Alive and living: ransomware viruses in 2019

Ransomware viruses, like other types of malware, evolve and change over the years - from simple lockers that prevented the user from entering the system, and “police” ransomware, which scared us with judicial prosecution for fictitious violations of the law, we came to encryption programs. These malware encrypt files on hard disks (or entire disks) and require ransom not for returning access to the system, but for the user’s information being not deleted, sold on a darknet or put up for public viewing on the network. Moreover, the payment of the ransom does not guarantee receipt of a key for decrypting files. And no, it was “a hundred years ago already,” but it is still an actual threat.
Given the success of hackers and the profitability of this type of attack, experts believe that in the future their frequency and ingenuity will only grow. According to Cybersecurity Ventures, in 2016 ransomware viruses attacked companies about once every 40 seconds, in 2019 it happens every 14 seconds, and in 2021 the frequency will increase to one attack in 11 seconds. It is worth noting that the required ransom (especially in targeted attacks on large companies or urban infrastructure) as a rule is many times lower than the damage caused by the attack. So, the May attack on the government structures of Baltimore, Maryland, in the USA, caused damage in the amount of more than 18 million dollars , with the amount of ransom declared by hackers of 76 thousand dollars in bitcoin equivalent. And the attack on the administration of Atlanta , Georgia, in August 2018 cost the city $ 17 million with the required ransom of $ 52 thousand.
Trend Micro specialists analyzed ransomware attacks in the first months of 2019, and in this article we will talk about the main trends that await the world in its second half.
Ransomware virus: a brief dossier
The meaning of the ransomware virus is clear from its very name: threatening to destroy (or, conversely, publish) information that is confidential or valuable to the user, hackers demand a ransom for returning access to it. For ordinary users, such an attack is unpleasant, but not critical: the threat of losing the music collection or vacation photos over the past ten years does not guarantee the payment of a ransom.
The situation for organizations looks completely different. Every minute of business downtime costs money, so the loss of access to the system, applications or data for a modern company is equal to losses. That is why the focus of attacks of ransomware viruses in recent years has gradually shifted from shelling by viruses to reducing activity and moving to targeted raids on organizations in areas in which the chance of getting a ransom and its size are greatest. In turn, organizations seek to protect themselves from threats in two main areas: by developing ways to effectively restore infrastructure and databases after attacks, as well as adopting more advanced cyber defense systems that detect and destroy malware in a timely manner.
In order to stay up to date and develop new solutions and technologies to combat malware, Trend Micro constantly analyzes the results obtained from its cybersecurity systems. According to Trend Micro Smart Protection Network , the situation with ransomware viruses in recent years looks like this:
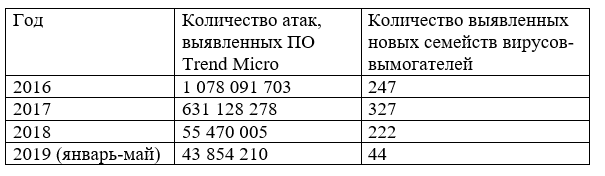
Victim Selection in 2019
This year, cybercriminals have clearly begun to take a more careful approach to the choice of victims: their goal is organizations that are worse protected and are willing to pay a large sum for the quick restoration of normal activities. That is why since the beginning of the year, several attacks have been recorded on government structures and the administration of large cities, including Lake City (ransom - 530 thousand US dollars) and Riviera Beach (ransom - 600 thousand US dollars) in the state of Florida, USA .
By industry, the main attack vectors look like this:
- 27% - government agencies;
- 20% - production;
- 14% - healthcare;
- 6% - retail;
- 5% - education.
Often cybercriminals use the OSINT method (search and gather information from publicly available sources) to prepare for an attack and evaluate its profitability. By collecting information, they better understand the organization’s business model and the reputation risks that it may suffer from an attack. Hackers also look for the most important systems and subsystems that can be completely isolated or disabled using ransomware viruses - this increases the chance of a ransom. Last but not least, the state of cybersecurity systems is assessed: it makes no sense to launch an attack on a company whose IT specialists are highly likely to repel it.
In the second half of 2019, this trend will still be relevant. Hackers will find new areas of activity in which violation of business processes leads to maximum losses (for example, transport, important infrastructure, energy).
Penetration and infection methods
Changes are also constantly taking place in this area. The most popular tools are phishing, malicious advertisements on websites and infected web pages, as well as exploits. At the same time, the main "accomplice" of attacks is still the user-employee who opens these sites and downloads files via links or from e-mail, which provokes further infection of the entire network of the organization.
However, in the second half of 2019, these tools will be added:
- more active use of attacks using social engineering (an attack in which the victim voluntarily performs the actions necessary for the hacker or provides information, considering, for example, that he is communicating with a representative of the organization’s management or client), which simplifies the collection of information about employees from public sources;
- the use of stolen credentials, for example, logins and passwords from remote administration systems, which can be purchased on the darknet;
- physical hacking and penetration, which will allow hackers to locate critical systems on the spot and neutralize the security system.
Attack Concealment Techniques
Thanks to the development of cybersecurity systems, which Trend Micro also contributes to, the discovery of the classic ransomware virus families has recently been greatly simplified. Machine learning and behavioral analysis technologies help identify malware even before it enters the system, so hackers have to come up with alternative methods to hide attacks.
Already known to experts in the field of IT security and new technologies of cybercriminals, they are aimed at neutralizing sandboxes for analyzing suspicious files and machine learning systems, developing fileless malware and using infected licensed software, including software from cybersecurity vendors and various remote services with access to the organization’s network.
Conclusions and recommendations
In general, we can say that in the second half of 2019, there is a high probability of targeted attacks on large organizations that are capable of paying a large ransom to cybercriminals. At the same time, hackers do not always develop hacking solutions and malware on their own. Some of them, for example, the infamous GandCrab team, which has already ceased operations , having earned about $ 150 million, continue to work under the RaaS (ransomware-as-a-service, or ransomware-as-a-service) scheme, similar to antiviruses and cyber protection systems). That is, not only their creators, but also “tenants” are engaged in the distribution of successful ransomware and crypto-lockers this year.
In such circumstances, organizations need to constantly update their cybersecurity systems and data recovery schemes in case of an attack, because the only effective way to deal with ransomware viruses is not to pay a ransom and deprive their authors of a source of profit.
All Articles