
I was once at ZeroNights, this is another conference on information security, which this year was completely slag.
There, as always, I wanted to break something, get a prize for it, etc., but as I found out, there were no interesting tasks there, and I had to entertain myself.
What happened there doesn’t carry a special semantic load, but what started later is something.
As the conference ended, all its participants took tickets for the peregrine falcon, the last peregrine falcon St. Petersburg - Moscow leaves at 21:00, and I had time for it ...
Took a place in Sapsan
I sat down in my seat in the carriage, thought what to do, and began to read a book, when suddenly a man came up to me and asked me to change places, for he was going with his girlfriend. I have changed, because as they say give good to people - and it will return to you.
I was sitting reading a book, and I realized that damn it, I didn’t break off anything interesting, I’ll sit down for my pentest of the task, which remained unfulfilled.
I decided to go to the post office, but the Internet did not catch, on the way there was often 2G coverage, which was AWESOME.
I decided to connect to the local WiFi peregrine falcon.
I did it for the first time!
Well, then, he asked me to enter the car number, places and the last 4 digits of the passport for authorization, and here I was already a little interested in what I can do with this Sapsan grid, but nevertheless, the pentest of work task was a priority.
I go to Yandex mail, and I see this picture:
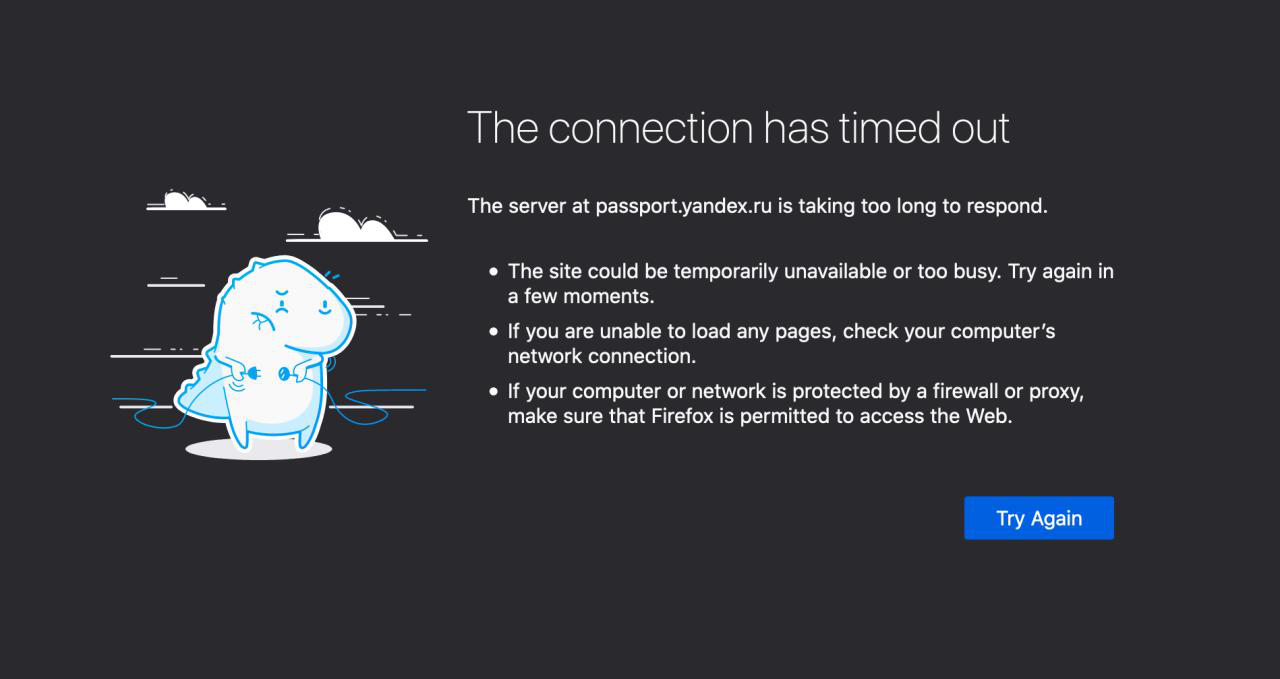
super slow internet didn’t even load mail
And I thought, and to hell with him, I’ll have to read a book ... And then I remembered what aroused my interest, and this is authorization in WiFi by the numbers of the passport and the number of the place with the car. So Sapsan locally stores data on all passengers, who is in what place. But what if you check how difficult it is to access it.
I needed only NMAP and a couple of public exploits.
I will not describe data for authorization in systems, so as not to offend Russian Railways (the data for authorization is the same on all peregrine falcons).
How I broke Peregrine Falcon
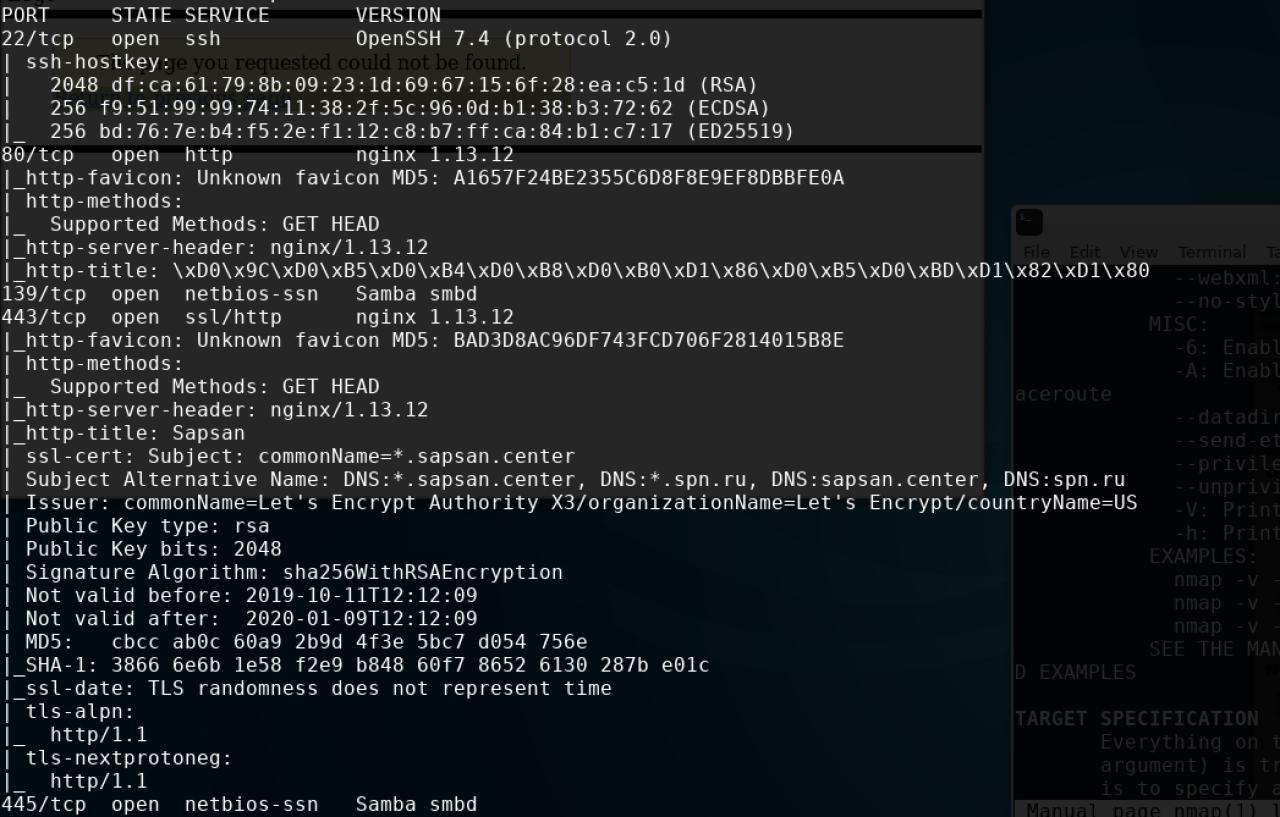
I run nmap with the -v -A sapsan.center options, and see which ports are open for them.
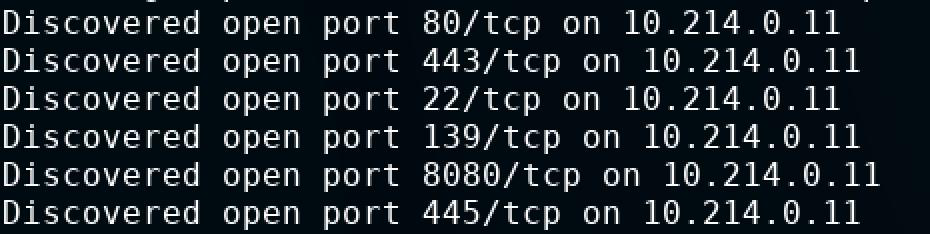
And I understand that a lot of services are hanging.
I won’t disclose all ports, but much can be seen in the screenshots :-) I think you shouldn’t cover up, because the same hack will take you no more than 20 minutes (20 minutes only because their server lags).
Well, I went for a walk on the services that stand there.
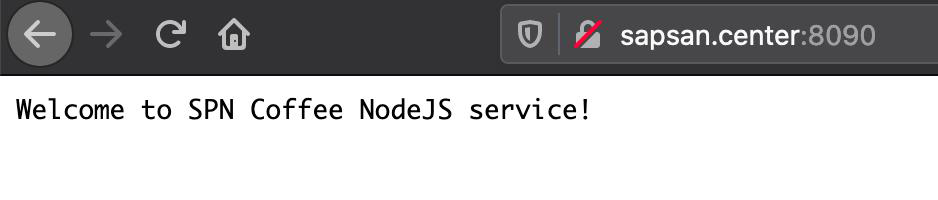
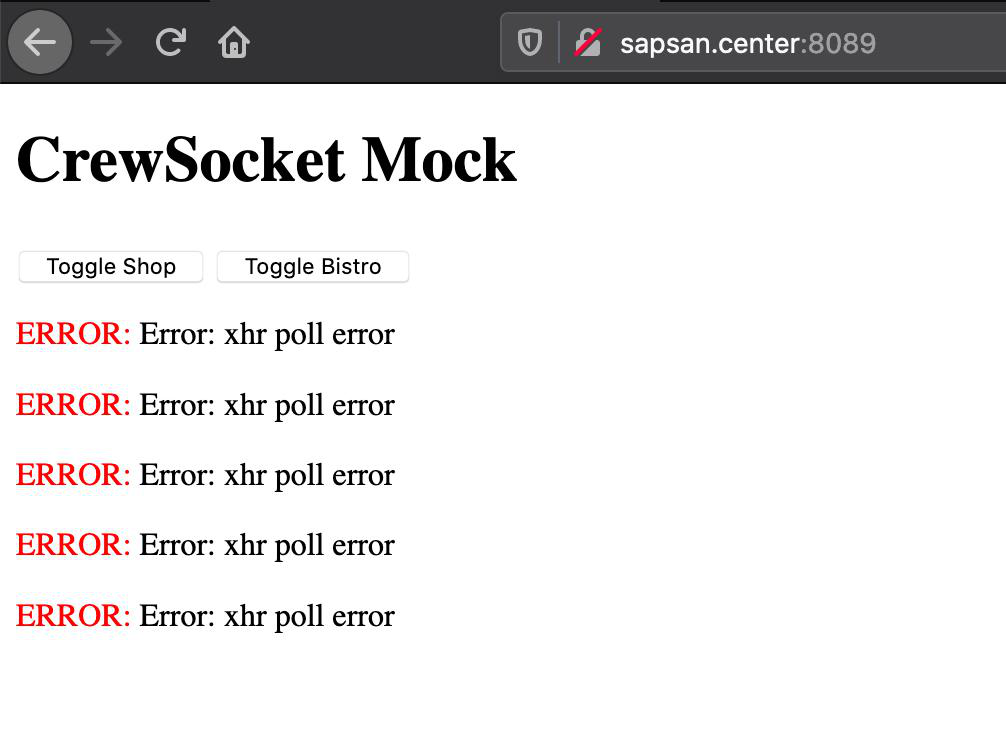
And without hesitation, I realized that they have one server for everything, and there is a stupid docker there. I got to cAdvisor, and ofigel.
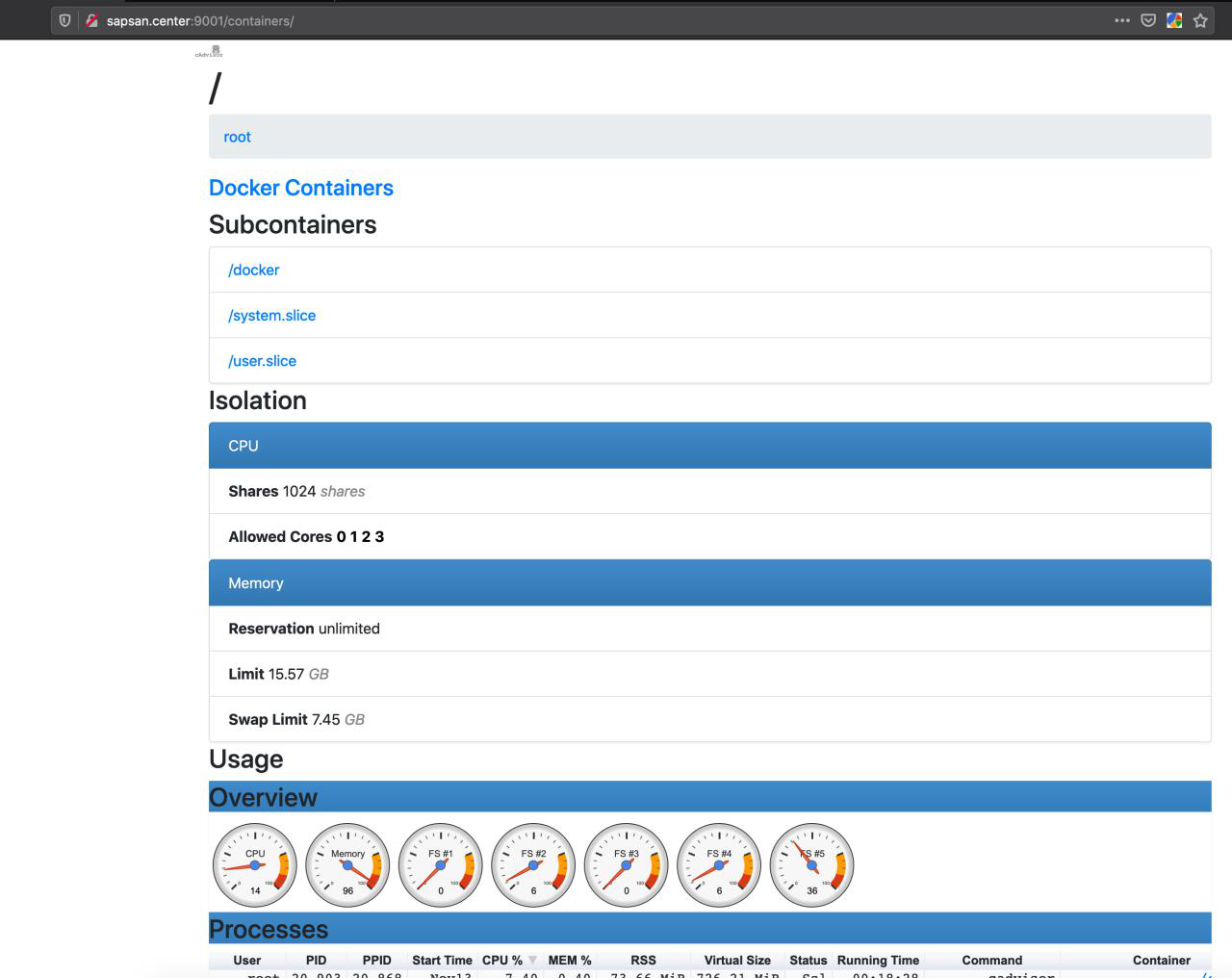
With RAM on their server everything is bad, does MB lag on this? Let's see what they generally have, which containers work, which processes are running, etc.
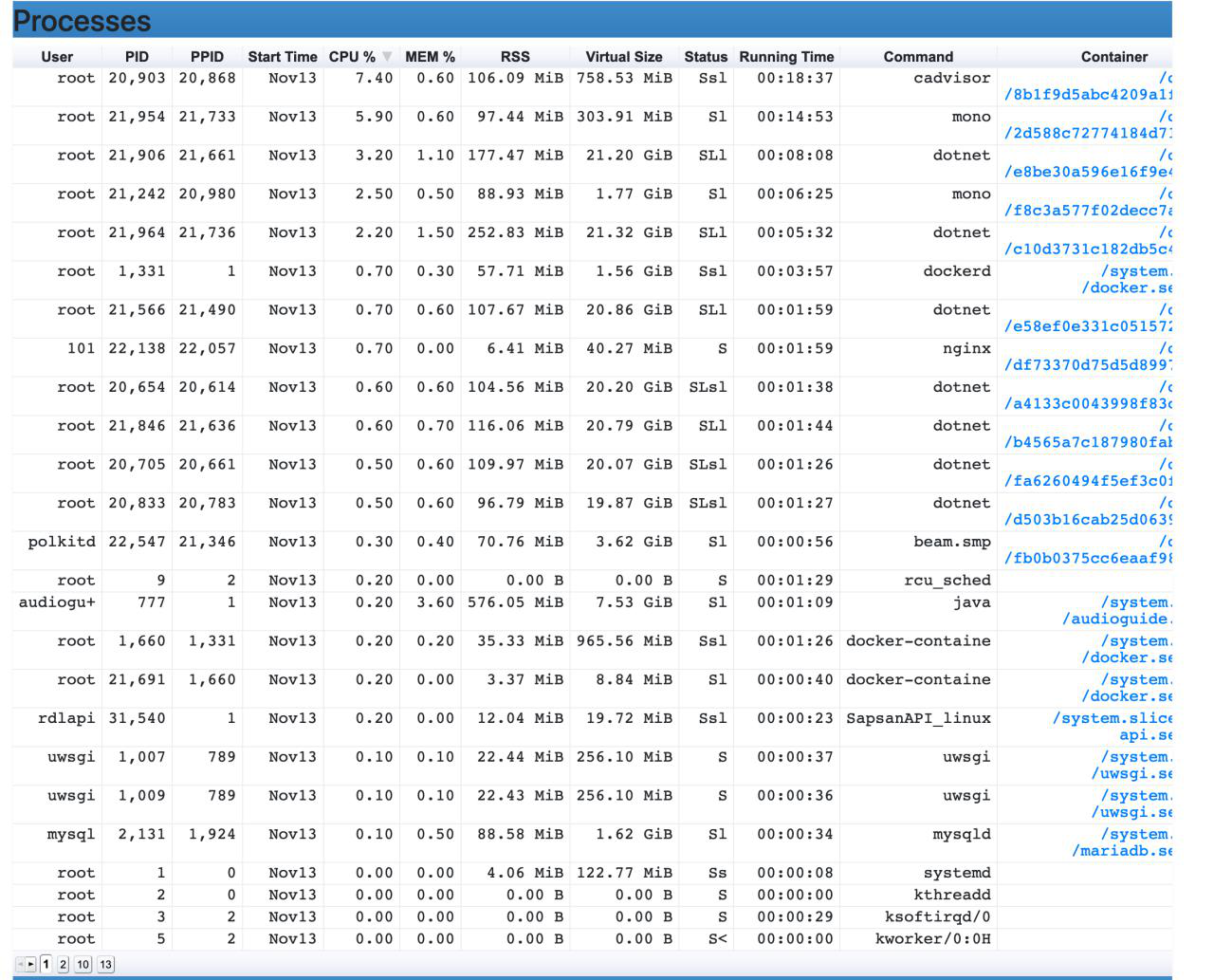
He funnily wants to run under the centos, if there is no Windows to put next, but as I recall, Net Core eats more under the line of RAM than under Windows.
Then I went to study the contents of the containers, and some public CVE flooded into the system. (they have simple passwords, and ssh access to the root is open).
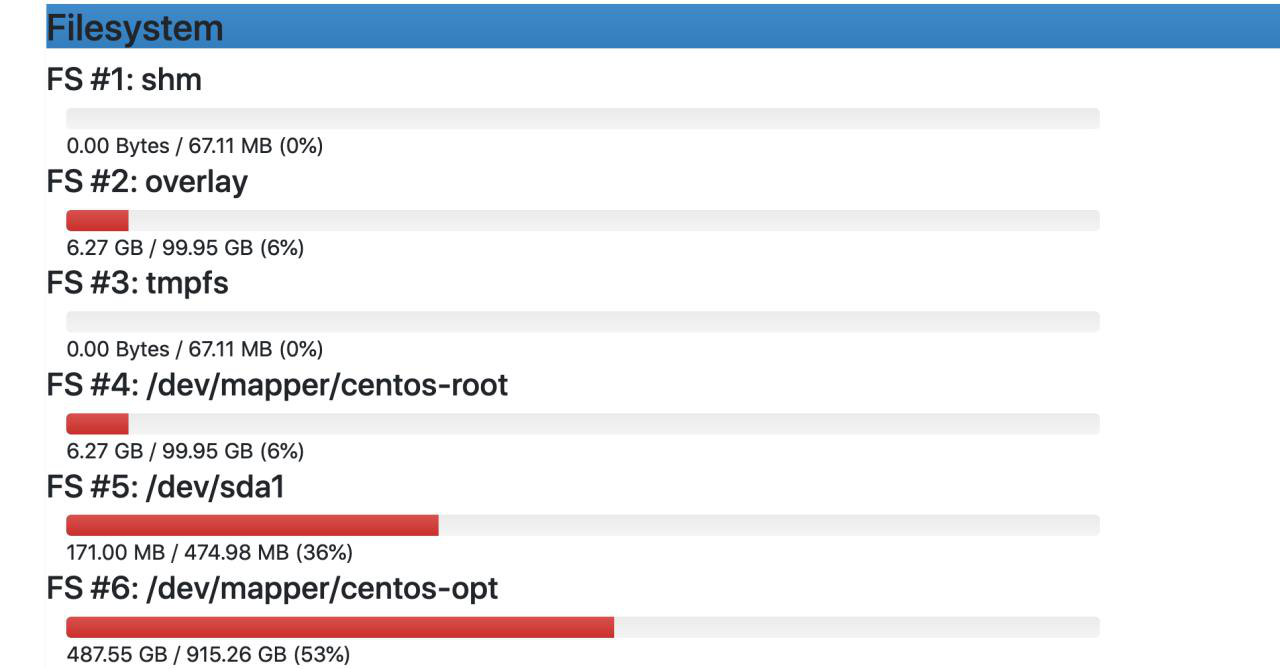
They had a lot of good info stored on the disk, and in the database (mysql) they had all the passengers of the current and past flights.
Also from there, the Russian Railways network has If you want, you will find it there yourself.
But most of all I was killed by the fact that Russian Railways did not even spend on a certificate, and put let's encrypt on their domains for HTTPS
The conclusion from all this:
I did not take many screenshots, because I did not think to write an article. But a few years ago I already applied to Russian Railways with a vulnerability, and they shaved me with the payment and just fixed it, so my attitude towards them is not so hot. Although I do not publish personal data.
Everything is configured terribly, the same passwords everywhere - a sign of a good admin, and the storage of data in text documents is also buzzing. Especially tasks in the crown. Russian Railways, correct everything, I’ll check it again in a couple of months.
Everyone who is connected to their WiFi is subject to traffic sniffs, because everything goes through their proxies, you can easily collect HTTP traffic, but if you try a little, then HTTPS (checked).
It is not difficult to get access to the data of the passengers of the flight, and it takes 20 minutes on their strength.
I hope you enjoyed my reading, even though I don’t know how to write articles. For fan mb something else then break off.
All good, and breaks for the fan.