Foreword
This text will be one of the rewritten chapters for the training manual on information protection of the Department of Radio Engineering and Control Systems, as well as, from this training code, the Department of Information Protection of the MIPT (GU). The full tutorial is available on github (see also draft releases ). On Habrir I plan to upload new "big" pieces, firstly, to collect useful comments and observations, and secondly, to give the community more overview material on useful and interesting topics. Previous sections of the chapter “Cryptographic Protocols”: 1 , 2 , 3 , 4 , 5 ; next in order: 7 .
Asymmetric protocols, or protocols based on cryptosystems with public keys, can weaken the requirements for the preliminary stage of protocols. Instead of a shared secret key that two parties must have (either each of the parties and a trusted center), in the protocols considered below, the parties must first exchange public keys (between themselves or with a trusted center). Such a preliminary exchange may take place over an open communication channel, under the assumption that the cryptanalyst cannot influence the contents of the communication channel at this stage.
Denning — Sacco Protocol
The protocol was proposed by Dorothy Denning and Giovanni Sacco in 1981 ( Dorothy E. Denning, Giovanni Maria Sacco ). In this protocol, the initiator (Alice) turns to the trusted center (Trent) for certificates of both participants at once. The same participant is also responsible for the formation of a new session key .
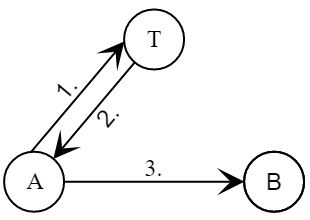
- Alice generates a new session key
- Bob verifies the trust center signature on the certificate decrypts session key and verifies Alice’s signature.
Missing Message any identifiers makes the protocol vulnerable to attack with a known session key and allows the second side (Bob) to impersonate the initiator (Alice) in a session with a third party (Clara).
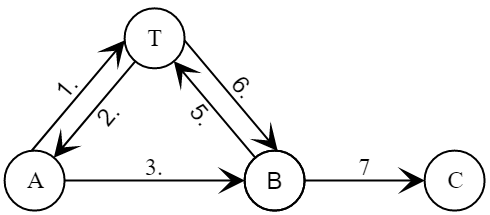
- Alice and Bob had a protocol session, generating a new session key .
- Bob plays messages and from Alice in a session with Clara:
- Clara successfully verifies the signature of the trusted center on the certificate decrypts session key and verifies Alice’s signature.
As a result, Clara is sure that she received a new session key from Alice. .
DASS Protocol
The DASS protocol was an integral part of the Distributed Authentication Security Service (DASS), developed by DEC and described in RFC 1507 in September 1993.
In the DASS protocol, by analogy with the Wide-Mouth Frog and Denning – Sacco protocols, the initiator (Alice) generates a new session key and, for each protocol session, a new pair of sender’s public and private keys. The Trusted Center (Trent) is used as a repository of participants' public key certificates. But unlike Denning-Sacco, both participants turn to the trusted center in turn.
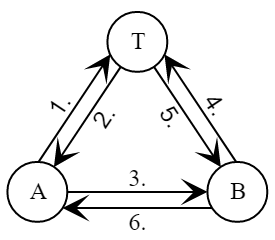
Using public key certificates and that Trent sends, and further confirmation of ownership of the corresponding keys, participants can authenticate each other. Successfully decrypting timestamps from messages and provides proof of ownership of the session key.
The protocol uses the lifetime ( ) session key but the timestamp is not included in the message. As a result, the protocol remains vulnerable to an attack with a known session key. Suppose Mellory was able to record a completely past communication session between Alice and Bob, and then was able to access the session key . This allows Mellory to authenticate herself as Alice in front of Bob.
On the first pass, Mellory changes only the first message containing a time stamp . Mellory copies the rest from the recorded communication session. If Bob does not record the keys used, he will not notice the spoofing. The simplest fix for this vulnerability is to include a timestamp in the message. .
Since the session key is in the protocol encrypted by the "master" key Bob , then compromising the latter will lead to a compromise of all previously used session keys. That is, the protocol does not provide perfect direct secrecy (goal G9).
Neither Trent nor Bob are involved in the formation of new session keys. Therefore, Alice can force Bob to use the old session key, as in the Wide-Mouth Frog and Yahalom protocols.
Wu Lama Protocol
The Wu-Lama protocol, proposed in 1992 ( Thomas YC Woo, Simon S. Lam ), adds random numbers of participants to messages, which protects the protocol, including from repeated attacks, and also provides confirmation of key ownership. It is also the only protocol considered in this section in which a new key is generated by a trusted party (Trent).
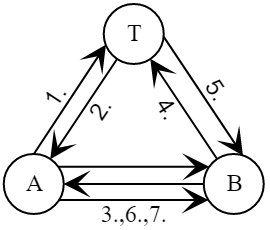
Since in the session key certificate Alice's random number is present , the attacker will not be able to use the old certificate in a new session on behalf of Bob. Therefore, the 6th pass of the protocol allows Alice to make sure that Bob knows the new session key , and therefore owns his "master" key (as this is the only way to get the certificate from the message )
Message from Alice to Bob on the seventh passage allows us to guarantee at the same time that Alice knows her “master” key (since it was able to decrypt ), and a new session key because it was able to correctly encrypt this key.
Afterword
The last section of the chapter on key distribution is the already published material on the quantum protocol BB84 . So the current article actually completes the series of sections about cryptographic protocols for Habr. The author will be grateful for factual and other comments on the text.