
This article will solve several more problems. Links to other parts below.
The first part: Ethernet, FTP, Telnet, HTTP, Bluetooth - the basics of traffic analysis. Solving problems on a network with r0ot-mi.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
Cisco password
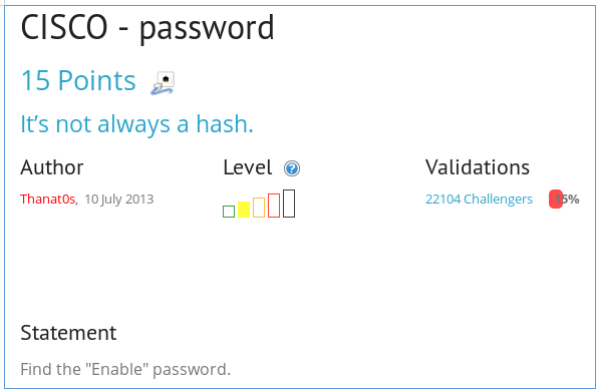
We are asked to find enable password and give cisco config.
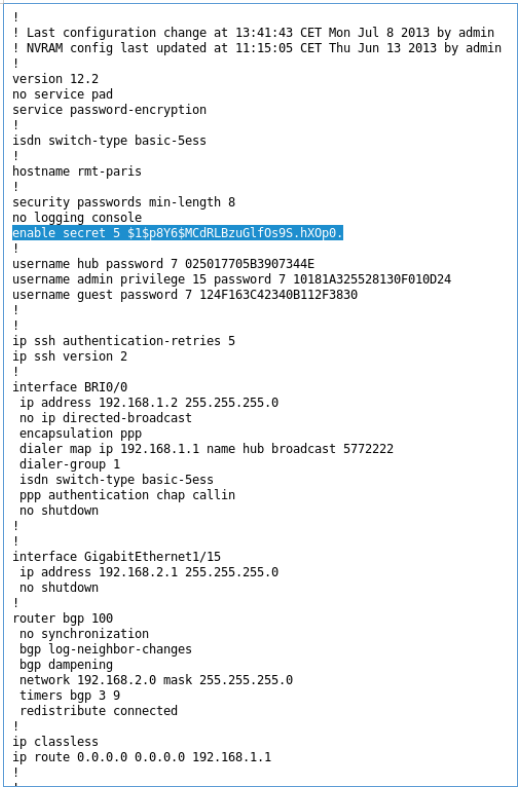
The config contains its hash, let's scroll through it. I will use hashcat.
hashcat -a 0 -m 500 cisco_hash rockyou.txt --force
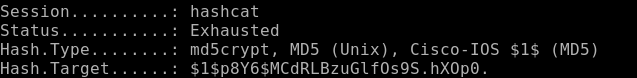
And we do not find the password. Let's quack others. You can use this site for this .
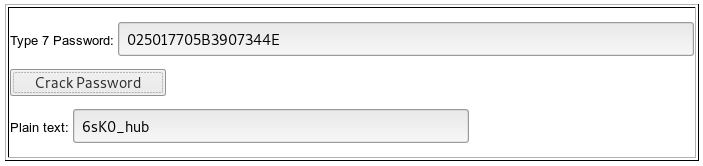
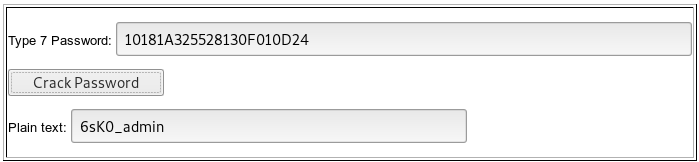
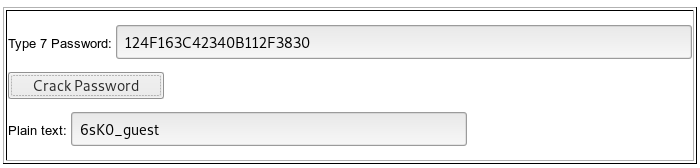
We crack all cisco type 7 passwords. We see the pattern: 6sK0_ user name. Let's take a hash from the line 6sK0_enable by a similar principle. First, a little about the hash format.
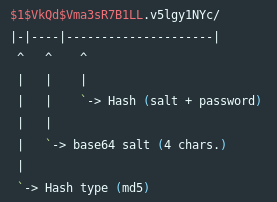
As you can see, the hash consists of three parts. The first part is a hash type (in this case MD5, we used it in hashcat), the second and third part are salt and hash. We use python.
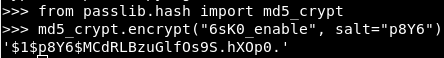
This hash matches the hash in the config. The problem is solved.
DNS zone transfert

As can be understood from the task, we need to complete the transfer of the DNS zone.
DNS zone transfer is a type of DNS transaction. It is one of the mechanisms for synchronizing the contents of several DNS databases between servers. Information contained in the DNS zone can be considered confidential from the point of view of operational security. For example, resource records may contain server role information or SSH key fingerprints.
You can transfer a zone using the dig program, where we specify the host, port, transaction type - axfr, and domain.
dig @challenge01.root-me.org -p 54011 axfr ch11.challenge01.root-me.org
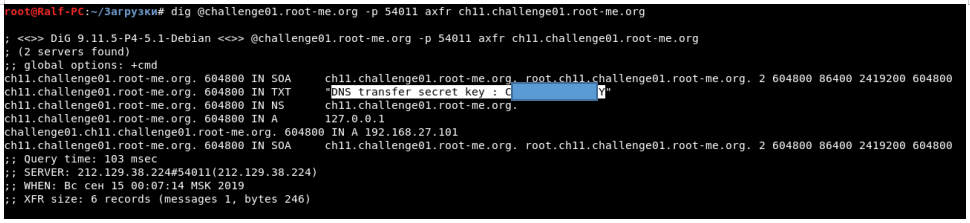
We get the secret key.
IP TTL

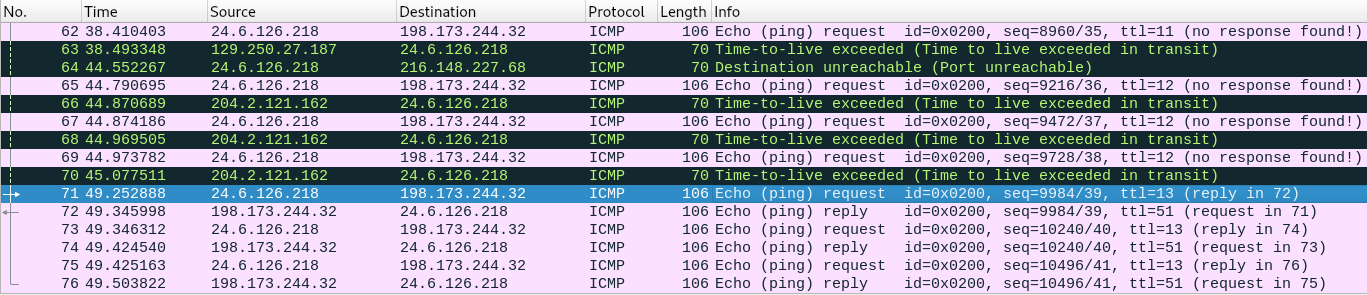
We are given a traffic dump and are asked to find the TTL used to reach the target host. It is very easy. We open the dump and notice that some answers are marked in black, while the TTL is 11 and 12. When the request TTL is 13, the answer comes without errors. That is, the desired TTL is 13.
LDAP null bind
We need to access the data, from where it will be necessary to find out the email address.
LDAP is an easily extensible directory access protocol that uses TCP / IP and allows authentication (bind), search (search) and comparison (compare), as well as the operation of adding, changing or deleting entries.
The name of the task hints at a null request. The fact is that such a request does not require authentication to receive information. We will test using the ldapsearch program. A little about the options: we need to specify the host (-H), specify the normal authentication (-x), the nesting level of the search (-s) in this case only in the root entry (base), and also the type of attributes - we will also search for user attributes (* ) and operating (+).
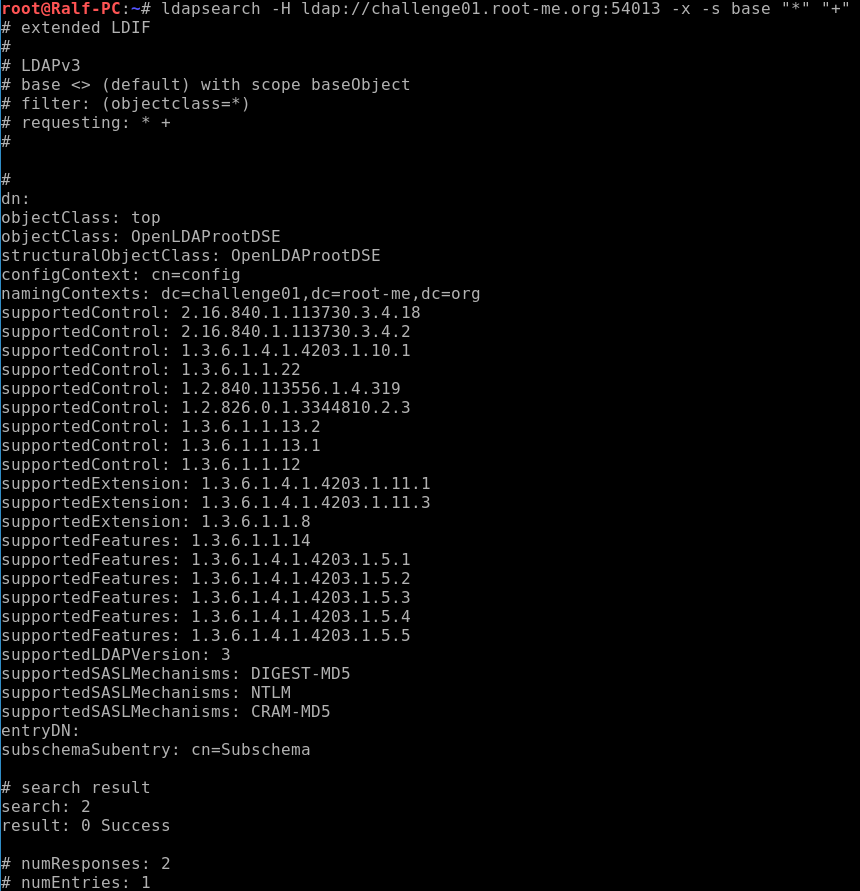
As you can see, the attributes were returned to us, which means the assumption about the zero request was correct. Moreover, namingContexts matches what is given in the task.
There is no organization unit in the address provided to us. Since the request is zero, we will specify the standard anonymous.

We get the data where we find the mail.
SIP authentication
Need to find a password. This is very easy, as the last column contains either a hash or a password. Trying PLAIN ... Fits ...

I would argue over the complexity of this assignment and its assessment.
ETHERNET - Patched transmission
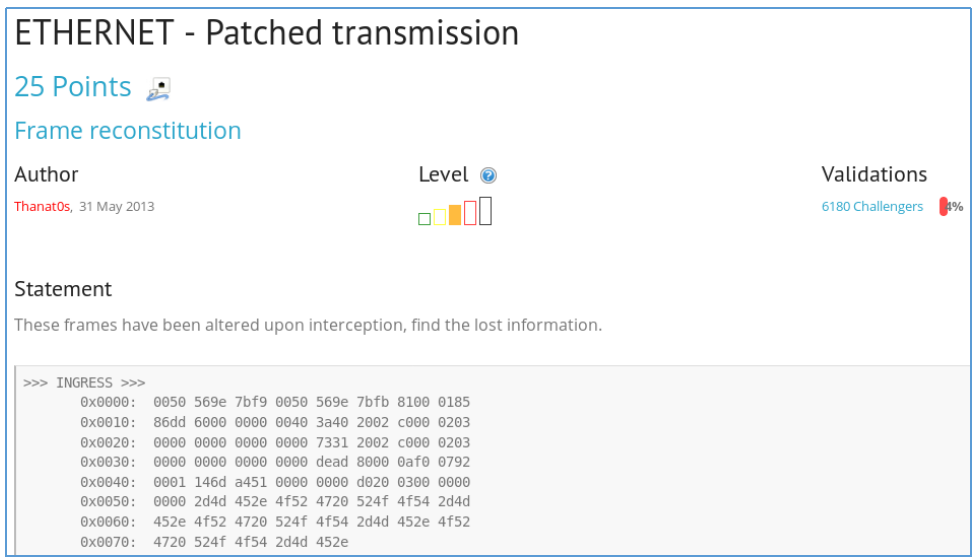
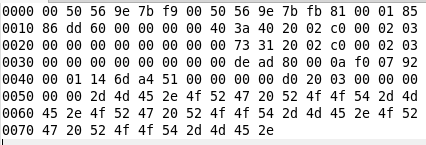
We are given packages in hexadecimal form. In the last packet, 10 bytes were changed, they need to be restored. The most convenient way to work with packages is in Wireshark. In order to load a hexadecimal dump, you need to bring it to the following form.
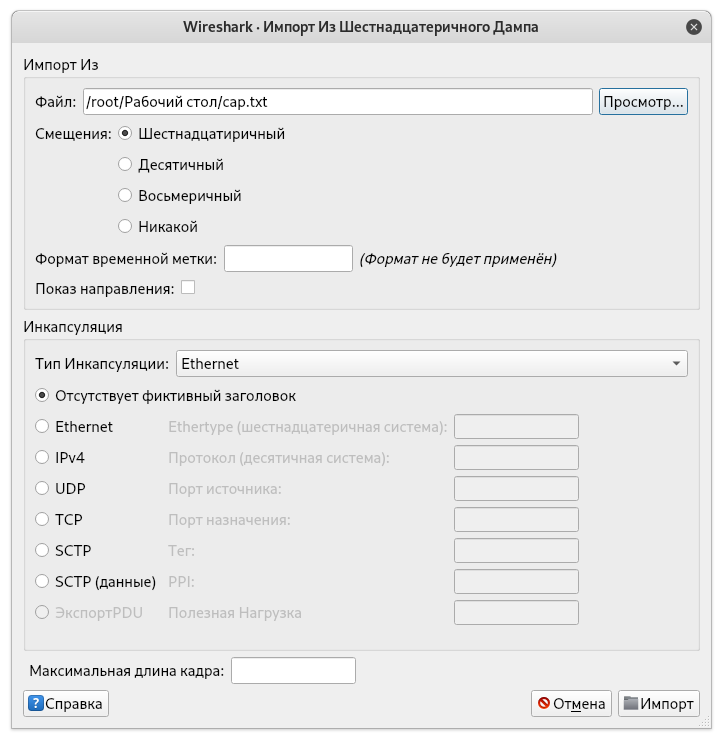
Next, select File -> Import from Hex ...
After downloading all the packages, you need to merge them. To do this, select File -> Merge. Now we have the following picture.
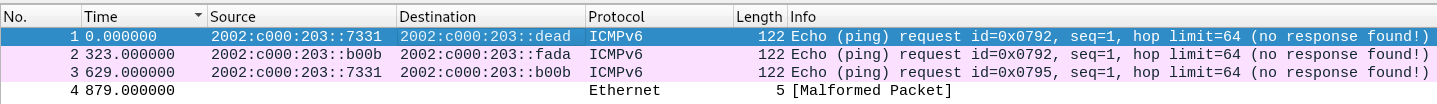
We look at what bytes need to be restored.
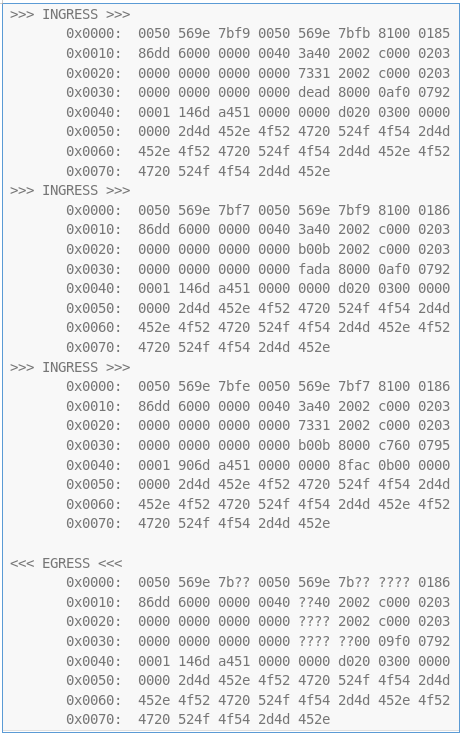
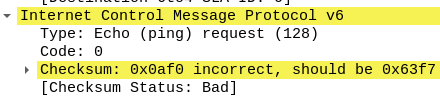
We take into account 2 facts. The first: three request packets and one response packet, the second: 1 and 3 packets are marked with a bad checksum.
From this we can conclude that we are analyzing the ICMPv6 response to the request of the second packet. Let's start the order. The first 16 bytes are the MAC addresses of the receiver and source. We take from the second package and change places, i.e. first 2 unknown bytes of f9f7. Next comes the types 8100 and 3a. Next come the IP addresses of the source and receiver, also swap from the second packet - fadab00b.
The last byte is left. This is a type of ICMPv6 message.
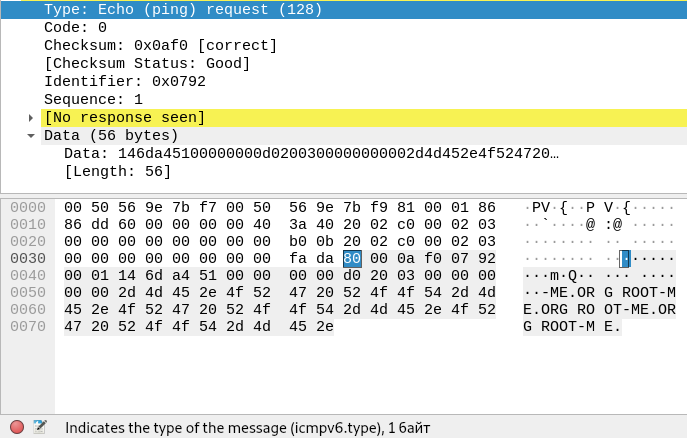
In the second request (128) packet, we have responce.

That is, the last byte sought is 81. We collect, send, the answer is correct.
Further more and more complicated ... You can join us on Telegram . There you can propose your own topics and vote on the choice of topics for the following articles.