[POSSIBLE] SORM decrypts HTTPS traffic to Mail.ru and ICQ
At the Chaos Constructions 2019 conference, Leonid darkk Evdokimov showed an interesting report about the SORM control panel accidentally discovered in the public domain. The report can be viewed here: darkk.net.ru/2019/cc In a nutshell: the panel with the statistics of the operation of the SORM software and hardware systems from MFI Soft stuck out on the Internet and everyone did not care.
At some point in time, raw dumps of intercepted traffic stuck out, which the search engine shodan.io managed to index. Here is one of these dumps: archive.li/RG9Lj
There are MAC addresses, IMEI phones and various other personal information. But the most interesting thing in these dumps is that there somehow got traffic to some hosts on port 443 (HTTPS) in the clear! That is, fully GET requests are visible, and this may mean that SORM can decrypt HTTPS. Let's try to think how this is possible.
Here's what the intercepted chunks of traffic look like. It can be seen that the connection occurs on port 443, but the GET request is visible in its entirety:
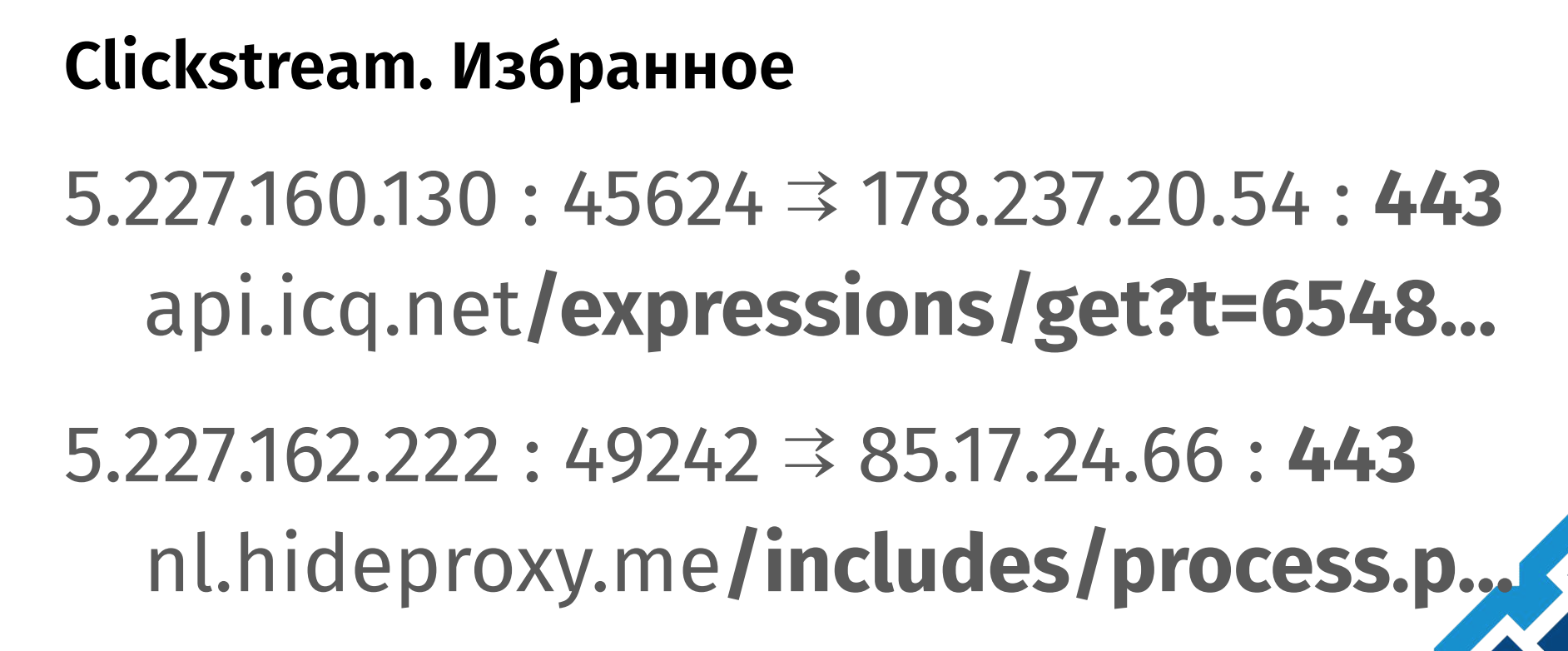
It is clear that the system is somehow gaining access to traffic that must be encrypted. How exactly this happens is not known exactly and there is no way to check it. Therefore, it remains only to build hypotheses.
Option 1: HTTP traffic on port 443
Usually, when sending HTTP traffic to the HTTPS port (443), the web server returns an error:

Error requesting HTTP port 443
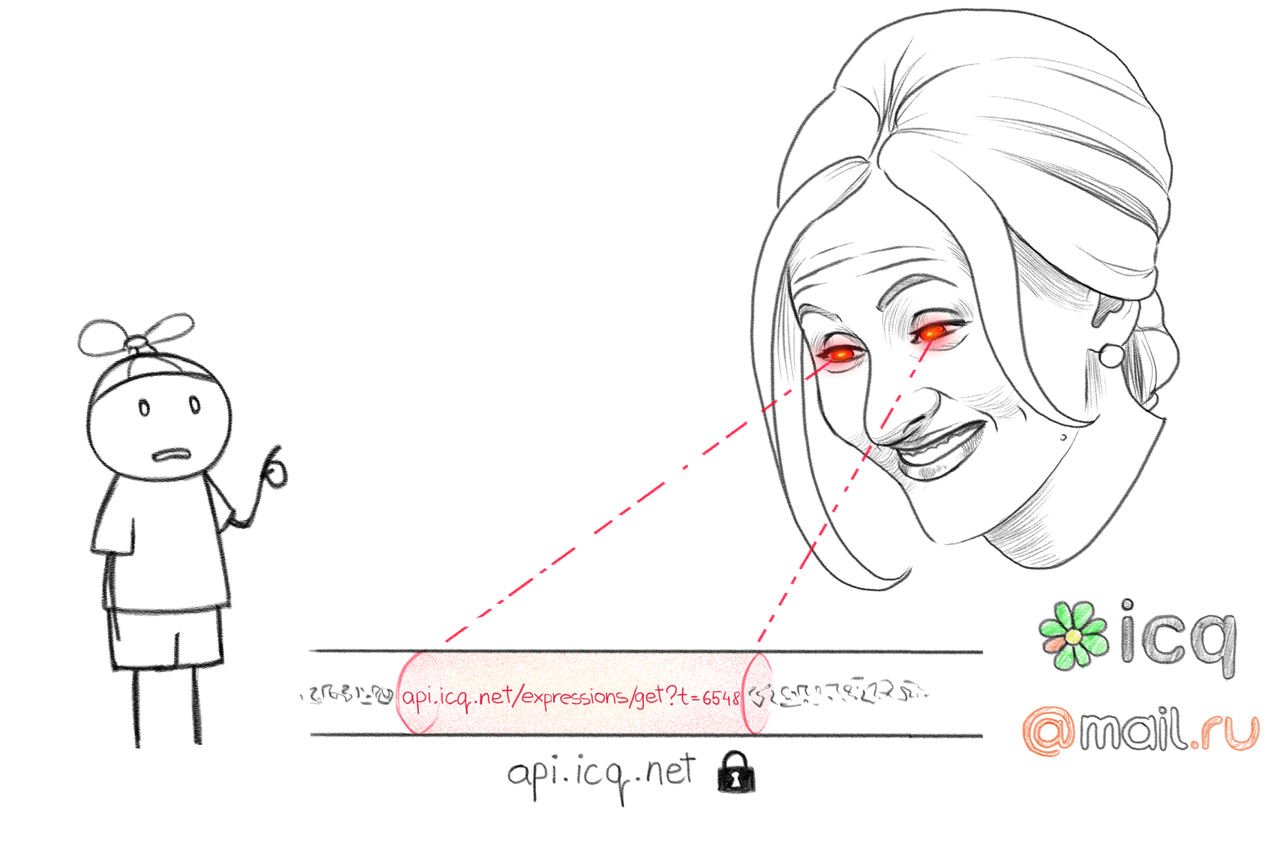
The author of the report suggests that some hosts might accept unencrypted HTTP traffic on port 443. Indeed, such hosts were found, for example, mra1.mail.ru.
This can be verified as follows:
curl -v http://mra1.mail.ru:443
, . .
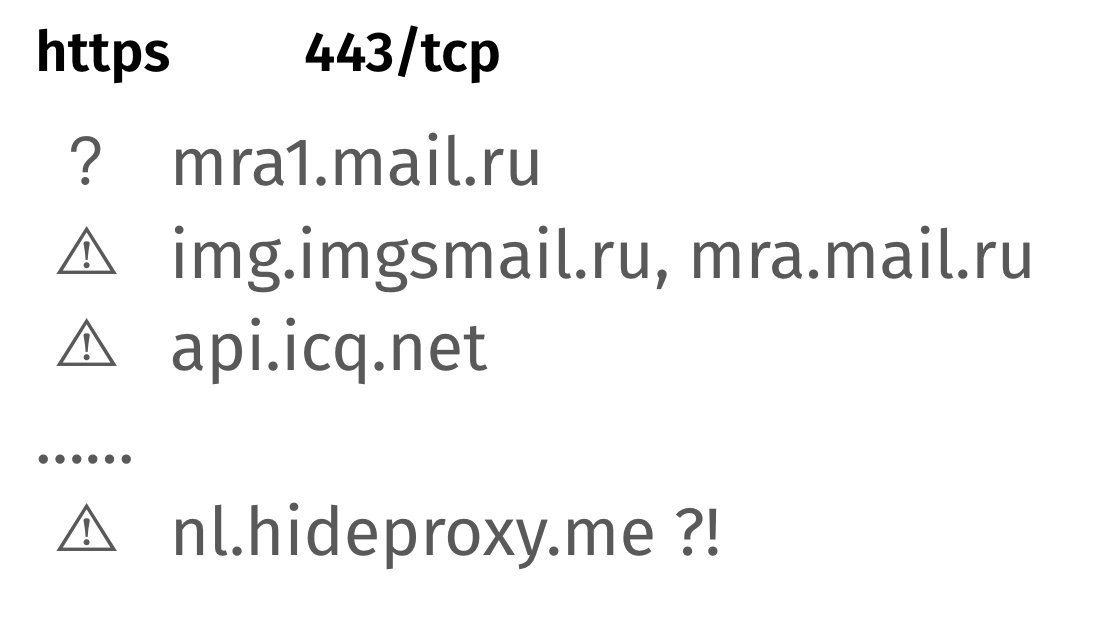
HTTP- HTTPS-
, . ICQ HTTPS HTTP. , . , , .
2:
TLS , (Perfect Forward Secrecy).
:
- . ICQ, MiTM-
- .
. , ., , .
, . , , , , ..
UPD
, - . , . HTTPS .
Mail.ru Group
ICQ HTTP- 443 . - , .. 443 .
ICQ - .
All Articles