Lock code in iOS: how Apple switched from defense in defense to guarding a single frontier
In a previous article, I talked about the mode of restricting access to accessories in devices running iOS. In the article, I focused on the features of iOS, which makes the security of user data dependent on the only "insurmountable" protective line: the screen lock code. Almost all protective measures are somehow tied to a lock code. Apple periodically (on a complex schedule) disables biometrics in the iPhone, forcing the user to enter a passcode to unlock the screen. Turned on or rebooted the phone - you need a lock code. Used SOS mode - lock code. The phone has not been used for several hours - again the lock code. Connect to the computer - and enter the lock code again. Want to set a password for backup? Starting with iOS 13 and here you need a lock code.
It would seem that the user just needs to set a long and complex lock code to completely secure the device. However, this behavior is no different from the hypothetical security system of the building, where only the entrance is guarded - while the doors to the offices are always wide open, there are no passwords on the computers in the offices, and you can get unlimited access to the internal network from any device simply by connecting to the network Wi-Fi (of course, also completely open).
Fantasy? Indeed, the described sounds strange, but it is in this state that the iOS security system is now. In fact, all protection is entirely based on a single line of defense, which is the screen lock code - with only one small condition: the user account is protected by two-factor authentication.
If you know the screen lock code, you can extract almost all data from the iPhone, including passwords from accounts. How to do it? Create a backup by protecting it with a password. And what is the lock code for? Here are the steps to create such a backup:
The lock code can be used for full, unlimited access to passwords from the Keychain on the iPhone itself. Moreover, knowing the lock code, you can easily view all user-saved passwords both in the Keychain and in a third-party password manager that is connected to the iOS autofill system (for example, Roboform).
Knowing the lock code, you can easily untie the stolen phone from iCloud. To do this, just change the iCloud password directly in the phone settings; Enter the original password for the owner of the iPhone for this is not necessary. With minimal dexterity, the iCloud password changes in a few seconds, after which Find my iPhone turns off instantly.
Using the lock code, you can decrypt the user password database in iCloud, its SMS and iMessage messages, as well as Health data. There is a subtle point here: in order to access this data, the user account must be protected by two-factor authentication.
Well, with what exactly is accessible to the attacker who learned the lock code, we figured out. But what does two-factor authentication have to do with it?
The fact is that only with the inclusion of two-factor authentication, some advanced features of iCloud become available. At the same time, the entire smartphone turns into the very additional factor that is necessary for ... but for what.
"Horrible! No, I definitely won’t include two-factor authentication, it’s just dangerous! ”Logical reasoning? Honestly, not really: enabling two-factor authentication with the iPhone, knowing its lock code, will be very, very simple, which brings us back to the first point. But turning off 2FA today is very difficult, almost impossible.
Using a blocking code, an attacker (or law enforcement agencies) can do a number of undesirable things for the user. The lock code is almost the only and last remaining line of defense. If it crashes, an attacker can do almost anything with the iPhone itself or with data in the cloud - a complete analogue of the building, the entire security system of which is limited to a digital lock at the entrance. You can simply go further along the chain: passwords from accounts from the Keychain will help you log in to social networks; if you find a password for your Google account - you can access the data that has accumulated user devices with Android.
Apple is aware of all this. For a long time now, when setting up your iPhone or iPad, you will be prompted to enter a 6-digit lock code (previously there were only 4). Yes, you can enable a 4-digit lock code, but the security of this step is doubtful: 4-digit lock codes using special tools can be cracked within half an hour. But it can take up to 19 years to search passwords consisting of 6 digits - this is quite safe. However, the solutions we know about use peculiar workarounds: in some cases, the first several hundred thousand passwords (AFU, certain generations of hardware) are sorted out much faster, and frequency dictionaries are used instead of exhaustive search.
What about hardware overkill protection? All 64-bit iOS devices have a Secure Enclave security subsystem, the hardware often of which is Secure Element, which limits the speed and number of possible attempts. To date, Secure Enclave protection has been more or less circumvented for all generations of iPhone and iPad, except for the latter, based on the SoC A12. Among the "safe" models - iPhone Xs, Xs Max and Xr. In these models, the search speed will be limited to one password in 10 minutes; As far as I know, manufacturers of hacking tools have not managed to circumvent this limitation. But for older models, especially in AFU mode (After First Unlock, i.e. the phone was taken from the user in the on state, and the user unlocked it at least once after turning on), the search speed is several times faster.
True - but only for devices registered in an account with active two-factor authentication. Surprisingly, this is so: perhaps the most powerful mechanism, an advanced deterrent, after the appearance of which iPhone thefts were reduced several times, you can turn it off, knowing only the lock code and nothing more.
How it's done? I need the iPhone itself and its lock code. Launch the Find iPhone system application. In the application - a password entry field with the inscription “Required”. Ignore it by clicking on “Forgot Apple ID or password?” And we’ll see a phone lock code request:
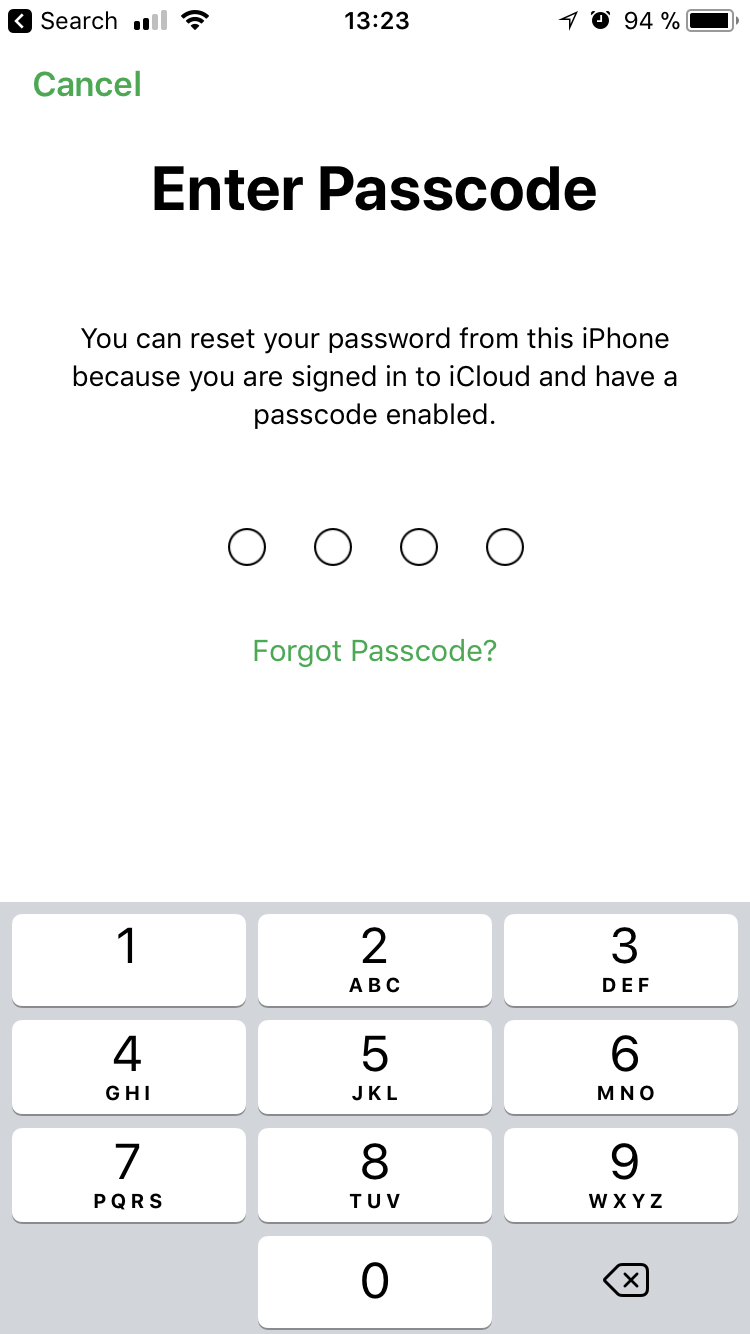
We enter the lock code, and in the next step we set a new password for iCloud:
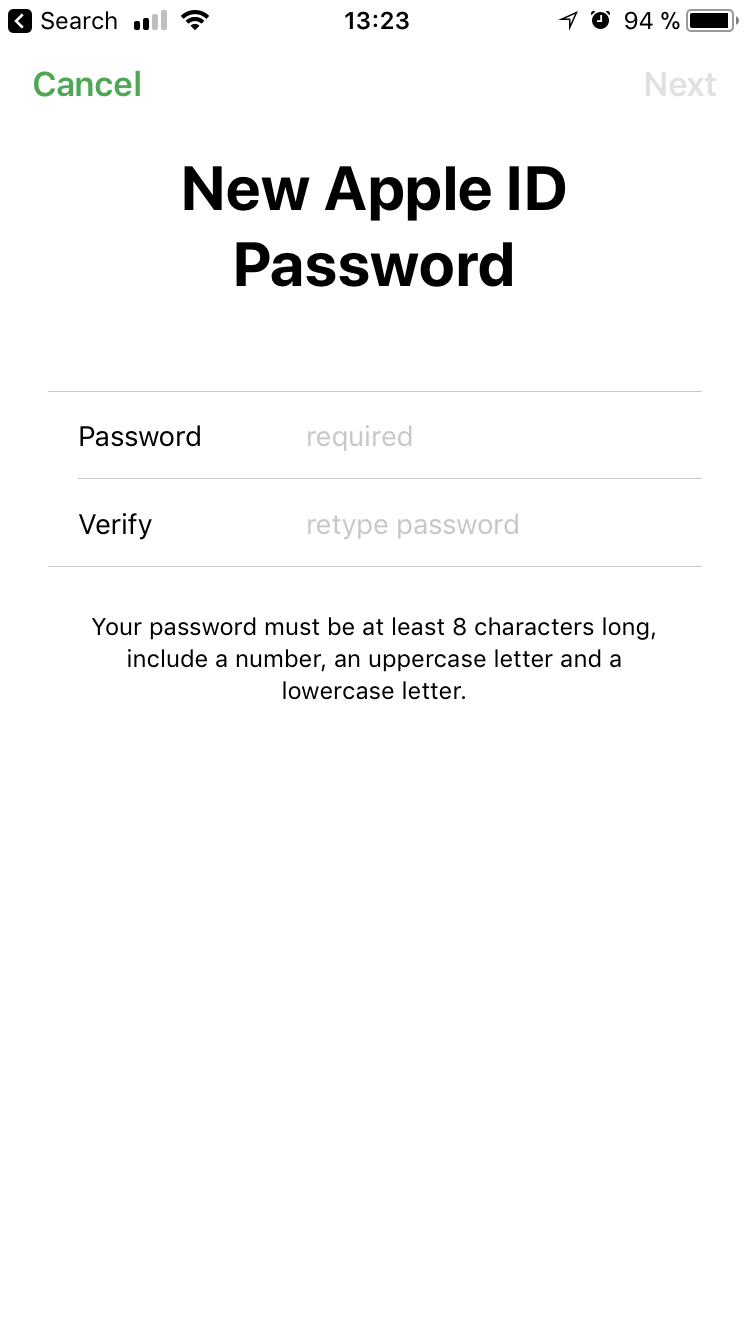
The problem is solved: we now know the password from Apple ID / iCloud; iCloud lock can be disabled from the system settings.
An alternative method does not require the use of the Find My Phone application. We go into the Apple ID in the device settings, and then open the Password & Security item:
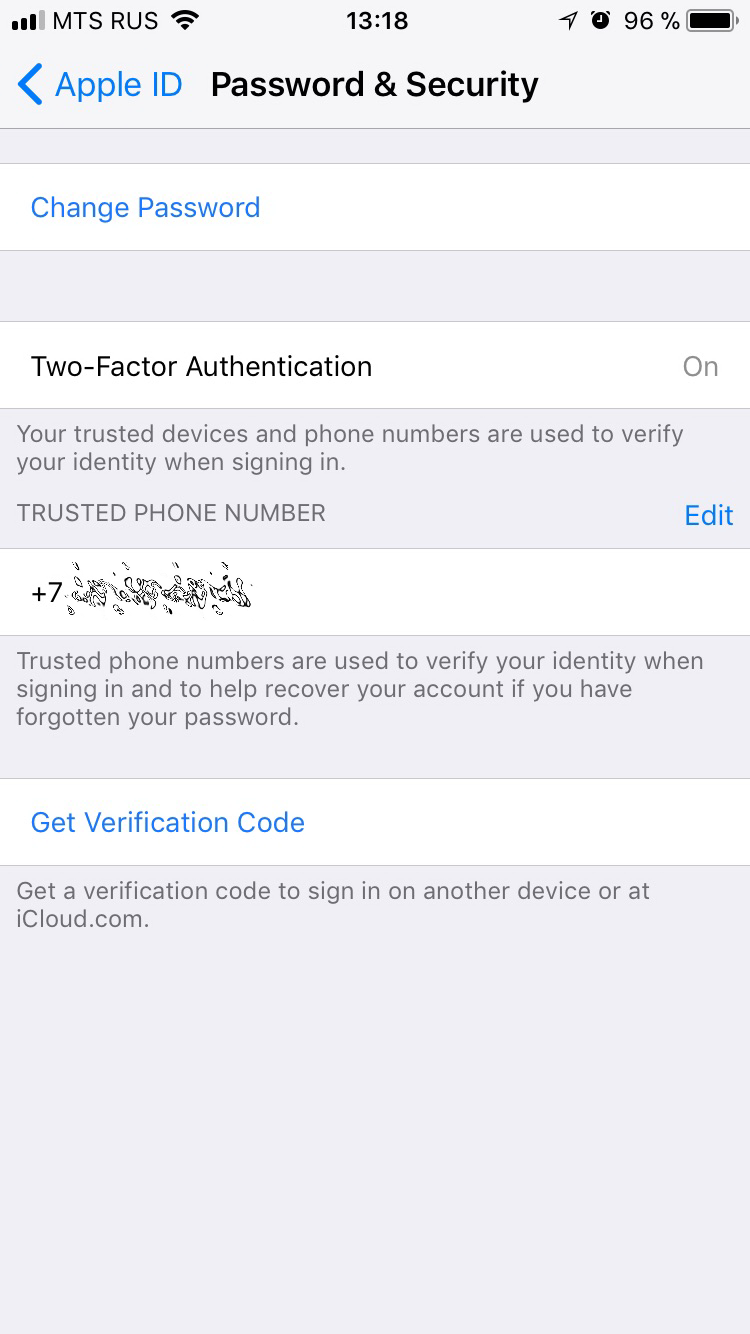
Next is Change Password. There will be a request for the device lock code:
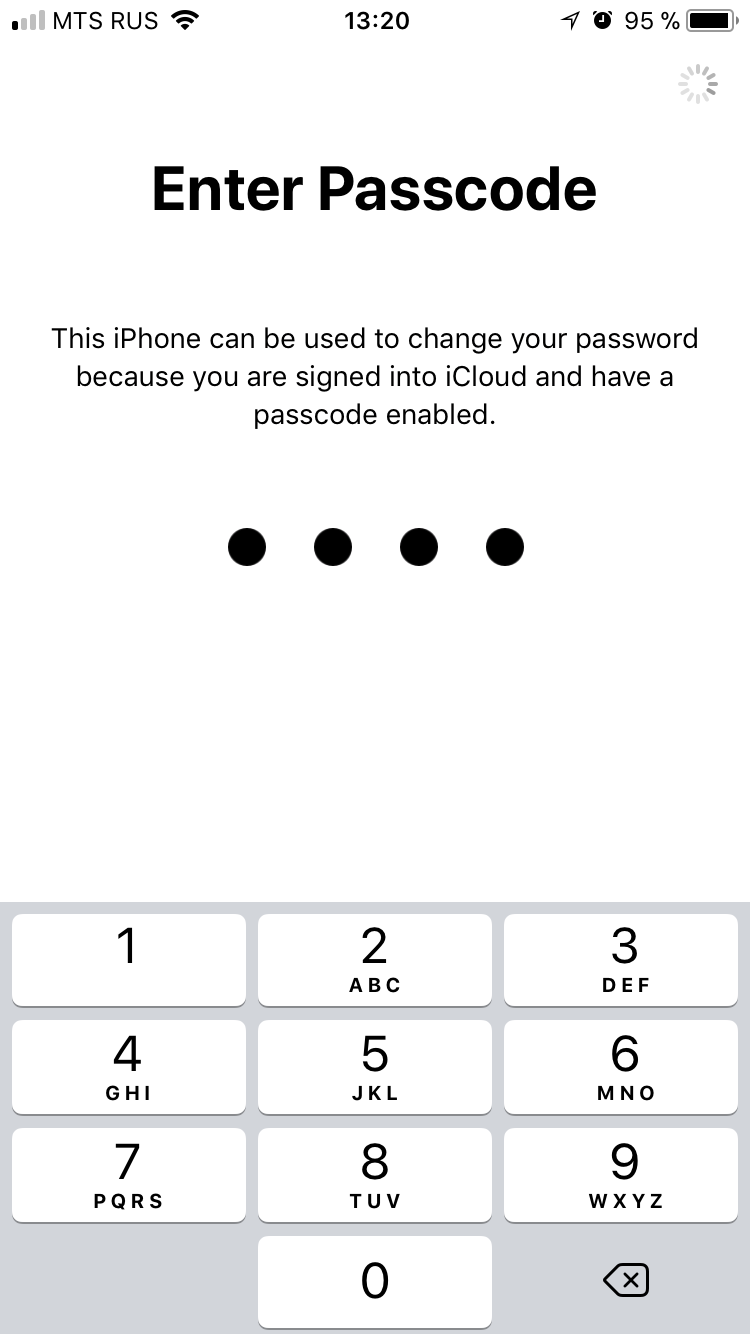
After that, change the password for iCloud / Apple ID:
Even after this, the original owner can still regain control of the account by sending a restore request and specifying a trusted phone number.

The Trusted Phone Number settings indicate the phone number to which SMS will be sent for two-factor authentication. It is this number that the owner will be able to use to restore access to the account if the attacker changes his Apple ID password.
You cannot delete a single number, but this will not stop the attacker. The first step will be to add a new “trusted phone number”, the second is to delete the old one that belonged to the former owner of the account. From that moment on - really everything: quickly recovering access to the account from the original owner of the device will fail. In the best case, this can be done after a long verification procedure, during which the traces of the stolen device will be lost.
From my point of view, the iOS security system now leaves much to be desired. The only line of defense is completely inadequate protection. (Here I will mention the password protection of “Screen Time”; it is not perfect, but better than nothing. Somehow I will talk more about this protection.)
How can security be enhanced? I would suggest the following measures.
Is it possible to somehow strengthen the security of iOS? Corporate users can use the Apple Configurator system, in which you can set restrictions on the manipulation of the account. It makes sense to end users to set the “Screen Time” password. If you don’t get carried away with self-restrictions, then the experience of using the device will not be affected, but you will not be able to reset the password for the backup: in addition to the screen lock code, the system will also ask you to enter the “Screen Time” password. In addition, you can configure the restrictions in such a way that without the “Screen Time” password you cannot change the password for the account or delete it from the iPhone.
It would seem that the user just needs to set a long and complex lock code to completely secure the device. However, this behavior is no different from the hypothetical security system of the building, where only the entrance is guarded - while the doors to the offices are always wide open, there are no passwords on the computers in the offices, and you can get unlimited access to the internal network from any device simply by connecting to the network Wi-Fi (of course, also completely open).
Fantasy? Indeed, the described sounds strange, but it is in this state that the iOS security system is now. In fact, all protection is entirely based on a single line of defense, which is the screen lock code - with only one small condition: the user account is protected by two-factor authentication.
What can I do if I know the iPhone lock code
If you know the screen lock code, you can extract almost all data from the iPhone, including passwords from accounts. How to do it? Create a backup by protecting it with a password. And what is the lock code for? Here are the steps to create such a backup:
- We connect iPhone to the computer. Starting with iOS 11, to connect to a computer on the iPhone, you need not only to click “agree” to the connection request, but also enter a lock code .
- Launch iTunes or iOS Forensic Toolkit and see if the password for the backup is set. Not installed? Great, install your own and create a backup! (Why set a password - I will write it separately; in a nutshell, only data such as the Keychain and some others get into the backup copy with the password). Only one thing can interfere: starting with iOS 13, you need to enter a lock code to set a password for the backup. Password is set, but unknown to you? It also does not matter: starting with iOS 11, the password for the backup can be reset ... by entering the screen lock code on the iPhone!
The lock code can be used for full, unlimited access to passwords from the Keychain on the iPhone itself. Moreover, knowing the lock code, you can easily view all user-saved passwords both in the Keychain and in a third-party password manager that is connected to the iOS autofill system (for example, Roboform).
Knowing the lock code, you can easily untie the stolen phone from iCloud. To do this, just change the iCloud password directly in the phone settings; Enter the original password for the owner of the iPhone for this is not necessary. With minimal dexterity, the iCloud password changes in a few seconds, after which Find my iPhone turns off instantly.
Using the lock code, you can decrypt the user password database in iCloud, its SMS and iMessage messages, as well as Health data. There is a subtle point here: in order to access this data, the user account must be protected by two-factor authentication.
What does two-factor authentication have to do with it?
Well, with what exactly is accessible to the attacker who learned the lock code, we figured out. But what does two-factor authentication have to do with it?
The fact is that only with the inclusion of two-factor authentication, some advanced features of iCloud become available. At the same time, the entire smartphone turns into the very additional factor that is necessary for ... but for what.
- To reset the password in iCloud (matches the password for the Apple ID account). They reset the password for iCloud, and then on the thumb: disconnected Find my iPhone, untying the iPhone from iCloud lock; dragged photos from the cloud (you can google Celebgate here), extracted backups, a list of calls, and so on.
- To access passwords in the iCloud cloud. Here I just note that the passwords of the iCloud Keychain cloud keychain are encrypted with a key that depends on the lock code. By the way, the lock code is suitable for any device participating in synchronization. Without two-factor authentication, passwords simply won’t be synchronized to the cloud, so this item is right here.
- Health data. This includes data on user activity - the number of steps, heart rate (if a watch or tracker is used), and so on. Very useful information if you can manage it competently. Again, the Health data falls into the cloud if and only if two-factor authentication is enabled, and to decrypt them you will need to enter a lock code.
- "Screen time." There are limitations and statistics on the use of all devices of the user and his children. Again, cloud sync does not work without 2FA.
- SMS and iMessage. You can enable their synchronization in iCloud only with two-factor authentication, traditionally you need a lock code for decryption.
"Horrible! No, I definitely won’t include two-factor authentication, it’s just dangerous! ”Logical reasoning? Honestly, not really: enabling two-factor authentication with the iPhone, knowing its lock code, will be very, very simple, which brings us back to the first point. But turning off 2FA today is very difficult, almost impossible.
Protecting the lock code from brute force attacks
Using a blocking code, an attacker (or law enforcement agencies) can do a number of undesirable things for the user. The lock code is almost the only and last remaining line of defense. If it crashes, an attacker can do almost anything with the iPhone itself or with data in the cloud - a complete analogue of the building, the entire security system of which is limited to a digital lock at the entrance. You can simply go further along the chain: passwords from accounts from the Keychain will help you log in to social networks; if you find a password for your Google account - you can access the data that has accumulated user devices with Android.
Apple is aware of all this. For a long time now, when setting up your iPhone or iPad, you will be prompted to enter a 6-digit lock code (previously there were only 4). Yes, you can enable a 4-digit lock code, but the security of this step is doubtful: 4-digit lock codes using special tools can be cracked within half an hour. But it can take up to 19 years to search passwords consisting of 6 digits - this is quite safe. However, the solutions we know about use peculiar workarounds: in some cases, the first several hundred thousand passwords (AFU, certain generations of hardware) are sorted out much faster, and frequency dictionaries are used instead of exhaustive search.
What about hardware overkill protection? All 64-bit iOS devices have a Secure Enclave security subsystem, the hardware often of which is Secure Element, which limits the speed and number of possible attempts. To date, Secure Enclave protection has been more or less circumvented for all generations of iPhone and iPad, except for the latter, based on the SoC A12. Among the "safe" models - iPhone Xs, Xs Max and Xr. In these models, the search speed will be limited to one password in 10 minutes; As far as I know, manufacturers of hacking tools have not managed to circumvent this limitation. But for older models, especially in AFU mode (After First Unlock, i.e. the phone was taken from the user in the on state, and the user unlocked it at least once after turning on), the search speed is several times faster.
And what is the truth, you can turn off iCloud Lock without knowing the password for iCloud?
True - but only for devices registered in an account with active two-factor authentication. Surprisingly, this is so: perhaps the most powerful mechanism, an advanced deterrent, after the appearance of which iPhone thefts were reduced several times, you can turn it off, knowing only the lock code and nothing more.
How it's done? I need the iPhone itself and its lock code. Launch the Find iPhone system application. In the application - a password entry field with the inscription “Required”. Ignore it by clicking on “Forgot Apple ID or password?” And we’ll see a phone lock code request:

We enter the lock code, and in the next step we set a new password for iCloud:

The problem is solved: we now know the password from Apple ID / iCloud; iCloud lock can be disabled from the system settings.
An alternative method does not require the use of the Find My Phone application. We go into the Apple ID in the device settings, and then open the Password & Security item:

Next is Change Password. There will be a request for the device lock code:

After that, change the password for iCloud / Apple ID:

Even after this, the original owner can still regain control of the account by sending a restore request and specifying a trusted phone number.

The Trusted Phone Number settings indicate the phone number to which SMS will be sent for two-factor authentication. It is this number that the owner will be able to use to restore access to the account if the attacker changes his Apple ID password.
You cannot delete a single number, but this will not stop the attacker. The first step will be to add a new “trusted phone number”, the second is to delete the old one that belonged to the former owner of the account. From that moment on - really everything: quickly recovering access to the account from the original owner of the device will fail. In the best case, this can be done after a long verification procedure, during which the traces of the stolen device will be lost.
How would it be right?
From my point of view, the iOS security system now leaves much to be desired. The only line of defense is completely inadequate protection. (Here I will mention the password protection of “Screen Time”; it is not perfect, but better than nothing. Somehow I will talk more about this protection.)
How can security be enhanced? I would suggest the following measures.
- "Return, as it was in iOS 10": before version iOS 11, no one could ever reset the password to the local backup. Forgot password? You can backup in iCloud and reset the phone to factory settings; The password for the backup was reset. But it was impossible to simply remove the iPhone, find out the lock code and remove the backup: the password for the backup could be set long and very difficult (you still have to enter it once during installation and the second one when restoring the device), and breaking it is extremely slow , of the order of hundreds of attempts per second using hardware acceleration on the GPU.
- Do not allow adding or removing trusted phone numbers without confirming your iCloud password. Now to add a new trusted number to which you can get the 2FA code, just enter the iPhone lock code.
- Prevent password reset for Apple ID / iCloud using a lock code. Try to somehow change or reset the password for your Google account - make sure that the access recovery system can be made both convenient and safe.
- And even more so, do not allow the disconnection of Find my iPhone after resetting the password. Here, again, I’ll send it to Google: it’s enough to change (not even reset, just change!) The Google Account password and turn off FRP (Factory Reset Protection) protection for three days: the period is sufficient to have time to do something About the stolen device. This moment acquires special significance in the light of the fact that robbers now not only take the smartphone from the victim, but force them to inform them of the lock code, instantly changing the password from the cloud and untying the device from iCloud.
Is it possible to somehow strengthen the security of iOS? Corporate users can use the Apple Configurator system, in which you can set restrictions on the manipulation of the account. It makes sense to end users to set the “Screen Time” password. If you don’t get carried away with self-restrictions, then the experience of using the device will not be affected, but you will not be able to reset the password for the backup: in addition to the screen lock code, the system will also ask you to enter the “Screen Time” password. In addition, you can configure the restrictions in such a way that without the “Screen Time” password you cannot change the password for the account or delete it from the iPhone.
All Articles