Firefox (already fixed) and Chrome allow Alt-Svc header to scan intranet ports
UPDATE : in the current Firefox 68, the vulnerability has already been fixed (thanks to Dukat ).
Trishita Tiwari and Ari Trachtenberg of Boston University published a paper showing a new attack method for scanning ports on hosts on a user's internal network or on a local host ( CVE-2019-11728 ). The attack is carried out using the Alt-Svc HTTP header, introduced in RFC-7838 HTTP Alternate Services (approved in 2016).
The Alt-Svc HTTP header allows you to redirect a request to a new host and port. This is used to balance the load. For example:
Alt-Svc: http/1.1="other.example.com:443";ma=200;persist=1
instructs the browser to connect to the other.example.org host on port 443 to receive the requested page using HTTP / 1.1. The "ma" parameter sets the maximum duration of the redirection. In addition to HTTP / 1.1, the HTTP / 2-over-TLS (h2), HTTP / 2-over plain text (h2c), SPDY (spdy) and QUIC (quic) protocols using UDP are supported.
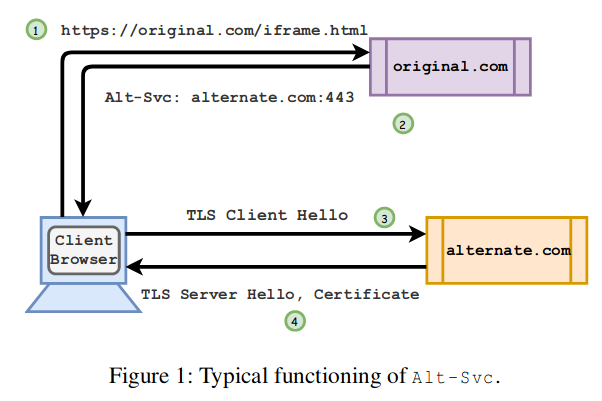
The attacking host can sequentially sort through the internal network addresses and network ports, using the delay between repeated requests as a sign: if the redirected resource is unavailable, the browser instantly receives an RST packet in response and immediately marks the alternative service unavailable and resets the redirection lifetime specified in the request. If the network port is open, then it takes more time to complete the connection (an attempt will be made to establish a connection with the appropriate packet exchange) and the browser will not respond instantly.
This also allows you to bypass restrictions on connections to ports that browsers consider unsafe for connections ( Firefox , Chrome ), for example, ports on mail and DNS services.
Possible attack methods other than port scanning:
- DDoS attacks with amplification. For example, the TLS handshake for non-HTTP services forces the server to transmit certificate information to the client, forcing the server to respond 60 times with more data than was requested.

- Bypass malware and phishing protection with Google Safe Browsing. Redirecting to a malicious host using Alt-Svc does not generate a warning.
- Tracking the user bypassing the protection from trackers. It uses an iframe that calls Alt-Svc to an external motion tracking handler. It can also be used to track users by providers who have a web page for logging in, for example, WiFi captive portal. The user's browser remembers the unique Alt-Svc for the iframe of the tracking domain. The next time you visit this page, you can see at the network level where the client’s browser will go.
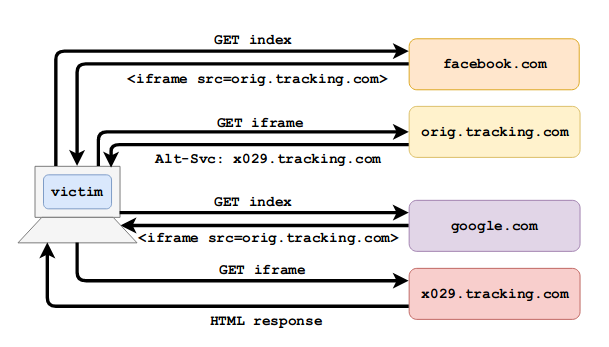
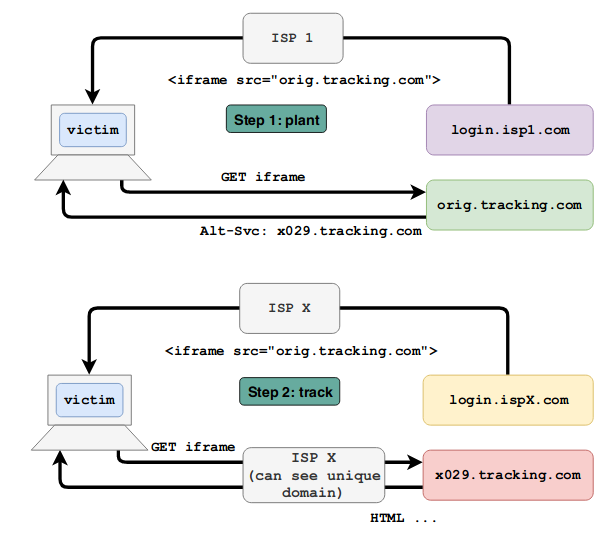
- If a site uses Alt-Svc redirection, then ISP (or any other man-in-the-middle), when a user goes to a specific page, can establish the fact of a previous visit to this site.
- IDS log clogging with false positives
For Firefox, Alt-Svc processing can be disabled as follows: about: config -> network.http.altsvc.enabled: false (thanks for the tip to Anonymous with opennet).
All Articles