Collage Project: How to Combat Internet Censorship with Custom Content
A team of scientists from Georgia State University of Technology has published the concept of a new lock bypass tool. The project is called Collage, and its concept involves the use of so-called user-generated content. We present to your attention the main points of this work.
Introduction
In the modern world, Internet blocking has long become something commonplace. Censorship is introduced not only by authoritarian regimes, in one form or another restrictions on freedom of speech exist even in such democratic countries as Great Britain, Australia or South Korea.
In parallel with the spread of censorship, block bypass systems are also developing. Most censorship tools that exist today involve the use of proxies, but it is often easy for the censor to detect and block them. For advanced censors, this is not difficult - for example, in China they effectively block Tor.
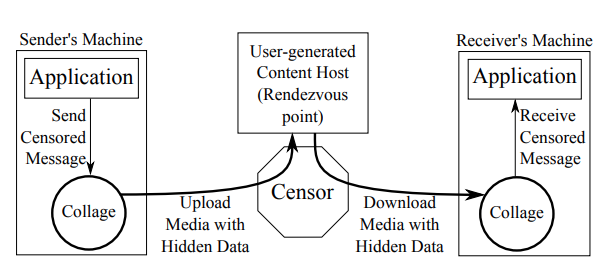
In this study, scientists at the University of Georgia tried to describe a method of bypassing locks that does not rely on one or more proxies, but involves a massive launch of sites that host user-generated content.
Concept: Collage Project
The idea is to use user-generated content as a disguise for Internet traffic. Collage uses existing sites to host user-created content (blog platforms, social networks, etc.) that hides encrypted messages.
For the censor, finding and blocking content that is hidden in photos, text and videos all over the Internet is a much more difficult task than finding and blocking a specific proxy.
Considerations for Censor Activities
It is assumed that the censor does not plan to completely block the Internet, some connections are considered allowed. However, for him, the ability to monitor, analyze, block or change some parts of the traffic is important.
Also, the developers of the system believed that the censor has enough resources in order to arrange the iron for monitoring traffic on a large number of network sections.
At the same time, the objectives of the censor may change. One of them is the pursuit of specific users, for which purpose the identification of patterns of behavior based on traffic is used. Another task is to block specific content, in order to solve it, the censor can even distort the traffic so that the forbidden content simply does not open by the browser.
How it works
Collage system consists of three levels: vector, message level and application level.
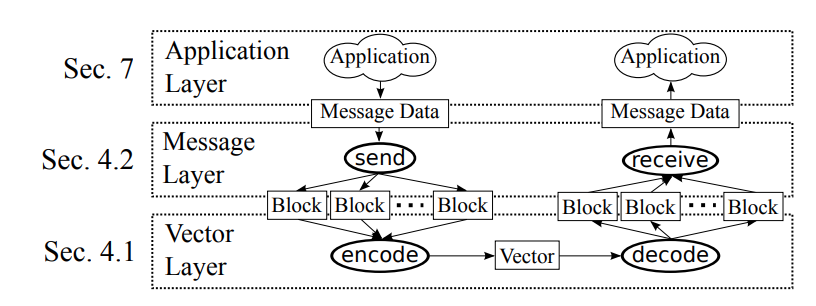
Three-level Collage model. Operations are shown in ovals, intermediate data in rectangles.
At the vector level, “masking content” is created in which the message is written. For example, this can be a video with an encrypted message, and in this case the YouTube video will be the vector. The second level is responsible for the description of the protocol for sending and receiving messages. Above all this, you can add any number of applications.
For successful data exchange, the sender and the recipient of information must conduct the rendezvous procedure. To do this, each of them performs a certain sequence of actions. For example, the sender can generate a sequence of HTTP requests that are decrypted as “upload a photo with the“ flowers ”tag to Flickr hosting, and the recipient should send a request“ find on Flickr a photo with the “flowers” tag and upload the first 50 of them. ”
The final implementation of Collage is a Python library with 650 lines of code. It describes the message level logic, including the job database, vector encoding and decoding. To complete the tasks, the popular browser automation tool Selenium is used. The application visits websites, performs the necessary tasks and downloads vectors.
Other articles on the use of resident proxies for business:
All Articles