Training Cisco 200-125 CCNA v3.0. Day 14. VTP, Pruning, and Native VLAN
Today we will continue our discussion of VLAN and discuss the VTP protocol, as well as the concepts of VTP Pruning and Native VLAN. In a previous video we talked about VTP, and the first thing that comes to your mind when you hear about VTP is that it is not a trunking protocol, despite what is called a “VLAN trunking protocol”.

As you know, there are two popular trunking protocols - the Cisco ISL proprietary protocol, which is not used today, and the 802.q protocol, which is used in network devices of various manufacturers to encapsulate trunking traffic. This protocol is also used in Cisco switches. We have already said that VTP is the VLAN synchronization protocol, that is, it is designed to synchronize the VLAN database in all switches of the network.

We mentioned various VTP modes - server, client, transparent. If the device uses server mode, this allows you to make changes, add or remove VLANs. Client mode does not allow changes to switch settings; you can configure a VLAN database only through a VTP server, and it will be replicated to all VTP clients. The switch in transparent mode does not make changes to its own VLAN database, but simply passes through itself and passes the changes to the next device in client mode. This mode is similar to disabling the VTP protocol on a specific device, turning it into a carrier of information about VLAN changes.
Back to Packet Tracer and the network topology discussed in the previous lesson. We configured the VLAN10 network for the sales department and the VLAN20 network of the marketing department, combining them with three switches.

Between switches SW0 and SW1, VLAN20 is connected, and between SW0 and SW2, VLAN10 is connected due to the fact that we added VLAN10 to the VLAN database of switch SW1.
In order to consider the operation of the VTP protocol, let's use one of the switches as a VTP server, let it be SW0. If you remember, by default all switches work in the VTP server mode. Let's go to the switch command line terminal and enter the show vtp status command. You see the current version of VTP protocol - 2 and revision number of configuration 4. If you remember, every time changes are made to the VTP database, the revision number is increased by one.
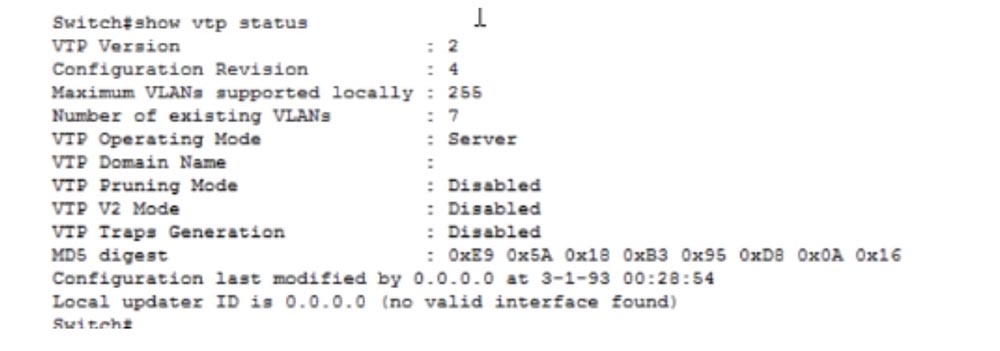
The maximum number of supported VLANs is 255. This number depends on the brand of a particular Cisco switch, since different switches can support a different number of local virtual networks. The number of existing VLANs is 7, in a minute we will consider what kind of network. VTP management mode - server, domain name is not set, VTP Pruning mode is disabled, we will return to this later. VTP V2 and VTP Traps Generation modes are also disabled. To take the 200-125 CCNA exam, you don’t need to know about the last two modes, so don’t worry about them.
Let's take a look at the VLAN database, for which we use the show vlan command. As we saw in the previous video, we have 4 unsupported networks: 1002, 1003, 1004, and 1005.
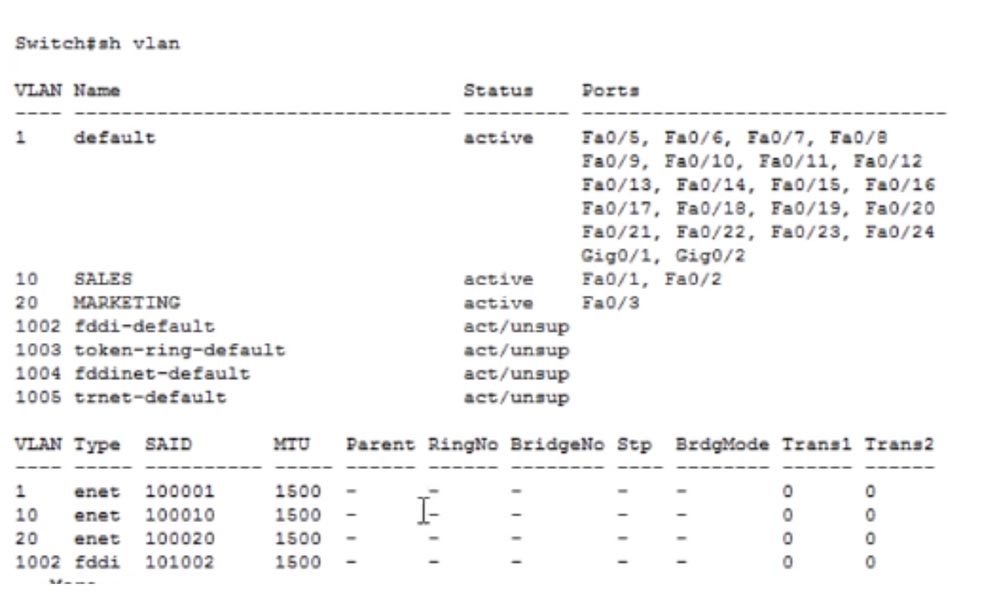
It also lists the 2 VLANs 10 and 20 we created and the default network VLAN1. Now let's move on to another switch and enter the same command to view the VTP status. You see that the revision number for this switch is 3, it is in VTP server mode and all other information is similar to the first switch. When I enter the show VLAN command, I will see that we made 2 changes in the settings, one less than the switch SW0, which is why the revision number of SW1 is 3. We made 3 changes in the default settings of the first switch, so its revision number increased to 4.
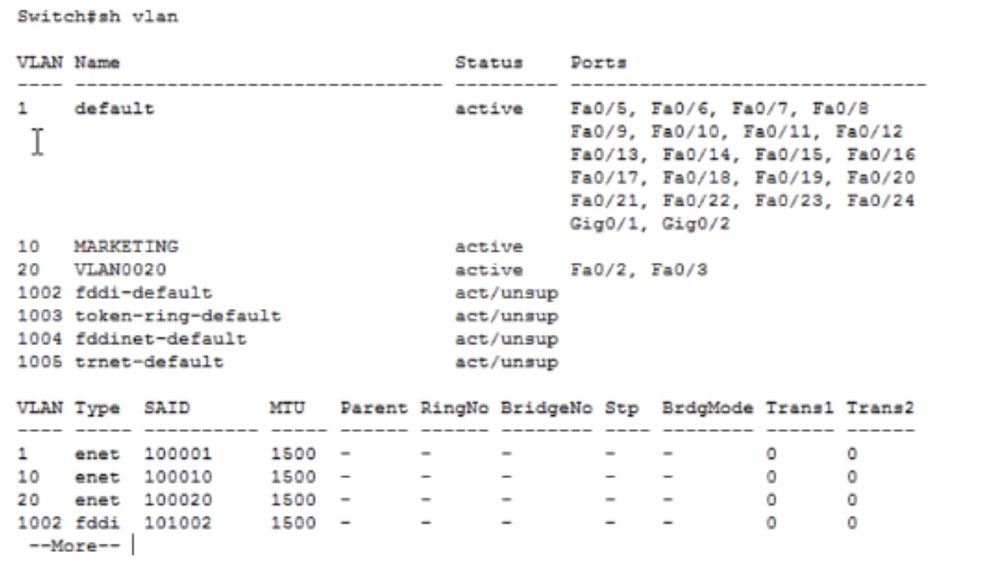
Now let's look at the status of SW2. The revision number here is 1, and this is strange. We must have a second revision, because 1 change was made to the settings. Let's look at the VLAN database.
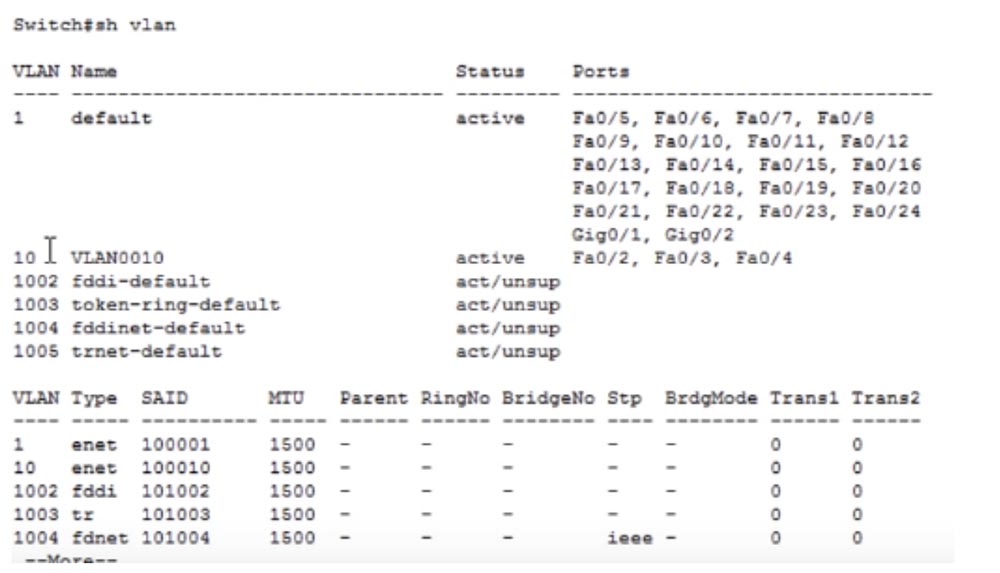
We made one change by creating a VLAN10 network, and I do not know why this information was not updated. Perhaps this was due to the fact that we do not have a real network, but a software network simulator, in which there may be errors. When you have the opportunity to work with real devices while practicing at Cisco, this will help you more than the Packet Tracer simulator. Another useful thing in the absence of real devices would be GNC3, or the Cisco network simulator. This is an emulator that uses the real operating system of the device, for example, a router. There is a difference between the simulator and the emulator - the first is a program that looks like a real router, but it is not. The emulator programmatically creates only the device itself, but uses real software for its operation. But if you don’t have the opportunity to work with real Cisco IOS software, the best option would be Packet Tracer.
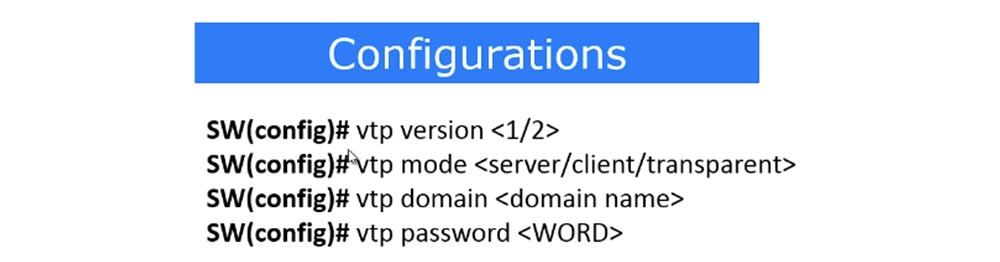
So, we need to configure SW0 as a VTP server, for this I go into global configuration mode and enter the vtp version 2 command. As I said, we can install the version of the protocol that we need - 1 or 2, in this case we need a second version. Next, with the vtp mode command, we set the VTP mode of the switch - server, client, or transparent. In this case, we need server mode, and after entering the vtp mode server command, the system displays a message that the device is already in server mode. Next, we need to configure the VTP domain, for which we use the vtp domain nwking.org command. Why is this needed? If there is another device with a higher revision number on the network, all other devices with a lower revision begin to replicate the VLAN database from this device. However, this only happens when the devices have the same domain name. For example, if you work in nwking.org, you specify this domain, if in Cisco, then the domain is Cisco.com, and so on. The domain name of your company’s devices allows you to distinguish them from devices of another company or any other external network devices. If you assign a company domain name to a device, then you make it part of the company's network.
The next thing to do is set a VTP password. It is needed so that a hacker, having a device with a large revision number, could not copy his VTP settings to your switch. I enter the cisco password using the vtp password cisco command. After that, replication of VTP data between switches will be possible only if the passwords match. If the wrong password is used, the VLAN database will not be updated.
Let's try to create some more VLANs. To do this, I use the config t command, with the vlan 200 command I create a network with the number 200, give it the name TEST and save the changes with the exit command. Then I create another vlan 500 network and call it TEST1. If you now enter the show vlan command, then in the virtual network table of the switch you can see these two new networks, to which no ports are assigned.
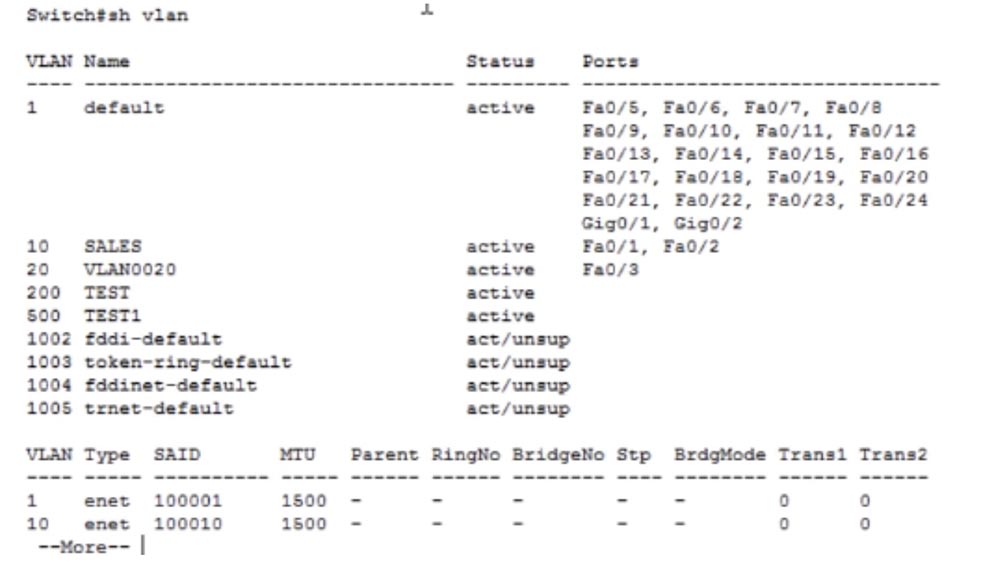
Let's move on to SW1 and see its VTP status. We see that nothing has changed here, except for the domain name, the number of VLANs has remained equal to 7. We do not see the appearance of the networks we created, because the VTP password does not match. Let's set the VTP password on this switch by entering the conf t, vtp pass and vtp password cisco commands in sequence. The system issued a message that the device VLAN database now uses the Cisco password. Let's take a look at the VTP status again to check if the information has been replicated. As you can see, the number of existing VLANs automatically increased to 9.
If you look at the VLAN database of this switch, you can see that the VLAN200 and VLAN500 networks we created automatically appeared in it.
The same thing needs to be done with the last switch SW2. Let's enter the show vlan command - you see that there were no changes in it. Similarly, there are no changes in VTP status. In order for this switch to update the information, you also need to configure a password, that is, enter the same commands as for SW1. After that, the number of VLANs in the SW2 status will increase to 9.
That's what the VTP protocol is for. This is a great thing, which provides automatic updating of information in all client network devices after making changes to the server device. You do not need to manually make changes to the VLAN database of all switches - replication occurs automatically. If you have 200 network devices, your changes will be saved simultaneously on all two hundred devices. Just in case, we need to make sure that SW2 is also a VTP client, so go to the settings with the config t command and enter the vtp mode client command.
Thus, in our network, only the first switch is in VTP Server mode, the other two are in VTP Client mode. If now I go into the settings of SW2 and enter the vlan 1000 command, I get the message: "VTP VLAN configuration is not allowed when the device is in client mode." Thus, I cannot make any changes to the VLAN database if the switch is in VTP client mode. If I want to make any changes, I need to go to the switch server.
I go into the settings of the SW0 terminal and enter the commands vlan 999, name IMRAN and exit. This new network appeared in the VLAN database of this switch, and if I now go to the database of the switch client SW2, then I will see that the same information appeared here, that is, replication occurred.
As I said, VTP is a great piece of software, but if used improperly, this protocol can disrupt the whole network. Therefore, you need to be very careful with the company network if the domain name and VTP password are not specified. In this case, all the hacker needs is to insert the cable of his switch into a wall outlet on the wall, connect to any office switch using the DTP protocol and then, using the created trunk, update all the information using the VTP protocol. So the hacker will be able to delete all important VLANs, taking advantage of the fact that the revision number of his device is higher than the revision number of the remaining switches. At the same time, company switches will automatically replace all VLAN database information with information replicated from a malicious switch, and your entire network will collapse.
This is due to the fact that computers are connected via a network cable to a specific switch port to which VLAN 10 or VLAN20 is connected. If these networks are removed from the LAN database of the switch, it will automatically disconnect the port belonging to a nonexistent network. Typically, a company’s network may crash precisely because the switches simply disable the ports associated with the VLAN that were removed during the next update.
In order to prevent such a problem from occurring, you need to set the VTP domain name and password or use the Cisco Port Security function, which allows you to manage the MAC addresses of switch ports by introducing various restrictions on their use. For example, if someone else tries to change the MAC address, the port will immediately shut down. Very soon we will get to know this feature of Cisco switches very closely, and now you just need to know that Port Security allows you to make sure that VTP is protected from an attacker.
Summarize what the VTP setting is. This choice of protocol version is 1 or 2, the purpose of the VTP mode is server, client or transparent. As I said, the last mode does not update the VLAN database of the device itself, but simply passes all the changes to neighboring devices. The following are the commands for assigning a domain name and password: vtp domain <domain name> and vtp password <password>.
Now let's talk about VTP Pruning settings. If you look at the network topology, you can see that all three switches have the same VLAN database, which means that VLAN10 and VLAN20 are part of all 3 switches. Technically, the SW2 switch does not need a VLAN20 network, because it does not have ports related to this network. However, regardless of this, all traffic directed from the Laptop0 computer via the VLAN20 network goes to switch SW1 and from it flows through the trunk to SW2 ports. Your main task as a network specialist is to make sure that as little data as possible is transmitted over the network. You must ensure the transfer of the necessary data, but how to limit the transfer of information that this device does not need?
You need to make sure that traffic destined for VLAN20 devices will not go to the SW2 ports through the trunk when it is not needed. That is, Laptop0 traffic should reach SW1 and further to computers on the VLAN20 network, but should not go beyond the right trunk port of SW1. This can be achieved using VTP Pruning.
To do this, we need to go into the settings of the VTP server SW0, because, as I already said, VTP settings can be made only through the server, go to the global configuration settings and type the vtp pruning command. Since Packet Tracer is just a simulator, there is no such command in its command line prompts. However, when I type vtp pruning and press "Enter", the system will report that vtp pruning is not available.
Using the show vtp status command, we will see that the VTP Pruning mode is in the disabled state, so we need to make it available by moving it to the enable position. Having done this, we activate the VTP Pruning mode on all three switches of our network within the network domain.
Let me remind you what VTP Pruning is. When we enable this mode, the switch server SW0 tells switch SW2 that only VLAN10 is configured on its ports. After that, the switch SW2 informs the switch SW1 that it does not need any traffic other than the traffic destined for the VLAN10 network. Now, thanks to VTP Pruning, the SW1 switch has information that it does not need to send VLAN20 traffic on the SW1-SW2 trunk.
As a network administrator, this is very convenient for you. You do not need to manually enter commands, since the switch is smart enough to send exactly what a particular network device requires. If tomorrow you will place another unit of marketing staff in a neighboring building and connect its VLAN20 network to switch SW2, this switch will immediately inform switch SW1 that it now has VLAN10 and VLAN20 networks and will ask you to transfer traffic for both networks to it. This information is constantly updated on all devices, which makes communication more efficient.
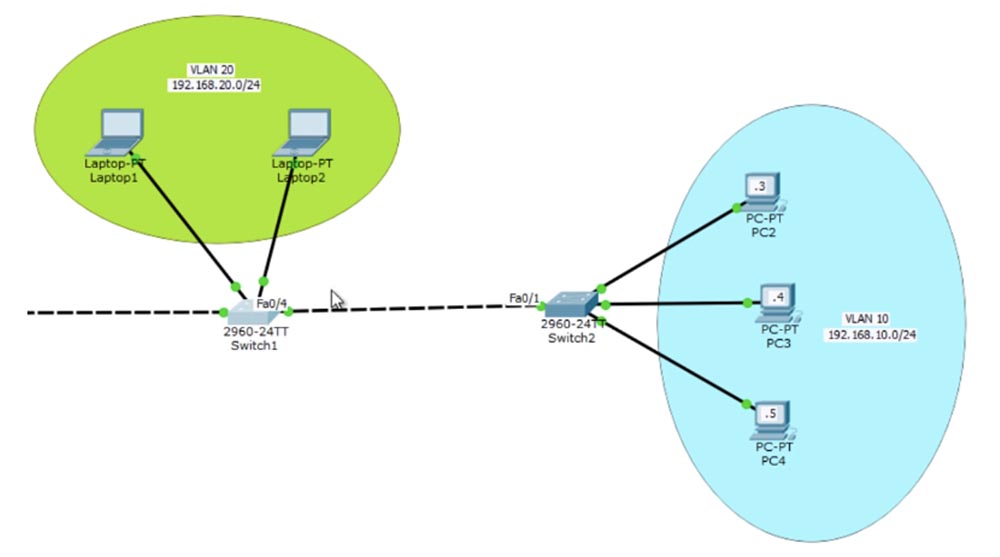
There is another way to specify the traffic transfer - use a command that allows data transfer only for the specified VLAN. I go into the settings of the switch SW1, where I am interested in the Fa0 / 4 port, and enter the commands int fa0 / 4 and switchport trunk allowed vlan. Since I already know that SW2 has only VLAN10, I can specify the SW1 switch so that its trunk port allows only traffic for this network to pass by using the allowed vlan command. Thus, I programmed the Fa0 / 4 trunk port to transmit traffic for VLAN10 only. This means that this port will not pass further traffic VLAN1, VLAN20 or any other network except the specified one.
You may ask which is better to use - VTP Pruning or the allowed vlan command. The answer is subjective, because in some cases it makes sense to use the first method, and in some the second. As a network administrator, you yourself must choose the best solution. In some cases, the decision to program the port to allow traffic for a specific VLAN can be good, but in some cases it can be bad. In the case of our network, using the allowed vlan command may be warranted if we are not going to change the network topology. But if anyone later wants to add a group of devices using VLAN20 to SW 2, it is more advisable to apply VTP Pruning mode.
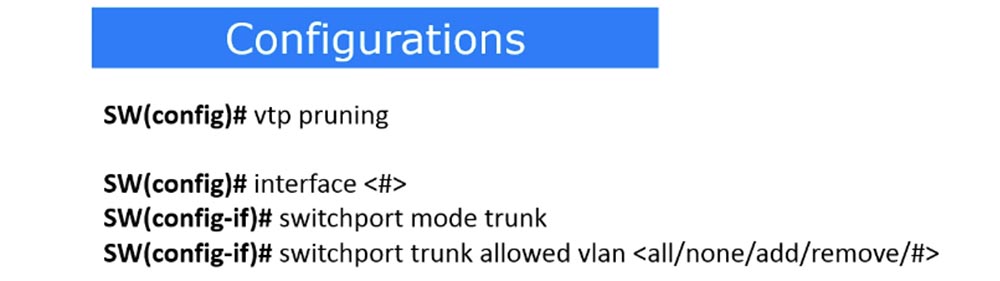
So, setting up VTP Pruning consists in using the following commands. The vtp pruning command provides automatic use of this mode. If you want to configure VTP Pruning of a trunk port to manually skip specific VLAN traffic, then use the command to select the trunk port number interface <#>, enable the trunk mode switchport mode trunk and enable the traffic of a specific network using the switchport trunk allowed vlan < all / none / add / remove / #>.
You can use 5 parameters in the last command. All means that traffic is allowed for all VLANs, none - traffic is not allowed for all VLANs. If you use the add parameter, you can add traffic pass for another network. For example, we have allowed VLAN10 traffic, and with the add command you can also allow the passage of VLAN20 network traffic. The remove command allows you to remove one of the networks, for example, if you use the remove 20 parameter, only the transmission of VLAN10 traffic remains.
Now consider native VLAN. We have already said that native VLAN is a virtual network for passing untagged traffic through a specific trunk port.

I go into the settings for a specific port, as indicated by the command line header SW (config-if) #, and use the switchport trunk native vlan <network number> command, for example, VLAN10. Now all VLAN10 network traffic will pass through the tagless tag.
Back to the logical network topology in the Packet Tracer window. If I use the switchport trunk native vlan 20 command for the Fa0 / 4 switch port, then all VLAN20 network traffic will go through the Fa0 / 4 - SW2 trunk untagged. When the SW2 switch receives this traffic, it will think: “this is untagged traffic, so I have to forward it to the native VLAN”. For this switch, native VLAN is network VLAN1. Networks 1 and 20 are not connected in any way, but since native VLAN mode is used, we have the opportunity to route VLAN20 traffic to a completely different network. However, this traffic will be unencapsulated, and the networks themselves should still match.
Let's look at an example. I will go into SW1 settings and use the switchport trunk native vlan 10 command. Now any VLAN10 traffic will come from the trunk port untagged. When it reaches trunk port SW2, the switch will understand that it must forward it to VLAN1. As a result of this solution, traffic will not be able to reach PC2, 3, and 4 computers, since they are connected to the access ports of the switch intended for VLAN10.
, native VLAN Fa0/4, VLAN10, Fa0/1, VLAN1. , - native VLAN.

Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

As you know, there are two popular trunking protocols - the Cisco ISL proprietary protocol, which is not used today, and the 802.q protocol, which is used in network devices of various manufacturers to encapsulate trunking traffic. This protocol is also used in Cisco switches. We have already said that VTP is the VLAN synchronization protocol, that is, it is designed to synchronize the VLAN database in all switches of the network.

We mentioned various VTP modes - server, client, transparent. If the device uses server mode, this allows you to make changes, add or remove VLANs. Client mode does not allow changes to switch settings; you can configure a VLAN database only through a VTP server, and it will be replicated to all VTP clients. The switch in transparent mode does not make changes to its own VLAN database, but simply passes through itself and passes the changes to the next device in client mode. This mode is similar to disabling the VTP protocol on a specific device, turning it into a carrier of information about VLAN changes.
Back to Packet Tracer and the network topology discussed in the previous lesson. We configured the VLAN10 network for the sales department and the VLAN20 network of the marketing department, combining them with three switches.

Between switches SW0 and SW1, VLAN20 is connected, and between SW0 and SW2, VLAN10 is connected due to the fact that we added VLAN10 to the VLAN database of switch SW1.
In order to consider the operation of the VTP protocol, let's use one of the switches as a VTP server, let it be SW0. If you remember, by default all switches work in the VTP server mode. Let's go to the switch command line terminal and enter the show vtp status command. You see the current version of VTP protocol - 2 and revision number of configuration 4. If you remember, every time changes are made to the VTP database, the revision number is increased by one.

The maximum number of supported VLANs is 255. This number depends on the brand of a particular Cisco switch, since different switches can support a different number of local virtual networks. The number of existing VLANs is 7, in a minute we will consider what kind of network. VTP management mode - server, domain name is not set, VTP Pruning mode is disabled, we will return to this later. VTP V2 and VTP Traps Generation modes are also disabled. To take the 200-125 CCNA exam, you don’t need to know about the last two modes, so don’t worry about them.
Let's take a look at the VLAN database, for which we use the show vlan command. As we saw in the previous video, we have 4 unsupported networks: 1002, 1003, 1004, and 1005.

It also lists the 2 VLANs 10 and 20 we created and the default network VLAN1. Now let's move on to another switch and enter the same command to view the VTP status. You see that the revision number for this switch is 3, it is in VTP server mode and all other information is similar to the first switch. When I enter the show VLAN command, I will see that we made 2 changes in the settings, one less than the switch SW0, which is why the revision number of SW1 is 3. We made 3 changes in the default settings of the first switch, so its revision number increased to 4.

Now let's look at the status of SW2. The revision number here is 1, and this is strange. We must have a second revision, because 1 change was made to the settings. Let's look at the VLAN database.

We made one change by creating a VLAN10 network, and I do not know why this information was not updated. Perhaps this was due to the fact that we do not have a real network, but a software network simulator, in which there may be errors. When you have the opportunity to work with real devices while practicing at Cisco, this will help you more than the Packet Tracer simulator. Another useful thing in the absence of real devices would be GNC3, or the Cisco network simulator. This is an emulator that uses the real operating system of the device, for example, a router. There is a difference between the simulator and the emulator - the first is a program that looks like a real router, but it is not. The emulator programmatically creates only the device itself, but uses real software for its operation. But if you don’t have the opportunity to work with real Cisco IOS software, the best option would be Packet Tracer.
So, we need to configure SW0 as a VTP server, for this I go into global configuration mode and enter the vtp version 2 command. As I said, we can install the version of the protocol that we need - 1 or 2, in this case we need a second version. Next, with the vtp mode command, we set the VTP mode of the switch - server, client, or transparent. In this case, we need server mode, and after entering the vtp mode server command, the system displays a message that the device is already in server mode. Next, we need to configure the VTP domain, for which we use the vtp domain nwking.org command. Why is this needed? If there is another device with a higher revision number on the network, all other devices with a lower revision begin to replicate the VLAN database from this device. However, this only happens when the devices have the same domain name. For example, if you work in nwking.org, you specify this domain, if in Cisco, then the domain is Cisco.com, and so on. The domain name of your company’s devices allows you to distinguish them from devices of another company or any other external network devices. If you assign a company domain name to a device, then you make it part of the company's network.
The next thing to do is set a VTP password. It is needed so that a hacker, having a device with a large revision number, could not copy his VTP settings to your switch. I enter the cisco password using the vtp password cisco command. After that, replication of VTP data between switches will be possible only if the passwords match. If the wrong password is used, the VLAN database will not be updated.
Let's try to create some more VLANs. To do this, I use the config t command, with the vlan 200 command I create a network with the number 200, give it the name TEST and save the changes with the exit command. Then I create another vlan 500 network and call it TEST1. If you now enter the show vlan command, then in the virtual network table of the switch you can see these two new networks, to which no ports are assigned.

Let's move on to SW1 and see its VTP status. We see that nothing has changed here, except for the domain name, the number of VLANs has remained equal to 7. We do not see the appearance of the networks we created, because the VTP password does not match. Let's set the VTP password on this switch by entering the conf t, vtp pass and vtp password cisco commands in sequence. The system issued a message that the device VLAN database now uses the Cisco password. Let's take a look at the VTP status again to check if the information has been replicated. As you can see, the number of existing VLANs automatically increased to 9.
If you look at the VLAN database of this switch, you can see that the VLAN200 and VLAN500 networks we created automatically appeared in it.
The same thing needs to be done with the last switch SW2. Let's enter the show vlan command - you see that there were no changes in it. Similarly, there are no changes in VTP status. In order for this switch to update the information, you also need to configure a password, that is, enter the same commands as for SW1. After that, the number of VLANs in the SW2 status will increase to 9.
That's what the VTP protocol is for. This is a great thing, which provides automatic updating of information in all client network devices after making changes to the server device. You do not need to manually make changes to the VLAN database of all switches - replication occurs automatically. If you have 200 network devices, your changes will be saved simultaneously on all two hundred devices. Just in case, we need to make sure that SW2 is also a VTP client, so go to the settings with the config t command and enter the vtp mode client command.
Thus, in our network, only the first switch is in VTP Server mode, the other two are in VTP Client mode. If now I go into the settings of SW2 and enter the vlan 1000 command, I get the message: "VTP VLAN configuration is not allowed when the device is in client mode." Thus, I cannot make any changes to the VLAN database if the switch is in VTP client mode. If I want to make any changes, I need to go to the switch server.
I go into the settings of the SW0 terminal and enter the commands vlan 999, name IMRAN and exit. This new network appeared in the VLAN database of this switch, and if I now go to the database of the switch client SW2, then I will see that the same information appeared here, that is, replication occurred.
As I said, VTP is a great piece of software, but if used improperly, this protocol can disrupt the whole network. Therefore, you need to be very careful with the company network if the domain name and VTP password are not specified. In this case, all the hacker needs is to insert the cable of his switch into a wall outlet on the wall, connect to any office switch using the DTP protocol and then, using the created trunk, update all the information using the VTP protocol. So the hacker will be able to delete all important VLANs, taking advantage of the fact that the revision number of his device is higher than the revision number of the remaining switches. At the same time, company switches will automatically replace all VLAN database information with information replicated from a malicious switch, and your entire network will collapse.
This is due to the fact that computers are connected via a network cable to a specific switch port to which VLAN 10 or VLAN20 is connected. If these networks are removed from the LAN database of the switch, it will automatically disconnect the port belonging to a nonexistent network. Typically, a company’s network may crash precisely because the switches simply disable the ports associated with the VLAN that were removed during the next update.
In order to prevent such a problem from occurring, you need to set the VTP domain name and password or use the Cisco Port Security function, which allows you to manage the MAC addresses of switch ports by introducing various restrictions on their use. For example, if someone else tries to change the MAC address, the port will immediately shut down. Very soon we will get to know this feature of Cisco switches very closely, and now you just need to know that Port Security allows you to make sure that VTP is protected from an attacker.
Summarize what the VTP setting is. This choice of protocol version is 1 or 2, the purpose of the VTP mode is server, client or transparent. As I said, the last mode does not update the VLAN database of the device itself, but simply passes all the changes to neighboring devices. The following are the commands for assigning a domain name and password: vtp domain <domain name> and vtp password <password>.

Now let's talk about VTP Pruning settings. If you look at the network topology, you can see that all three switches have the same VLAN database, which means that VLAN10 and VLAN20 are part of all 3 switches. Technically, the SW2 switch does not need a VLAN20 network, because it does not have ports related to this network. However, regardless of this, all traffic directed from the Laptop0 computer via the VLAN20 network goes to switch SW1 and from it flows through the trunk to SW2 ports. Your main task as a network specialist is to make sure that as little data as possible is transmitted over the network. You must ensure the transfer of the necessary data, but how to limit the transfer of information that this device does not need?
You need to make sure that traffic destined for VLAN20 devices will not go to the SW2 ports through the trunk when it is not needed. That is, Laptop0 traffic should reach SW1 and further to computers on the VLAN20 network, but should not go beyond the right trunk port of SW1. This can be achieved using VTP Pruning.
To do this, we need to go into the settings of the VTP server SW0, because, as I already said, VTP settings can be made only through the server, go to the global configuration settings and type the vtp pruning command. Since Packet Tracer is just a simulator, there is no such command in its command line prompts. However, when I type vtp pruning and press "Enter", the system will report that vtp pruning is not available.
Using the show vtp status command, we will see that the VTP Pruning mode is in the disabled state, so we need to make it available by moving it to the enable position. Having done this, we activate the VTP Pruning mode on all three switches of our network within the network domain.
Let me remind you what VTP Pruning is. When we enable this mode, the switch server SW0 tells switch SW2 that only VLAN10 is configured on its ports. After that, the switch SW2 informs the switch SW1 that it does not need any traffic other than the traffic destined for the VLAN10 network. Now, thanks to VTP Pruning, the SW1 switch has information that it does not need to send VLAN20 traffic on the SW1-SW2 trunk.
As a network administrator, this is very convenient for you. You do not need to manually enter commands, since the switch is smart enough to send exactly what a particular network device requires. If tomorrow you will place another unit of marketing staff in a neighboring building and connect its VLAN20 network to switch SW2, this switch will immediately inform switch SW1 that it now has VLAN10 and VLAN20 networks and will ask you to transfer traffic for both networks to it. This information is constantly updated on all devices, which makes communication more efficient.

There is another way to specify the traffic transfer - use a command that allows data transfer only for the specified VLAN. I go into the settings of the switch SW1, where I am interested in the Fa0 / 4 port, and enter the commands int fa0 / 4 and switchport trunk allowed vlan. Since I already know that SW2 has only VLAN10, I can specify the SW1 switch so that its trunk port allows only traffic for this network to pass by using the allowed vlan command. Thus, I programmed the Fa0 / 4 trunk port to transmit traffic for VLAN10 only. This means that this port will not pass further traffic VLAN1, VLAN20 or any other network except the specified one.
You may ask which is better to use - VTP Pruning or the allowed vlan command. The answer is subjective, because in some cases it makes sense to use the first method, and in some the second. As a network administrator, you yourself must choose the best solution. In some cases, the decision to program the port to allow traffic for a specific VLAN can be good, but in some cases it can be bad. In the case of our network, using the allowed vlan command may be warranted if we are not going to change the network topology. But if anyone later wants to add a group of devices using VLAN20 to SW 2, it is more advisable to apply VTP Pruning mode.

So, setting up VTP Pruning consists in using the following commands. The vtp pruning command provides automatic use of this mode. If you want to configure VTP Pruning of a trunk port to manually skip specific VLAN traffic, then use the command to select the trunk port number interface <#>, enable the trunk mode switchport mode trunk and enable the traffic of a specific network using the switchport trunk allowed vlan < all / none / add / remove / #>.
You can use 5 parameters in the last command. All means that traffic is allowed for all VLANs, none - traffic is not allowed for all VLANs. If you use the add parameter, you can add traffic pass for another network. For example, we have allowed VLAN10 traffic, and with the add command you can also allow the passage of VLAN20 network traffic. The remove command allows you to remove one of the networks, for example, if you use the remove 20 parameter, only the transmission of VLAN10 traffic remains.
Now consider native VLAN. We have already said that native VLAN is a virtual network for passing untagged traffic through a specific trunk port.

I go into the settings for a specific port, as indicated by the command line header SW (config-if) #, and use the switchport trunk native vlan <network number> command, for example, VLAN10. Now all VLAN10 network traffic will pass through the tagless tag.
Back to the logical network topology in the Packet Tracer window. If I use the switchport trunk native vlan 20 command for the Fa0 / 4 switch port, then all VLAN20 network traffic will go through the Fa0 / 4 - SW2 trunk untagged. When the SW2 switch receives this traffic, it will think: “this is untagged traffic, so I have to forward it to the native VLAN”. For this switch, native VLAN is network VLAN1. Networks 1 and 20 are not connected in any way, but since native VLAN mode is used, we have the opportunity to route VLAN20 traffic to a completely different network. However, this traffic will be unencapsulated, and the networks themselves should still match.
Let's look at an example. I will go into SW1 settings and use the switchport trunk native vlan 10 command. Now any VLAN10 traffic will come from the trunk port untagged. When it reaches trunk port SW2, the switch will understand that it must forward it to VLAN1. As a result of this solution, traffic will not be able to reach PC2, 3, and 4 computers, since they are connected to the access ports of the switch intended for VLAN10.
, native VLAN Fa0/4, VLAN10, Fa0/1, VLAN1. , - native VLAN.

Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles