The key AES-256 was removed from a distance of 1 meter on the electromagnetic radiation of the computer
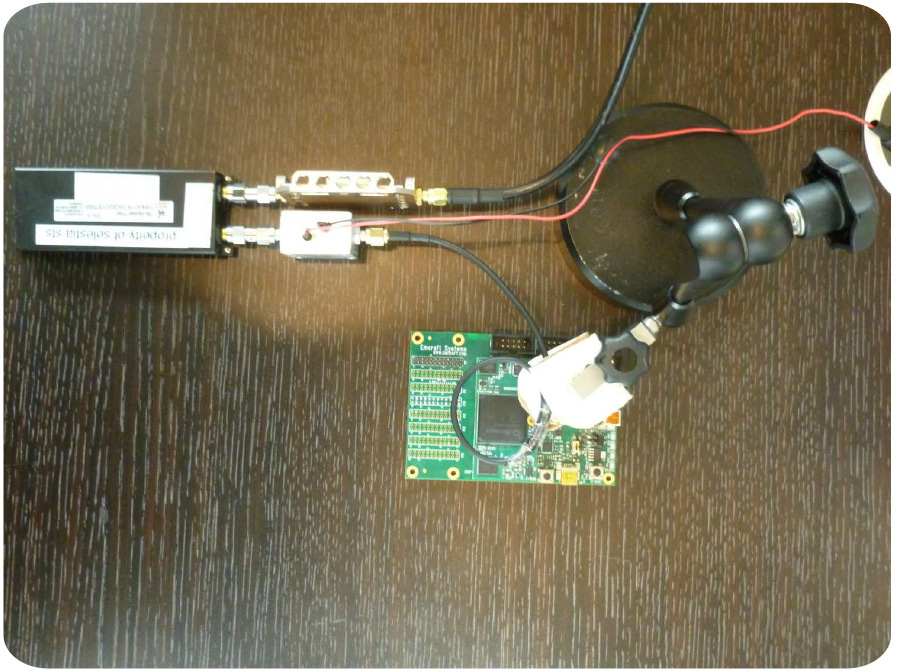
Equipment for the removal of the electromagnetic signal
Any computer during operation creates an electromagnetic field, in which the spectral components vary slightly depending on the operations that the device performs. These laws of physics are the basis for conducting an attack on electromagnetic radiation - a representative of the class of attacks on third-party channels. Information about the physical processes in the device may be enough to restore the value of the bits in memory.
Scanning of electromagnetic radiation of a PC for reading passwords was carried out before, there is nothing new here. But before that, the mass of expensive and bulky equipment was used for this. Now the threat has reached a new level. In principle, such an attack can be carried out even imperceptibly for the victim, simply by sitting next to a PC with a small “bug” in your pocket (in the photo above).
Fox-IT researchers demonstrated a TEMPEST attack from a distance of 1 meter, using a minimum set of equipment worth only 200 euros. To collect the necessary amount of information, it is necessary to record electromagnetic radiation for 5 minutes (1 meter distance) or 50 seconds (30 cm distance).
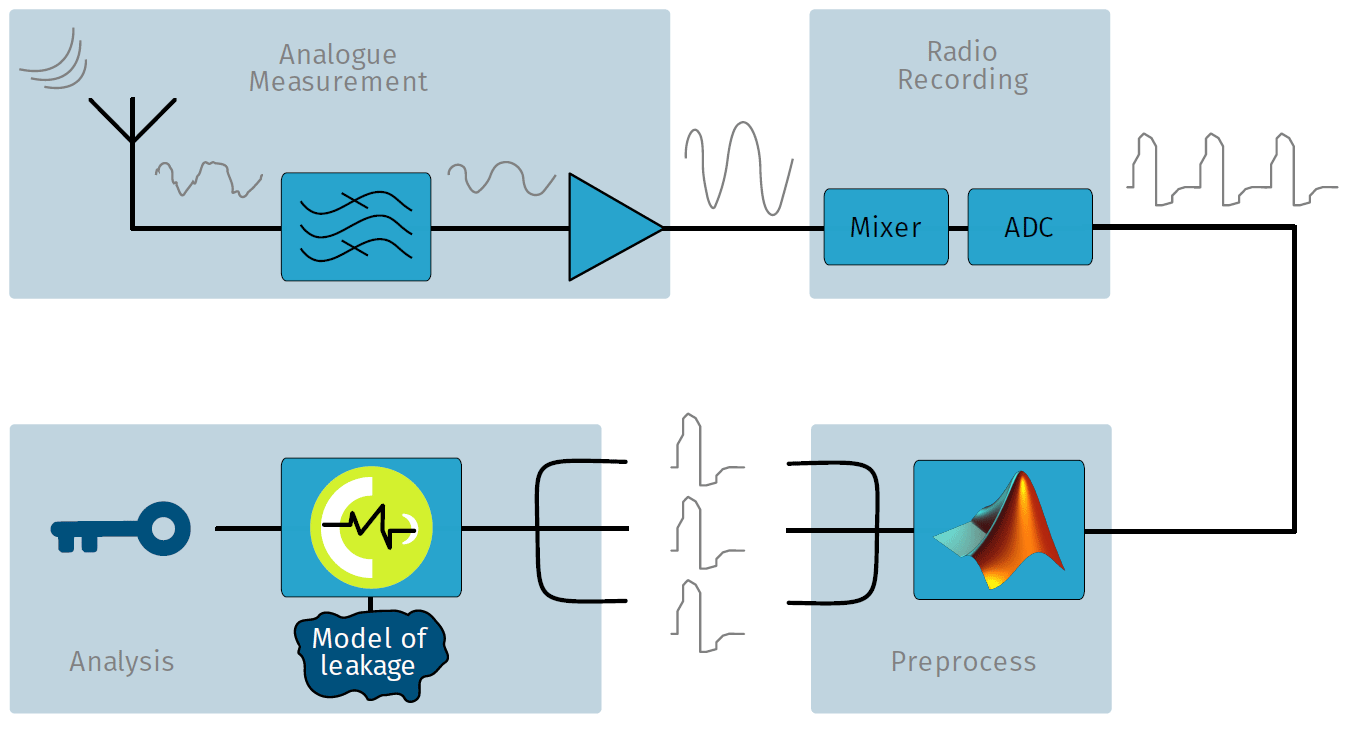
The authors described the experimental conditions in more detail in a scientific paper (pdf) . The attack algorithm is shown in the diagram below. It includes four phases:
- Analog measurements.
- Record radio signal.
- Preliminary processing.
- Analysis.
Analog measurements require an antenna with associated electronics, which will measure the characteristics of the electromagnetic field, filter the necessary frequencies and amplify the signal. As it turned out, a small and simple loop antenna, which is very easy to make from a piece of unnecessary cable and scotch, catches the signal surprisingly effectively.

Loop antenna
Then the signal is filtered and amplified. Researchers filtered a 10 MHz wide area near the clock frequency (142 MHz) and amplified it with a cheap Mini Circuits amplifier. The cost of all the "iron" - less than 200 euros.
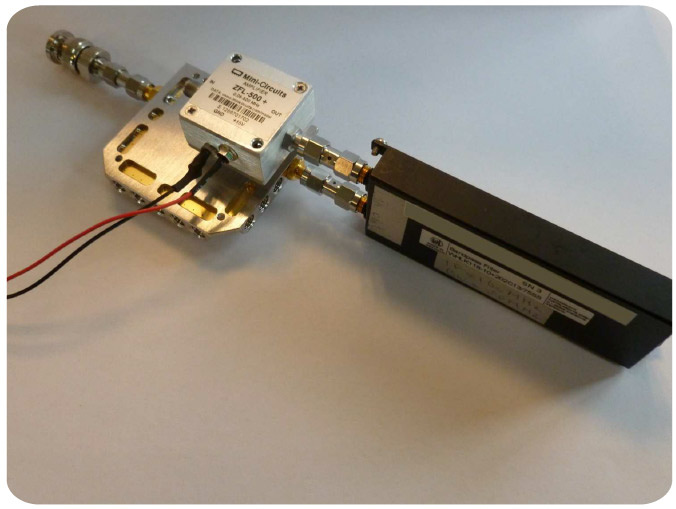
Filter amplifier
Before recording the radio signal is converted to digital form. You can record a signal on different equipment: from expensive professional equipment to a budget software radio in the form of a flash drive for 20 euros. Experiments have shown that even such a cheap flash drive is enough to record a signal for a successful attack. In other words, not only special services or corporations with large exploration budgets can carry out such an attack, but absolutely any people. A lot of money is not needed here.
During preprocessing, the program searches for signal areas where encryption begins in the computer's memory using the AES-256 key. The signal is divided into corresponding blocks. There is also a data conversion for further analysis.
The illustration below shows the signal that the SR-7100 recorded in the 10 MHz band. This signal corresponds to a single AES-256 encryption unit running on SoC SmartFusion2. The experiment used OpenSSL AES implementation on the ARM Cortex-M3 core. As you can see, visible, clear patterns are noticeable at each stage of processing. You can see the input / output signal from the processor, the phase of calculations for the key schedule and 14 rounds of encryption.
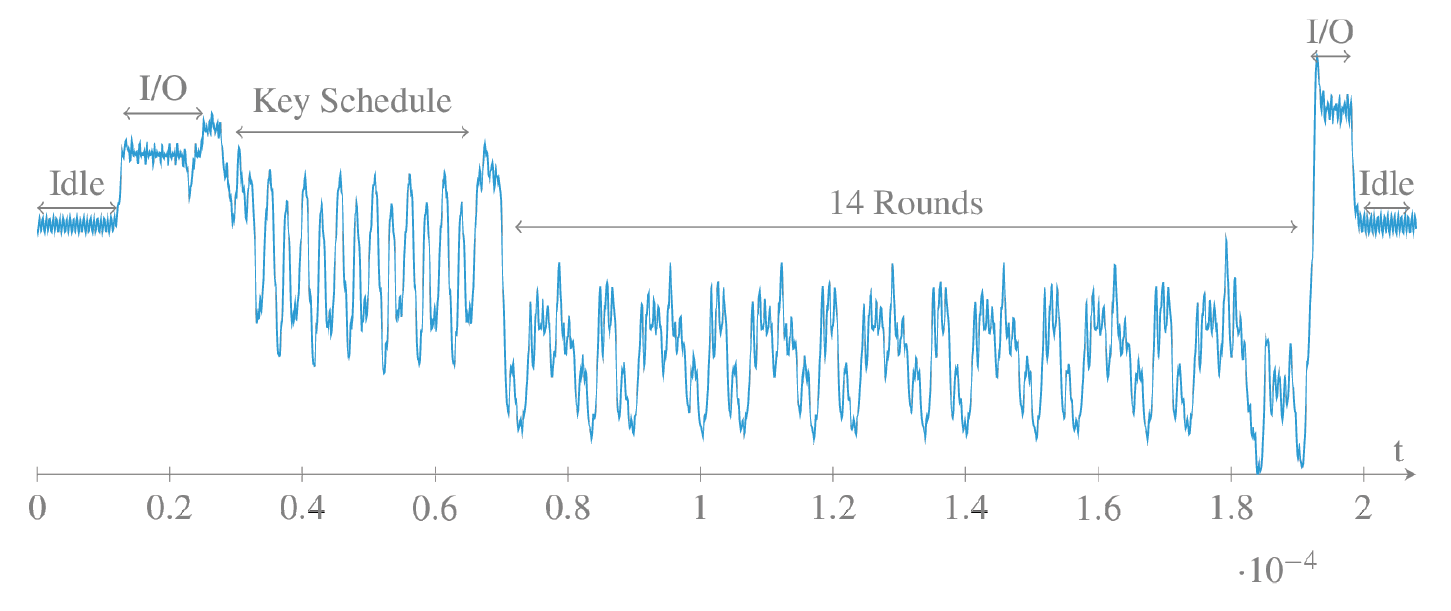
Of course, for such a small fragment the cipher cannot be restored. You need to accumulate a lot of such computing units with encryption rounds on different input data. For the accumulation of information and you need to sit next to the computer for several minutes, hiding the antenna in your pocket.
The recorded signal of electromagnetic radiation corresponds to the power consumption of the device. In turn, it correlates with the data that the processor processes at a particular point in time.
In the end, the analysis is performed using the Riscure Inspector program. The task is to find correlations between the guesswork of the key bytes and the recorded signal. This is the most difficult part, because you need to develop an effective model of information leakage from a computer’s memory into an electromagnetic field, so that the analysis can really predict the encryption key bytes. In this case, the analysis is performed by enumerating all 256 possible values of each key byte. Researchers write: in order to guess the correct value of each byte, just a few seconds is enough (256 variants per byte, for 32 bytes it is 8192 attempts). For comparison, direct brute force on AES-256 would require a brute force of 2,256 options and would continue until the end of the Universe.
So, Fox-IT specialists managed to put together all the pieces of the puzzle. As far as they can judge, this is the first public demonstration of a hidden attack on electromagnetic radiation at a distance. This is an occasion to reflect on those who are seeking to reliably protect the computer from information leaks. For such protection, you need to reliably shield it. Maybe wrapped in foil.
All Articles