
At the end of 2019, several Russian entrepreneurs turned to the Group-IB cybercrime investigation department, who faced the problem of unauthorized access by unknown persons to their correspondence in the Telegram messenger. The incidents occurred on iOS and Android devices, regardless of which client the federal mobile operator was the victim of.
The attack began when a message was sent to the Telegram messenger from the Telegram service channel (this is the official messenger channel with a blue verification checkmark) with a confirmation code that the user did not request. After that, an SMS with an activation code fell on the victim’s smartphone - and almost immediately a notification came to the Telegram service channel that the account was logged in from a new device.
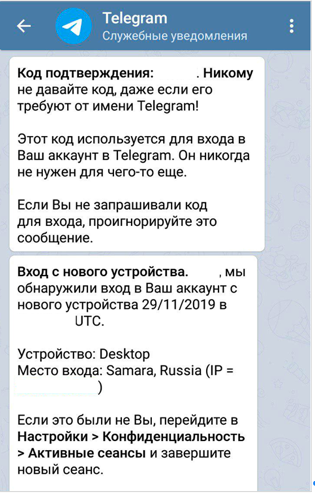
In all cases that Group-IB is aware of, attackers logged into another person’s account via the mobile Internet (they probably used disposable SIM cards), and in most cases the attackers IP address was in Samara.
Access by order
A study by Group-IB Computer Forensics Laboratory, where the electronic devices of the victims were transferred, showed that the equipment was not infected with spyware or a banking trojan, the accounts were not hacked, and no SIM cards were replaced. In all cases, the attackers gained access to the victim's messenger using SMS codes received when entering the account from a new device.
This procedure is as follows: when the messenger is activated on a new device, Telegram sends the code through the service channel to all user devices, and then (upon request) an SMS message is sent to the phone. Knowing this, the attackers themselves initiate a request to send an SMS with an activation code by the messenger, intercept this SMS and use the received code to successfully authorize in the messenger.
Thus, attackers gain illegal access to all current chats, except secret ones, as well as to the history of correspondence in these chats, including the files and photos that were sent to them. Upon discovering this, a legitimate Telegram user can forcefully terminate an attacker session. Thanks to the implemented protection mechanism, the reverse cannot occur, the attacker cannot complete the older user’s sessions in 24 hours. Therefore, it is important to detect an extraneous session in time and complete it so as not to lose access to your account. Group-IB specialists sent a notification to the Telegram team about their study of the situation.
The investigation of incidents continues, and at the moment it is not precisely established which scheme was used to circumvent the SMS factor. At different times, researchers gave examples of SMS interception using attacks on the SS7 or Diameter protocols used in mobile networks. Theoretically, such attacks can be implemented with the illegal use of special technical means or insiders in mobile operators. In particular, on hacker forums in Darknet, there are fresh announcements with offers to hack various instant messengers, including Telegram.
“Experts in different countries, including Russia, have repeatedly stated that social networks, mobile banking and messengers can be hacked using vulnerabilities in the SS7 protocol, but these were isolated cases of targeted attacks or experimental research,” comments Sergey Lupanin , Head of Group-IB Cybercrime Investigation Department, - In a series of new incidents, which are already more than 10, the attackers obviously want to put this way of earning money. In order to prevent this from happening, you need to increase your own level of digital hygiene: at least use two-factor authentication wherever possible, and add a mandatory second factor to SMS, which is functionally embedded in Telegram itself. ”
How to protect yourself?
1. Telegram has already implemented all the necessary cybersecurity options that will reduce the attacker's efforts to nothing.
2. On iOS and Android devices for Telegram, go to the Telegram settings, select the “Privacy” tab and assign “Cloud Password \ Two-step verification” or “Two step verification”. A detailed description of how to enable this option is given in the instructions on the official messenger website: telegram.org/blog/sessions-and-2-step-verification (https://telegram.org/blog/sessions-and-2-step-verification)
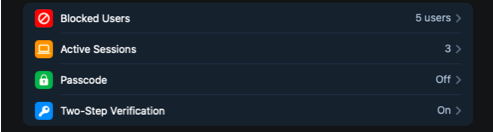
3. It is important not to set an email address to restore this password, because, as a rule, password recovery to email also occurs via SMS. Similarly, you can increase the protection of your WhatsApp account.