
In December 2018, Group-IB specialists discovered a new family of sniffers called FakeSecurity . They were used by one criminal group that infected sites run by CMS Magento. An analysis showed that in a recent campaign, attackers conducted an attack using malware to steal passwords. The victims were the owners of online shopping sites that were infected with a JS sniffer. Information Security Incident Response Center CERT Group-IB warned the attacked resources, and Threat Intelligence Group-IB analyst Viktor Okorokov decided to talk about how it was possible to identify criminal activity.
Recall that in March 2019, Group-IB published the report “Crime without punishment: analysis of JS-sniffer families”, which analyzed 15 families of different JS-sniffers that were used to infect more than two thousand online store sites.
Single address
During the infection, the attackers injected a link to a malicious script into the site code, this script was loaded and at the time of payment for the goods intercepted the payment data of the online store visitor, and then sent them to the attackers server. In the early stages of attacks using FakeSecurity, malicious scripts and sniffer gates themselves were located on the same magento-security [.] Org domain.

Later, some Magento sites were infected with the same sniffer family, but this time the attackers used new domain names to host the malicious code:
- fiswedbesign [.] com
- alloaypparel [.] com
Both of these domain names were registered to the same email address greenstreethunter @ india [.] Com . The same address was provided during the registration of the third domain name firstofbanks [.] Com .

Convincing request
An analysis of the three new domains used by the criminal group FakeSecurity showed that some of them were involved in the malware distribution campaign, which began in March 2019. Attackers distributed links to pages that said that the user needs to install the missing plug-in for the correct display of the document. If the user started downloading the application, his computer was infected with malware to steal passwords.

In total, 11 unique links were revealed that led to fake pages that prompted the user to install malware.
- hxxps: //www.etodoors.com/uploads/Statement00534521 [.] html
- hxxps: //www.healthcare4all.co.uk/manuals/Statement00534521 [.] html
- hxxps: //www.healthcare4all.co.uk/lib/Statement001845 [.] html
- hxxps: //www.healthcare4all.co.uk/doc/BankStatement001489232 [.] html
- hxxp: //verticalinsider.com/bookmarks/Bank_Statement0052890 [.] html
- hxxp: //thepinetree.net/n/docs/Statement00159701 [.] html
- hxxps: //www.readicut.co.uk/media/pdf/Bank_Statement00334891 [.] html
- hxxp: //www.e-cig.com/doc/pdf/eStmt [.] html
- hxxps: //www.genstattu.com/doc/PoliceStatement001854 [.] html
- hxxps: //www.tokyoflash.com/pdf/statment001854 [.] html
- hxxps: //www.readicut.co.uk/media/pdf/statment00789 [.] html
A potential victim of a malicious campaign received spam e-mail, the letter contained a link to a page of the first level. This page is a small HTML document with an iframe, the content of which is loaded from a second-level page. The second-level page is a landing page with content that prompts the recipient to install a certain executable file. In the case of this malicious campaign, the attackers used a landing page with the theme of installing the missing plug-in for Adobe Reader, so the first-level page imitated a link to a PDF file that was opened in an online viewing mode in a browser. The second-level page contains a link to a malicious file distributed as part of a malicious campaign, which will be downloaded when the Download plugin button is clicked.
An analysis of the pages used in this campaign showed that usually the second-level pages were located on the domains of the attackers, while the first-level page and the directly malicious file were most often on the hacked e-commerce sites.
Example page structure for malware distribution
Through spam, a potential victim receives a link to an HTML file, for example, hxxps: //www.healthcare4all [.] Co [.] Uk / manuals / Statement00534521 [.] Html . The HTML file by reference contains an iframe element with a link to the main content of the page; in this example, the page content is located at hxxps: // alloaypparel [.] com / view / public / Statement00534521 / PDF / Statement001854 [.] pdf . As we see from this example, in this case, the attackers used the registered domain, and not the hacked site, to host the page content. In the interface that is displayed via this link, there is a Download plugin button. If the victim clicks this button, the executable file will be downloaded from the link specified in the page code; in this example, the executable file is downloaded at hxxps: //www.healthcare4all [.] co [.] uk / manuals / Adobe-Reader-PDF-Plugin-2.37.2.exe , that is, the malicious file itself is stored on the hacked site.
Mephistopheles of our time
An analysis of the alloaypparel [.] Com domain revealed that the malware distribution used the Mephistophilus phishing kit to create and deploy phishing pages for the distribution of malware: Mephistophilus uses several types of landing pages that prompt the user to install the supposedly missing plug-in necessary for the application to work. In fact, the user will be installed malware, a link to which the operator adds through the administrative panel Mephistophilus.
The Mephistophilus system for targeted phishing attacks was launched on clandestine forums in August 2016. This is a standard phishing kit using web fakes offering malware downloads under the guise of a plugin update (MS Word, MS Excel, PDF, YouTube) to view the contents of a document or page. Mephistophilus was developed and released for sale by the user of underground forums under the nickname Kokain. To successfully infect using a phishing kit, an attacker must prompt the user to click on the link leading to the page generated by Mephistophilus. Regardless of the topic of the phishing page, a message appears that you need to install the missing plug-in for the correct display of an online document or YouTube video. To do this, Mephistophilus has several types of phishing pages that mimic legitimate services:
- Microsoft Office365 Word or Excel Online Document Viewer
- Online PDF Viewer
- YouTube Clone Page

Injured
As part of the malware campaign, the criminal group was not limited to using self-registered domain names: attackers also used several online store sites that had previously been infected with the FakeSecurity sniffer to store samples of distributed malicious files.
In total, 5 unique links were found to 5 unique samples of malware, 4 of which were stored on hacked sites running CMS Magento:
- hxxps: //www.healthcare4all [.] co [.] uk / manuals / Adobe-Reader-PDF-Plugin-2.37.2.exe
- hxxps: //www.genstattu [.] com / doc / Adobe-Reader-PDF-Plugin-2.31.4.exe
- hxxps: // firstofbanks [.] com / file_d / Adobe-Reader-PDF-Plugin-2.35.8.exe
- hxxp: // e-cig [.] com / doc / Adobe-Reader-PDF-Plugin-2.31.4.exe
- hxxp: // thepinetree [.] net / docs / msw070619.exe
The malware samples distributed in this campaign are samples of the Vidar styler designed to steal passwords from browsers and some applications. He also knows how to collect files according to specified parameters and transfer them to the administrative panel, which facilitates, for example, theft of cryptocurrency wallet files. Vidar presents malware-as-a-service: all the data collected is transmitted to the gate, and then sent to the centralized administration panel, where each buyer of the styler can view the logs that came from infected computers.
Capable thief
Vidar Styler appeared in November 2018. It was developed and put up for sale on underground forums by a user under the pseudonym Loadbaks. According to the description of the developer, Vidar can steal passwords from browsers, files by certain paths and masks, bank card data, cold wallet files, Telegram and Skype correspondence, as well as browsing history of sites. The rental price of the styler is from $ 250 to $ 300 per month. The admin panel of the styler and the domains used as gates are located on the servers of the Vidar authors, which reduces infrastructure costs for customers.
In the case of the msw070619.exe malicious file, in addition to spreading using the Mephistophilus landing page, a malicious DOC file BankStatement0040918404.doc (MD5: 1b8a824074b414419ac10f5ded847ef1) was also detected, which dropped this executable file to disk using macros. The BankStatement0040918404.doc DOC file was attached as an attachment to malicious emails, the distribution of which was part of a malicious campaign.
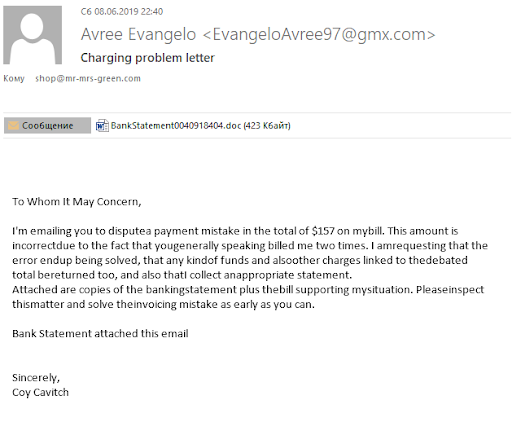
Prepare the attack
The detected message (MD5: 53554192ca888cccbb5747e71825facd) was sent to the contact address of the site running CMS Magento, from which it can be concluded that the administrators of online stores were one of the targets of the malicious campaign, and the purpose of the infection was access to the administrative panel of Magento and other e-commerce -platforms for subsequent installation of a sniffer and theft of customer data from infected stores.
Thus, the infection scheme as a whole consisted of the following steps:
- The attackers deployed the Mephistophilus Phishing Kit admin panel on alloaypparel [.] Com .
- Attackers placed malicious password theft malware on hacked legitimate sites and on their own sites.
- Using a phishing kit, attackers deployed several landing pages for the distribution of malware, as well as created malicious documents with a macro that downloaded malware onto a user's computer.
- Attackers conducted a spam campaign to send letters with malicious attachments, as well as with links to landing pages for installing malware. At least part of the attackers' goals are the administrators of online shopping sites.
- If the administrator’s computer’s computer was successfully compromised, the stolen credentials were used to access the store’s administrative panel and install the JS-sniffer to steal bank cards of users making payments on the infected site.
Link to other attacks
The attacking infrastructure was deployed on a server with the IP address 200.63.40.2, which belongs to the Panamaservers [.] Com server rental service. Before the FakeSecurity campaign, this server was used for phishing, as well as for hosting administrative panels of various malicious programs to steal passwords.
Based on the specifics of the FakeSecurity campaign, it can be assumed that the administrative panels of the Lokibot and AZORUlt stylers located on this server could be used in previous attacks of the same group in January 2019. According to this article , on January 14, 2019, unknown attackers distributed Lokibot malware by mass mailing with a malicious DOC file in an attachment. On January 18, 2019, a mailing list of malicious documents that installed the AZORUlt malware was also performed. The analysis of this campaign revealed the following administrative panels located on the server with the IP address 200.63.40.2:
- http [:] // chuxagama [.] com / web-obtain / Panel / five / PvqDq929BSx_A_D_M1n_a.php (Lokibot)
- http [:] // umbra-diego [.] com / wp / Panel / five / PvqDq929BSx_A_D_M1n_a.php (Lokibot)
- http [:] // chuxagama [.] com / web-obtain / Panel / five / index.php (AZORUlt)
The domain names chuxagama [.] Com and umbra-diego [.] Com were registered by the same user with the email address dicksonfletcher@gmail.com. The same address was used to register the worldcourrierservices [.] Com domain name in May 2016, which was then used as a site for the fraudulent company World Courier Service.
Based on the fact that, as part of the FakeSecurity malware campaign, attackers used malware to steal passwords and distributed it through spam e-mail, and also used a server with an IP address of 200.63.40.2, it can be assumed that a malicious campaign was carried out in January 2019 the same criminal group.
Indicators
File name Adobe-Reader-PDF-Plugin-2.37.2.exe
- MD5 3ec1ac0be981ce6d3f83f4a776e37622
- SHA-1 346d580ecb4ace858d71213808f4c75341a945c1
- SHA-256 6ec8b7ce6c9858755964f94acdf618773275589024e2b66583e3634127b7e32c
- Size 615984
File name Adobe-Reader-PDF-Plugin-2.31.4.exe
- MD5 58476e1923de46cd4b8bee4cdeed0911
- SHA-1 aafa9885b8b686092b003ebbd9aaf8e604eea3a6
- SHA-256 15abc3f55703b89ff381880a10138591c6214dee7cc978b7040dd8b1e6f96297
- Size 578048
File name Adobe-Reader-PDF-Plugin-2.35.8.exe
- MD5 286096c7e3452aad4acdc9baf897fd0c
- SHA-1 26d71553098b5c92b55e49db85c719f5bb366513
- SHA-256 af04334369878408898a223e63ec50e1434c512bc21d919769c97964492fee19
- Size 1069056
File name Adobe-Reader-PDF-Plugin-2.31.4.exe
- MD5 fd0e11372a4931b262f0dd21cdc69c01
- SHA-1 54d34b6a6c4dc78e62ad03713041891b6e7eb90f
- SHA-256 4587da5dca2374fd824a15e434dae6630b24d6be6916418cee48589aa6145ef6
- Size 856576
File name msw070619.exe
- MD5 772db176ff61e9addbffbb7e08d8b613
- SHA-1 6ee62834ab3aa4294eebe4a9aebb77922429cb45
- SHA-256 0660059f3e2fb2ab0349242b4dde6bf9e37305dacc2da870935f4bede78aed34
- Size 934448
- fiswedbesign [.] com
- alloaypparel [.] com
- firstofbanks [.] com
- magento-security [.] org
- mage-security [.] org
- https [:] // www [.] healthcare4all [.] co [.] uk / manuals / Adobe-Reader-PDF-Plugin-2.37.2.exe
- https [:] // www [.] genstattu [.] com / doc / Adobe-Reader-PDF-Plugin-2.31.4.exe
- https [:] // firstofbanks [.] com / file_d / Adobe-Reader-PDF-Plugin-2.35.8.exe
- http [:] // e-cig [.] com / doc / Adobe-Reader-PDF-Plugin-2.31.4.exe
- http [:] // thepinetree [.] net / docs / msw070619.exe