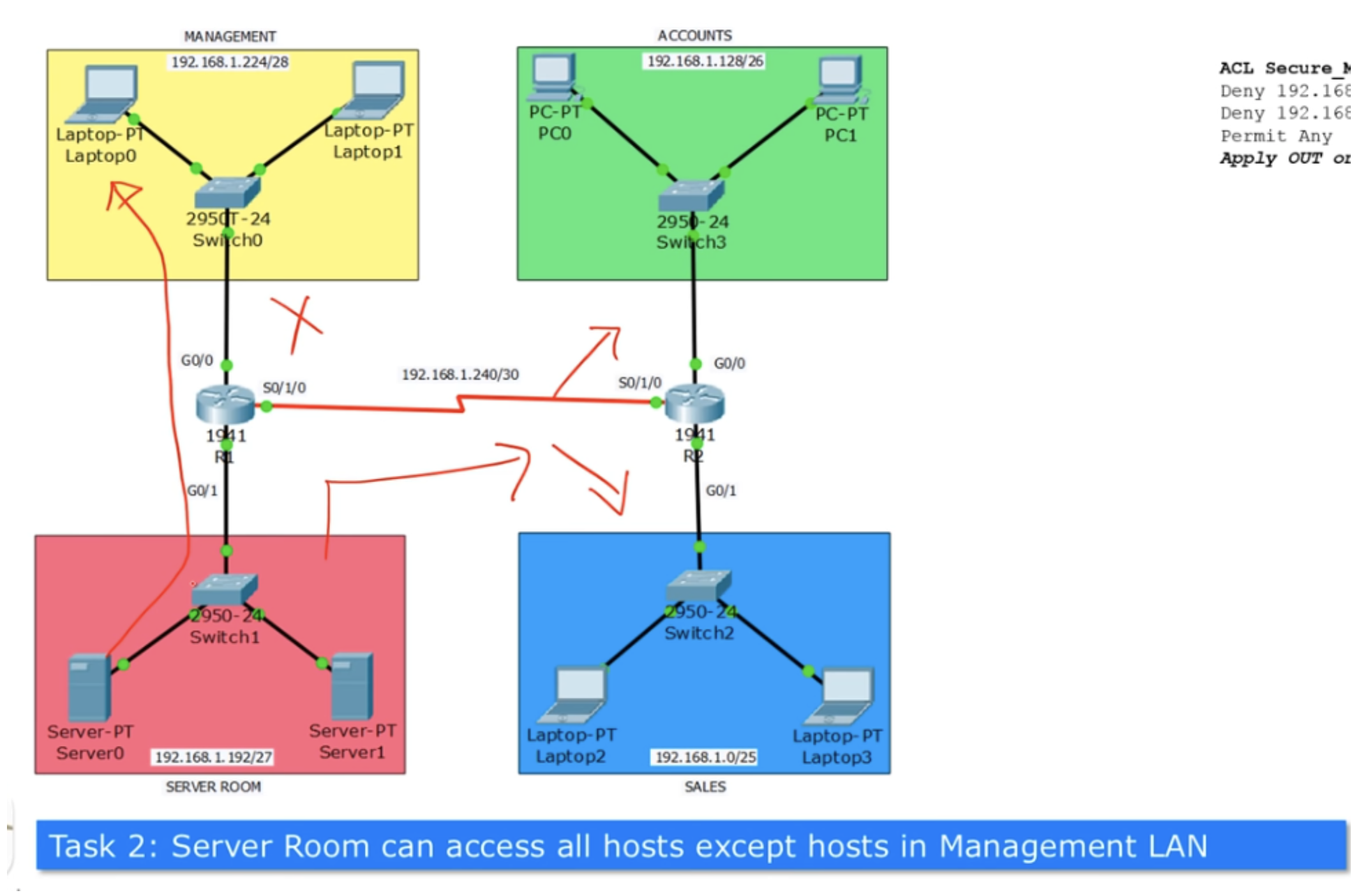
If we apply the Deny condition 192.168.1.192/27 to the input interface G0 / 1, and as you remember, the standard ACLs are placed closer to the traffic source, we will block all traffic altogether, including the sales and accounting department.

Since we want to block only traffic directed to the management department, we must apply ACLs to the output interface G0 / 0. You can solve this problem only by placing the ACL closer to the destination. At the same time, traffic from the accounting network and the sales department should freely reach the management department, so the last line of the list will be the Permit any command - allow any traffic except the traffic specified in the previous condition.
Let's move on to Problem 3: Laptop 3 from the sales department should not have access to any devices other than those located on the local network of the sales department. Suppose that a trainee is working at this computer and should not go beyond his LAN.
In this case, you need to apply the ACL on the input interface G0 / 1 of router R2. If we assign the IP address 192.168.1.3/25 to this computer, then the Deny condition 192.168.1.3/25 must be met, and traffic from any other IP address should not be blocked, so Permit any will be the last line of the list.
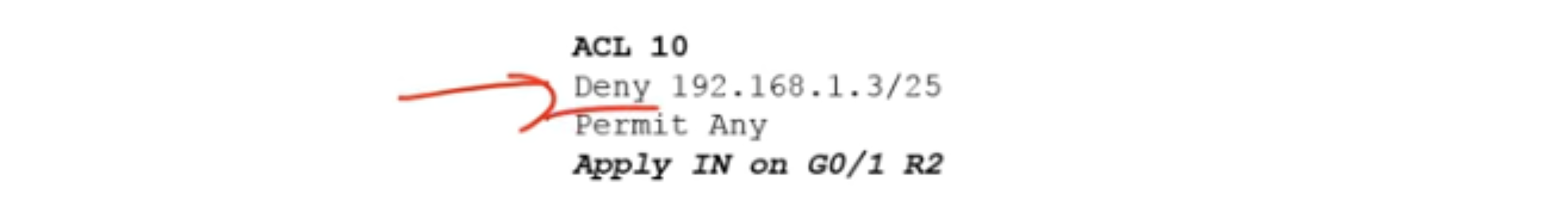
At the same time, traffic prohibition will not have any effect on Laptop2.
The next will be Task No. 4: only the computer PC0 of the finance department can have access to the server network, but not the management department.
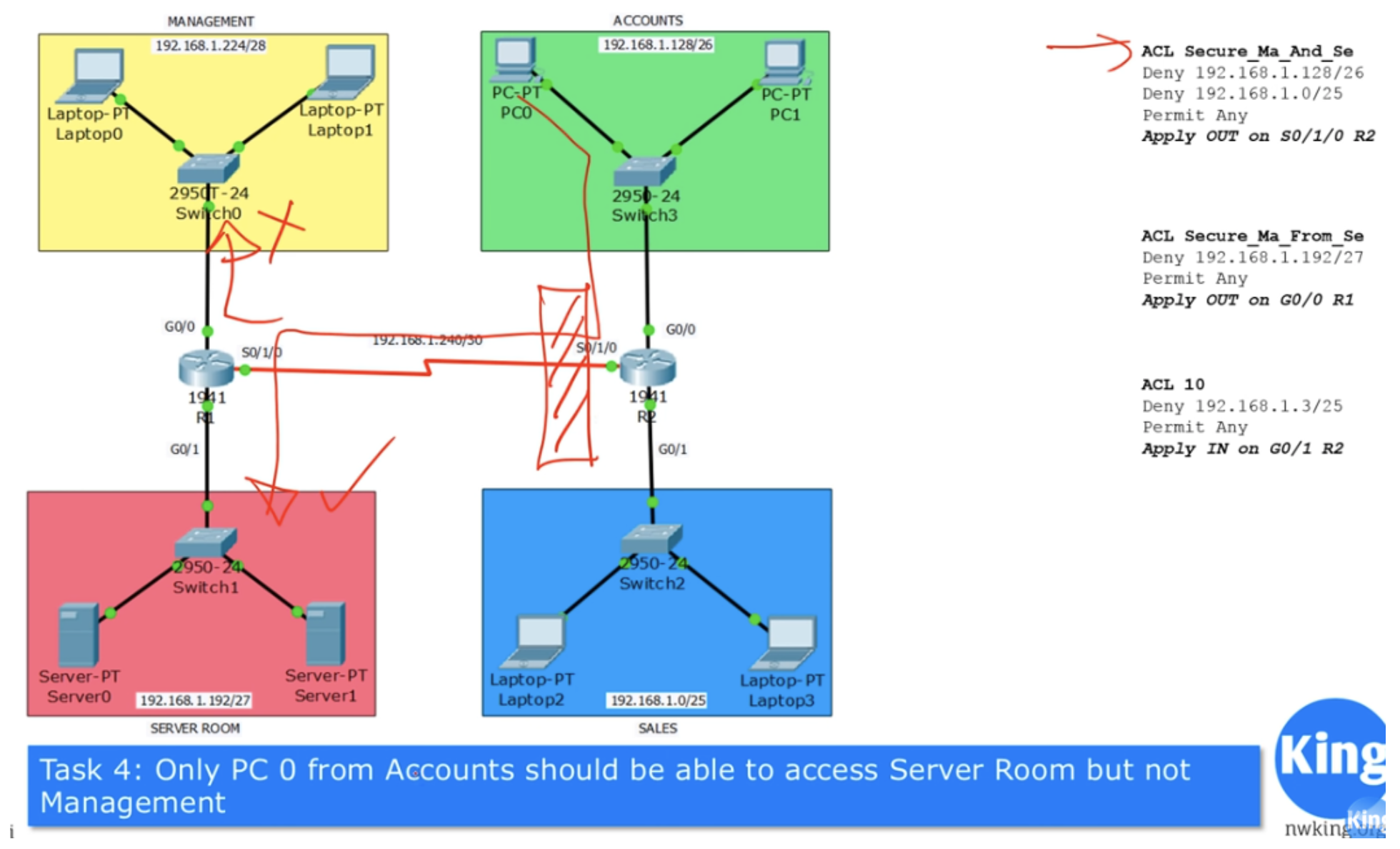
If you remember, the ACL from Task # 1 blocks all outgoing traffic on the S0 / 1/0 interface of router R2, but Task # 4 says that you need to ensure that traffic is transmitted only to PC0, so we should make an exception.
All the tasks that we are currently solving should help you in a real situation when setting up ACLs for the office network. For convenience, I used the classic form of recording, but I advise you to write all the lines manually on paper or print them on a computer in order to be able to make corrections to the recordings. In our case, according to the conditions of Task No. 1, a classic ACL is compiled. If we want to add an exception to it for PC0 of type Permit <IP address of PC0>, we can only place this line fourth in the list, after the line Permit Any. However, since the address of this computer is in the Deny 192.168.1.128/26 condition verification address range, its traffic will be blocked immediately after this condition is fulfilled and the router will simply not reach the fourth line that allows traffic from this IP address.
Therefore, I will have to completely redo the ACL of Task 1, deleting the first line and replacing it with Permit 192.168.1.130/26, which allows PC0 traffic, and then re-enter the lines that prohibit all accounting and sales department traffic.

Thus, in the first line we have a command for a specific address, and in the second - a common for the entire network in which this address is located. If you use the modern type of ACL, you can easily make changes to it by placing the Permit line 192.168.1.130/26 as the first command. If you have a classic ACL, you will need to completely remove it and then re-enter the commands in the correct order.
The solution to Problem # 4 is to place the Permit line 192.168.1.130/26 at the top of the ACL from Task # 1, because only in this case the PC0 traffic will leave the output interface of router R2 without hindrance. The traffic of PC1 will be completely blocked because its IP address is subject to the prohibition contained in the second line of the list.
We will now move on to Packet Tracer to make the necessary settings. I already configured the IP addresses of all devices because the simplified previous schemes were a little difficult to understand. In addition, I configured RIP between the two routers. On the given network topology, communication between all devices of 4 subnets is possible without any restrictions. But as soon as we apply the ACL, traffic will begin to be filtered.
I will start from the finance department PC1 and try to ping the IP address 192.168.1.194, which belongs to Server0 located in the server room. As you can see, pinging is successful without any problems. I am also successfully pinging the laptop of the management department's Laptop0. The first packet is discarded due to ARP, the remaining 3 are freely pinged.
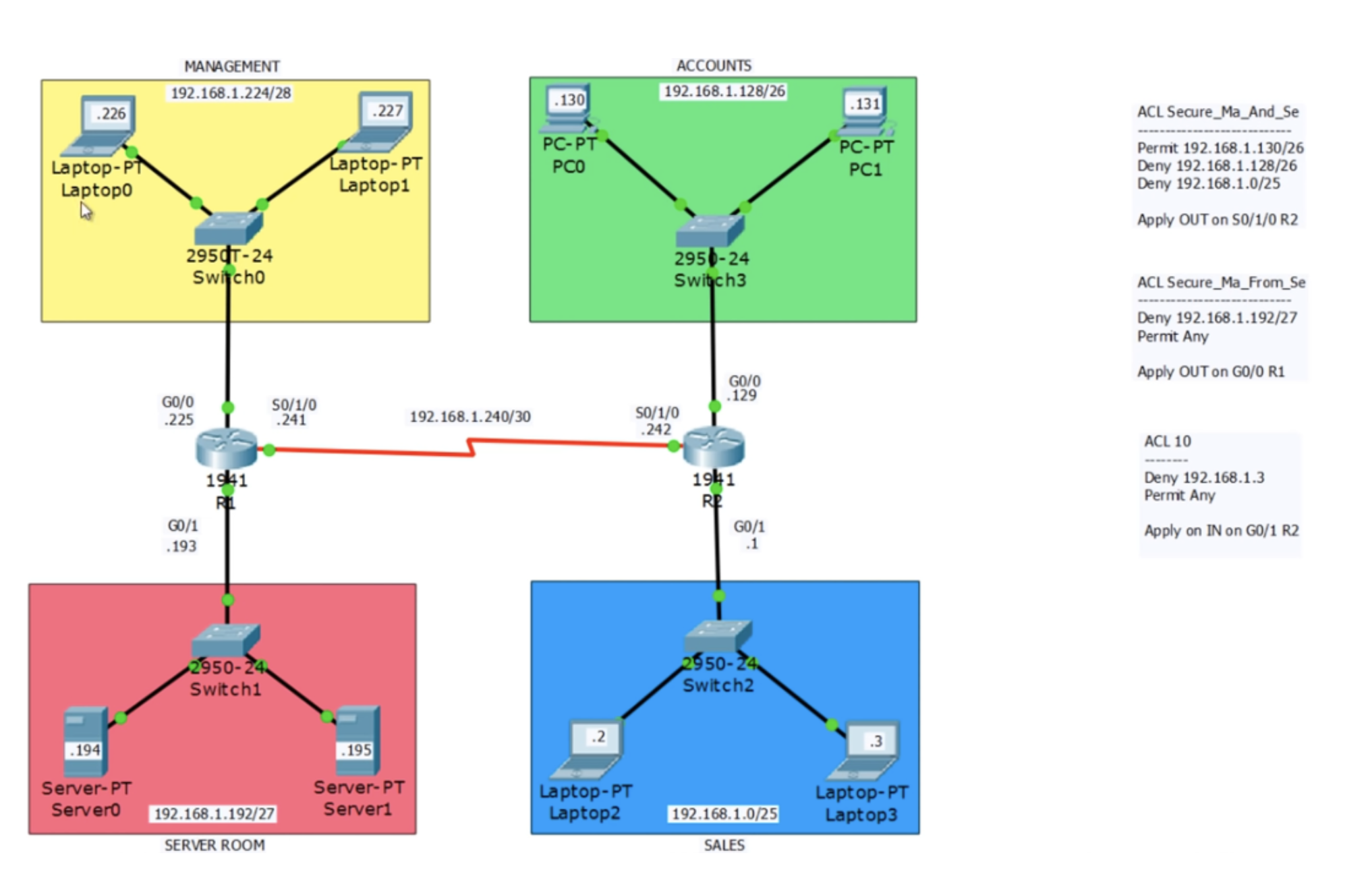
In order to organize traffic filtering, I go into the settings of the R2 router, activate the global configuration mode and am going to create a list of ACLs of a modern look. We also have a classic ACL 10. To create the first list, I enter a command in which you need to specify the same list name that we wrote on paper: ip access-list standard ACL Secure_Ma_And_Se. After that, the system gives hints of possible parameters: I can choose deny, exit, no, permit or remark, and also enter the Sequence Number from 1 to 2147483647. If I do not, the system will assign it automatically.
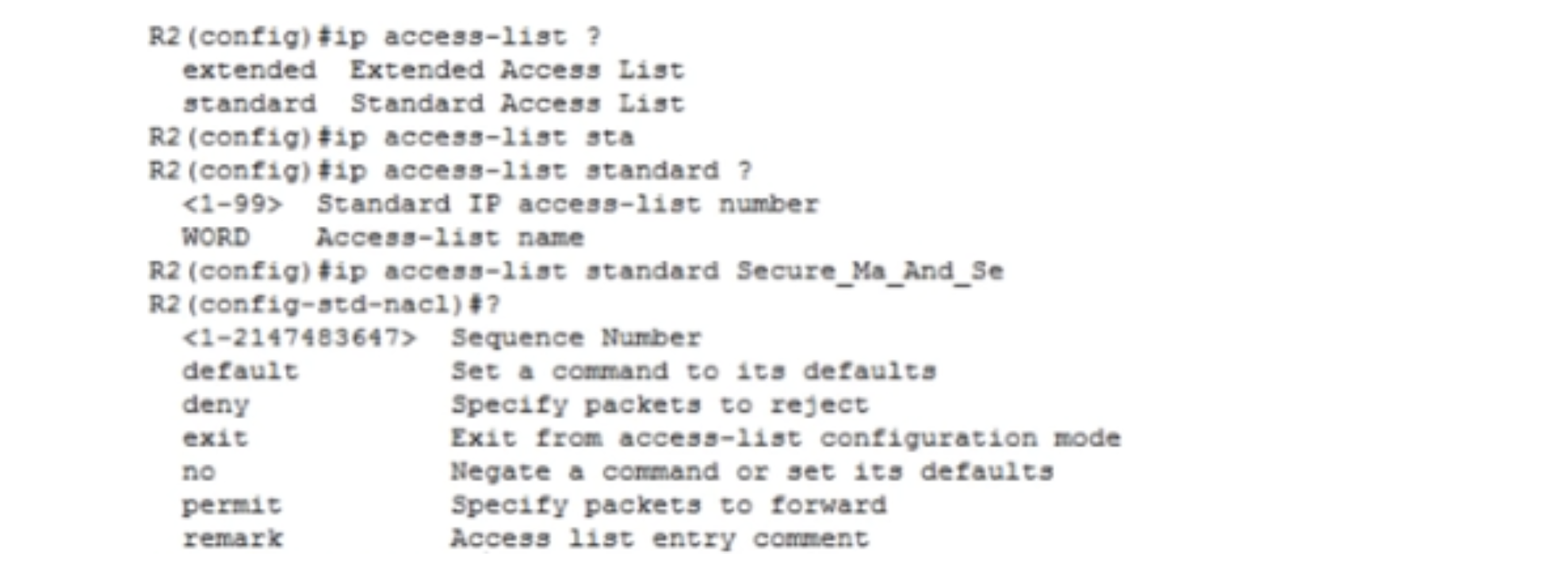
Therefore, I do not enter this number, but immediately proceed to the permit host 192.168.1.130 command, since this permission is valid for a specific PC0 device. I can also use the wildcard mask, now I will show how to do it.
Next, I enter the deny 192.168.1.128 command. Since we have / 26, I use the backward mask and supplement the command with it: deny 192.168.1.128 0.0.0.63. Thus, I deny 192.168.1.128/26 network traffic.
Similarly, I block traffic from the following network: deny 192.168.1.0 0.0.0.127. All other traffic is allowed, so I enter the permit any command. Next, I have to apply this list to the interface, so I use the int s0 / 1/0 command. Then I type ip access-group Secure_Ma_And_Se, and the system gives a hint with a choice of interface - in for incoming packets and out for outgoing ones. We need to apply the ACL to the output interface, so I use the ip access-group Secure_Ma_And_Se out command.
Let's go to the PC0 command line and ping the IP address 192.168.1.194, which belongs to Server0. Ping is successful because we used a special ACL condition for PC0 traffic. If I do the same from PC1, the system will give an error: “destination host is not available”, because traffic from other accounting IP addresses is blocked for server access.
By logging into the R2 CLI of the router and typing the show ip address-lists command, you can see how the traffic of the financial department network was routed - it shows how many times ping was skipped according to the permission and how many times it was blocked according to the ban.
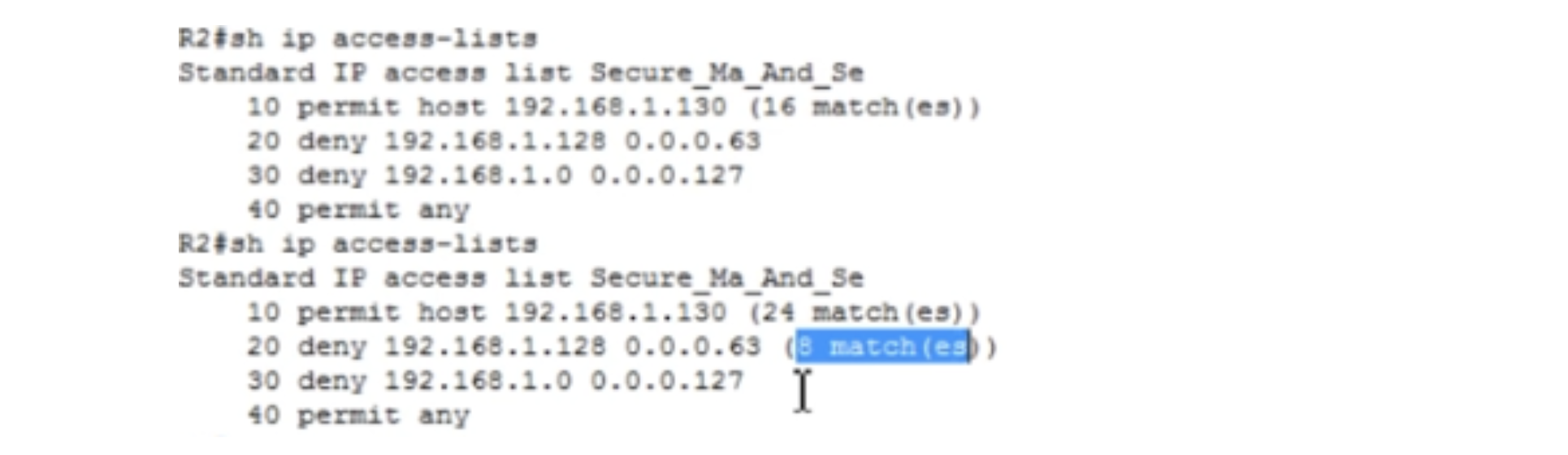
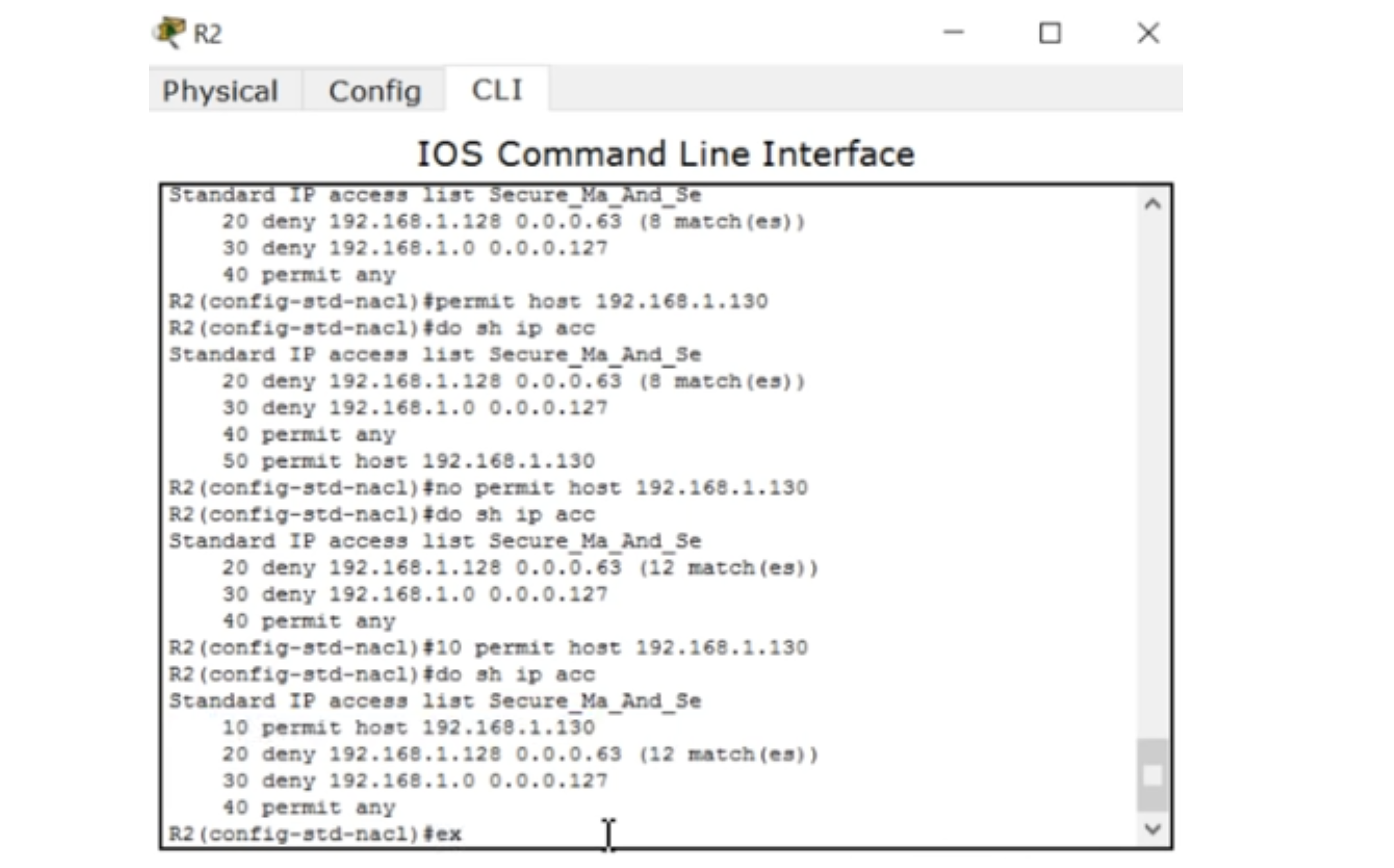
We can always go into the settings of the router and see the access list. Thus, the conditions of Tasks No. 1 and No. 4 are fulfilled. Let me show you one more thing. If I want to fix something, I can enter the global configuration mode of R2 settings, enter the ip access-list standard Secure_Ma_And_Se command and then the command “host 192.168.1.130 is not allowed” - no permit host 192.168.1.130.
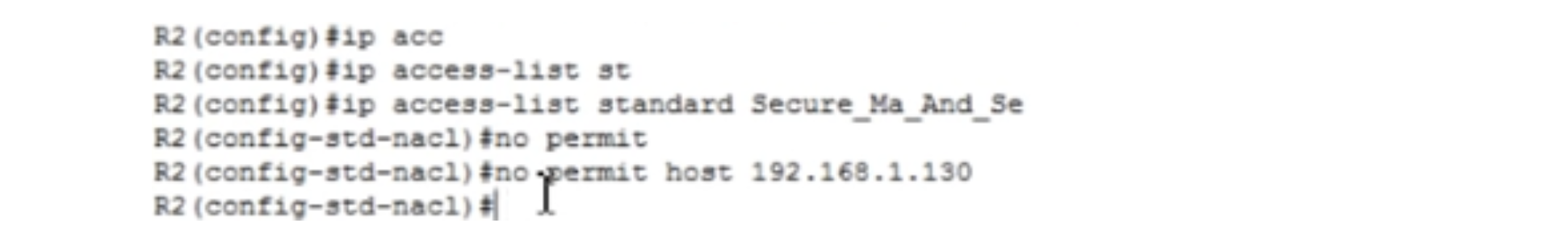
If we look at the access list again, we will see that line 10 has disappeared, we only have lines 20,30 and 40 left. In this way, we can edit the ACL access list in the settings of the router, but only if it is not in a classic form.
Now let's move on to the third ACL, because it also concerns the R2 router. It says that any traffic from the Laptop3 should not leave the network of the sales department. In this case, Laptop2 should communicate with the computers of the financial department without any problems. To check this, I ping the IP address 192.168.1.130 from this laptop and make sure everything works.
Now I will go to the command line of Laptop3 and ping the address 192.168.1.130. Pinging is successful, but we don’t need it, since by the condition of the task Laptop3 can only communicate with Laptop2 located on the same network of the sales department. To do this, create another ACL using the classic method.
I will return to the R2 settings and try to recover the deleted record 10 using the permit host 192.168.1.130 command. You see that this entry appeared at the end of the list at number 50. However, access will not work anyway, because the line with the resolution of a specific host is at the end of the list, and the line that prohibits all network traffic is at the top of the list. If we try to ping management0 laptop Laptop0 from the PC0 computer, we get the message “destination host is not available”, despite the fact that the ACL has an allow record at number 50.
Therefore, if you want to edit the existing ACL, you need to enter the no permit host 192.168.1.130 command in R2 mode (config-std-nacl), check that line 50 has disappeared from the list, and enter the 10 permit host 192.168.1.130 command. We see that now the list has acquired its original form, where this entry took the first line. Sequence numbers help edit the list in any form, so the modern ACL form is much more convenient than the classic one.
Now I will show how the classical form of the ACL 10 works. To use the classic list, you need to enter the access – list 10? Command, and, following the prompt, select the desired action: deny, permit or remark. Then I enter the line access – list 10 deny host, after which I type the command access – list 10 deny 192.168.1.3 and add a backward mask. Since we have a host, the direct subnet mask is 255.255.255.255, and the return is 0.0.0.0. As a result, to prohibit host traffic, I must enter the access – list 10 deny 192.168.1.3 0.0.0.0 command. After that, you need to specify permissions, for which I type the command access – list 10 permit any. This list needs to be applied to the G0 / 1 interface of router R2, so I consistently enter the commands in g0 / 1, ip access-group 10 in. Regardless of whether the list is used, classic or modern, the application of this list to the interface is carried out by the same commands.
To check the settings are correct, I go to the Laptop3 command line terminal and try to ping the IP address 192.168.1.130 - as you can see, the system reports that the destination host is unavailable.
Let me remind you that you can use the show ip access-lists command and the show access-lists command to check the list. We must solve another problem that relates to the router R1. To do this, I go to the CLI of this router and go into global configuration mode and enter the ip access-list standard Secure_Ma_From_Se command. Since we have a network 192.168.1.192/27, its subnet mask will be 255.255.255.224, which means that the reverse mask will be 0.0.0.31 and you need to enter the deny 192.168.1.192 0.0.0.31 command. Since all other traffic is allowed, the list ends with the permit any command. In order to apply the ACL to the output interface of the router, the ip access-group Secure_Ma_From_Se out command is used.

Now I will go to the Server0 command line terminal of the server and try to ping the Management0 Laptop0 at the IP address 192.168.1.226. The attempt failed, but if I send a ping to the address 192.168.1.130, the connection will be established without problems, that is, we forbade the server computer to communicate with the management department, but allowed communication with all other devices in other departments. Thus, we successfully solved all 4 problems.
Let me show you something else. We go into the settings of the R2 router, where we have 2 types of ACLs - classic and modern. Suppose I want to edit ACL 10, Standard IP access list 10, which in the classic form consists of two entries 10 and 20. If you use the do show run command, you can see that at first we have a modern access list of 4 entries without numbers under the general heading Secure_Ma_And_Se, and below are two ACL 10 entries of the classic form with the name of the same access-list 10 being repeated.
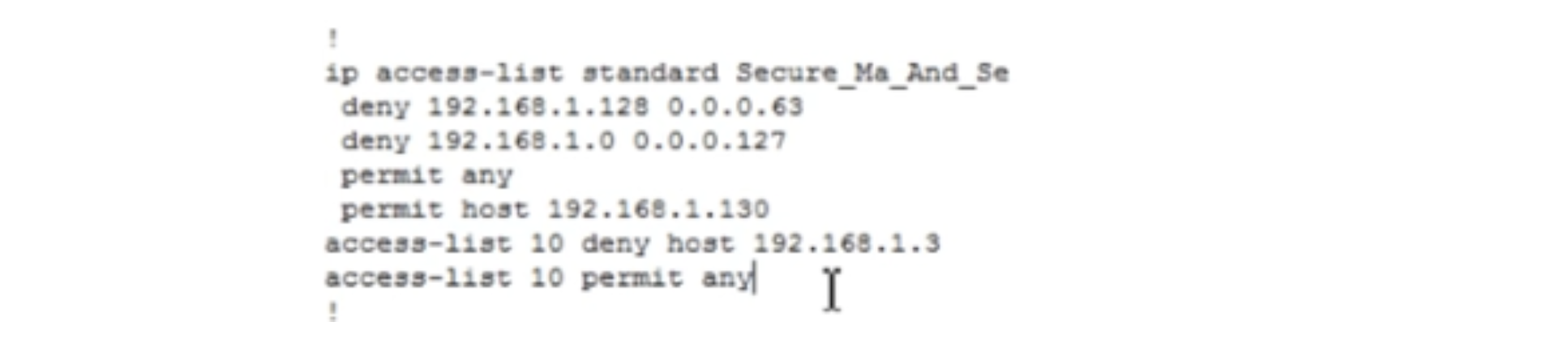
If I want to make some changes, for example, to delete the deny host 192.168.1.3 entry and enter the entry for the device from another network, I need to use the delete command for this entry only: no access-list 10 deny host 192.168.1.3. But as soon as I enter this command, all entries in the ACL 10 will disappear completely. That's why the classic look of the ACL is very inconvenient for editing. The modern recording method is much more convenient to use, as it allows free editing.
In order to learn the material of this video tutorial, I advise you to review it again and try to solve the problems yourself without prompting. ACL is an important topic of the CCNA course, and many are embarrassed, for example, by creating a wildcard mask. I assure you that it’s enough to understand the concept of mask conversion, and everything will become much simpler. Remember that the most important thing in understanding the topics of the CCNA course is practical training, because only practice will help you understand a particular Cisco concept. Practice is not copy-paste of my teams, but solving problems in my own way. Ask questions to yourself: what needs to be done to block the flow of traffic from here to where to apply the conditions and so on, and try to answer them.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

We found that accounting and sales department traffic can be blocked on the R2 exit interface using the ACL listed.

Do not worry about the format of this list, it is only needed as an example to understand the essence of the ACL. We will get to the right format as soon as we get started with Packet Tracer.
Problem number 2 is as follows: the server can communicate with any hosts except the hosts of the management department. That is, the server computers can have access to any computers of the sales and accounting department, but should not have access to the computers of the management department. This means that the server IT staff should not have remote access to the computer of the head of the management department, and in case of a malfunction, come to his office and fix the problem on the spot. Keep in mind that this task does not carry any practical sense, because I don’t know the reasons why the server room could not communicate over the network with the management department, so in this case we just consider a case study.
To solve this problem, you first need to determine the path of traffic transfer. Data from the server is fed to the input interface G0 / 1 of the router R1 and sent to the management department via the output interface G0 / 0.

If we apply the Deny condition 192.168.1.192/27 to the input interface G0 / 1, and as you remember, the standard ACLs are placed closer to the traffic source, we will block all traffic altogether, including the sales and accounting department.

Since we want to block only traffic directed to the management department, we must apply ACLs to the output interface G0 / 0. You can solve this problem only by placing the ACL closer to the destination. At the same time, traffic from the accounting network and the sales department should freely reach the management department, so the last line of the list will be the Permit any command - allow any traffic except the traffic specified in the previous condition.
Let's move on to Problem 3: Laptop 3 from the sales department should not have access to any devices other than those located on the local network of the sales department. Suppose that a trainee is working at this computer and should not go beyond his LAN.
In this case, you need to apply the ACL on the input interface G0 / 1 of router R2. If we assign the IP address 192.168.1.3/25 to this computer, then the Deny condition 192.168.1.3/25 must be met, and traffic from any other IP address should not be blocked, so Permit any will be the last line of the list.

At the same time, traffic prohibition will not have any effect on Laptop2.
The next will be Task No. 4: only the computer PC0 of the finance department can have access to the server network, but not the management department.

If you remember, the ACL from Task # 1 blocks all outgoing traffic on the S0 / 1/0 interface of router R2, but Task # 4 says that you need to ensure that traffic is transmitted only to PC0, so we should make an exception.
All the tasks that we are currently solving should help you in a real situation when setting up ACLs for the office network. For convenience, I used the classic form of recording, but I advise you to write all the lines manually on paper or print them on a computer in order to be able to make corrections to the recordings. In our case, according to the conditions of Task No. 1, a classic ACL is compiled. If we want to add an exception to it for PC0 of type Permit <IP address of PC0>, we can only place this line fourth in the list, after the line Permit Any. However, since the address of this computer is in the Deny 192.168.1.128/26 condition verification address range, its traffic will be blocked immediately after this condition is fulfilled and the router will simply not reach the fourth line that allows traffic from this IP address.
Therefore, I will have to completely redo the ACL of Task 1, deleting the first line and replacing it with Permit 192.168.1.130/26, which allows PC0 traffic, and then re-enter the lines that prohibit all accounting and sales department traffic.

Thus, in the first line we have a command for a specific address, and in the second - a common for the entire network in which this address is located. If you use the modern type of ACL, you can easily make changes to it by placing the Permit line 192.168.1.130/26 as the first command. If you have a classic ACL, you will need to completely remove it and then re-enter the commands in the correct order.
The solution to Problem # 4 is to place the Permit line 192.168.1.130/26 at the top of the ACL from Task # 1, because only in this case the PC0 traffic will leave the output interface of router R2 without hindrance. The traffic of PC1 will be completely blocked because its IP address is subject to the prohibition contained in the second line of the list.
We will now move on to Packet Tracer to make the necessary settings. I already configured the IP addresses of all devices because the simplified previous schemes were a little difficult to understand. In addition, I configured RIP between the two routers. On the given network topology, communication between all devices of 4 subnets is possible without any restrictions. But as soon as we apply the ACL, traffic will begin to be filtered.
I will start from the finance department PC1 and try to ping the IP address 192.168.1.194, which belongs to Server0 located in the server room. As you can see, pinging is successful without any problems. I am also successfully pinging the laptop of the management department's Laptop0. The first packet is discarded due to ARP, the remaining 3 are freely pinged.

In order to organize traffic filtering, I go into the settings of the R2 router, activate the global configuration mode and am going to create a list of ACLs of a modern look. We also have a classic ACL 10. To create the first list, I enter a command in which you need to specify the same list name that we wrote on paper: ip access-list standard ACL Secure_Ma_And_Se. After that, the system gives hints of possible parameters: I can choose deny, exit, no, permit or remark, and also enter the Sequence Number from 1 to 2147483647. If I do not, the system will assign it automatically.

Therefore, I do not enter this number, but immediately proceed to the permit host 192.168.1.130 command, since this permission is valid for a specific PC0 device. I can also use the wildcard mask, now I will show how to do it.
Next, I enter the deny 192.168.1.128 command. Since we have / 26, I use the backward mask and supplement the command with it: deny 192.168.1.128 0.0.0.63. Thus, I deny 192.168.1.128/26 network traffic.
Similarly, I block traffic from the following network: deny 192.168.1.0 0.0.0.127. All other traffic is allowed, so I enter the permit any command. Next, I have to apply this list to the interface, so I use the int s0 / 1/0 command. Then I type ip access-group Secure_Ma_And_Se, and the system gives a hint with a choice of interface - in for incoming packets and out for outgoing ones. We need to apply the ACL to the output interface, so I use the ip access-group Secure_Ma_And_Se out command.
Let's go to the PC0 command line and ping the IP address 192.168.1.194, which belongs to Server0. Ping is successful because we used a special ACL condition for PC0 traffic. If I do the same from PC1, the system will give an error: “destination host is not available”, because traffic from other accounting IP addresses is blocked for server access.
By logging into the R2 CLI of the router and typing the show ip address-lists command, you can see how the traffic of the financial department network was routed - it shows how many times ping was skipped according to the permission and how many times it was blocked according to the ban.

We can always go into the settings of the router and see the access list. Thus, the conditions of Tasks No. 1 and No. 4 are fulfilled. Let me show you one more thing. If I want to fix something, I can enter the global configuration mode of R2 settings, enter the ip access-list standard Secure_Ma_And_Se command and then the command “host 192.168.1.130 is not allowed” - no permit host 192.168.1.130.

If we look at the access list again, we will see that line 10 has disappeared, we only have lines 20,30 and 40 left. In this way, we can edit the ACL access list in the settings of the router, but only if it is not in a classic form.
Now let's move on to the third ACL, because it also concerns the R2 router. It says that any traffic from the Laptop3 should not leave the network of the sales department. In this case, Laptop2 should communicate with the computers of the financial department without any problems. To check this, I ping the IP address 192.168.1.130 from this laptop and make sure everything works.
Now I will go to the command line of Laptop3 and ping the address 192.168.1.130. Pinging is successful, but we don’t need it, since by the condition of the task Laptop3 can only communicate with Laptop2 located on the same network of the sales department. To do this, create another ACL using the classic method.
I will return to the R2 settings and try to recover the deleted record 10 using the permit host 192.168.1.130 command. You see that this entry appeared at the end of the list at number 50. However, access will not work anyway, because the line with the resolution of a specific host is at the end of the list, and the line that prohibits all network traffic is at the top of the list. If we try to ping management0 laptop Laptop0 from the PC0 computer, we get the message “destination host is not available”, despite the fact that the ACL has an allow record at number 50.
Therefore, if you want to edit the existing ACL, you need to enter the no permit host 192.168.1.130 command in R2 mode (config-std-nacl), check that line 50 has disappeared from the list, and enter the 10 permit host 192.168.1.130 command. We see that now the list has acquired its original form, where this entry took the first line. Sequence numbers help edit the list in any form, so the modern ACL form is much more convenient than the classic one.

Now I will show how the classical form of the ACL 10 works. To use the classic list, you need to enter the access – list 10? Command, and, following the prompt, select the desired action: deny, permit or remark. Then I enter the line access – list 10 deny host, after which I type the command access – list 10 deny 192.168.1.3 and add a backward mask. Since we have a host, the direct subnet mask is 255.255.255.255, and the return is 0.0.0.0. As a result, to prohibit host traffic, I must enter the access – list 10 deny 192.168.1.3 0.0.0.0 command. After that, you need to specify permissions, for which I type the command access – list 10 permit any. This list needs to be applied to the G0 / 1 interface of router R2, so I consistently enter the commands in g0 / 1, ip access-group 10 in. Regardless of whether the list is used, classic or modern, the application of this list to the interface is carried out by the same commands.
To check the settings are correct, I go to the Laptop3 command line terminal and try to ping the IP address 192.168.1.130 - as you can see, the system reports that the destination host is unavailable.
Let me remind you that you can use the show ip access-lists command and the show access-lists command to check the list. We must solve another problem that relates to the router R1. To do this, I go to the CLI of this router and go into global configuration mode and enter the ip access-list standard Secure_Ma_From_Se command. Since we have a network 192.168.1.192/27, its subnet mask will be 255.255.255.224, which means that the reverse mask will be 0.0.0.31 and you need to enter the deny 192.168.1.192 0.0.0.31 command. Since all other traffic is allowed, the list ends with the permit any command. In order to apply the ACL to the output interface of the router, the ip access-group Secure_Ma_From_Se out command is used.

Now I will go to the Server0 command line terminal of the server and try to ping the Management0 Laptop0 at the IP address 192.168.1.226. The attempt failed, but if I send a ping to the address 192.168.1.130, the connection will be established without problems, that is, we forbade the server computer to communicate with the management department, but allowed communication with all other devices in other departments. Thus, we successfully solved all 4 problems.
Let me show you something else. We go into the settings of the R2 router, where we have 2 types of ACLs - classic and modern. Suppose I want to edit ACL 10, Standard IP access list 10, which in the classic form consists of two entries 10 and 20. If you use the do show run command, you can see that at first we have a modern access list of 4 entries without numbers under the general heading Secure_Ma_And_Se, and below are two ACL 10 entries of the classic form with the name of the same access-list 10 being repeated.

If I want to make some changes, for example, to delete the deny host 192.168.1.3 entry and enter the entry for the device from another network, I need to use the delete command for this entry only: no access-list 10 deny host 192.168.1.3. But as soon as I enter this command, all entries in the ACL 10 will disappear completely. That's why the classic look of the ACL is very inconvenient for editing. The modern recording method is much more convenient to use, as it allows free editing.
In order to learn the material of this video tutorial, I advise you to review it again and try to solve the problems yourself without prompting. ACL is an important topic of the CCNA course, and many are embarrassed, for example, by creating a wildcard mask. I assure you that it’s enough to understand the concept of mask conversion, and everything will become much simpler. Remember that the most important thing in understanding the topics of the CCNA course is practical training, because only practice will help you understand a particular Cisco concept. Practice is not copy-paste of my teams, but solving problems in my own way. Ask questions to yourself: what needs to be done to block the flow of traffic from here to where to apply the conditions and so on, and try to answer them.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles