
Over the past decade, the number and level of complexity of cyber attacks by both pro-government hacker groups and financially motivated cybercriminals has increased significantly. People, companies and government organizations can no longer be confident in the security of cyberspace, as well as in the integrity and security of their data. The Internet has become the circulatory system of our civilization. However, the freedom of communication and the global opportunities that the Internet provides are increasingly being threatened: plums and data leaks, cyber attacks by warring states are the realities that each of us lives in today.
The leading and most frightening trend in 2019, we consider the use of cyber weapons
in open military operations. Conflict between states has taken on new forms, and cyber
activity plays a leading role in this destructive dialogue. Attacks on critical infrastructure and targeted destabilization of the Internet in individual countries usher in a new era of cyber attacks. We are confident that a peaceful existence is no longer possible in isolation from cybersecurity: this factor cannot be ignored by any state, not a single corporation, not a single person.
Six years ago, we released the first High-Tech Crime Trends report. Then it was the only study of the trends of cybercrime in Russia and one of the first in the world. As before, the Group-IB annual report shows the changes that have occurred over the year, being a single and maximally comprehensive source of strategic and tactical data on current cyber threats in the world. This study describes the period H2 2018 - H1 2019.
Conducting open military operations using cyber weapons
In the first 6 months of 2019, three open military operations became known: in March, as a result of the attack on Venezuelan hydropower plants, most of the country was left without electricity for several days, in May, in response to a cyberattack, the Israeli army launched a missile attack on Hamas hackers, and in June, the US used cyber weapons against Iranian missile launch control systems in response to a downed American drone.
No attacker tools were installed, and in the latter case, a cyber attack occurred just a few days after the drone incident. This confirms the assumption that the critical infrastructures of many countries are already compromised, and attackers simply go unnoticed until the right moment.
Violation of the stability of the Internet at the state level
In the modern world, maximum social and economic damage can be caused by disconnecting people and business from communication. At the same time, countries building centralized access control to the Internet are becoming more vulnerable and may become the first target.
In recent years, attacks on different levels of the communications infrastructure have been tested, and by 2019, successful cases of attacks on Internet routing and BGP hijacking, on domain name registrars, root DNS server administrators, national domain administrators and DNS hijacking, on local filtering systems are known and traffic blocking.

New threats associated with the widespread adoption of 5G
Switching to 5G technology will only aggravate the threat situation for the telecommunications industry. The first reason is the architectural features that open up opportunities for new types of attacks on networks of operators. The second reason is the competition for a new market, which can lead to a demonstration of the hacking capabilities of individual vendors and the emergence of a large number of anonymous studies on the vulnerabilities of certain technological solutions.
Hidden threats from pro-government groups
Despite the fact that a relatively large number of studies on new pro-government groups have been published over the past period, this area remains poorly understood. The activity of 38 groups was noticed (7 - new, the purpose of which is espionage), but this does not mean that other well-known groups have stopped their activity - most likely, their campaigns simply remained below the radar of analysts.
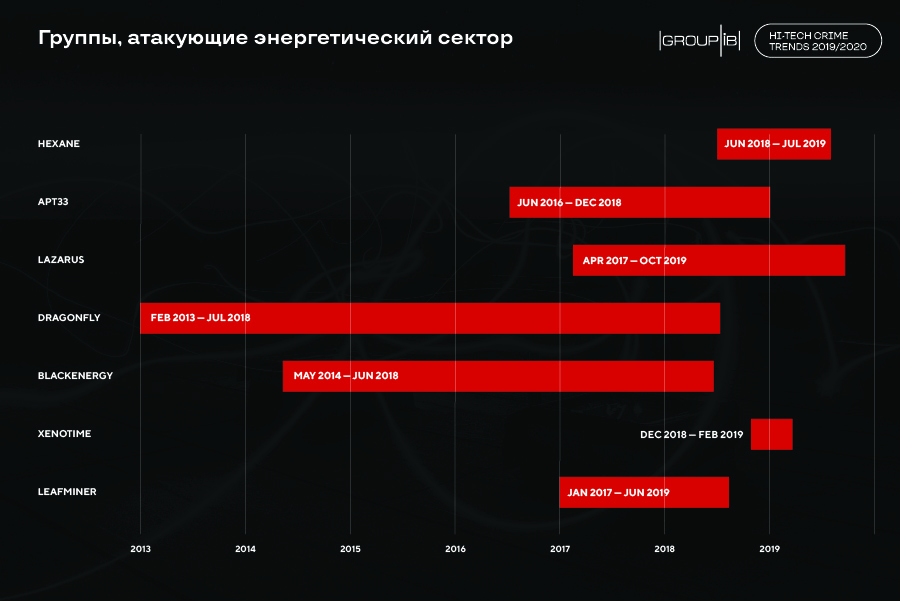
For example, in the energy sector, only two frameworks are known - Industroyer and Triton (Trisis) - and both were found as a result of the error of their operators. Most likely, there are a significant number of similar, undetected threats, and this is a time bomb.
It is also worth noting that pro-government groups known in the public space are mainly from developing countries, however, information on attacks and tools of such groups from developed countries is still not published.

Reverse hacking: opposition of pro-government groups
In 2019, cases of the appearance of publicly available information became more frequent
about attacking tools on behalf of supposedly hacktivists or former members of the group. Most often, these are examples of reverse hacking, when attackers themselves become victims. At present, private companies do not have the right to conduct such operations, and only special public services have such powers officially.
Targeted attacks on foreign banks by Russian-speaking groups
Only 5 groups now pose a real threat to the financial sector: Cobalt, Silence, MoneyTaker - Russia, Lazarus - North Korea, SilentCards - a new group from Kenya.
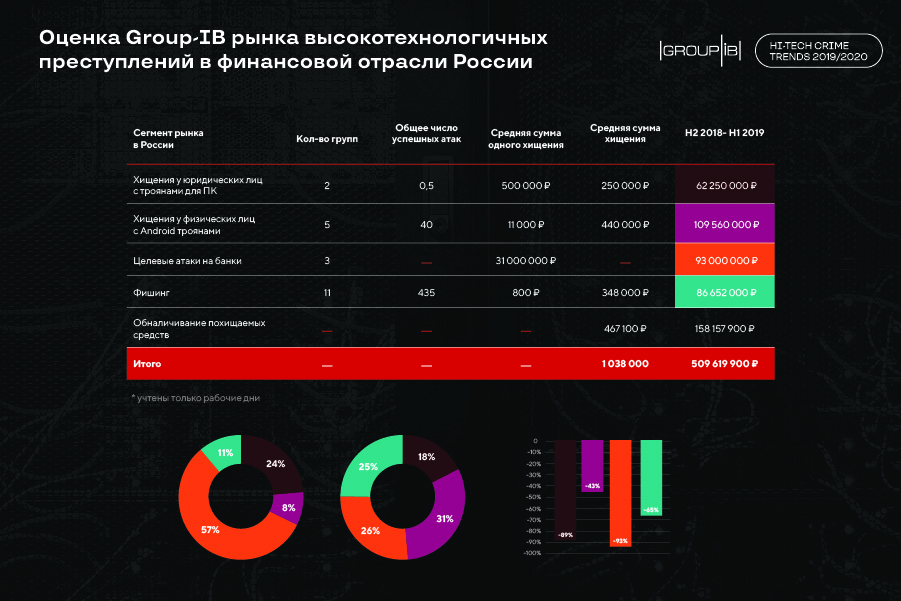
In Russia, the damage from targeted attacks on banks by financially motivated groups for the study period decreased by almost 14 times. This is due, inter alia, to switching the focus of Russian-speaking financially-motivated groups to foreign banks.

The gradual disappearance of trojans for PC and Android
The trend for the disappearance of Trojans for PCs from the landscape of cyber threats continues: in Russia - in the "home" of this type of malware - they stopped writing them. Brazil was the only country actively creating trojans, but their use is exclusively local. Only Trickbot has evolved significantly over the past year and can now be used both for targeted attacks on banks and for spying on government agencies, as was the case with the Zeus Trojan.
Trojans for Android disappear more slowly than for PCs, however, in any case, the number of new ones is several times less than obsolete. New programs evolve from SMS interception to automatic transfer of funds through bank mobile applications - auto-fill.
The number of active Trojans will continue to decline due to the introduction of defenses and a sharp reduction in economic benefits for attackers.
The evolution of social engineering without malware
Against the backdrop of the fall of the Trojans, the threat of social engineering without the use of malicious code is growing. Attackers continue to use fake accounts on social networks, make calls from reliable numbers using well-designed scripts, and buy for reliability
passport database, etc. Relatively new methods of social engineering include controlling the phone with the help of remote access programs that victims install on their devices under the guidance of telephone fraudsters.
Carding Market Growth Through JS Sniffer
With a fall in financial returns from the use of banking Trojans for PC and Android, attackers began to use a more effective way to earn money - JS-sniffers. Already, their number exceeds the number of trojans, and the total number of cards compromised with their help increased by 38%. JS sniffers will become the most dynamically developing threat, especially for countries where 3D Secure is not common.
New attacks on insurance, consulting and construction companies
In 2019, Group-IB specialists recorded attacks by a new group called RedCurl. The main goals of the group are espionage and financial gain. After unloading significant documentation, the attackers install the miners in the infrastructure of the compromised company.
A feature of this group is the very high quality of phishing attacks - for each company, attackers create a separate letter. RedCurl uses a unique proprietary trojan that communicates with the management server through legitimate services, which makes it very difficult to detect malicious activity
in infrastructure.
For more than 16 years, Group-IB experts have been investigating cyber incidents by analyzing the tools and infrastructure of attackers. Every new cyberattack aimed
to a company, political party or critical infrastructure facility, it gives us the opportunity to see the evolution of tactics and tools for their implementation. We are deeply convinced that public organizations and private actors that fight cybercrime must share data and publish
their research.
Thanks to the use of unique tools for monitoring the infrastructure of cybercriminals, as well as a thorough study of the research of other cybersecurity teams in different countries, we find and confirm common patterns that form an integral picture of the development of cyber threats. On this basis, we formulate forecasts that come true every year throughout the life of the report.
Download the full Hi-Tech Crime Trends 2019/2020 report here .