Security Week 35: statistics of leaked passwords and attacks through Google Drive
 Last week was marked by at least two high-profile events in the field of information security. For the first time in a long time, jailbreak is available for current Apple iPhone models with the latest iOS 12.4 firmware ( news , post on the hub). Jailbreak exploits a vulnerability that was closed in iOS 12.3, but apparently, by mistake, "opened" again in the latest version 12.4.
Last week was marked by at least two high-profile events in the field of information security. For the first time in a long time, jailbreak is available for current Apple iPhone models with the latest iOS 12.4 firmware ( news , post on the hub). Jailbreak exploits a vulnerability that was closed in iOS 12.3, but apparently, by mistake, "opened" again in the latest version 12.4.
A version of the VLC 3.0.8 video player has been released, in which several serious vulnerabilities have been closed ( news ), including those that ensure the execution of arbitrary code when opening a prepared .MKV file. It is noteworthy that in late July, serious vulnerabilities were also reported , also related to MKV processing, but those problems in the end turned out to be a figment of the researcher’s imagination and the strange configuration of his computer. But fresh vulnerabilities are real.
But today we’ll not talk about this, but about passwords. Google summed up the first results of using the Password Checkup extension for the Chrome browser and shared ( news , original blog post ) interesting statistics: only a quarter of passwords are changed to new ones, even if the user is notified of a leak. And at the same time, we will consider new attempts by spammers to break through to the user, this time through Google Drive.
The Password Checkup extension for the Chrome browser was released by Google in February this year. Last week, Google experts shared the first results of its work. The extension verifies all passwords entered by the user against the leak database. You can check your e-mail (and more recently, the password) manually, for example, on one of the most famous leaking resources - HaveIBeenPwned Troy Hunt. The extension automates this process and notifies you of a password or login-password pair, which is already in the database.
How do our passwords go public? There are two options: phishing or malware infection, when the password is stolen from you personally, or hacking the site or service that you use. Stolen passwords fall on the black market of personal information about users and sooner or later find themselves in open or conditionally open access. Google is checking a huge database of leaks of 4 billion records. Troy Hunt saved 8.4 billion records at the time of publication. There are a lot of duplicates and errors in such leaks, but given the massive hacks of popular services (from LinkedIn to Yahoo, from Dropbox to thousands of forums), we can confidently assume that all our passwords five years ago have long been in the public domain.

When determining a login with a leaked password, the Chrome extension displays a warning, reports the URL of the site on which the insecure password was used, and recommends changing it. How are passwords secure in the extension itself? It is not very clear that there is no separate privacy policy for Password Checkup, but it is emphasized that statistics on the operation of the extension are collected only anonymously. Troy Hunt has a “paranoid” mode - in the web service, only a hash is sent to the site to check the password for the leak database, but you can also download the hashed password database and check it offline.
And here is what anonymous statistics gathered from Google. In just six months, 650 thousand users took advantage of the extension. A good selection, but you must understand that among all the tens of millions of users of the Google Chrome browser this is a drop in the bucket. Therefore, in statistics, there may be a “survivor's mistake” - only those who already care about their safety put an extension, so there can be fewer “positives”. In total, 21 million unique login-password combinations for 746 thousand sites were checked. Of these, 316,000 were identified as unsafe, that is, one and a half percent of the total.
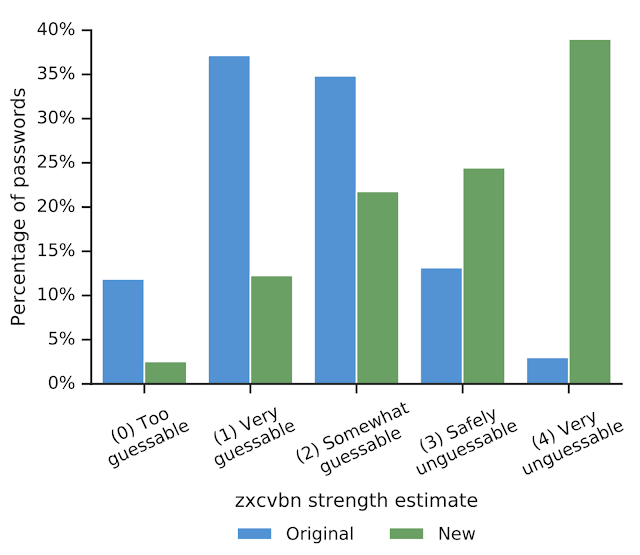
Only in 26% of cases from these 300+ thousand operations, users decided to change the password. 60% of the passwords were replaced by sufficiently strong ones - those that are difficult to select by brute force or dictionaries. There is a tendency to improve the quality of passwords. The graph above shows that the old passwords (which need to be replaced) were much more often simple. New (which replaced) in most cases were more difficult. The full results of the study are published here . The relative anonymity of the service is also confirmed there: on the Google side, work was done only with hashed passwords, and the domain name was cut off from logins in case of using an email address.
The Password Checkup extension allows you to evaluate how your own passwords are leaked. But it is not a solution to protect against future leaks, since the problem of reusing passwords remains. A really working solution is a password manager that generates random and complex passwords for each site individually. Some password managers also start using leak databases: in this case, you will quickly find out that one of the one-time passwords has been stolen, and you can easily replace only it, and not all passwords on all servers at once.
Google Drive Spam
Spammers continue to search for new ways to penetrate your phones and mailboxes, while actively using common network services. We recently wrote about a spam delivery method by creating an event on the Google calendar. In this case, the original message can be filtered by the GMail spam filter, but with the default calendar settings you will still receive a notification to the phone (sometimes at three in the morning). Today we’ll talk about spam through file sharing.
Google Drive and similar services for malicious attacks have been used for a long time, the initial tactic was to create pages with popular keywords, which, due to the high trust in Google Drive from search engines, fell into the top lines of search results. But there is also an alternative way: to share a document with a large number of users of Google services (taking e-mail from spam databases), and already in the document itself insert a link to a malicious, phishing or fraudulent site. It looks something like this:
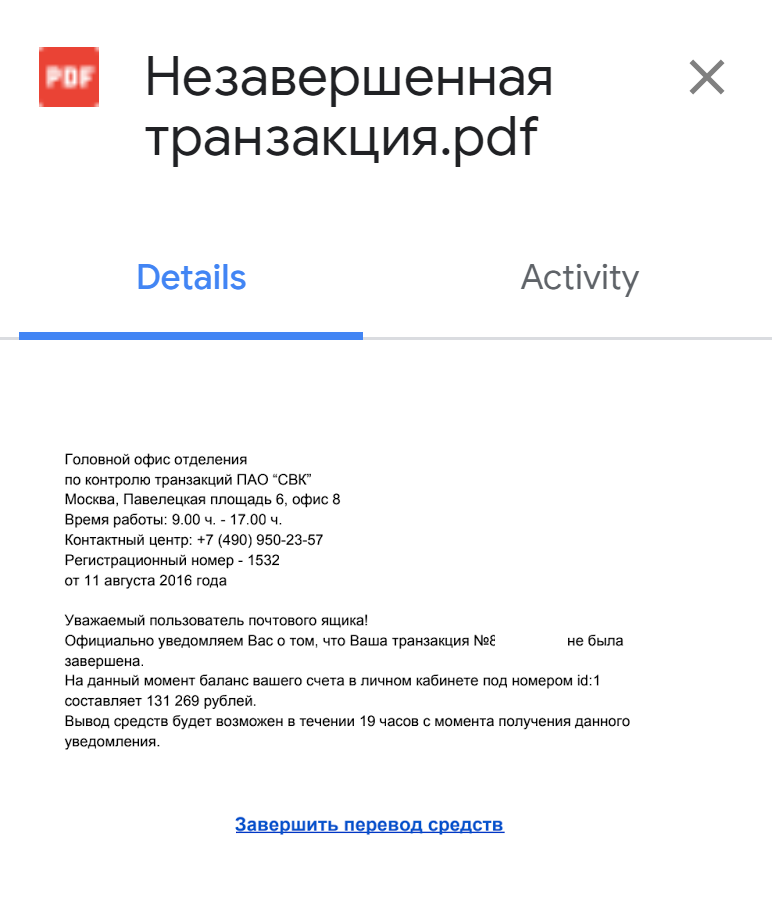
The document not only appears in the list of shared for your account. If the Google Drive application is installed on the phone (and it is usually installed there), then notification will also come to the smartphone. It seems the only way to get rid of notifications is to turn them off for the Google Drive app on your phone. In the Google Drive interface, you can only turn off the duplication of notifications in the mail, but this can break the workflow with legitimate contacts. And GMail itself blocks spam notifications quite successfully.
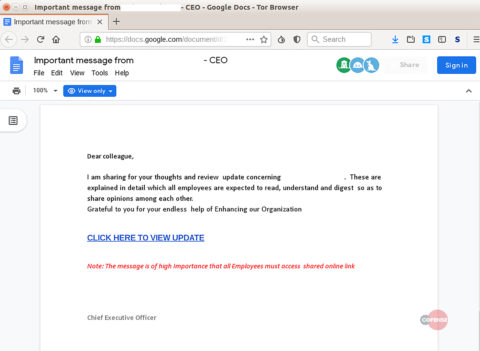
You can survive spam, the problem is that the exact same method is used for targeted attacks. An article on the Bleeping Computer website ( news , source ) provides examples of malicious attacks that use both Google Drive and, for example, the WeTransfer file sharing service. Everything is simple: we create a document (supposedly a template for an important working letter), send it on behalf of the big boss in the company to his subordinates. The document has a link (disguised as “make changes” or “update the document”), which leads either to a phishing site or to a page with malicious content.
A narrowly targeted campaign is more likely to break through the organization’s spam filter, and employees who are used to working with cloud services may not notice the catch. And such a scenario simply cannot be blocked, a combination of measures is required: a finely tuned spam filter, employee training and protection against malware. And by the way, massive spam through Google Docs can be sent (and has a chance to break through the filters) not only from one-day accounts, but also from users who look quite real. If your Google account password (Microsoft, Zoho and so on) is leaked according to the script described at the beginning of the post, then, in addition to all other troubles, your account can be used for such dark affairs.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
All Articles