To solve this problem, you can use the radius authentication plug-in for the apache2 server. All actions on the Web server are performed for the Linux Debian stretch distribution .
Web server setup
1. Install the radius module for apache2:
sudo apt install libapache2-mod-auth-radius sudo a2enmod auth_radius
2. We select the necessary site and in its configuration we make changes:
ServerName web1.test2.ru ServerAdmin webmaster@localhost DocumentRoot /var/www/html # radius (, , ) AddRadiusAuth 127.0.0.1 P@ssw0rd 5 AddRadiusCookieValid 60
In the section "Directory" also indicate:
AuthType Basic AuthName "Radius Authentication" AuthBasicAuthoritative Off AuthBasicProvider radius AuthRadiusAuthoritative on AuthRadiusActive On Require valid-user
3. Reboot the web server daemon:
sudo apache2ctl restart
The web server is ready.
Configuring Radius Server (NPS)
Launch the NPS management console.
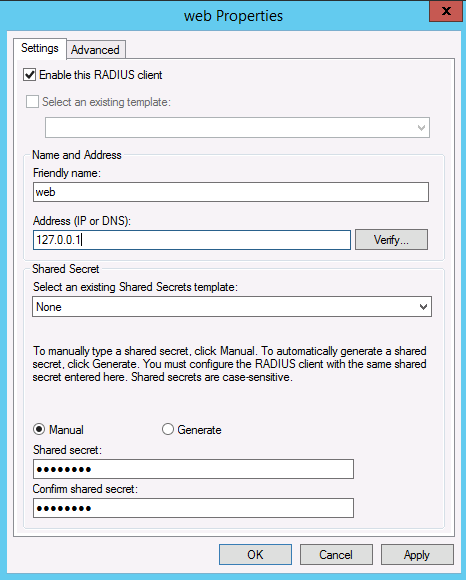
1. Add our Web server as a client:
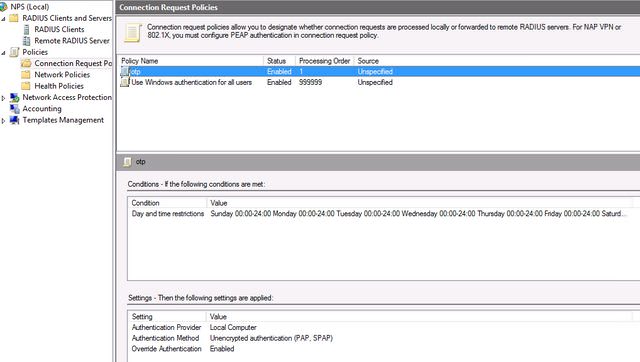
2. In the connection request policies, create a rule according to the enterprise security policy:
Adding a user with network access rights
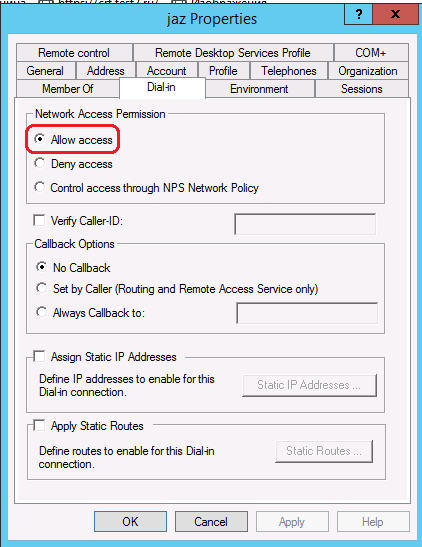
We create the user and on the Dial-in tab we provide network access rights:
Configure JAS Server
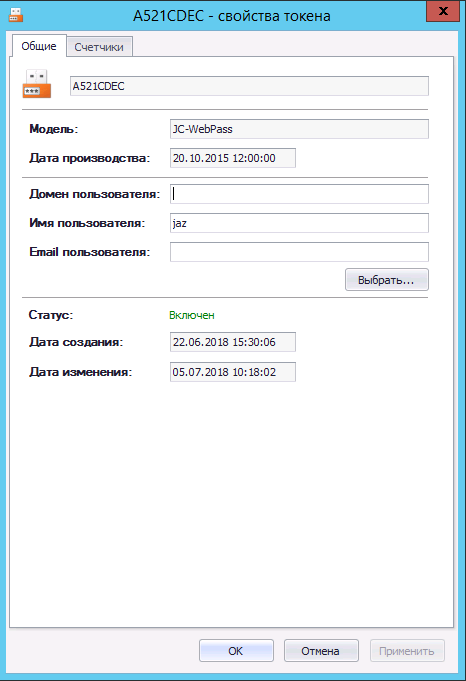
In the JAS management console, add any of the above OTP authenticators.
Specify the username in the properties:
For more information on configuring the JAS server, see the product documentation and the Knowledge Base .
Work check
In the browser, go to our site. Login and password must be requested. Enter username and one-time password:
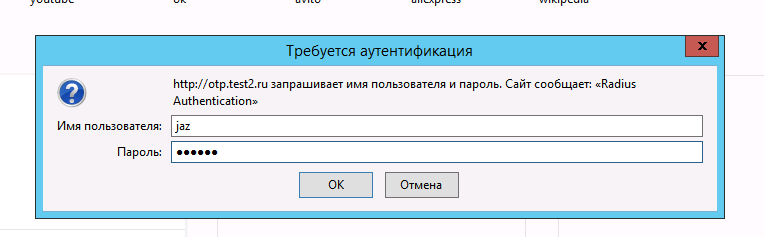
If everything is done correctly, we get access to our website, password protected:

Additionally:
www.adminsehow.com/2010/03/how-to-authenticate-apache-2-with-radius-on-debian