Passive DNS in the hands of the analyst
The Domain Name System (DNS) is like a phone book that translates user-friendly names, such as “ussc.ru”, into IP addresses. Since DNS activity is present in almost all communication sessions, regardless of protocol. Thus, DNS logging is a valuable data source for an information security specialist, allowing them to detect anomalies or obtain additional data about the system under study.
In 2004, Florian Weimer proposed such a method of logging as Passive DNS, which allows you to restore the history of DNS data changes with the ability to index and search, which can provide access to the following data:
- Domain name
- IP address of the requested domain name
- Date and time of reply
- Response type
- etc.
Data for Passive DNS is collected from recursive DNS servers with built-in modules or by intercepting responses from the DNS servers responsible for the zone.
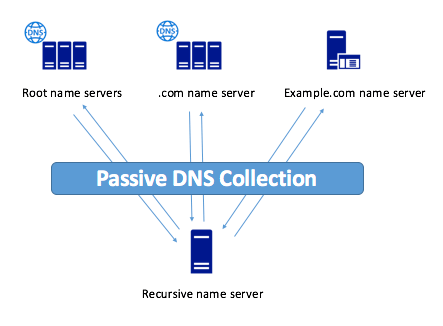
Figure 1. Passive DNS (taken from Ctovision.com )
The peculiarity of Passive DNS is that there is no need to register the client's IP address, which helps protect user privacy.
At the moment, there are many services that provide access to Passive DNS data:
| DNSDB | VirusTotal | Passivetotal | Octopus | Securitytrails | Umbrella Investigate | |
|---|---|---|---|---|---|---|
| Company | Farsight security | VirusTotal | Riskisk | SafeDNS | Securitytrails | Cisco |
| Access | Upon request | No registration required | Free registration | Upon request | No registration required | Upon request |
| API | Is present | Is present | Is present | Is present | Is present | Is present |
| Customer availability | Is present | Is present | Is present | Absent | Absent | Absent |
| Start data collection | 2010 year | year 2013 | year 2009 | Displays only the last 3 months | 2008 year | 2006 year |
Table 1. Services with access to Passive DNS data
Options for using Passive DNS
Using Passive DNS, you can build connections between domain names, NS servers and IP addresses. This allows you to build maps of the systems under study and track changes in such a map from the first detection to the current moment.
Passive DNS also facilitates the detection of traffic anomalies. For example, tracking changes in NS zones and records like A and AAAA allows you to detect malicious sites using the fast flux method, which is designed to hide C&C from detection and blocking. Since legitimate domain names (with the exception of those used for load balancing) will not often change their IP addresses, and most legitimate zones rarely change their NS servers.
Passive DNS, in contrast to direct enumeration of subdomains in dictionaries, allows you to find even the most exotic domain names, for example, “222qmxacaiqaaaaazibq4aaidhmbqaaa0undefined7140c0.p.hoff.ru”. It also sometimes allows you to find test (and vulnerable) areas of a website, materials for developers, etc.
Examining links from emails using Passive DNS
At the moment, spam is one of the main ways through which an attacker penetrates the victim’s computer or steals confidential information. Let's try to examine the link from such a letter using Passive DNS to evaluate the effectiveness of this method.
Figure 2. Spam email
The link from this letter led to the site magnit-boss.rocks, which offered to automatically collect bonuses and receive money:

Figure 3. The page hosted on the magnit-boss.rocks domain
To study this site, the Riskiq API was used, which already has 3 ready-made clients in Python , Ruby and Rust .
First of all, we will learn the whole history of this domain name, for this we use the command:
pt-client pdns --query magnit-boss.rocks
This command will display information about all DNS resolutions associated with this domain name.
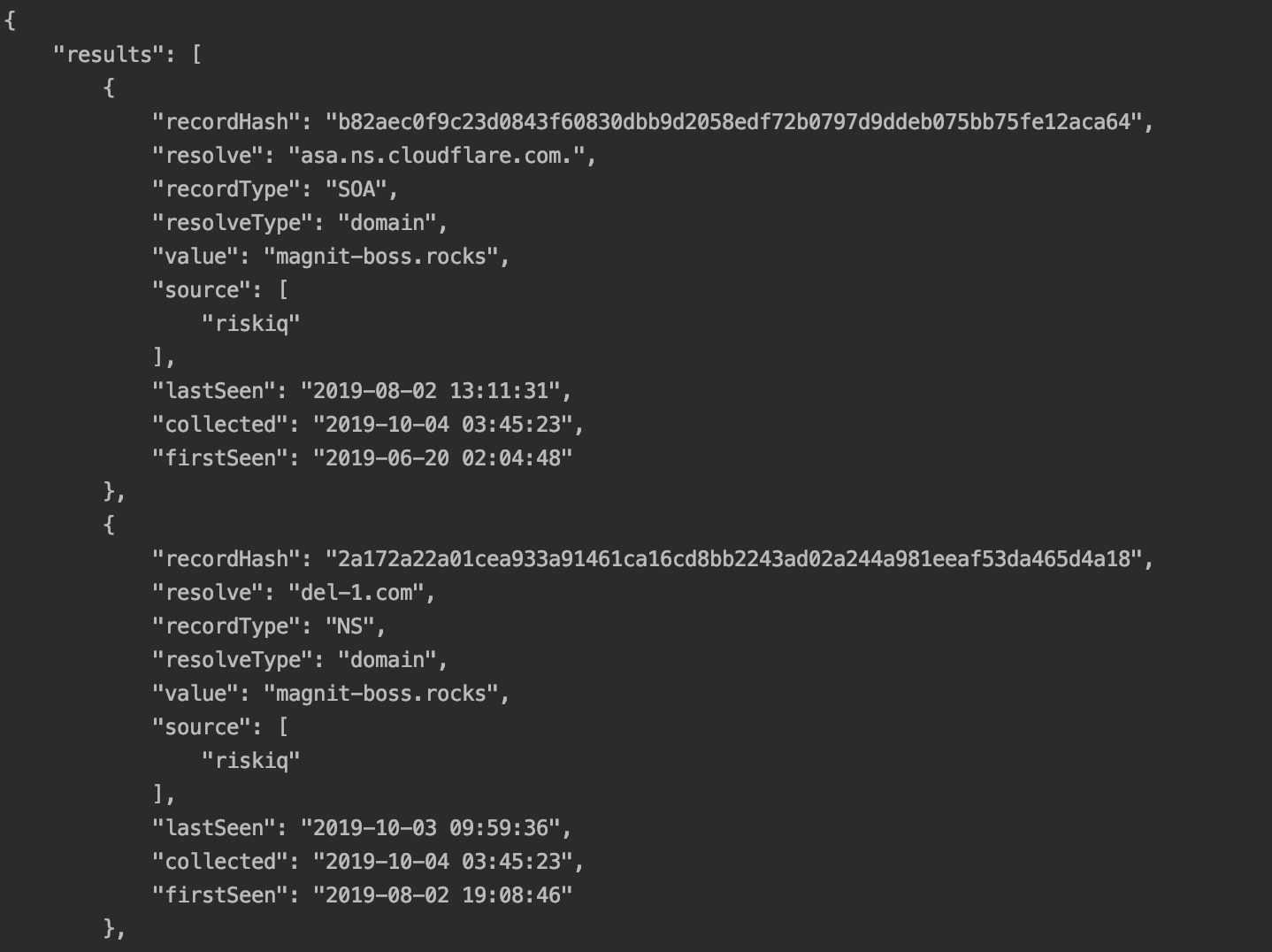
Figure 4. Response from the Riskiq API
Let's bring the answer from the API to a more visual form:
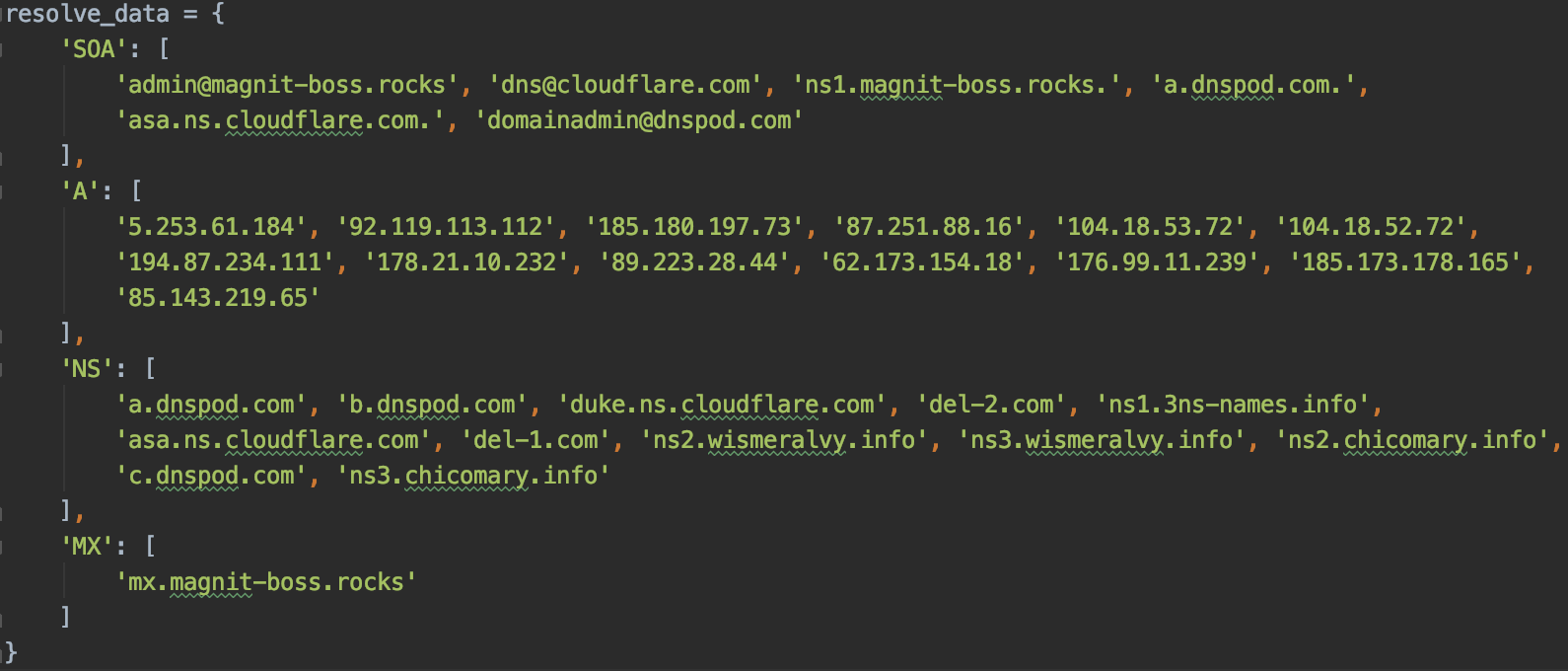
Figure 5. All records from the response
For further research, IP addresses were taken to which this domain name was resolved at the time of receipt of the letter 01.08.2019, such IP addresses are the following addresses 92.119.113.112 and 85.143.219.65.
Using the command:
pt-client pdns --query
you can get all the domain names that are associated with these IP addresses.
IP-address 92.119.113.112 has 42 unique domain names that resolved into this IP-address, among which there are such names:
- magnit-boss.club
- igrovie-avtomaty.me
- pro-x-audit.xyz
- zep3-www.xyz
- and etc
IP address 85.143.219.65 has 44 unique domain names that resolved to this IP address, among which there are such names:
- cvv2.name (site for the sale of credit card data)
- emaills.world
- www.mailru.space
- and etc
Connections with these domain names suggest phishing, but we believe in good people, so we’ll try to get a bonus of 332,501.72 rubles? After clicking on the “YES” button, the site asks us to transfer 300 rubles from the card to unlock the account and sends us to as-torpay.info to enter data.

Figure 6. Ac-pay2day.net home page
It looks like a legal site, there is an https certificate, and the main page offers to connect this payment system to your site, but, alas, all the links to the connection do not work. This domain name resolves to only 1 ip-address - 190.115.19.74. It, in turn, has 1475 unique domain names that resolved to this IP address, including such names as:
- ac-pay2day.net
- ac-payfit.com
- as-manypay.com
- fletkass.net
- as-magicpay.com
- and etc
As we can see, Passive DNS allows you to quickly and efficiently collect data about the investigated resource and even build a kind of imprint that allows you to reveal a whole scheme for the theft of personal data, from its receipt to the likely point of sale.

Figure 7. Map of the investigated system
Not everything is as rosy as we would like. For example, such investigations can easily break up on CloudFlare or similar services. And the effectiveness of the collected database is very dependent on the number of DNS queries passing through the module for collecting Passive DNS data. Nevertheless, Passive DNS is a source of additional information for the researcher.
Author: Specialist of the Ural Center for Security Systems
All Articles